Short Summary
On September 17, 2024, CERT-AGID issued a warning about a malspam campaign using PEC mailboxes, initially linked to the Italian domain Excite, which did not support any malicious payload. The campaign has since evolved, now utilizing an active domain that releases a JavaScript file leading to the installation of the Vidar malware. This marks the fourth wave of Vidar-related incidents recorded by CERT-AGID in 2024.
Keypoints
- Warning issued by CERT-AGID regarding a malspam campaign.
- Initial link to the Italian domain Excite did not contain malicious payloads.
- Campaign evolved to use an active domain delivering Vidar malware.
- Fourth wave of Vidar incidents recorded in 2024.
- Malware authors target PEC mailboxes due to their legal value and perceived trustworthiness.
- Countermeasures have been implemented with the support of PEC providers.
- Users are advised to be cautious of suspicious PEC communications.
MITRE ATT&CK TTPs – created by AI
- Credential Dumping (T1003)
- Using compromised PEC accounts to access sensitive data.
- Phishing (T1566)
- Sending fraudulent communications through compromised PEC accounts.
- Malicious File (T1203)
- Delivery of JavaScript files leading to malware installation.
Full Article Translation
17/09/2024
Yesterday, CERT issued a notice regarding a malspam campaign conducted via PEC mailboxes, in which the link used to the Italian domain Excite did not support any malicious payload. Apparently, the authors of this campaign later made modifications, reintroducing the same content but using an active domain that releases a JavaScript file leading to the installation of the Vidar malware.
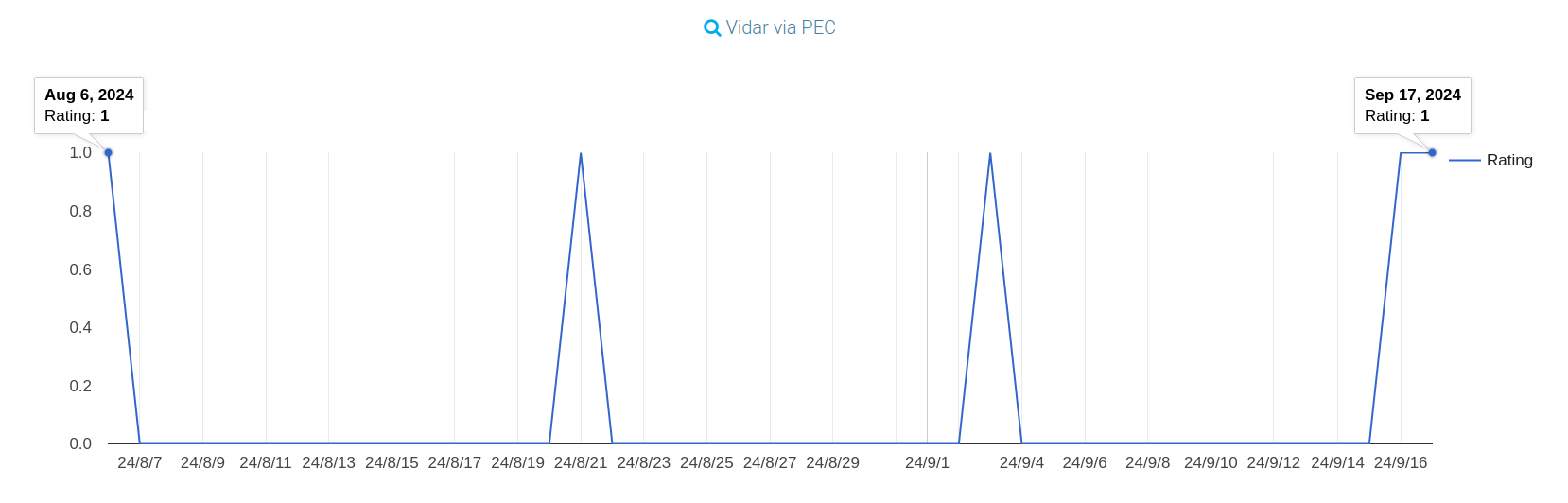
This is the fourth wave using Vidar (the fifth if we include the erroneous one from yesterday) that CERT-AGID has recorded in 2024, all concentrated from August to today.
Why do malware authors prefer to compromise PEC in Italy?
Malware authors (sLoad before and Vidar today) find compromising PEC mailboxes an attractive target due to their legal value and the trust they inspire. By compromising these accounts, they can generally access sensitive data and send fraudulent communications that appear authentic, thus increasing the chances of deception and malware dissemination. This false sense of security, along with the common belief that PEC is immune to compromises, makes Certified Electronic Mail a prime target for cyberattacks in Italy.
Countermeasures
Countermeasures have already been implemented with the support of PEC providers. The IoCs related to the campaign have been disseminated through the CERT-AgID IoC Feed to PEC providers and accredited structures.
Users are advised to pay close attention to communications received via PEC, especially when they contain links deemed suspicious. In case of doubt, emails considered suspicious can always be forwarded to the email address malware@cert-agid.gov.it.
Indicators of Compromise
To make public the details of today’s campaign, the following IoCs detected are reported:
Link: Download IoC
Source: Original Post