Short Summary:
Medusa is a Ransomware-as-a-Service (RaaS) targeting Windows environments, active since June 2021. It gained attention in early 2023 with the launch of its Dedicated Leak Site. Medusa spreads through exploiting vulnerabilities and hijacking accounts, utilizing advanced techniques to evade detection. Security teams are encouraged to validate their defenses against Medusa’s tactics using new tools from AttackIQ.
Key Points:
- Medusa Ransomware has been active since June 2021, primarily targeting Windows systems.
- Gained notoriety in early 2023 with the introduction of a Dedicated Leak Site (Medusa Blog).
- Should not be confused with MedusaLocker, another RaaS family active since 2019.
- Propagation methods include exploiting unpatched vulnerabilities and hijacking accounts.
- Employs Living-off-the-Land techniques to blend in with legitimate traffic.
- AttackIQ has released an attack graph to help validate security controls against Medusa’s TTPs.
- Security teams can assess their posture against opportunistic adversaries using AttackIQ’s tools.
- Recent reports indicate an escalation in Medusa’s activities as of January 2024.
- Medusa uses ASPX web shells and BITSAdmin jobs for payload deployment.
- Employs various WMI commands for local system and network reconnaissance.
- Encrypts files using RSA 2048 + AES 256 after deleting Volume Shadow Copies.
- Detection and mitigation strategies are recommended for key techniques used by Medusa.
- AttackIQ offers services to enhance security posture against ransomware threats.
Medusa is a Ransomware-as-a-Service (RaaS) primarily focused on Windows-based environments that has been active since June 2021. The ransomware gained notoriety in early 2023, following an escalation in its activities associated with the introduction of a Dedicated Leak Site (DLS) called Medusa Blog, a .onion site accessible via TOR.
Medusa Ransomware should not be confused with MedusaLocker, another similarly named RaaS family that has been active since mid-2019.
Medusa is predominantly propagated through the exploitation of vulnerable services, such as public-facing assets or applications with known unpatched vulnerabilities, and the hijacking of legitimate accounts, often using Initial Access Brokers (IABs) for infiltration.
The ransomware operators have been observed implementing Living-off-the-Land (LotL) techniques which employ legitimate software for malicious purposes, which can blend in with regular traffic and behavior, making detection challenging.
AttackIQ has released a new attack graph that brings together the post-compromise Tactics, Techniques, and Procedures (TTPs) exhibited by Medusa to help customers validate their security controls and their ability to defend against this disruptive and destructive threat.
Validating your security program performance against these behaviors is vital in reducing risk. By using this new assessment template in the AttackIQ Security Optimization Platform, security teams will be able to:
- Evaluate security control performance against baseline behaviors associated with the Medusa ransomware.
- Assess their security posture against an opportunistic adversary.
- Continuously validate detection and prevention pipelines against a playbook similar to those of many of the groups currently focused on ransomware activities.
Medusa Ransomware – 2024-01 – Complete Infection Chain
 Click for larger
Click for larger
In January 2024, Palo Alto Networks reported having noticed an escalation in activity associated with Medusa ransomware. In addition, they reported previously responding to a Medusa-related incident which allowed them to uncover interesting Tactics, Tools, and Procedures (TTPs) used by Medusa operators.
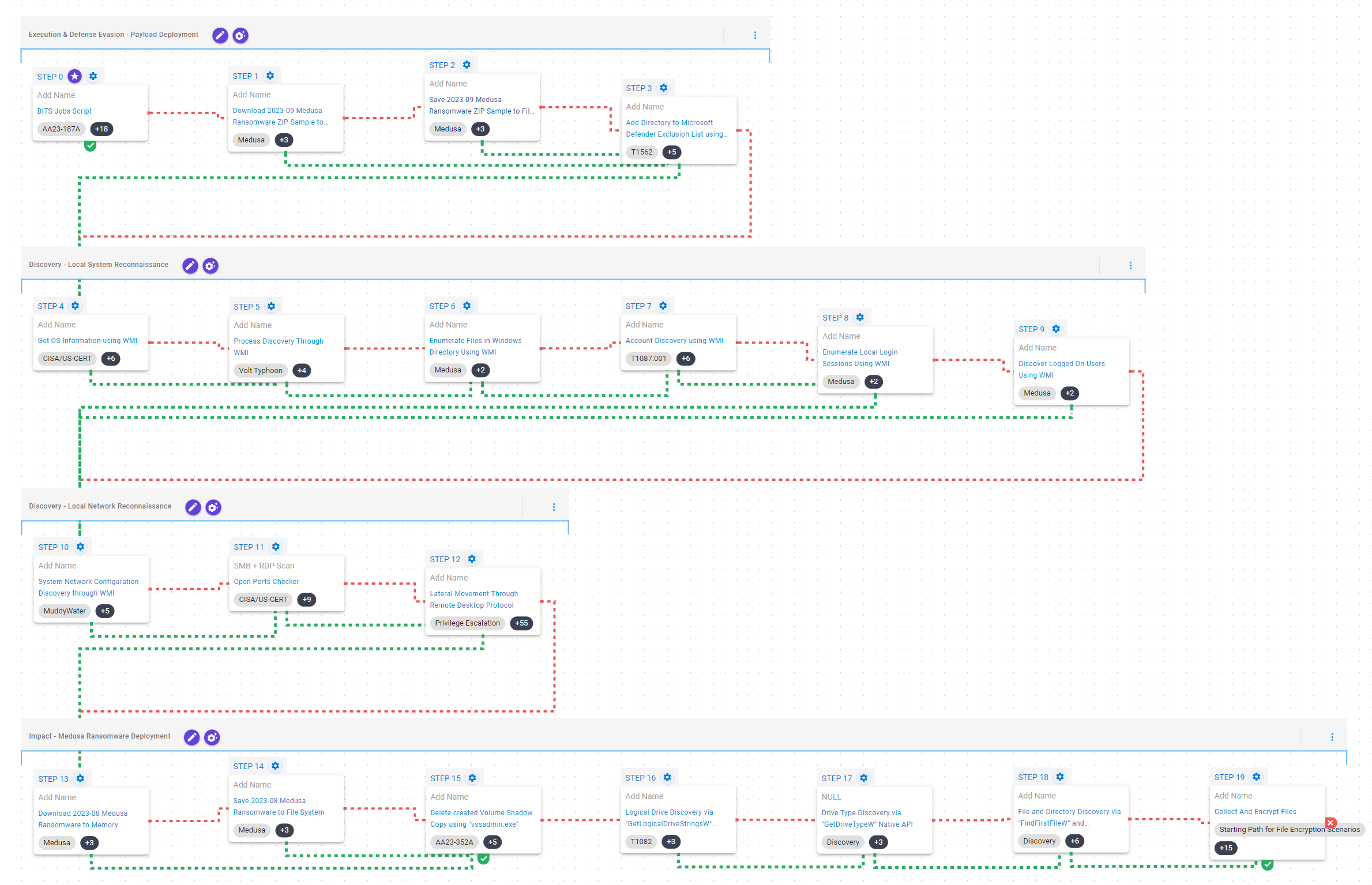
Execution & Defense Evasion – Payload Deployment
 Click for larger
Click for larger
This stage begins immediately after obtaining initial access which Medusa commonly achieves through the exploitation of vulnerable public-facing services. Once access is gained, Medusa operators typically employ an ASPX web shell to initialize a BITSAdmin job to download a remote ZIP file. This ZIP file contains a Remote Monitoring and Management (RMM) software used to achieve persistence.
Finally, Medusa’s operators will attempt to evade defenses by adding the working directory to Microsoft Defender’s exclusion list.
BITS Jobs (T1197): This scenario executes bitsadmin to create a BITS job and configure it to download a remote payload. Background Intelligent Transfer Service (BITS) is a native mechanism used by legitimate applications to use a system’s idle bandwidth to retrieve files without disrupting other applications.
Ingress Tool Transfer (T1105): These scenarios download to memory and save to disk in two separate scenarios to test network and endpoint controls and their ability to prevent the delivery of known malicious content.
Impair Defenses: Disable or Modify Tools ( T1562.001 ): This scenario uses the Add-MpPreference cmdlet to add the %TEMP%aiq-temp-exclusion directory path to the Windows Defender exclusion list.
Discovery – Local System Reconnaissance
 Click for larger
Click for larger
This stage focuses on the reconnaissance of the compromised system through the use of several Windows Management Instrumentation (WMI) commands. The purpose is to obtain information about the operating system, active processes, available files, user accounts, and their respective login information.
System Information Discovery (T1082): This scenario executes the Win32_OperatingSystem WMI command to collect OS information.
Process Discovery (T1057): This scenario executes the Process WMI command to discover running processes.
File and Directory Discovery (T1083): This scenario uses the CIM_DataFile WMI Class to enumerate files on the Windows directory.
Account Discovery: Local Account (T1087.001): This scenario executes the useraccount WMI command to get a list of local accounts.
Account Discovery (T1087): This scenario executes the Win32_LogonSession WMI command to list logon sessions.
Account Discovery (T1087): This scenario executes the Win32_LoggedOnUser WMI command to discover information related to a session and a user account.
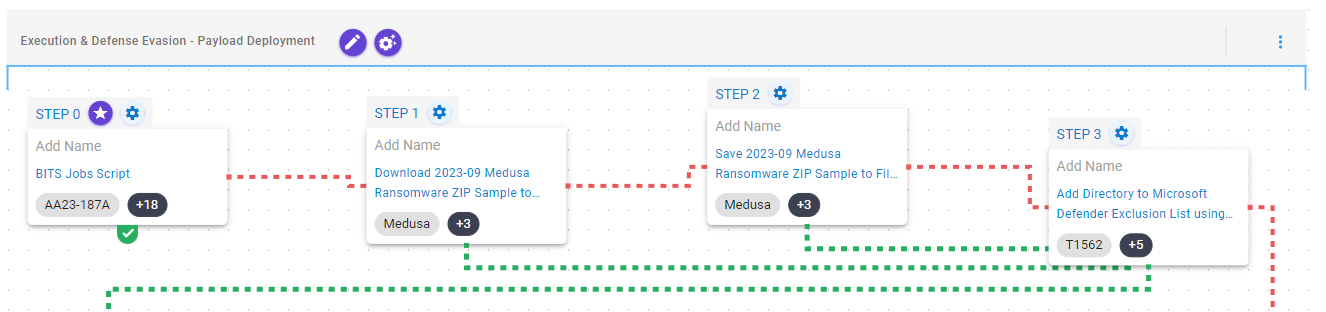
Discovery – Local Network Reconnaissance
 Click for larger
Click for larger
This stage focuses on reconnaissance of the local network to identify potential additional targets. For this purpose, the system’s network configuration is discovered using WMI, and ports associated with Server Message Block (SMB) and Remote Desktop Protocol (RDP) are scanned using the Nmap tool.
To conclude, an attempt will be made to move laterally to one of the identified systems through RDP.
System Network Configuration Discovery (T1016): This scenario executes a set of WMI commands to obtain information about the system network configuration.
Remote System Discovery (T1018): This scenario performs a scan of the local network using Nmap to discover any remotely accessible system with ports 139, 445, or 3389 open.
Remote Services: Remote Desktop Protocol (T1021.001): This scenario attempts to move laterally within a network using the Remote Desktop Protocol (RDP) protocol.
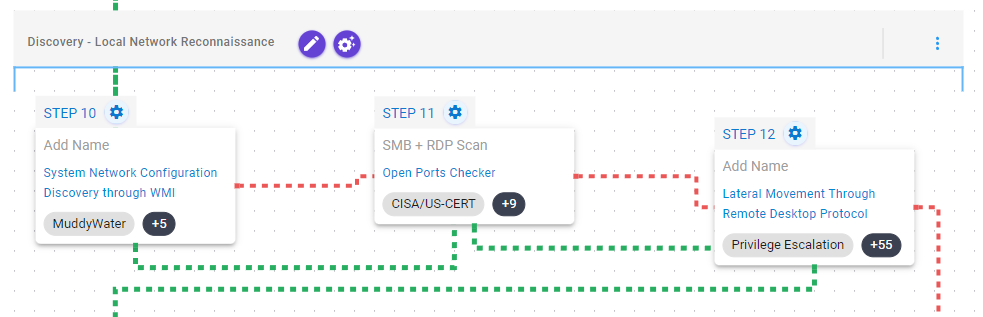
Impact – Medusa Ransomware Deployment
 Click for larger
Click for larger
This stage begins with the deployment of Medusa which, once operational, will immediately proceed to the removal of a Volume Shadow Copy using vssadmin.
Next, Medusa will retrieve information regarding the available disks and files on the system through several Windows API calls. Then it will proceed to encrypt the discovered files using an encryption scheme combining RSA 2048 + AES 256.
Inhibit System Recovery (T1490): This scenario executes the vssadmin.exe utility to delete a recent Volume Shadow Copy created by the assessment template.
System Information Discovery (T1082): This scenario executes the GetLogicalDriveStringsW API call to retrieve logical drives from the system.
System Information Discovery (T1082): This scenario executes the GetDriveTypeW API call to each drive letter to retrieve the type of all of them.
File and Directory Discovery (T1083): This scenario will call the FindFirstFileW and FindNextFileW Windows API to perform the enumeration of the file system.
Data Encrypted for Impact (T1486): This scenario performs the file encryption routines used by common ransomware families. Files matching an extension list are identified and encrypted in place using similar encryption algorithms.
Detection and Mitigation Opportunities
Given the number of different techniques being utilized by this threat, it can be difficult to know which to prioritize for prevention and detection opportunities. AttackIQ recommends first focusing on the following techniques emulated in our scenarios before moving on to the remaining techniques.
1. Ingress Tool Transfer (T1105):
This actor relies heavily in downloading additional stages of malware. Endpoint and Network security controls should both be employed to try and detect the delivery of these malicious payloads.
1a. Detection
The following signatures can help identify when native utilities are being used to download malicious payloads.
PowerShell Example:
Process Name == (Cmd.exe OR Powershell.exe)
Command Line CONTAINS ((“IWR” OR “Invoke-WebRequest") AND “DownloadData” AND “Hidden”)
1b. Mitigation
MITRE ATT&CK has the following mitigation recommendations.
2. Inhibit System Recovery (T1490):
Adversaries often delete Volume Shadow Copies to prevent the possibility of restoring files back to their original state. This is a common technique used by ransomware as it prevents the recovery of files once the ransomware encryption routine successfully completes execution.
2a. Detection
Detecting deletion of Volume Shadow Copies is usually the first step that occurs and can be detected by looking at the command line activity:
Via vssadmin.exe:
Process Name == (cmd.exe OR powershell.exe)
Command Line CONTAINS (“vssadmin” AND “Delete Shadows”)
Via PowerShell:
Process Name == powershell.exe
Command Line == “Get-WmiObject Win32_Shadowcopy | ForEach-Object ($_.Delete();)”
2b. Mitigation
MITRE ATT&CK has the following mitigation recommendations for Inhibit System Recovery
3. Data Encrypted for Impact (T1486):
Preventing systems and files from being encrypted should be a top priority. Ensuring that you have layered endpoint defenses including Antivirus and EDR solutions is critical.
3a. Detection
Ransomware attacks are best prevented and alerted by your EDR/AV Policies. Typically, a configuration for ransomware protection is presented and we strongly encourage that it is enabled in your security controls.
Detecting suspicious Data Exfiltration: Detecting exfiltration is well suited for IDS/IPS and DLP solutions. These products should be configured to identify sensitive files. If sensitive files, or a large amount of web traffic is sent to a rare external IP, it should be detected or prevented depending on security policies for the security control. Historical NetFlow data logging can also bubble up hosts that are experience uncommon peaks in outgoing traffic.
Detecting Ransomware-like File Encryption: Utilizing an EDR or SIEM/SOAR product can help detect and prevent suspicious file encryption related to ransomware attacks. Utilizing these tools to look for excessive file modifications (greater than 1000 on a system) within less than a minute of time is a good starting indicator.
To increase the fidelity a bit, you could include file modification of file extensions to popular ransomware extensions such as .conti, .Locky, .Ryuk, etc. If possible, with a SOAR or preventative EDR platform, we recommend setting these detections to kill all processes involved in creating the alert as it will most likely stop the spread of the Ransomware.
3b. Mitigation
MITRE ATT&CK Recommends the following mitigations:
Wrap-up
In summary, this attack graph will evaluate security and incident response processes and support the improvement of your security control posture against the activities carried out by Medusa ransomware operators. With data generated from continuous testing and use of this assessment template, you can focus your teams on achieving key security outcomes, adjust your security controls, and work to elevate your total security program effectiveness against a known and dangerous threat.
AttackIQ offers a comprehensive Breach and Attack Simulation Platform to assist security teams. This includes AttackIQ Flex, a tailored pay-as-you-go service; AttackIQ Ready!, a fully managed service for continuous security optimization; and AttackIQ Enterprise, a co-managed service offering enhanced support. These services ensure your team maintains a robust security posture.
The post Emulating the Petrifying Medusa Ransomware appeared first on AttackIQ.