Short Summary:
The article discusses the security risks associated with internationalized domain names (IDNs), particularly in the context of the Nitrogen malware campaign, where attackers used Punycode to create deceptive domains. The research team from WhoisXML API analyzed over 63,000 unique fully qualified domain names (FQDNs) containing native-language characters to uncover trends and potential threats in DNS security.
Key Points:
- Internationalized domain names (IDNs) allow organizations to use native-language domain names.
- Cyber attackers can exploit IDNs to create look-alike domains for spoofing legitimate sites.
- The Nitrogen malware campaign used Punycode to craft deceptive domains, such as wìnscp[.]net.
- The study analyzed 63,105 unique FQDNs from a database of over 58 billion rows.
- Findings include the most used top-level domains (TLDs), geolocation of IP addresses, and WHOIS registration data.
- Two internationalized TLDs were among the most common, potentially linked to impersonation campaigns.
- The top 10 TLDs accounted for 96.27% of the FQDNs analyzed.
- A white paper titled “Early Homograph Threat Detection: A DNS Study of IDNs and Native Language Characters” is available for further insights.
MITRE ATT&CK TTPs – created by AI
- Phishing (T1566)
- Threat actors may use deceptive domains to lure victims into downloading malicious software.
- Domain Spoofing (TLD-0001)
- Attackers create look-alike domains using Punycode to impersonate legitimate entities.
- Credential Dumping (T1003)
- Malicious domains may be used to harvest credentials from unsuspecting users.
While the usage of internationalized domain names (IDNs) has allowed organizations the world over to enter the global market using their native-language domain names, it can also enable cyber attackers to craft look-alikes of legitimate domains they wish to spoof.
Case in point? The Nitrogen malware campaign, where threat actors exploited Punycode to create deceptive domains. They used wìnscp[.]net (Punycode translation: xn—wnscp-tsa[.]net) to lure targets into downloading a fake WinSCP installer.
To further explore such DNS security risks, the WhoisXML API research team analyzed the top-level domain (TLD) distribution, IP resolution, and WHOIS registration data of 63,105 unique fully qualified domain names (FQDNs) containing native-language characters.
Download our white paper “Early Homograph Threat Detection: A DNS Study of IDNs and Native Language Characters” to explore our complete insights that leverage comprehensive passive DNS data from our Premium DNS Database.
Methodology
The data for our study came from the Premium DNS Database file dated 6 June 2024. We specifically extracted a sample comprising 63,105 unique FQDNs containing native-language characters from more than 58 billion rows of data.
Next, we analyzed the FQDNs’ IP resolutions by querying their corresponding IP addresses on Bulk IP Geolocation Lookup. This step allowed us to obtain pertinent information about their ISP administration and geographic locations.
After that, we used Bulk WHOIS Lookup to retrieve the root domains’ WHOIS information. We then analyzed the registrars, registrant countries, and redaction status of the top 100 root domains.
Preview of Study Findings
Our study of IDNs and native-language characters in FQDNs highlights:
- The most used TLDs in the FQDNs
- The geolocation countries of the top 100 IP addresses resolving the FQDNs
- The ISPs of the top 100 IP addresses
- The hosts of the top FQDNs with native-language characters
- The registrars of the top 100 root domains
- How many of the top 100 root domains had privacy-protected WHOIS information
- The existence of suspicious FQDNs and IDNs potentially impersonating legitimate entities
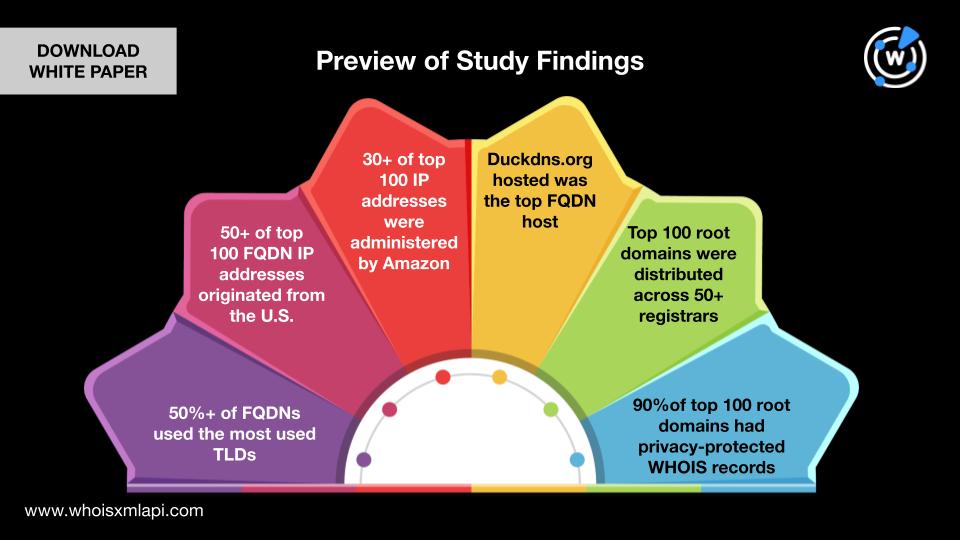
Take a look at an extract from our white paper showing the TLDs most commonly used in the FQDNs and suspicious.
Most Used TLDs in the FQDNs
Two internationalized TLDs were among the most commonly used based on the data in our passive DNS database. They were .xn—fiqs8s or .中国, which appeared in 16,647 FQDNs, and .xn—fiqz9s or .中國, which appeared in 16,638 FQDNs. Domains sporting these TLDs can potentially figure in campaigns impersonating financial organizations.
| SAMPLE MEMBERS | LIKELY IMITATED ENTITY |
|---|---|
| 1stcâpital[.]xn—fiqs8s 1stcâpital[.]xn—fiqz9s 1stcépital[.]xn—fiqz9s |
First Capital Bank |
| 1stcălgary[.]xn—fiqs8s 1stcălgăry[.]xn—fiqs8s 1stcălgăry[.]xn—fiqz9s |
First Calgary Financial |
The rest of the top 10 were regular TLDs comprising .com (9,747 FQDNs), .org (5,823 FQDNs), .cn (3,570 FQDNs), .net (3,431 FQDNs), .app (2,342 FQDNs), .in (1,251 FQDNs), .io (833 FQDNs), and .edu (471 FQDNs).
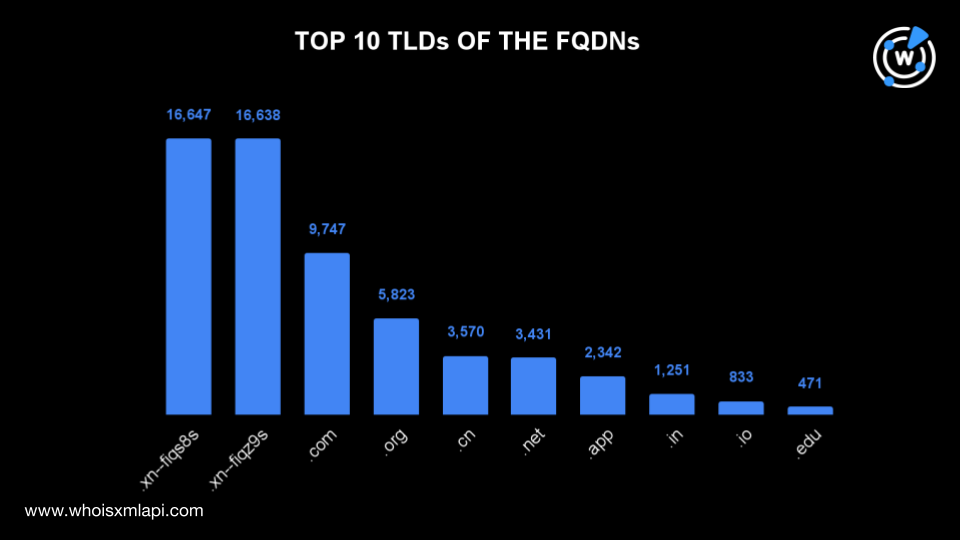
The top 10 TLDs accounted for 96.27% of the total number of FQDNs, while the remaining domains were distributed across 104 other TLDs.
Want to check out the remaining findings of our study? Download our complete white paper “Early Homograph Threat Detection: A DNS Study of IDNs and Native-Language Characters” now.
Source: Original Post