Summary: Google security researchers have highlighted the ongoing threat posed by info-stealing malware, specifically RECORDSTEALER, which specializes in stealing sensitive information like credit card data and passwords. Despite the arrest of its creator, the tactics used by RECORDSTEALER continue to influence modern cybercriminals.
Threat Actor: Cybercriminals | RECORDSTEALER
Victim: Internet users | internet users
Key Point :
- RECORDSTEALER was distributed through malicious ads and cracked software, often disguised as legitimate applications.
- The malware collected sensitive data from browsers and applications, including passwords, credit card information, and cryptocurrency wallets.
- Despite its creator’s arrest, the techniques used by RECORDSTEALER are still prevalent in other info-stealers, emphasizing the need for ongoing vigilance.
- Detection mechanisms focus on identifying suspicious archives and network activity to prevent data breaches.
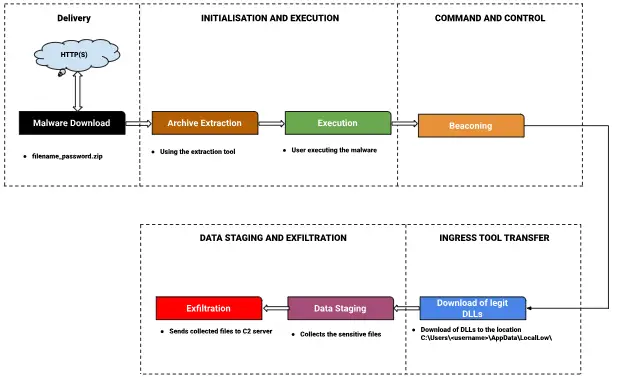
Google security researchers recently brought attention to the lingering impact of info-stealing malware. One such threat is the RECORDSTEALER malware, also known as RecordBreaker and Raccoon Stealer V2. This info-stealer, written in C, specializes in the theft of sensitive information, including credit card data, passwords, cookies, and cryptocurrency wallets.
RECORDSTEALER was actively disseminated through malicious advertising and downloads of cracked software, often masquerading as legitimate applications. The malware was delivered in a password-protected archive, with the user unwittingly entering the password to extract it. Once successfully executed, it transmitted system information to a command-and-control (C2) server via encrypted RC4 requests. Among the exfiltrated data were unique device identifiers, usernames, and other parameters essential for further attacks.
Although RECORDSTEALER’s activity ceased following the arrest of its creator and the dismantling of its infrastructure, the tactics employed in these attacks remain in use by modern info-stealers. Cybercriminals continue to propagate malware via cracked software and disguise their malicious payloads as legitimate programs, posing a significant threat to users.
The malware’s operation involved collecting and transmitting data from infected systems. RECORDSTEALER actively harvested information from Google Chrome and Mozilla Firefox browsers, including saved passwords, credit card data, and cookies. Additionally, it was capable of stealing cryptocurrency wallet information, taking desktop screenshots, and collecting files related to applications such as Telegram and Discord.
Notably, many techniques RECORDSTEALER utilizes persist in other info-stealers, such as VIDAR and STEALC. This underscores the importance of monitoring malware activity, as even minor code alterations can hinder detection.
Various detection mechanisms combat such threats, including tracking suspicious archives and activity in directories with minimal access permissions. Detecting early signs of infection, such as creating malicious files or suspicious network requests, enables timely responses to threats and helps mitigate the consequences of data breaches.