Summary: Rapid7 Labs has published a report detailing CyberVolk, a politically motivated hacktivist group that has shifted to ransomware attacks, particularly targeting Spain in response to geopolitical events. The report highlights CyberVolk’s unique tactics, including a combination of DDoS and ransomware attacks, and examines the technical aspects of their ransomware.
Threat Actor: CyberVolk | CyberVolk
Victim: Various Spanish entities | Spanish entities
Key Point :
- CyberVolk emerged in June 2024, evolving from DDoS attacks to ransomware, targeting Spanish institutions.
- The ransomware features unique behaviors, including changing the victim’s wallpaper and monitoring Task Manager to avoid detection.
- Despite technical flaws, such as weak key validation and errors in the ransom note, CyberVolk has caused significant disruption to at least 27 entities in Spain.
- CyberVolk’s code shows similarities to Babuk ransomware, indicating a reuse of cryptographic routines while incorporating its own enhancements.
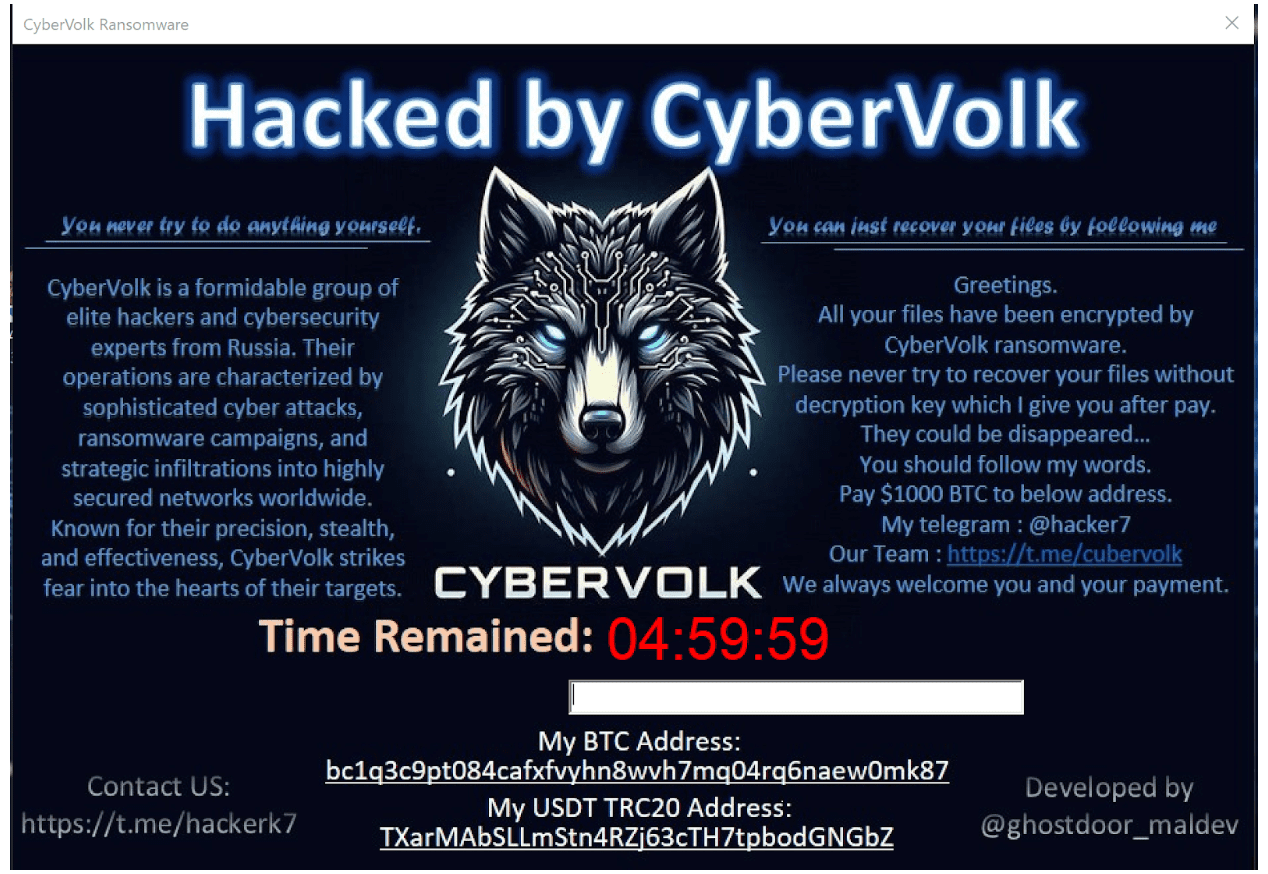
Cybersecurity researchers at Rapid7 Labs have released a detailed report on CyberVolk, a politically motivated hacktivist group that transitioned into using ransomware as a primary tool in their attacks. Emerging in June 2024, CyberVolk has rapidly become a significant threat, particularly targeting Spain in retaliation for geopolitical events, as outlined in Rapid7’s analysis.
CyberVolk’s origins are tied to the broader pro-Russian hacktivist movement. Initially, the group’s operations involved Distributed Denial of Service (DDoS) attacks, but the arrest of members from the notorious NoName57(16) group prompted a change in tactics. According to Rapid7, CyberVolk, alongside over 70 affiliated hacktivist groups, escalated their operations by adopting ransomware attacks, launching coordinated campaigns against Spanish institutions. As noted in the report, “CyberVolk initially positioned itself as a hacktivist organization, and then started to use ransomware as a tool for retaliation.”
CyberVolk’s mix of DDoS and ransomware attacks is a concerning development, particularly for critical infrastructure and government entities.
Rapid7’s analysis delves into the technical aspects of the CyberVolk ransomware itself, offering insights into how it operates and what makes it distinct from other ransomware strains. The report details how the ransomware follows a standard execution flow, but with some unique features:
- Wallpaper Change Pre-Encryption: One of the more unusual behaviors of CyberVolk ransomware is that it changes the victim’s desktop wallpaper to an image file (
tmp.bmp) before encryption even begins. - Task Manager Monitoring: To avoid detection, CyberVolk actively monitors if Task Manager is running and attempts to terminate it. As the report explains, “Another thread checks repeatedly if Task Manager is running by searching for a window with the class name ‘TaskManagerWindow.’ If found, it attempts to kill the process by sending a WM_CLOSE message.“
- File Encryption: CyberVolk encrypts files and assigns them a .cvenc extension. The encryption is thorough, scanning directories and subdirectories to ensure maximum disruption.
- Decryption Process: After encrypting the files, the ransomware presents the victim with a ransom note and demands payment in Bitcoin or USDT. However, Rapid7’s experiments found that the ransomware’s decryption process has some weaknesses. “CyberVolk’s key validation is weak enough that even random keys trigger the decryption routine, though files remain unusable without the correct key,” the report states, revealing a flaw in the ransomware’s functionality.
- Ransom Note Errors: In a bizarre oversight, the ransom note directs victims to a non-existent Telegram channel for payment instructions. “Looks like the ransomware creators were in such a rush to demand the ransom that they forgot to double-check their own link,” Rapid7 notes.
Further investigation into CyberVolk’s code revealed similarities with the infamous Babuk ransomware. Rapid7’s comparison using BinDiff showed overlaps in cryptographic routines, suggesting that CyberVolk’s developers likely reused portions of Babuk’s encryption framework. However, CyberVolk also adds its own enhancements, such as AES encryption and anti-analysis techniques to evade detection.
Despite some of its technical flaws, CyberVolk has proven to be a significant threat, particularly in Spain, where 27 entities have reportedly been affected since the group’s campaign began. The combination of ransomware and DDoS attacks sets CyberVolk apart from other groups, and as they refine their tactics, the threat will only grow. As the report emphasizes, “CyberVolk is evolving and has already proven effective, causing significant damage to entities in Spain.”
Related Posts:
Source: https://securityonline.info/cybervolk-from-hacktivism-to-ransomware-researcher-exposes-new-threat
Views: 0