Short Summary:
Recent advancements in penetration testing for CICS and IMS applications have highlighted the need for enhanced security measures in mainframe environments. This article discusses seven common vulnerabilities found in these systems and offers methods for testing and mitigating these risks.
Key Points:
- Significant advancements in penetration testing for CICS and IMS applications.
- Over 90% of mainframes utilize CICS for transaction management.
- CICS and IMS are critical for various industries, including banking and retail.
- Common vulnerabilities include unencrypted data transmission, insecure password policies, and remote code execution.
- Tools like Hack3270 and CICSPwn are essential for testing and exploiting vulnerabilities.
- Regular testing and reviews of security controls are necessary to protect mainframe environments.
- New methodologies and tools continue to uncover weaknesses in mainframe systems.
MITRE ATT&CK TTPs – created by AI
- Unencrypted Transmission of Data – TTP ID: T1040
- Conduct Nmap port scans to identify insecure ports.
- Insecure Password Policies – TTP ID: T1110
- Test password complexity by attempting mixed-case submissions.
- Hidden Fields Exploitation – TTP ID: T1071
- Use Hack3270 to discover hidden fields in CICS applications.
- Protected Fields Manipulation – TTP ID: T1203
- Test locked fields for vulnerabilities using Hack3270.
- Access To Administrative Transactions – TTP ID: T1078
- Check if low-privileged users can access administrative transactions.
- Unauthenticated Access to Transactions – TTP ID: T1070
- Test for authentication bypass by exiting authentication workflows.
- Remote Code Execution – TTP ID: T1203
- Use CECI commands to submit JCL and test for vulnerabilities.
In recent years, significant advancements have taken place within the field of penetration testing CICS and IMS applications. Open-source tool development and an overall rising demand for mainframe security evaluation have accelerated both the desire and required capabilities for mainframe pentesting services. In this post, we will cover 7 different ways to test your mainframe applications for vulnerabilities that are commonly seen in the wild.
It is estimated that over 90% of mainframes in use today implement CICS for transaction management and it is more critical than ever for practitioners to invest in the security of these trusted environments.
What is Customer Information Control System (CICS)?
The Customer Information Controls System, commonly known as CICS, is a transaction processing system originally developed by IBM in 1968 to deal with the limitations of traditional batch system tasks that needed access to the same resources (datasets, directories, etc.) at the same time. CICS has evolved over time to find prolific use in modern banking, insurance, retail, government, and other critical industries.
Key features of CICS
- Deployed on z/OS and z/VSE to provide an environment for transaction management
- A middleware-like mixed-language application server that is often referred to as a region
- Handles communications between user interfaces (e.g., terminals or web interfaces) and backend databases or services (DB2, SOAP, REST, RACF)
- Processes large volumes of online transactions* rapidly and with high reliability.
Summarily, CICS is responsible for managing real-time transactions on mainframes.
* A CICS transaction is a unit of processing initiated by a single request that may affect one or more objects
What is Information Management System (IMS)?
IMS (Information Management System) is a hierarchical database and transaction management system for mainframes. Also developed by IBM, IMS is widely used in finance, telecommunications, and retail industries for high-volume transaction processing and data management.
Two primary components
- The IMS DB (Database Manager) is a structured, non-relational database management system. It is optimized for fast access to large volumes of data, making it suitable for high-throughput environments.
- IMS TM (Transaction Manager) is used to control execution of transactions. It facilitates concurrent and reliable processing of real-time transactions in a queue-based system and handles communication between end users and applications accessing IMS DB.
In short, IMS is a hierarchical database and real-time transaction processing solution for mainframes.
Let’s now take a look at the following vulnerabilities within CICS and IMS applications and explore the accompanying tools and methods that may be used to discover them. All examples are based on real-world findings identified in NetSPI-conducted penetration tests.
- Unencrypted Transmission of Data
- Insecure Password Policies
- Hidden Fields Exploitation
- Protected Fields Manipulation
- Access To Administrative Transactions
- Unauthenticated Access to Transactions
- Remote Code Execution
1. Unencrypted Transmission of Data
Weakness
If the CICS region resides on an LPAR that uses unencrypted protocols, data transmitted will be susceptible to attacker-in-the-middle attacks. Any sensitive data intercepted will be in plaintext and entirely unencrypted, making it much easier for rapid theft of data to occur. Unencrypted ports frequently seen in use on mainframes are FTP/21 and Telnet/23 for TN3270. These insecure services could also potentially run on any port number depending on network configurations in use.
Test
To investigate, conduct a basic Nmap port scan of the CICS IP address to help determine if insecure ports are in use.
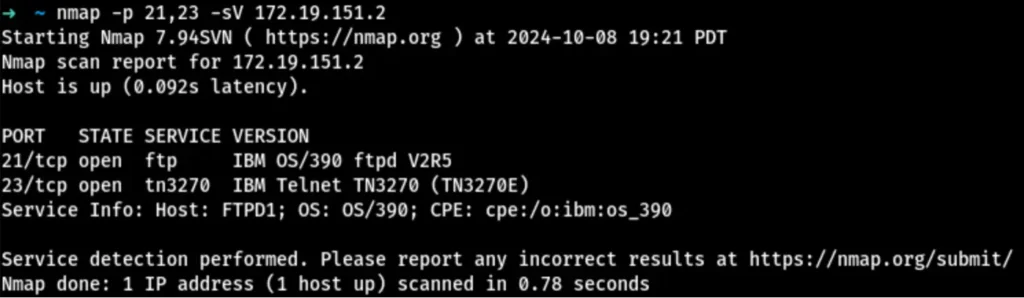
In the Nmap results seen above, unencrypted Telnet over port 23 and unencrypted FTP over port 21 are permitted for use. Insecure protocols such as Telnet or FTP transmit data in plaintext that if intercepted is easily readable.
2. Insecure Password Policies
Weakness
When authentication to CICS applications requires a low-level of password complexity, the ability for an attacker to successfully brute-force valid passwords becomes much more of a threat.
Test
Investigate password policies by checking for sufficient complexity or modifying what is submitted during authentication to test if validation is adequately secure.
- Connect to the appropriate CICS or IMS region for the test.
- At the logon command prompt, input a valid password but using invalid mixed case. For example, if the password is Netspi27, submit nETSPI27.
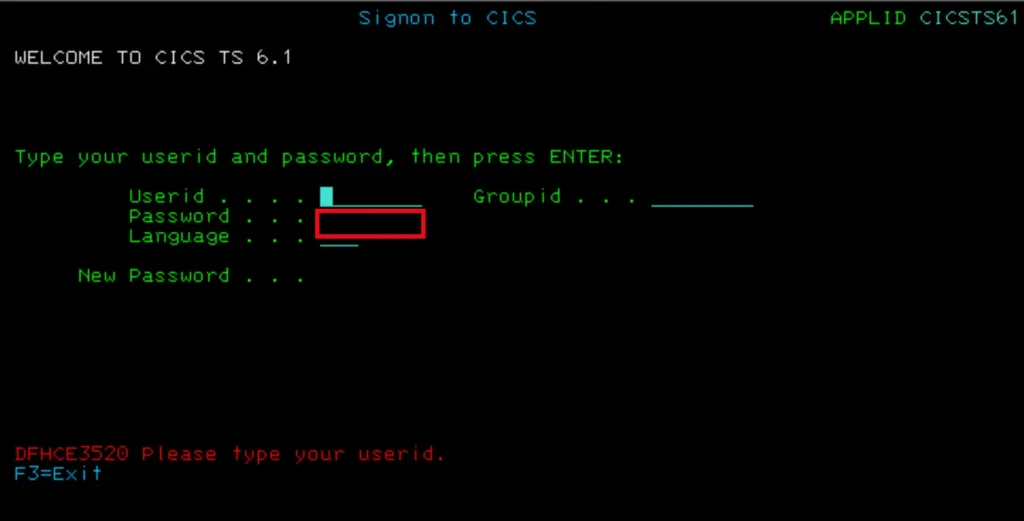
- If the session logs on successfully, passwords are insensitive to mixed-case submissions.
Weak passwords may arise in situations like the example shown above in which mixed case submissions are improperly validated. Another common scenario is allowing passwords that consist of less than 8 characters. When weak passwords are located alongside something like user enumeration (via differences in error messages or other means), the time it would take to brute force entire credential sets is dramatically reduced.
3. Hidden Fields Exploitation
Weakness
With the use of recently developed open-source tools like Hack3270, hidden fields within mainframe applications may be susceptible to unintended information disclosure or transaction and record manipulation.
Test
Utilize Hack3270 (https://github.com/gglessner/hack3270) to examine various CICS screens to see if additional functionality or information might be discovered.
- Connect to your test IP with a mainframe emulator, such as x3270.
- Launch the Hack3270 tool with the following command:
./hack3270.py [IP] [port] -t -d
- A proxy listener will be established over port 3271. Connect to the proxy with x3270 and select “Click to Continue.”
X3270 Connection pending
X3270 Connected
After submitting “Click to Continue”

- Complete any required authentication steps.
- Navigate to various transactions within the application, toggling the Hack Fields button between OFF and ON to see if hidden fields might be discovered.
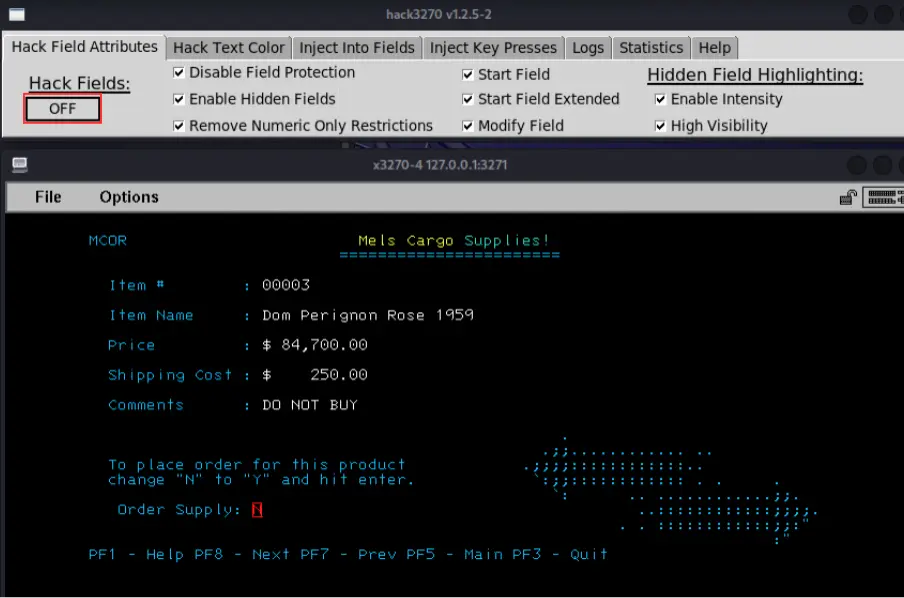
- In the example below an editable field that grants transaction permissions has been uncovered.

- This scenario illustrates how it may be possible to unhide fields designed to permit specific authorized actions within the context of a mainframe application transaction screen.
4. Protected Fields Manipulation
Weakness
In addition to hidden fields, locked or protected fields within CICS screens may also be vulnerable to data or transaction tampering.
Test:
- Follow steps 1-4 in the above example.
- Locate a transaction that is disallowed for the authenticated user.
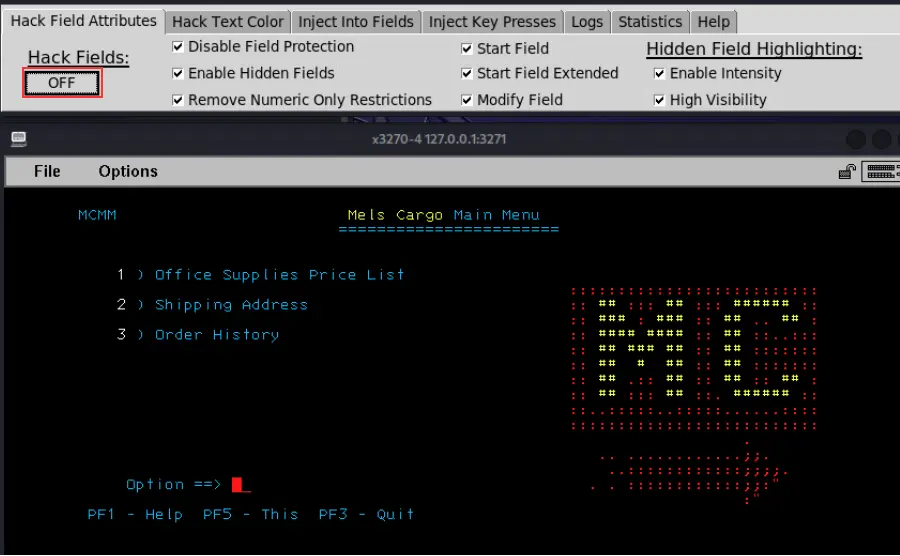
- With Hack Fields toggled to ON, take note of the locked Delete Order History transaction.
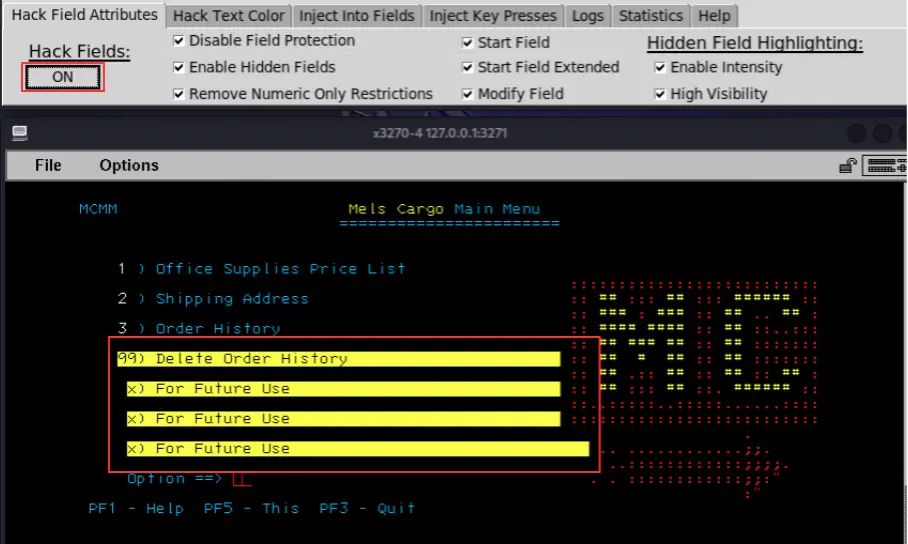
- Submit the transaction. If it completes successfully, the application is vulnerable to manipulation of protected fields.
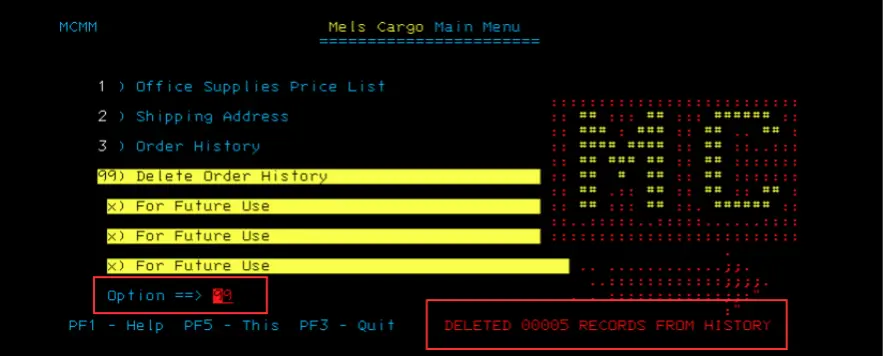
When locked fields are implemented as a means of security control, reviewing whether the configurations are susceptible to bypass with modern tooling is incredibly important.
5. Access To Administrative Transactions
Weakness
Users should only be granted access to the transactions they require for the specific duties of their role. Administrative transactions, such as CEMT, would allow an attacker to profile an entire CICS region and potentially disable transactions used for critical business functions.
Test
- Authenticate to the application as a lower-privileged user
- Clear the screen
- Input the transaction codes as seen below to determine whether a regular user is able to access or perform transactions that should require higher permission levels.
Examples
CICS:
CEMT INQ TRANto display all transactionsCECI START TRANSID('tranname')to execute a command in the region and display the result
IMS:
/DIS DB [dbname]to display the status of a database/DIS TRAN [tranname]to display the status of a transaction
If these transactions run for low-level users, access controls may need to be reassessed and reconfigured more appropriately for improved security.
6. Unauthenticated Access to Transactions
Weakness
When accessing CICS transactions authentication is required. However, if access controls are misconfigured, some bypasses may be possible. This can result in completely unauthenticated transaction processing.
Test
Exit authentication workflows during various stages of the process. Once exited, test to see if it is possible to submit CICS or IMS commands without authentication.
- Connect to the IP and port for the test. Input the appropriate command (i.e. DIMS) to reach the authentication screen.
- Input PF2 or another assigned key to exit the logon screen before completing authentication. Open the keyboard icon in an emulator or use your physical keyboard to do this, depending on how the region has been accessed.
- Once the log on process has been terminated, attempt to enter a CICS or IMS transaction number (ex:CECI) and select Enter.
If any CICS or IMS transactions run at this point, authentication controls have been successfully bypassed.
7. Remote Code Execution
Weakness
As mentioned earlier, CECI is a CICS command (command-level interpreter transaction) that is active by default but ideally should be disabled. CECI is an interface for CICS region APIs known as CICS Commands, one of these being the SPOOLOPEN transaction used to facilitate job submission to the internal JES2 reader. SPOOLOPEN may permit users to generate reverse shells with only limited access to CICS.
Test
- Connect to the CICS region. If presented with a CESN logon screen, select F3 to exit.
- Enter CECI on the screen
- Using the SPOOLWRITE and variable features of CECI, submit JCL. This can be accomplished with the following CECI command:
CECI SPOOLOPEN OUTPUT USERID('INTRDR ') NODE('LOCAL') TOKEN(&TOKTEST) - Create a variable in CECI and use the command below to write the JCL to the internal reader, one line at a time:
SPOOLWRITE TOKEN('TOKEN') FROM(&SQLKHDS) FLENGTH(80) - When the job is submitted it will run at the same permission level as the CICS default user
- This can be automated with CICSPwn as a single command:
python cicspwn.py -a APPLID -s custom --jcl /tmp/temp.jcl HOST/IP PORT
This bypass essentially grants an unauthenticated user the ability to submit JCL to the internal reader, which opens the door for many more compromises. Reverse shells on the mainframe could be established through this attack, potentially handing total control of mainframe resources over to an anonymous user.
Conclusion
Though CICS and IMS applications have been in use for many years, new penetration testing tools and methodologies are still uncovering previously unknown weaknesses in mainframe environments. From simple access control issues to total mainframe compromise, the range of potential threats for mainframes are as varied as those found against any other system or network.
Methodical techniques, frequent testing, and thorough reviews of controls from a creative mindset are all ways to help protect the attack-surface landscape of these critical systems.
For additional support, follow our technical updates on the NetSPI Hack Responsibly blog, review presentations given by our team at various events including DEFCON, BSides, SHARE, and others (Phil Young/Soldier of FORTRAN, David Bryan/VideoMan, Michelle Eggers), and keep an eye out for new open-source tooling that can assist in your mainframe testing activities.
To learn more about NetSPI Mainframe Pentesting, please visit: https://www.netspi.com/netspi-ptaas/network-penetration-testing/mainframe/
CICS Pentesting Resources
- Hack3270 – Tool used to unhide fields, unlock fields, submit keypresses, and log activity
- Damn Vulnerable CICS Application – Test environment to explore vulnerabilities
- CICSPwn – Pentesting tool used for reconnaissance, automation, and exploitation
The post Hacking CICS: 7 Ways to Defeat Mainframe Applications appeared first on NetSPI.

