Summary:
Keypoints:
MITRE Techniques
10/25/2024
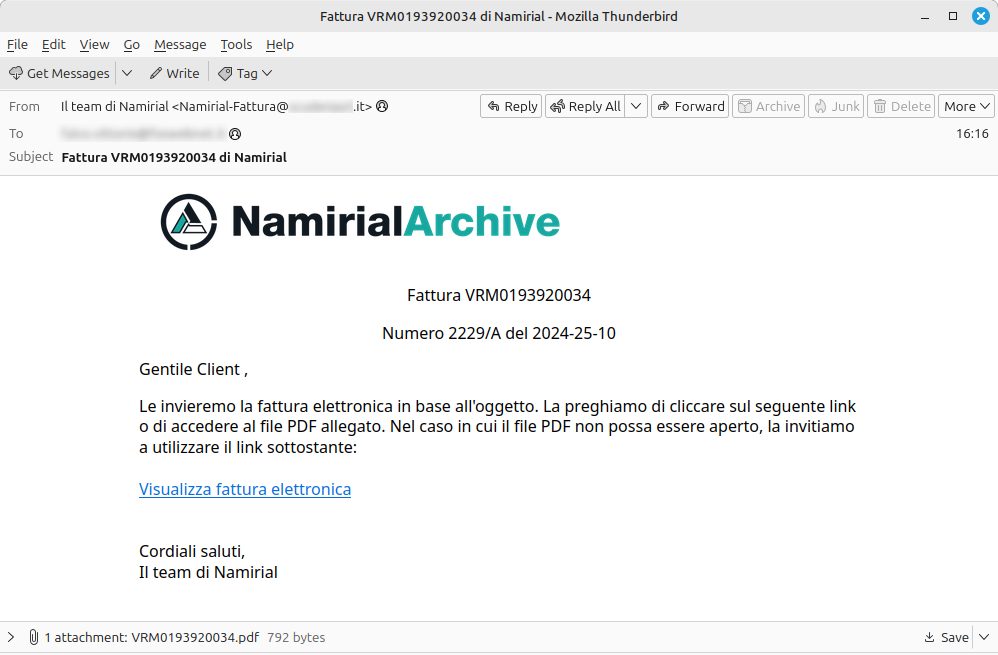
The CERT-AGID has detected a malicious campaign aimed at distributing the XWorm RAT trojan, disseminated through fake emails disguised as official communications from provider Namirial.
The email, written in Italian, invites the user to view an attached PDF document and, in case the file does not open correctly, suggests using an alternative link present in the body of the message.
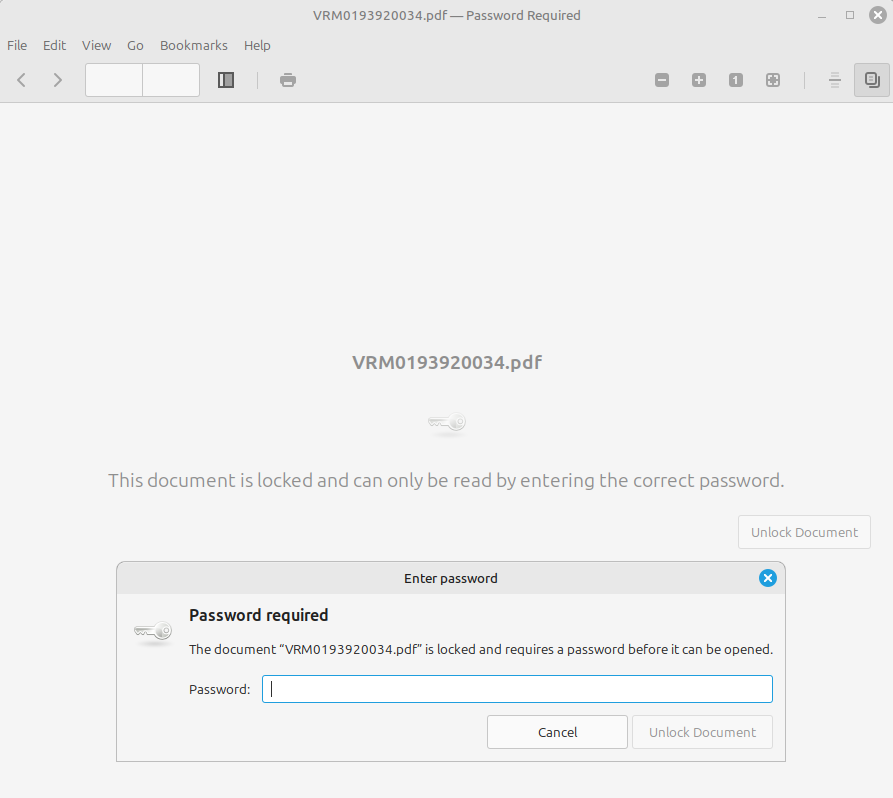
In reality, the PDF file acts as bait, as it is password-protected. This leads the victim to click on the only available alternative link that initiates the download of a ZIP archive, hosted on Dropbox, containing a URL file. From here, the chain of compromise begins.
The URL file exploits the TryCloudflare feature, which allows attackers to create temporary tunnels to local servers and test the service without needing a Cloudflare account. Each tunnel generates a random subdomain on the trycloudflare.com domain, used to route traffic through the Cloudflare network to the local server.
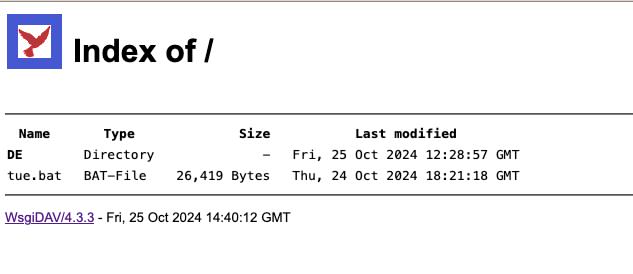
The URL file then proceeds to download a BAT file, obfuscated using the BatchShield tool. This can be easily deobfuscated using a specific tool called BatchShield decryptor.
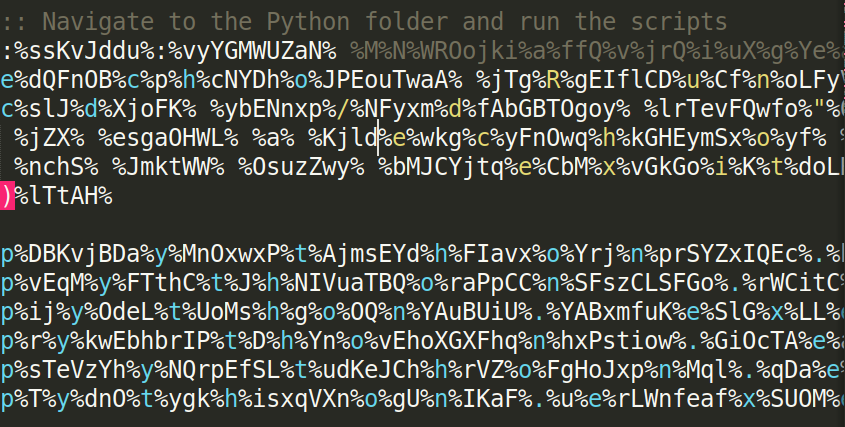
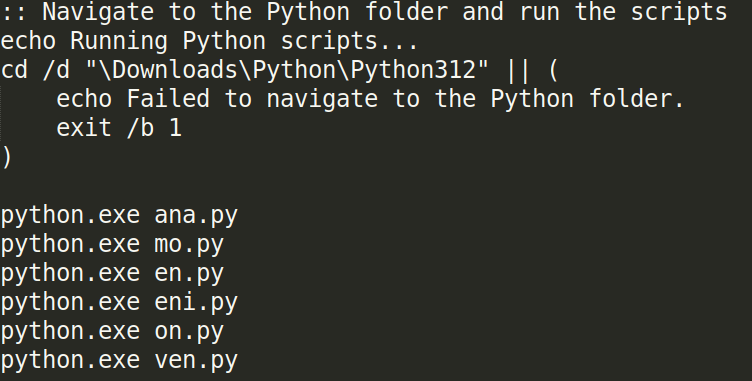
At this point, the procedure is well-known, having already been observed in previous campaigns. Another ZIP archive containing the Python interpreter is downloaded, which is used to execute the malicious scripts already included in the archive. This process leads to the release of one of the following malware: AsyncRAT, DCRat, GuLoader, VenomRAT, Remcos RAT, or, as in the current case, XWorm.
Indicators of Compromise
In order to make public the details of today’s campaign, the following IoCs have been detected:
Link: Download IoC
Source: Original Post