Summary: Recent findings reveal a resurgence of malicious activities on the npm registry, linked to North Korean threat actors employing sophisticated tactics to compromise developers and steal sensitive data. A variety of malicious npm packages have been identified, showcasing a coordinated campaign aimed at exploiting vulnerabilities within the npm ecosystem.
Threat Actor: North Korean threat actors | North Korean threat actors
Victim: npm registry users | npm registry users
Key Point :
- Multiple malicious npm packages have been published, including temp-etherscan-api and telegram-con, which contain obfuscated JavaScript for malware downloads.
- The qq-console package is linked to a North Korean campaign, utilizing Python scripts to search for valuable data while remaining undetected.
- New packages like helmet-validate and sass-notification demonstrate the threat actors’ ability to adapt and refine their techniques, leveraging established infrastructure for persistent attacks.
- These attacks exploit the trust within the npm ecosystem, allowing adversaries to bypass traditional security measures and target sensitive data and cryptocurrency assets.
Recent findings by the Phylum Research Team have brought to light a resurgence of malicious activities on the npm registry, with multiple attack vectors originating from groups aligned with North Korean objectives. Since August 12, 2024, a diverse array of tactics, techniques, and procedures (TTPs) have been observed, indicating a coordinated and persistent campaign.
The campaign has seen the publication of several malicious npm packages, including temp-etherscan-api, ethersscan-api, and telegram-con. These packages, while appearing legitimate, contain obfuscated JavaScript that initiates multi-stage malware downloads from remote servers. The malware is particularly insidious, as it targets cryptocurrency wallet browser extensions, attempting to exfiltrate sensitive data and establish long-term persistence on the victim’s machine.
Notably, the qq-console package, published on August 27, has been linked to a North Korean campaign known as “Contagious Interview.” This package exemplifies the sophisticated tactics employed by these threat actors, including the use of Python scripts and a full Python interpreter to carry out their malicious activities. The malware systematically searches for valuable data, all while remaining hidden from the user.
The Phylum Research Team’s analysis has revealed that North Korean threat actors are not only refining their techniques but also diversifying their attack vectors. On August 23, just minutes after the latest versions of ethersscan-api and telegram-con were published, another package, helmet-validate, appeared on npm. This package took a different approach, injecting a simple yet powerful piece of code into a file called config.js. This code, when executed, contacts a remote endpoint at the ipcheck[.]cloud domain, which the researchers linked to a previous North Korean operation involving fake job campaigns.
The ipcheck[.]cloud domain resolves to the same IP address that was previously associated with mirotalk[.]net, a domain used in these fake job campaigns. This connection suggests that North Korean threat actors are leveraging established infrastructure and tactics to launch new waves of attacks, further complicating efforts to trace and neutralize their activities.
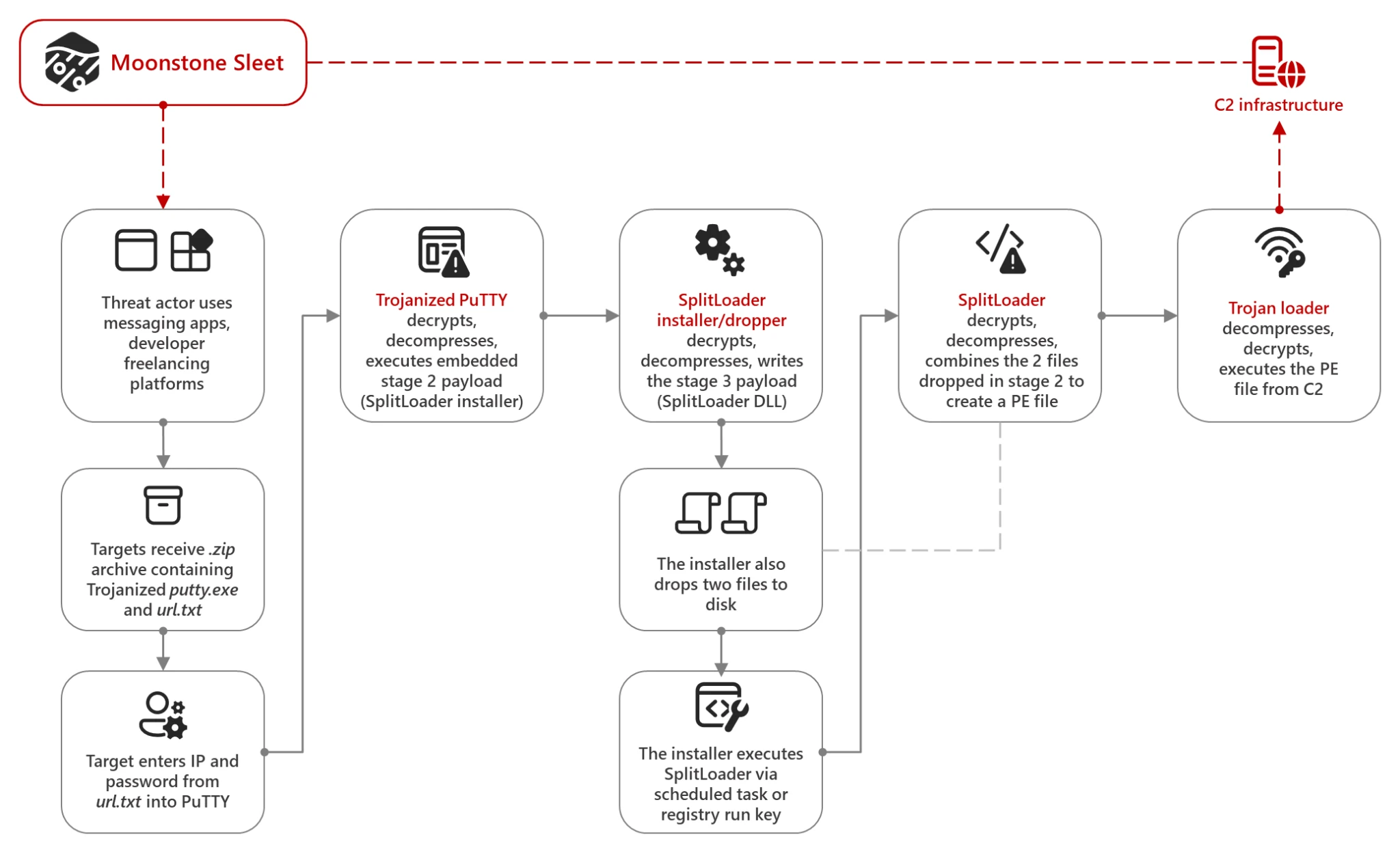
In another discovery, the researchers identified the publication of sass-notification on August 27. This package, attributed to the North Korean campaign known as “Moonstone Sleet,” employs a familiar yet effective attack vector. The package uses obfuscated JavaScript to execute batch and PowerShell scripts, which in turn download, decrypt, and execute a remote payload. The payload is executed as a DLL, and the scripts then clean up all traces of the attack, leaving behind a seemingly harmless package on the victim’s machine.
The persistence and sophistication of these attacks underscore the relentless efforts of North Korean threat actors to compromise developers and infiltrate companies. By exploiting the inherent trust within the npm ecosystem, these adversaries can bypass traditional security measures, gaining access to sensitive data, cryptocurrency, and other valuable assets.
Related Posts:
Source: https://securityonline.info/north-korean-cyberattacks-persist-developers-targeted-via-npm