Summary: Cisco has issued a security advisory for a critical vulnerability (CVE-2024-20432) in its Nexus Dashboard Fabric Controller (NDFC) that could allow low-privileged attackers to execute arbitrary commands on managed devices. The flaw, rated 9.9 on the CVSS scale, arises from improper user authorization and insufficient command validation in the REST API and web UI.
Threat Actor: Low-privileged remote attacker | low-privileged remote attacker
Victim: Cisco Nexus Dashboard Fabric Controller | Cisco Nexus Dashboard Fabric Controller
Key Point :
- The vulnerability allows authenticated attackers to execute arbitrary commands on managed devices.
- It affects the REST API and web UI due to improper user authorization and insufficient command argument validation.
- Successful exploitation could compromise the entire network fabric managed by Cisco NDFC.
- Cisco has released software updates to address the vulnerability, and no workarounds are available.
- As of the advisory’s release, there are no known public exploitations of this vulnerability.
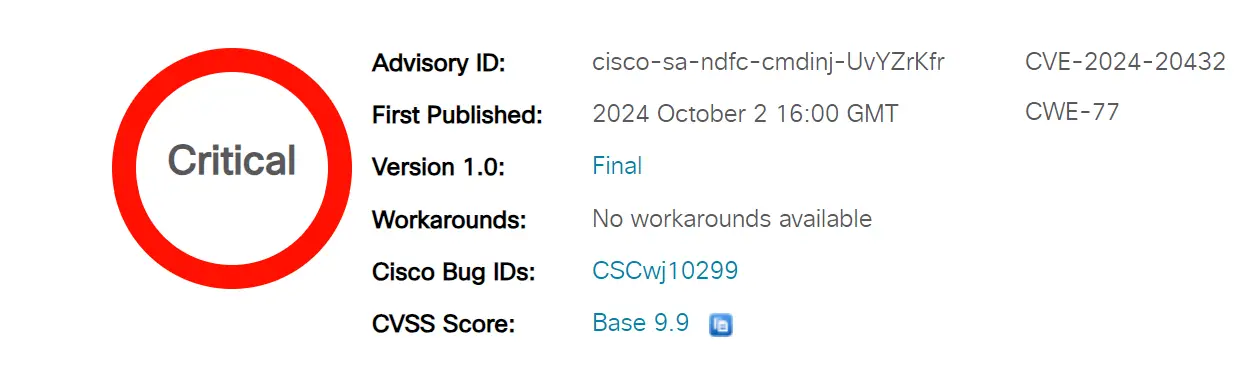
Cisco has issued a security advisory addressing a critical vulnerability (CVE-2024-20432) in its Nexus Dashboard Fabric Controller (NDFC). This flaw, which carries a severity rating of 9.9 out of 10 on the CVSS scale, could allow an authenticated, low-privileged remote attacker to execute arbitrary commands on managed devices with network-admin privileges.
The vulnerability resides in the REST API and web user interface of Cisco NDFC. It stems from improper user authorization and insufficient validation of command arguments. An attacker with valid credentials could exploit this weakness by submitting crafted commands to an affected REST API endpoint or through the web UI.
Successful exploitation could grant the attacker the ability to run arbitrary commands on the command-line interface (CLI) of a Cisco NDFC-managed device, potentially compromising the entire network fabric.
The CVE-2024-20432 vulnerability affects
- Cisco Nexus Dashboard Fabric Controller (NDFC)
- Note: This vulnerability does not affect Cisco NDFC when configured for Storage Area Network (SAN) controller deployment.
- Starting with Cisco Nexus Dashboard Release 3.1(1k), Cisco NDFC is distributed in unified releases.
Cisco has released software updates to address this critical vulnerability. There are currently no workarounds, making it imperative for administrators to act promptly.
| Cisco NDFC Release | First Fixed Release |
|---|---|
| 11.5 and earlier | Not vulnerable |
| 12.0 | 12.2.2 |
As of the advisory’s release, Cisco’s Product Security Incident Response Team (PSIRT) is not aware of any public exploitation of this vulnerability. However, given the critical nature of the flaw, the window for potential attacks remains open until patches are applied.