Short Summary:
Abyss Locker ransomware has emerged as a significant cybersecurity threat in 2023, targeting Windows and Linux systems across various industries. Known for its advanced encryption and multi-extortion tactics, it disrupts operations and demands hefty ransoms from businesses worldwide.
Key Points:
- Abyss Locker ransomware first appeared in 2023 and has rapidly gained notoriety.
- Targets multiple industries, including finance, manufacturing, healthcare, and technology.
- Utilizes advanced encryption techniques and multi-extortion tactics.
- Initially focused on Windows systems, but has expanded to Linux environments, particularly VMware ESXi.
- Employs sophisticated tactics such as lateral movement, service termination, and data exfiltration.
- Primarily targets the United States, with significant activity in Germany, the UK, and other countries.
- Defensive measures include advanced anti-malware, security audits, strong authentication, and continuous employee training.
MITRE ATT&CK TTPs – created by AI
- Phishing (T1566)
- Abyss Locker often gains initial access through phishing emails, tricking users into downloading malicious attachments or clicking on malicious links.
- Valid Accounts (T1078)
- The group may leverage stolen credentials to access targeted systems, especially through weak SSH configurations.
- Command and Scripting Interpreter (T1059)
- Uses various scripting languages and command-line interfaces to execute malicious code on the victim’s systems.
- System Services: Service Execution (T1569.002)
- Executes its payloads by abusing legitimate system services.
- Boot or Logon Autostart Execution (T1547)
- Establishes persistence by modifying system boot configurations, ensuring malicious processes start automatically upon reboot.
- Create or Modify System Process (T1543)
- May create or modify system processes to maintain persistence.
- Exploitation for Privilege Escalation (T1068)
- Exploits vulnerabilities or misconfigurations to gain elevated privileges on compromised systems.
- Obfuscated Files or Information (T1027)
- Uses obfuscation techniques to hide malicious code and avoid detection by security tools.
- Disable or Modify Tools (T1562.001)
- Disables or modifies security tools and services to evade detection and prevent recovery.
- Indicator Removal on Host (T1070)
- Deletes system logs, Volume Shadow Copies, and other traces to hinder forensic analysis and data recovery efforts.
- Brute Force (T1110)
- Attempts to gain access to accounts by performing brute-force attacks, especially on SSH accounts.
- Remote System Discovery (T1018)
- Scans the network to identify other systems for lateral movement and increased impact.
- System Information Discovery (T1082)
- Gathers information about the system’s configuration and network environment to tailor its attack.
- Remote Services: SMB/Windows Admin Shares (T1021.002)
- Uses compromised credentials to move laterally across the network via SMB or Windows Admin Shares.
- Data from Local System (T1005)
- Collects sensitive data from local systems before encrypting it for leverage in ransom demands.
- Exfiltration Over C2 Channel (T1041)
- Exfiltrates stolen data to command and control (C2) servers for use in extortion.
- Data Encrypted for Impact (T1486)
- Encrypts files on compromised systems, making them inaccessible without paying the ransom for the decryption key.
- Service Stop (T1489)
- Stops critical services and processes, such as databases and backups, to maximize damage and increase ransom payment likelihood.
In 2023, Abyss Locker ransomware emerged as a critical cybersecurity threat, aggressively targeting Windows and Linux systems across industries like finance, manufacturing, and technology. Known for its advanced encryption and multi-extortion tactics, Abyss Locker disrupts operations and demands hefty ransoms, making it a top concern for businesses worldwide.
Who is Abyss Ransomware?
Abyss Ransomware (also known as Abyss Locker) is a ransomware group that first appeared on the cybersecurity radar in 2023. Emerging as a potent threat, this group quickly gained notoriety for its aggressive targeting of various industries, including finance, manufacturing, healthcare, and information technology. Abyss Ransomware is believed to have roots in the infamous HelloKitty ransomware, leveraging its source code to develop its malicious operations.
Initially, the group focused on Windows systems, but it soon expanded its capabilities to include Linux environments, particularly VMware ESXi virtualized platforms. This expansion was marked by the introduction a specialized Linux encryptor designed to infiltrate and disrupt critical virtual environments. The group’s ability to adapt and evolve tactics has made it a significant player in ransomware.
Abyss Ransomware dark web platform
Abyss Ransomware operates as a multi-extortion ransomware group. It encrypts victims’ files and exfiltrates sensitive data, used as leverage in ransom negotiations. Victims who do not comply with the ransom demands face the threat of their data being exposed on a TOR-based website operated by the group.
The group’s operations are characterized by sophisticated tactics, including lateral movement within networks, termination of critical services and processes, and advanced encryption techniques. Abyss Ransomware has shown a particular focus on the United States, targeting sectors that include medical institutions, manufacturing companies, and tech firms. Their attacks have caused significant disruptions, often forcing organizations to negotiate and pay hefty ransoms to avoid further damage.
Despite its relatively recent emergence, the group has established itself as a formidable ransomware threat, demonstrating both technical prowess and a ruthless approach to extortion.

How Does Abyss Ransomware Operate?
According to the researchers, Abyss Ransomware employs various sophisticated Tactics, Techniques, and Procedures (TTPs) to maximize its impact on targeted systems. The group’s operations are notable for their technical complexity and strategic execution, particularly in Windows and Linux environments.
Notably, Abyss has seen two main versions (v1 and v2), with v2 introducing updates primarily in ransom note messaging and TOR addresses while maintaining the core functionality of v1. Here’s a breakdown of how Abyss Ransomware operates:
Initial Access Vectors
Abyss Ransomware typically gains initial access to its targets through phishing emails, exploiting weak SSH configurations, or leveraging known vulnerabilities in exposed servers. The group has been observed using brute-force attacks against SSH to establish a foothold, particularly in Linux environments. Once inside, Abyss rapidly deploys its payload to begin the encryption process.
Windows Version
According to the researchers, the Windows variant of Abyss Ransomware is highly destructive and strategically turns off critical services and processes before beginning encryption. Here’s a closer look at the process:
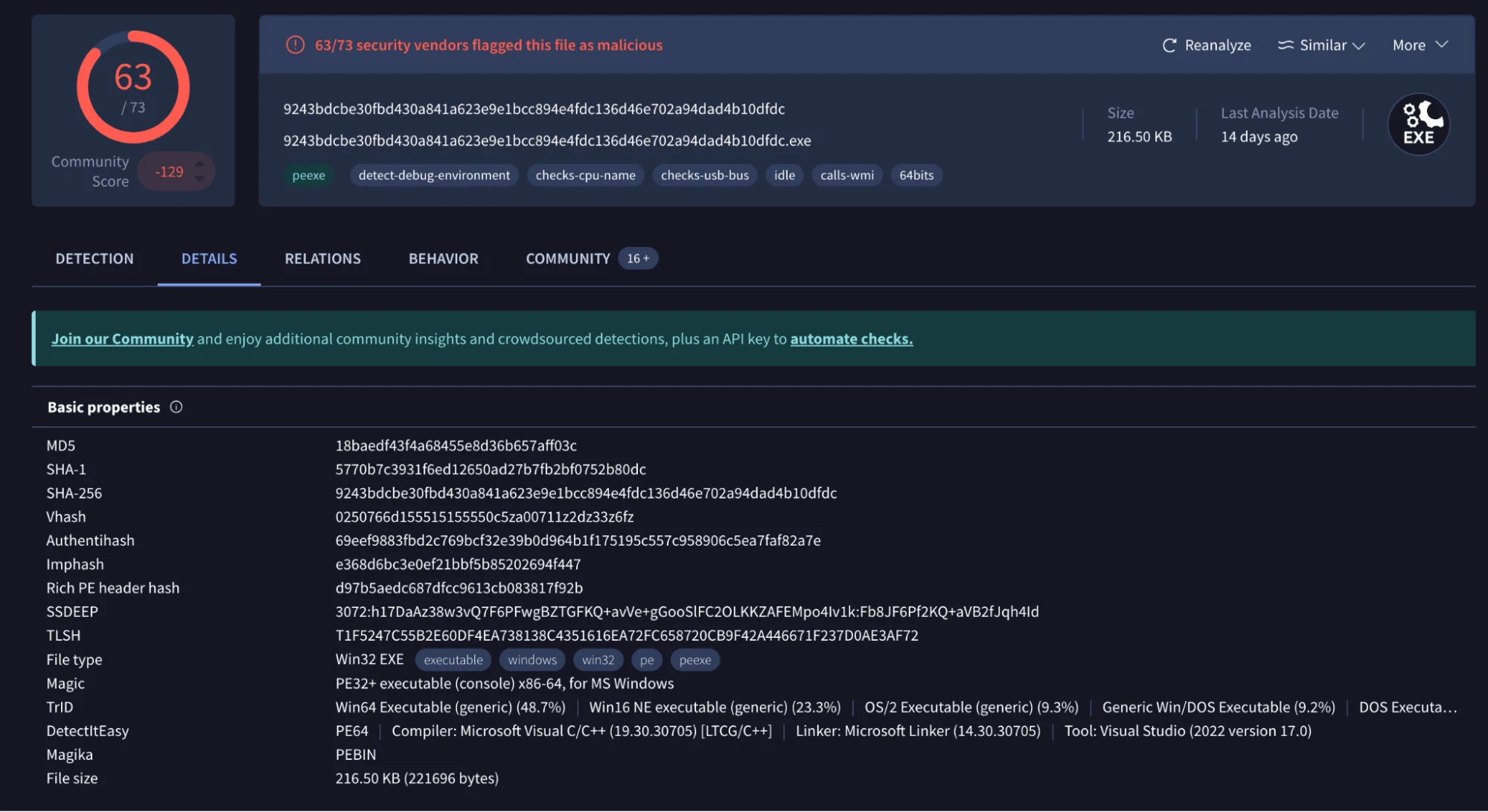
Basic properties of a known sample, written in C++ (VirusTotal)
- Service and Process Termination: Abyss Ransomware stops a wide range of services, including those related to databases (e.g., MSSQLServer), email systems (e.g., Microsoft Exchange), and backup solutions (e.g., Veeam, Acronis). By terminating these services, Abyss ensures that the system’s defenses are crippled, making the encryption process smoother and more effective.
- Volume Shadow Copy Deletion: To prevent the recovery of files from system backups, Abyss executes commands like vssadmin.exe delete shadows /all /quiet and wmic SHADOWCOPY DELETE. These commands erase volume shadow copies, making file restoration difficult without paying the ransom.
- Boot Configuration Changes: Abyss modifies the system’s boot configuration to turn off recovery options using commands such as bcdedit /set {default} recoveryenabled No and bcdedit /set {default} bootstatuspolicy IgnoreAllFailures. This ensures that the victim cannot quickly recover their system.
- File Encryption: Abyss encrypts files using the salsa_20 encryption algorithm, a method known for its efficiency and security. The ransomware appends a unique extension to the encrypted files, with v1 using a random five-letter extension and v2 using .abyss. This encryption method is implemented in the ransomware’s code, written in C++, a language known for its performance and control over system resources.
- Ransom Note: Abyss drops a ransom note named “WhatHappened.txt” in each affected directory after encryption. This note provides instructions for the victim on how to proceed with the ransom payment and includes a TOR link for communication with the attackers.
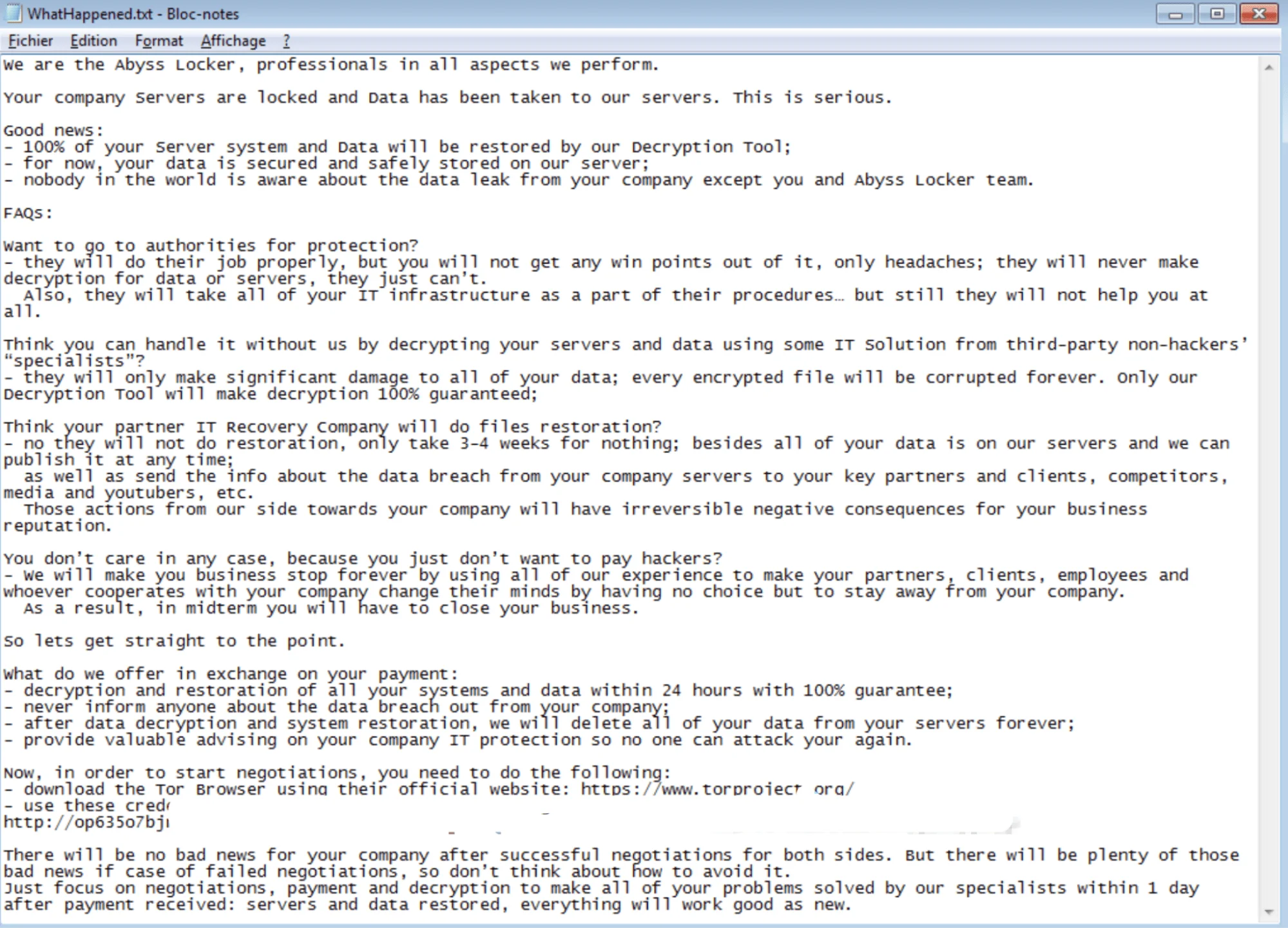
WhatHappened.txt (X)
- Desktop Wallpaper Replacement: To ensure the victim is aware of the attack, Abyss replaces the desktop wallpaper with a ransom message, further emphasizing the seriousness of the situation.

Abyss Ransomware replaces the victim’s desktop wallpaper with a ransom note (X)
Linux Version
The Linux variant of Abyss Ransomware is particularly dangerous for environments utilizing VMware ESXi virtualized infrastructure. Here’s how it operates:
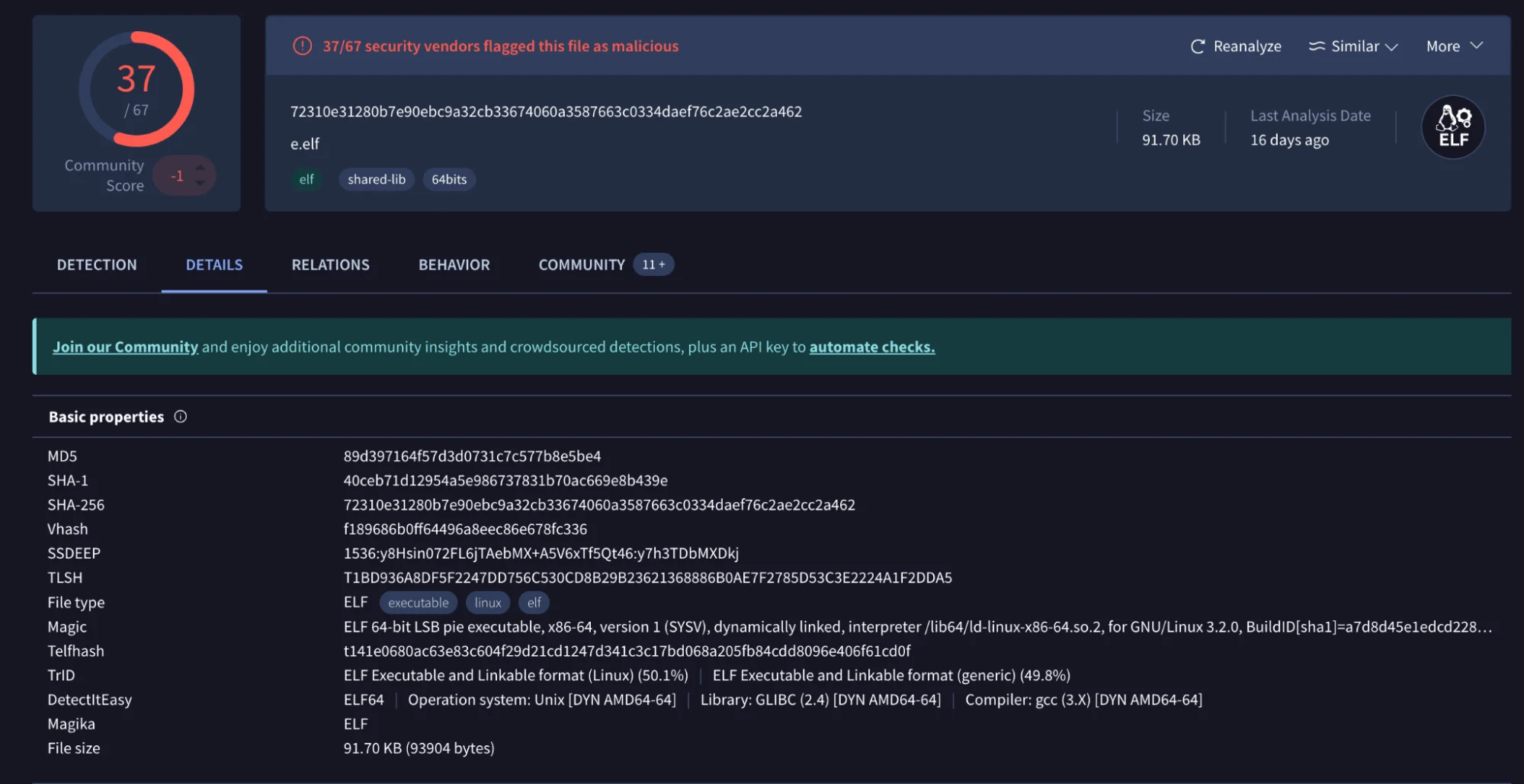
Basic properties of a known sample (VirusTotal)
- Targeting Virtual Machines: Abyss focuses on VMware ESXi environments, using the esxcli command-line tool to manage and manipulate Virtual Machines (VMs). The ransomware issues a command to list running VMs and forcefully shut them down if necessary, ensuring that the encryption process can proceed without interference.
- File Encryption: Similar to its Windows counterpart, the Linux variant encrypts files and appends the .crypt extension to them. The ransomware also drops a ransom note in each directory, named “README_TO_RESTORE,” which provides instructions for the victim.
- Exclusion of Critical Directories: To avoid destabilizing the system, Abyss excludes certain directories from encryption, such as /boot, /dev, and /usr/lib. This allows the system to remain operational to a degree, increasing the pressure on the victim to pay the ransom.
- Advanced Persistence Techniques: Abyss uses a combination of persistence mechanisms, including setting up daemon processes that ensure the ransomware remains active on the system, even after reboots or system changes.
Multi-Extortion Tactics
In addition to encryption, Abyss Ransomware engages in data exfiltration, stealing sensitive information before locking down the victim’s files. This data is used as additional leverage in ransom negotiations. If the victim fails to pay, the group threatens to release the data publicly on their TOR-based leak site, which could lead to significant reputational damage and legal consequences for the victim.
Abyss Ransomware’s operations demonstrate a high level of sophistication, with carefully designed strategies to ensure maximum disruption and leverage against its victims. Its ability to operate across multiple platforms and utilize advanced encryption and exfiltration techniques makes it a significant threat in the current cybersecurity landscape.
What Are the Targets of Abyss Ransomware?
Abyss ransomware has been highly active, targeting various industries and countries. Since its emergence, the group has launched numerous attacks, with a significant concentration in the United States.
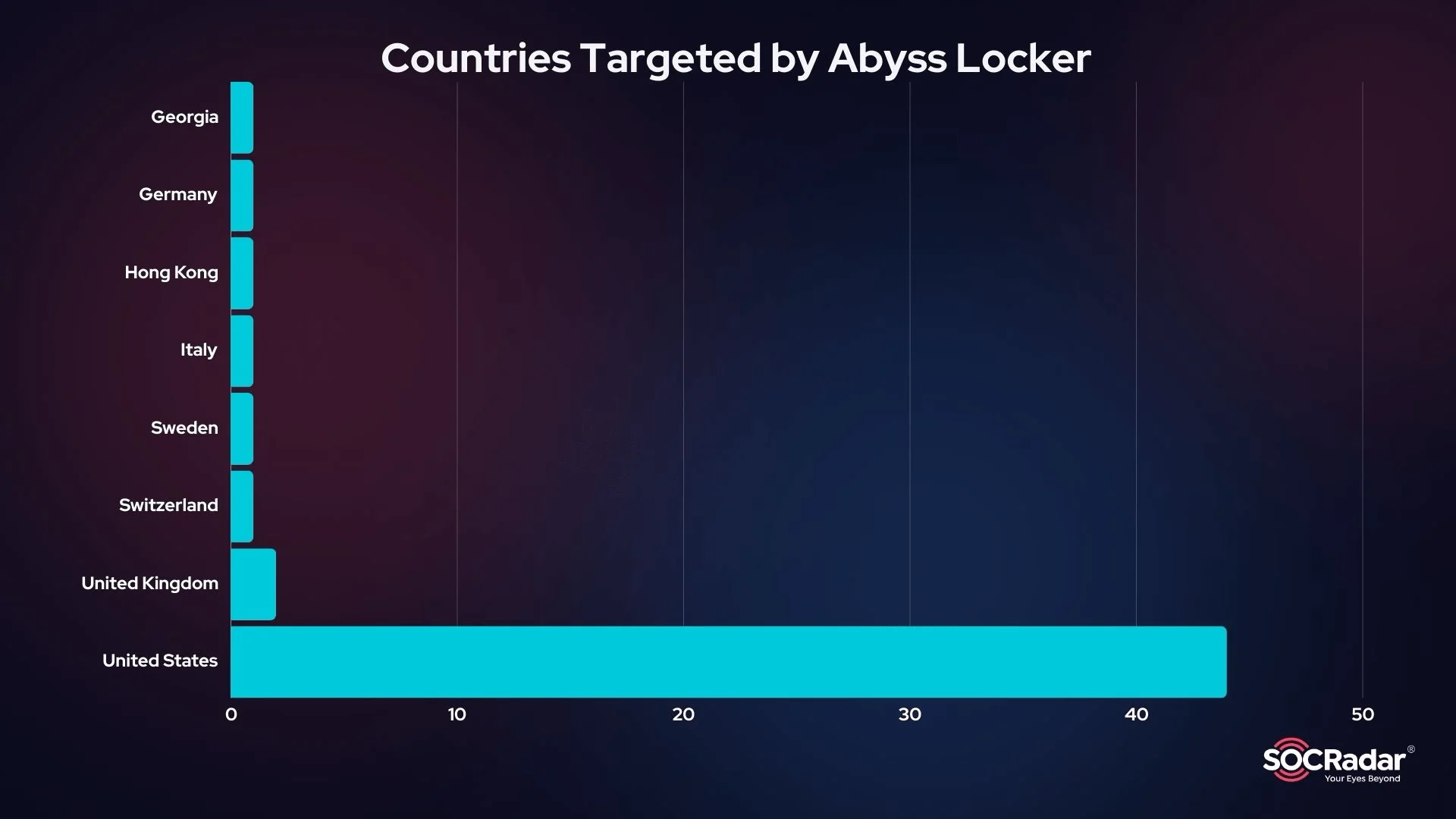
Targeted Countries So Far
The Abyss ransomware group has primarily focused on the United States, with 48 out of the total attacks occurring there. Other countries affected include Germany, the United Kingdom, Sweden, Switzerland, Canada, Georgia, Italy, and Hong Kong.
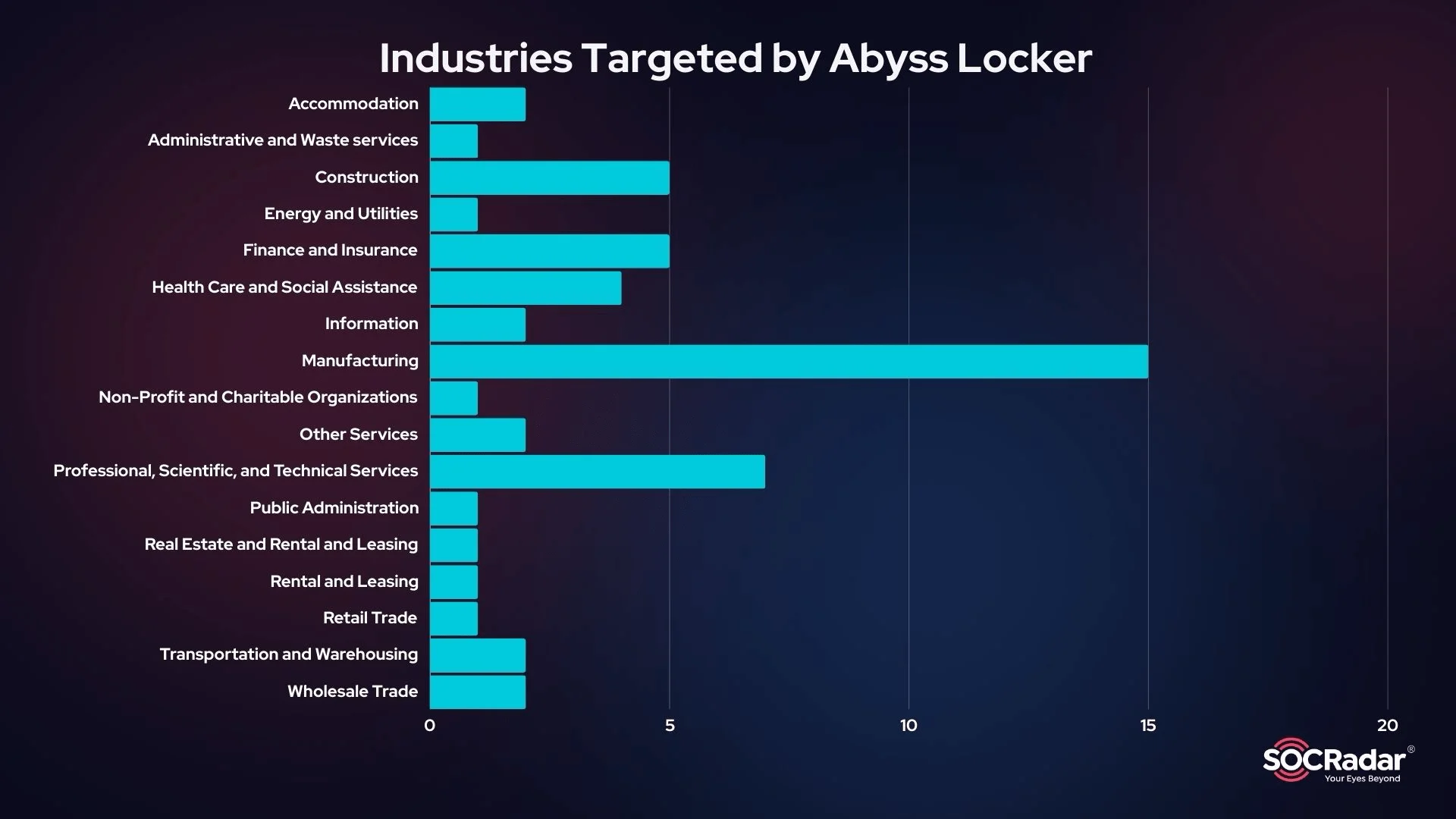
Targeted Industries So Far
Abyss has shown a particular interest in the Manufacturing sector, which has been hit the hardest. Other targeted industries include Finance and Insurance, Professional, Scientific, and Technical Services, Health Care and Social Assistance, and Construction.
Mitigation and Protection
Defending against Abyss Locker ransomware requires a multifaceted approach that incorporates advanced security tools and proactive strategies. Here are the key steps organizations should take:
- Advanced Anti-Malware Solutions
- Importance: Implementing advanced anti-malware software is crucial in combating Abyss Locker ransomware. These tools leverage signature-based detection, heuristic analysis, and machine learning algorithms to identify and block both known and emerging ransomware variants.
- Action: Deploy comprehensive anti-malware solutions, coupled with Endpoint Detection and Response (EDR) systems, to enhance real-time threat detection and response capabilities. These tools help prevent ransomware from infiltrating your systems and provide early warnings of potential threats.
- Security Audits and Vulnerability Management
- Importance: Regular security audits and vulnerability assessments are critical to identifying and addressing security gaps that Abyss Locker could exploit.
- Action: Conduct routine evaluations of your network configurations, system settings, and application vulnerabilities. This proactive approach helps you remediate weaknesses before attackers can exploit them. Implementing a continuous vulnerability management program ensures that your defenses are always up-to-date.
- Strong Authentication and Access Controls
- Importance: Enforcing strong authentication mechanisms and access controls significantly reduces the risk of unauthorized access, a common entry point for ransomware attacks.
- Action: Implement Multi-Factor Authentication (MFA) for all user accounts and ensure that access controls are strict and regularly reviewed. This adds an extra layer of security against credential-based attacks that Abyss Locker might use to gain entry into your network.
- Comprehensive Backup and Disaster Recovery Planning
- Importance: A robust Backup and Disaster Recovery (BDR) plan is essential for mitigating the impact of ransomware attacks and ensuring business continuity.
- Action: Establish a regular backup schedule for critical data, ensuring that backups are stored both onsite and offsite. Test your backups frequently to confirm that data can be restored quickly and effectively. This ensures that, in the event of an attack, you can recover your operations with minimal downtime and data loss.
- Dark Web Monitoring
- Importance: Monitoring the dark web for potential threats related to Abyss Locker can provide early warnings of planned attacks or data breaches.
- Action: Utilize advanced dark web monitoring tools, such as SOCRadar’s platform, to track unauthorized data transfers, detect exposures of Personally Identifiable Information (PII), and monitor dark web channels for any activity linked to Abyss Locker. This proactive monitoring can help you take preventive action before an attack materializes.
- Continuous Employee Training and Awareness
- Importance: Phishing emails are a common attack vector for ransomware. Educating employees about how to recognize and report suspicious activities can significantly reduce the risk of an initial compromise.
- Action: Regularly train your employees on cybersecurity best practices, including how to identify phishing attempts and avoid clicking on suspicious links or attachments. Implement simulated phishing exercises to reinforce this training and improve overall awareness.
- Incident Response Planning
- Importance: A well-defined incident response plan allows organizations to respond quickly and effectively to a ransomware attack.
- Action: Develop and maintain an incident response plan that outlines specific steps for dealing with ransomware incidents. This plan should include identifying the attack, containing its spread, eradicating the threat, and recovering from the incident. Regularly test the plan to ensure that it remains effective.
By following these mitigation and protection strategies, organizations can significantly reduce their vulnerability to Abyss Locker ransomware and similar threats. A proactive, layered approach to security will help maintain resilience against the constantly evolving landscape of cyber threats.

How Can SOCRadar Help?
SOCRadar provides comprehensive support to organizations facing the threat of ransomware like Abyss Locker, through a variety of advanced cybersecurity tools and services.
One of the key offerings is the Extended Threat Intelligence (XTI) platform, which delivers real-time threat detection capabilities. This platform monitors the evolving threat landscape continuously, enabling organizations to identify potential ransomware threats before they cause significant harm. By providing actionable insights into emerging threats, including specific Indicators of Compromise (IoCs) and Tactics, Techniques, and Procedures (TTPs) used by Abyss Ransomware, SOCRadar helps organizations stay one step ahead of attackers.
SOCRadar Attack Surface Management, Digital Footprint
Another crucial service is Attack Surface Management, which helps reduce vulnerabilities across your digital footprint. SOCRadar continuously scans for potential security gaps, providing organizations with a clear understanding of their exposure to external threats. By identifying and managing these vulnerabilities proactively, SOCRadar enables organizations to effectively minimize the risk of exploitation by ransomware like Abyss Locker.
SOCRadar Dark Web Monitoring
In addition to threat detection, SOCRadar’s Dark Web Monitoring service plays a crucial role in identifying potential risks early. Abyss Ransomware, like many other ransomware groups, may expose stolen data on dark web forums as part of their extortion strategy. SOCRadar’s monitoring service scans these hidden parts of the internet, detecting any mentions of your organization, leaked data, or indicators of an impending attack. By identifying these threats early, SOCRadar enables you to take preventive actions to protect your data and minimize potential damage.
Conclusion
Abyss Ransomware group has rapidly emerged as a formidable ransomware threat, targeting various industries with sophisticated tactics and advanced encryption techniques. Its ability to compromise both Windows and Linux environments, particularly within VMware ESXi virtualized platforms, underscores the need for organizations to adopt a robust and multifaceted cybersecurity strategy.
Proactive measures, such as regular system updates, strong authentication practices, comprehensive backup and disaster recovery planning, and continuous monitoring, are essential to mitigating the risks posed by Abyss Ransomware. Leveraging advanced tools like SOCRadar’s Extended Threat Intelligence, Attack Surface Management, and Dark Web Monitoring services further enhances an organization’s ability to detect, prevent, and respond to these threats effectively.
MITRE ATT&CK Tactics, Techniques, and Procedures (TTPs) for Abyss Ransomware
Abyss Locker ransomware employs a variety of tactics, techniques, and procedures (TTPs) that align with the MITRE ATT&CK framework. Understanding these TTPs is crucial for developing effective defense strategies against this threat. Below are the key TTPs associated with Abyss Locker:
| Tactic | Technique ID | Technique Name | Description |
| Initial Access | T1566 | Phishing | Abyss Locker often gains initial access through phishing emails, tricking users into downloading malicious attachments or clicking on malicious links. |
| Initial Access | T1078 | Valid Accounts | The group may leverage stolen credentials to access targeted systems, especially through weak SSH configurations. |
| Execution | T1059 | Command and Scripting Interpreter | Uses various scripting languages and command-line interfaces to execute malicious code on the victim’s systems. |
| Execution | T1569.002 | System Services: Service Execution | Executes its payloads by abusing legitimate system services. |
| Persistence | T1547 | Boot or Logon Autostart Execution | Establishes persistence by modifying system boot configurations, ensuring malicious processes start automatically upon reboot. |
| Persistence | T1543 | Create or Modify System Process | May create or modify system processes to maintain persistence. |
| Privilege Escalation | T1068 | Exploitation for Privilege Escalation | Exploits vulnerabilities or misconfigurations to gain elevated privileges on compromised systems. |
| Defense Evasion | T1027 | Obfuscated Files or Information | Uses obfuscation techniques to hide malicious code and avoid detection by security tools. |
| Defense Evasion | T1562.001 | Disable or Modify Tools | Disables or modifies security tools and services to evade detection and prevent recovery. |
| Defense Evasion | T1070 | Indicator Removal on Host | Deletes system logs, Volume Shadow Copies, and other traces to hinder forensic analysis and data recovery efforts. |
| Credential Access | T1110 | Brute Force | Attempts to gain access to accounts by performing brute-force attacks, especially on SSH accounts. |
| Discovery | T1018 | Remote System Discovery | Scans the network to identify other systems for lateral movement and increased impact. |
| Discovery | T1082 | System Information Discovery | Gathers information about the system’s configuration and network environment to tailor its attack. |
| Lateral Movement | T1021.002 | Remote Services: SMB/Windows Admin Shares | Uses compromised credentials to move laterally across the network via SMB or Windows Admin Shares. |
| Collection | T1005 | Data from Local System | Collects sensitive data from local systems before encrypting it for leverage in ransom demands. |
| Exfiltration | T1041 | Exfiltration Over C2 Channel | Exfiltrates stolen data to command and control (C2) servers for use in extortion. |
| Impact | T1486 | Data Encrypted for Impact | Encrypts files on compromised systems, making them inaccessible without paying the ransom for the decryption key. |
| Impact | T1489 | Service Stop | Stops critical services and processes, such as databases and backups, to maximize damage and increase ransom payment likelihood. |
IOC’s Related to Abyss Locker
Hash Values:
- 3B55904D3B37C810FC230B991A257939
- 2E4C626E67DF46B2A7258E73C04C4F73
- B1095D0837DD11B5280FCB29B5A1BB84
- 18BAEDF43F4A68455E8D36B657AFF03C
- D75E1C01C59B63D73F22E84A8A8819BF
- 6FF538DFD4B6A6FA796EA74EED50C80E
- E93EDA81803040E70D64168C8A83228F
- 2442FF56720D1887CB46DD37ED732407
- 4704CD96029606D6F501826D41805486
- 0B53120151A20A46EDF3EF85B8AC450F
- 72310e31280b7e90ebc9a32cb33674060a3587663c0334daef76c2ae2cc2a462
- 3fd080ef4cc5fbf8bf0e8736af00af973d5e41c105b4cd69522a0a3c34c96b6d
- 9243bdcbe30fbd430a841a623e9e1bcc894e4fdc136d46e702a94dad4b10dfdc
- 0763e887924f6c7afad58e7675ecfe34ab615f4bd8f569759b1c33f0b6d08c64
- dee2af08e1f5bb89e7bad79fae5c39c71ff089083d65da1c03c7a4c051fabae0
- e6537d30d66727c5a306dc291f02ceb9d2b48bffe89dd5eff7aa2d22e28b6d7c
- 1d04d9a8eeed0e1371afed06dcc7300c7b8ca341fe2d4d777191a26dabac3596
- 1a31b8e23ccc7933c442d88523210c89cebd2c199d9ebb88b3d16eacbefe4120
- 25ce2fec4cd164a93dee5d00ab547ebe47a4b713cced567ab9aca4a7080afcb7
- b524773160f3cb3bfb96e7704ef31a986a179395d40a578edce8257862cafe5f
- 362a16c5e86f13700bdf2d58f6c0ab26e289b6a5c10ad2769f3412ec0b2da711
- e5417c7a24aa6f952170e9dfcfdf044c2a7259a03a7683c3ddb72512ad0cd5c7
- 056220ff4204783d8cc8e596b3fc463a2e6b130db08ec923f17c9a78aa2032da
- 877c8a1c391e21727b2cdb2f87c7b0b37fb7be1d8dd2d941f5c20b30eb65ee97
- 2e42b9ded573e97c095e45dad0bdd2a2d6a0a99e4f7242695054217e2bba6829
File Indicators:
- .XPbS1
- 5620e71084c3bdc87a2522d4f5ad548a
- 837b3ddaaa7f209aac10480b43c248c20caaea2154ea13ef707e675a50bb2747
- temp%readme.bmp

Source: Original Post