Summary: Ransomware gangs like BianLian and Rhysida are increasingly utilizing Microsoft’s Azure Storage Explorer and AzCopy to exfiltrate data from compromised networks and store it in Azure Blob storage. This trend highlights the growing focus on data theft as a key strategy in ransomware operations, leveraging Azure’s trusted infrastructure to evade detection.
Threat Actor: BianLian, Rhysida | BianLian, Rhysida
Victim: Various organizations | various organizations
Key Point :
- Ransomware actors are using Azure Storage Explorer and AzCopy for data exfiltration, taking advantage of Azure’s trusted status to bypass security measures.
- ModePUSH researchers observed that attackers had to overcome technical challenges to use these tools effectively, indicating a sophisticated approach to data theft.
- Monitoring for AzCopy execution and unusual outbound traffic to Azure endpoints can help in detecting ransomware exfiltration attempts.
- Organizations using Azure should implement security measures like automatic logout to prevent unauthorized access during active sessions.

Ransomware gangs like BianLian and Rhysida increasingly use Microsoft’s Azure Storage Explorer and AzCopy to steal data from breached networks and store it in Azure Blob storage.
Storage Explorer is a GUI management tool for Microsoft Azure, while AzCopy is a command-line tool that can facilitate large-scale data transfers to and from Azure storage.
In attacks observed by cybersecurity firm modePUSH, the stolen data is then stored in an Azure Blob container in the cloud, where it can later be transferred by the threat actors to their own storage.
Source: modePUSH
However, the researchers noted that the attackers had to put in extra work to get Azure Storage Explorer working, including installing dependencies and upgrading .NET to version 8.
This is indicative of the increasing focus on data theft in ransomware operations, which is the main leverage for threat actors in the ensuing extortion phase.
Why Azure?
Though each ransomware gang has its own set of exfiltration tools, ransomware gangs commonly use Rclone for syncing files with various cloud providers and MEGAsync for syncing with MEGA cloud.
Azure, being a trusted enterprise-grade service that is often used by companies, is unlikely to be blocked by corporate firewalls and security tools. Therefore, data transfer attempts through it are more likely to go through and pass undetected.
Additionally, Azure’s scalability and performance, allowing it to handle large volumes of unstructured data, is highly beneficial when attackers attempt to exfiltrate large numbers of files in the shortest possible time.
modePUSH says it observed ransomware actors using multiple instances of Azure Storage Explorer to upload files to a blob container, speeding up the process as much as possible.
Detecting ransomware exfiltration
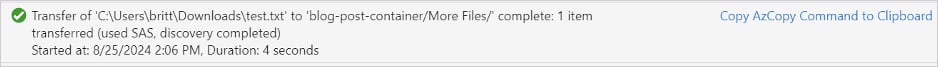
The researchers found that the threat actors enabled default ‘Info’ level logging when using Storage Explorer and AzCopy, which creates a log file at %USERPROFILE%.azcopy.
This log file is of particular value to incident responders, as it contains information on file operations, allowing investigators to quickly determine what data was stolen (UPLOADSUCCESSFUL) and what other payloads were potentially introduced (DOWNLOADSUCCESSFUL).
Source: modePUSH
Defense measures include monitoring for AzCopy execution, outbound network traffic to Azure Blob Storage endpoints at “.blob.core.windows.net” or Azure IP ranges, and setting alarms for unusual patterns in file copying or access on critical servers.
If Azure is already used in an organization, it is recommended to check the ‘Logout on Exit’ option to automatically sign out upon exiting the application, so as to prevent attackers from using the active session for file theft.