Summary: Insikt Group has reported a resurgence of Predator spyware infrastructure, which was thought to be inactive due to sanctions and public exposure. The entity behind Predator, Intellexa, has reengineered its delivery system, enabling continued covert surveillance on high-profile targets worldwide.
Threat Actor: Intellexa | Intellexa
Victim: High-profile targets | high-profile targets
Key Point :
- Predator spyware has been reactivated with new infrastructure clusters, including a previously undocumented customer in the Democratic Republic of the Congo.
- The introduction of a multi-tiered delivery system enhances customer anonymity, complicating efforts to trace operations back to specific actors.
- Insikt Group identified four distinct Predator clusters across Angola, the Democratic Republic of the Congo, Madagascar/UAE, and Saudi Arabia.
- Predator is primarily used against high-value targets, employing sophisticated capabilities to access sensitive data and device functionalities.
- The spyware market continues to grow, highlighting the persistent demand for mercenary surveillance tools despite public scrutiny and sanctions.
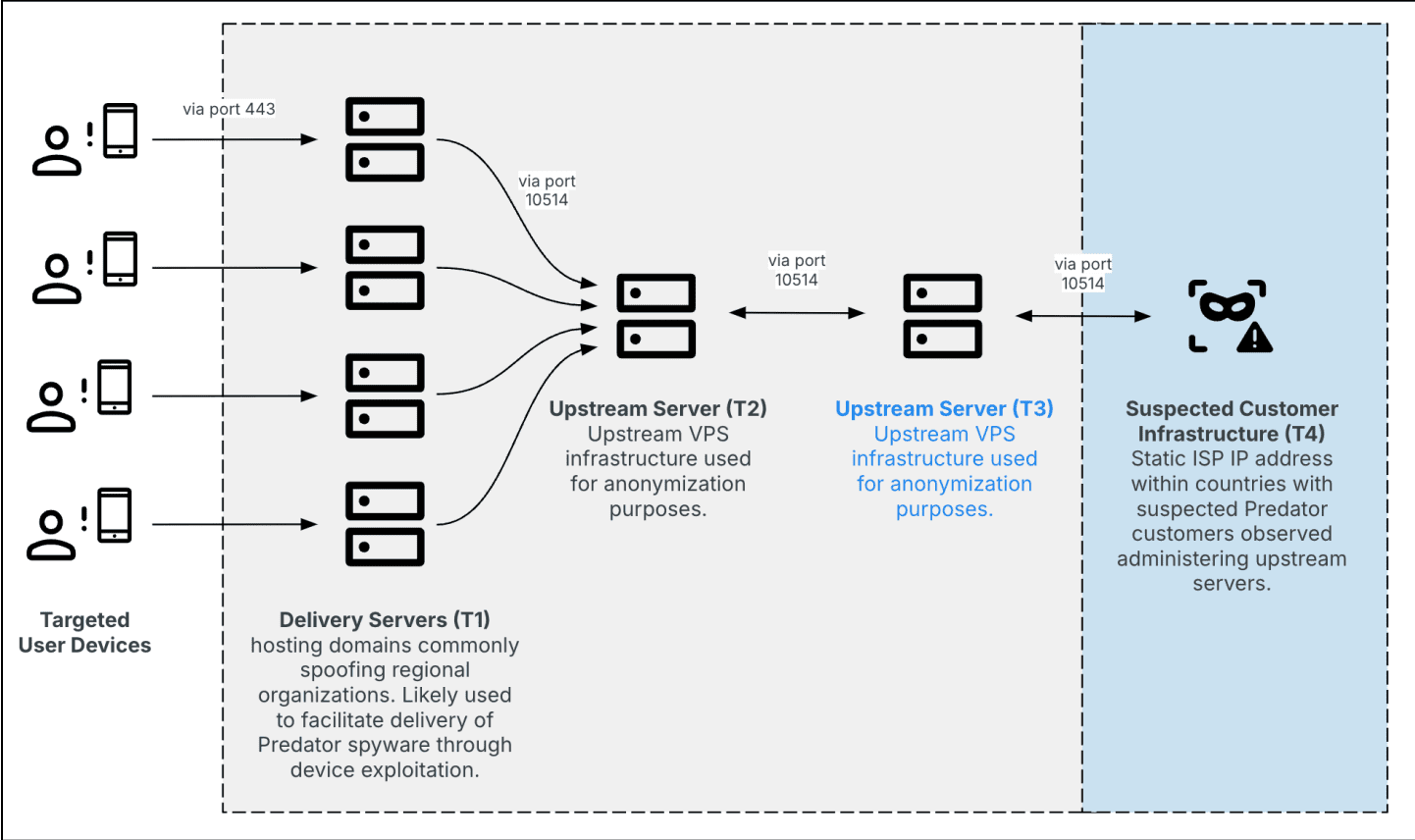
Recently, cybersecurity researchers from Insikt Group have identified a resurgence of Predator spyware infrastructure, previously believed to be largely inactive due to public exposure and U.S. government sanctions. Despite these setbacks, Intellexa, the entity behind Predator, has reengineered its spyware delivery system, allowing it to continue operating while evading detection.
Predator, a mercenary spyware developed by Cytrox, has been used for covert surveillance on high-profile targets worldwide since 2019. Following sanctions and public disclosures, Predator activity declined sharply in early 2024, but Insikt Group’s recent analysis reveals that the spyware is far from obsolete. The report, based on a combination of network artifacts and Recorded Future Network Intelligence, outlines the creation of new infrastructure clusters, including a previously undocumented customer from the Democratic Republic of the Congo.
One of the key updates in the Predator infrastructure is the introduction of an additional tier in its delivery system. This multi-tiered network aims to bolster customer anonymity, making it significantly more challenging to trace spyware operations back to specific actors or nation-states. Enhanced operational security, including revised server configurations and anonymization tactics, has made detection harder than ever.
Insikt Group identified four distinct Predator clusters across different countries:
- Angola – Likely linked to Portuguese-language domains previously associated with Predator.
- Democratic Republic of the Congo – A new cluster revealed, showing Predator’s presence in the politically unstable region.
- Madagascar/UAE – A potentially split cluster, demonstrating Predator’s reach across multiple geographies.
- Saudi Arabia – An inactive cluster, though historical ties to Predator’s earlier operations persist.
The Predator spyware is primarily used against high-value targets such as political figures, corporate executives, and activists. Its sophisticated capabilities, such as accessing a device’s microphone, camera, and sensitive data, make it a potent tool in intelligence gathering. The spyware likely persists in employing both “one-click” and “zero-click” attack methods, capitalizing on browser flaws and network access to infiltrate targeted devices. Although there’s no evidence of entirely remote zero-click attacks similar to those linked to Pegasus, Predator remains a potent weapon for those pursuing high-profile individuals.
With the spyware market continuing to grow despite public scrutiny and sanctions, Predator’s return underscores the persistent demand for mercenary surveillance tools. Insikt Group advises adopting comprehensive security measures, including regular device updates, mobile device management systems, and robust security awareness training. While these steps can reduce the risk, the evolving sophistication of spyware like Predator demands continuous vigilance from organizations and individuals alike.
Related Posts:
Source: https://securityonline.info/predator-spyware-roars-back-new-infrastructure-evasive-tactics