Summary: Security experts are warning about a new cyberattack method involving counterfeit CAPTCHA tests designed to distribute malware on Windows devices. Users are advised to remain vigilant and skeptical when faced with CAPTCHA challenges, as these can lead to the installation of harmful software like Lumma Stealer.
Threat Actor: Cybercriminals | cybercriminals
Victim: Windows Users | Windows Users
Key Point :
- Counterfeit CAPTCHA tests are being used to execute malicious commands on users’ devices.
- Completing these fake CAPTCHAs can lead to the installation of Lumma Stealer, which steals sensitive information.
- Cybercriminals are distributing these tests through phishing emails and compromised websites.
- Users should be cautious with CAPTCHA interactions and verify website legitimacy to avoid falling victim.
- Keeping systems updated and practicing safe browsing habits are essential for mitigating risks.
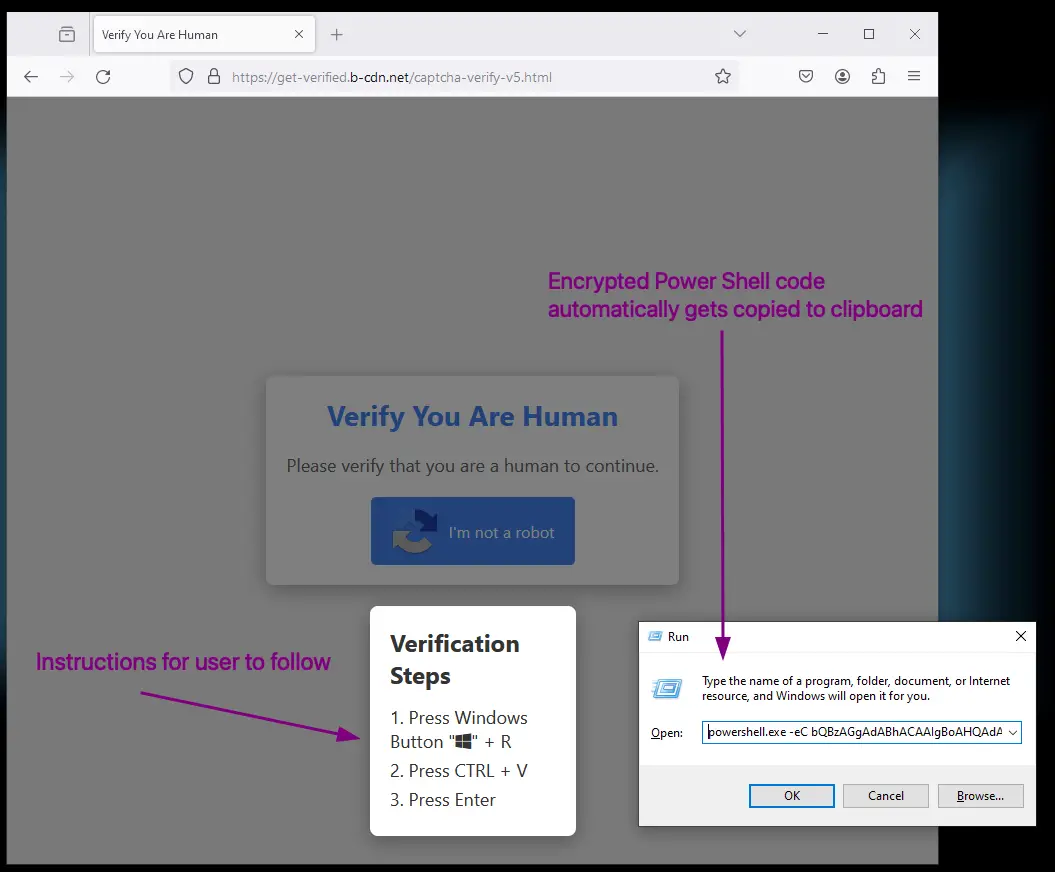
Security professionals are sounding the alarm about a novel cyberattack vector: the use of counterfeit CAPTCHA tests to distribute malware on Windows devices. Users are urged to exercise increased vigilance and skepticism when interacting with CAPTCHA challenges.
Traditional CAPTCHA tests serve as a security measure, ensuring that online actions are initiated by humans rather than automated bots. Cybercriminals have subverted this process, crafting fake CAPTCHA challenges that, when completed, execute a series of malicious commands.
These fake CAPTCHA tests prompt users to press “Windows + R” followed by “CTRL + V” and “Enter,” a sequence that, for many, may appear innocuous. However, this action triggers the download and execution of a PowerShell script that installs the Lumma Stealer malware.
2024-08-28 (Wednesday): More #Lumma #Stealer (#LummaStealer) from pages instructing potential victims to copy/paste #PowerShell script in a Run window. Recent examples of these human captcha style pages available at https://t.co/rMHcZ0Hesd #Unit42ThreatIntel #TimelyThreatIntel pic.twitter.com/GghbAPtFNc
— Unit 42 (@Unit42_Intel) August 29, 2024
According to cybersecurity researchers at Palo Alto Networks, Lumma Stealer is an information-stealing malware capable of exfiltrating sensitive data, including passwords, cookies, and cryptocurrency wallet credentials. The malware’s presence on a compromised device exposes users to significant risks of identity theft, financial fraud, and further cyberattacks.
The distribution of these malicious CAPTCHA tests is widespread, with researchers at Hudson Rock observing that visiting compromised websites can automatically copy the malicious script to a user’s clipboard. This increases the likelihood of unwitting execution.
Furthermore, cybersecurity expert John Hammond from Huntress has noted a recent resurgence of these attacks, suggesting that cybercriminals are actively refining and deploying this technique. These fake CAPTCHA tests can be distributed via phishing emails and messages, making them particularly dangerous.
To mitigate the risk associated with this new threat, users are advised to:
- Exercise caution with CAPTCHA: Be wary of any CAPTCHA test that requires actions beyond image selection or text input.
- Scrutinize URLs: Ensure the legitimacy of websites before interacting with any CAPTCHA challenge.
- Maintain updated systems: Keep operating systems, antivirus software, and web browsers up-to-date.
- Practice safe browsing habits: Avoid clicking on links or attachments in unsolicited emails or messages.
Related Posts:
Source: https://securityonline.info/cybercriminals-exploit-captcha-to-deliver-malware-experts-issue-warning