Short Summary
This weekend, a malicious campaign was identified and countered, utilizing compromised PEC accounts to target other users of the Certified Email service. The message, posing as a creditor, demands payment of 1305 euros and threatens legal action if not paid within five days. It includes a link to download an invoice, which may be a phishing attempt or malware.
Keypoints
- Malicious campaign using compromised PEC accounts.
- Message demands payment of 1305 euros under threat of legal action.
- Includes a suspicious link to download an invoice.
- Link points to an old domain, Excite.it, known from the 90s.
- No payload distributed, but requires basic authentication.
- Collaboration with PEC managers led to the campaign’s counteraction.
- Indicators of Compromise (IoC) shared with accredited public administrations.
- Users advised to verify payment requests for authenticity.
MITRE ATT&CK TTPs – created by AI
- Phishing – T1566
- Attempting to deceive users into providing sensitive information through fraudulent communications.
- Credential Dumping – T1003
- Exploitation of compromised accounts to gain unauthorized access to systems.
Full Article Translation
16/09/2024
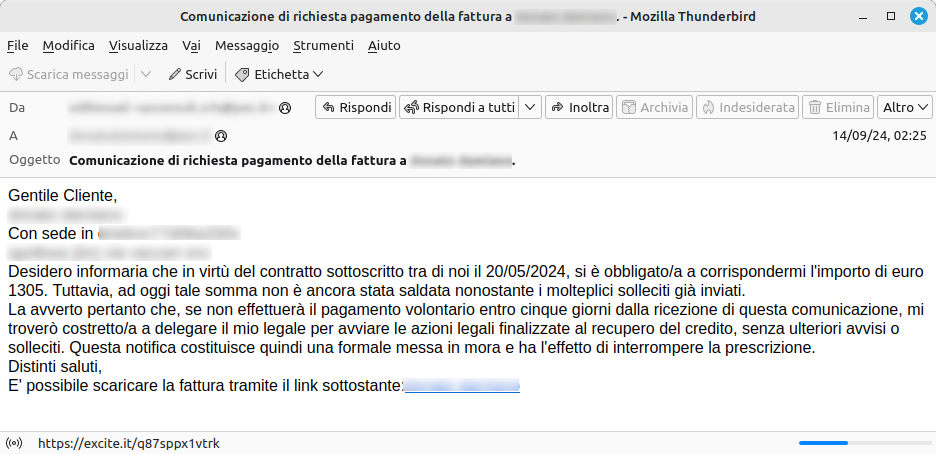
This weekend, a malicious campaign was identified and countered, utilizing some compromised PEC accounts to target other users of the Certified Email service.
The message, signed by an alleged creditor, demands payment of an amount of 1305 euros, threatening legal action if payment is not made within five days. The communication includes a link to download an invoice that could be a phishing attempt or malware, as observed in previous campaigns.
This time, the link points to a URL on the old domain Excite.it, a well-known Italian portal popular in the 90s (here is the info page on archive.org).
Fortunately, both the identified URLs and the main domain do not distribute any payload but require basic authentication.
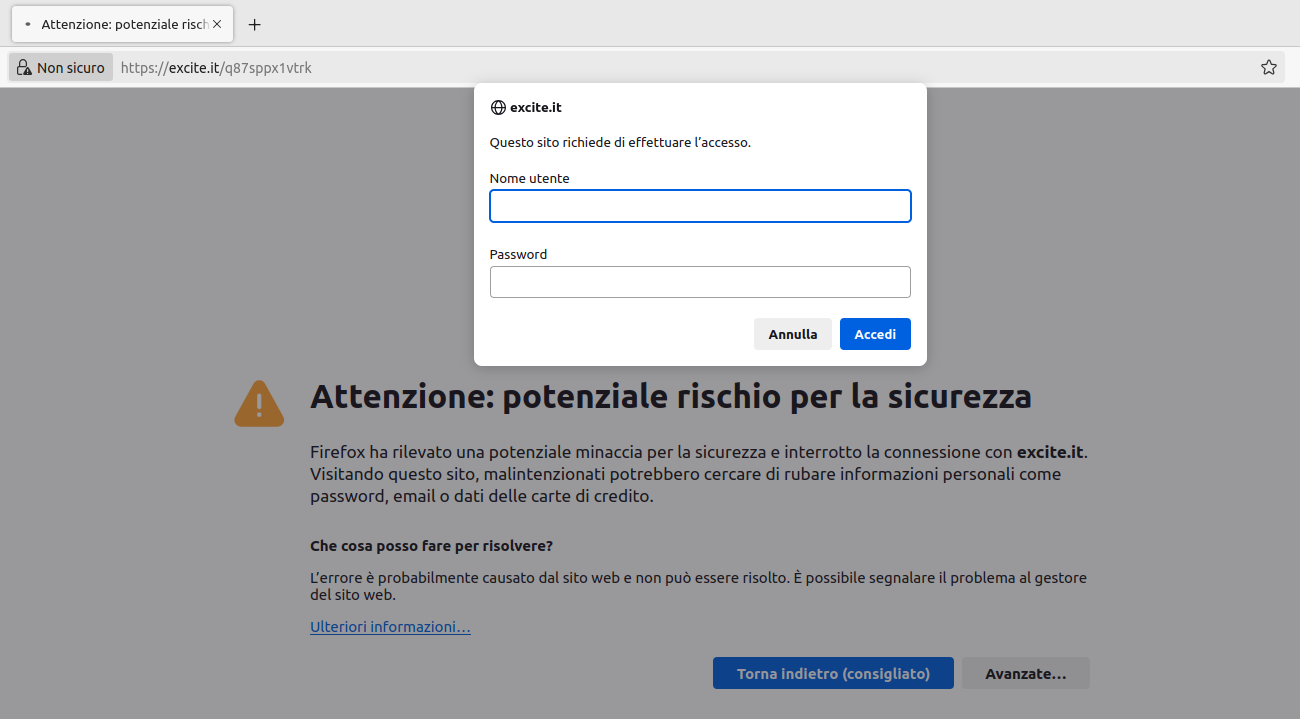
Thanks to the effective collaboration with PEC managers, the campaign was countered, and the Indicators of Compromise (IoC) were shared with public administrations accredited to the IoC flow, leading to the blocking of the main domain of Excite.
It is essential to remain vigilant against these scams and always verify the authenticity of payment requests, even when they come from a PEC mailbox. In case of doubt, the email malware@cert-agid.gov.it can be used to request any necessary checks.
Source: Original Post