“`html
Short Summary:
This article discusses a technique for dynamically analyzing Android malware using smali gadget injection, which allows for more flexible analysis compared to traditional methods. The process involves decompiling the APK, injecting a gadget into the smali file, and repackaging the APK for execution in a controlled environment.
Key Points:
- The dynamic analysis of Android malware is challenging due to limitations in existing tools like Frida.
- Smali gadget injection is introduced as a more flexible method for dynamic analysis.
- The process begins with decompiling the APK to identify the target methods for analysis.
- Tools like Apktool are used to extract and edit the smali files of the APK.
- Gadgets are injected into the smali files to log arguments and return values for debugging purposes.
- After injection, the smali files are assembled, signed, and repackaged into a new APK.
- The repackaged APK is executed in a virtual device environment for dynamic analysis.
- Logcat is used to view the output of decrypted strings during the analysis.
- This technique allows for various types of analysis, including variable manipulation and method invocation.
MITRE ATT&CK TTPs – created by AI
- Execution (T1203)
- Procedure: Exploiting vulnerabilities in applications to execute malicious code.
- Persistence (T1547)
- Procedure: Modifying application files to maintain persistence on the device.
- Privilege Escalation (T1068)
- Procedure: Gaining elevated permissions to access sensitive data or functionality.
- Defense Evasion (T1027)
- Procedure: Using obfuscation techniques to hide malicious activities from detection.
- Credential Access (T1003)
- Procedure: Extracting sensitive information such as passwords or tokens from the application.
“`
When dynamically analyzing Android malware, it is currently difficult to follow its code using debuggers unlike Windows malware. Although there is a technique [1] to hook a method dynamically by Frida [2], obtaining the in-progress state of the method is still difficult, and since Frida is not a tool dedicated to Android, only limited information can be obtained. In this article, I introduce smali gadget injection technique as a more flexible method for dynamic analysis of Android malware.
This method enables dynamic analysis by creating and injecting a gadget for analysis in the APK file to create a repackaged APK file.
Confirm the result of reverse compile
First, check the code of the Android malware to identify on which part of it you wish to perform dynamic analysis. Decompile results of APK files can be viewed as Java code by using a decompile tool such as JADX or JEB Pro. Figure 1 shows an example of the decompile result. In this technique, you need to know in advance the methods to decode and unpack from the decompile result. In the example in Figure 1, you can see that the malware receives an argument of String type in method a of class a in the package com.fky.lblabjglab. It then decrypts the string and returns a variable of String type. Note that although RC4 is used for encryption, it is not necessary to identify the encryption algorithm in this technique.
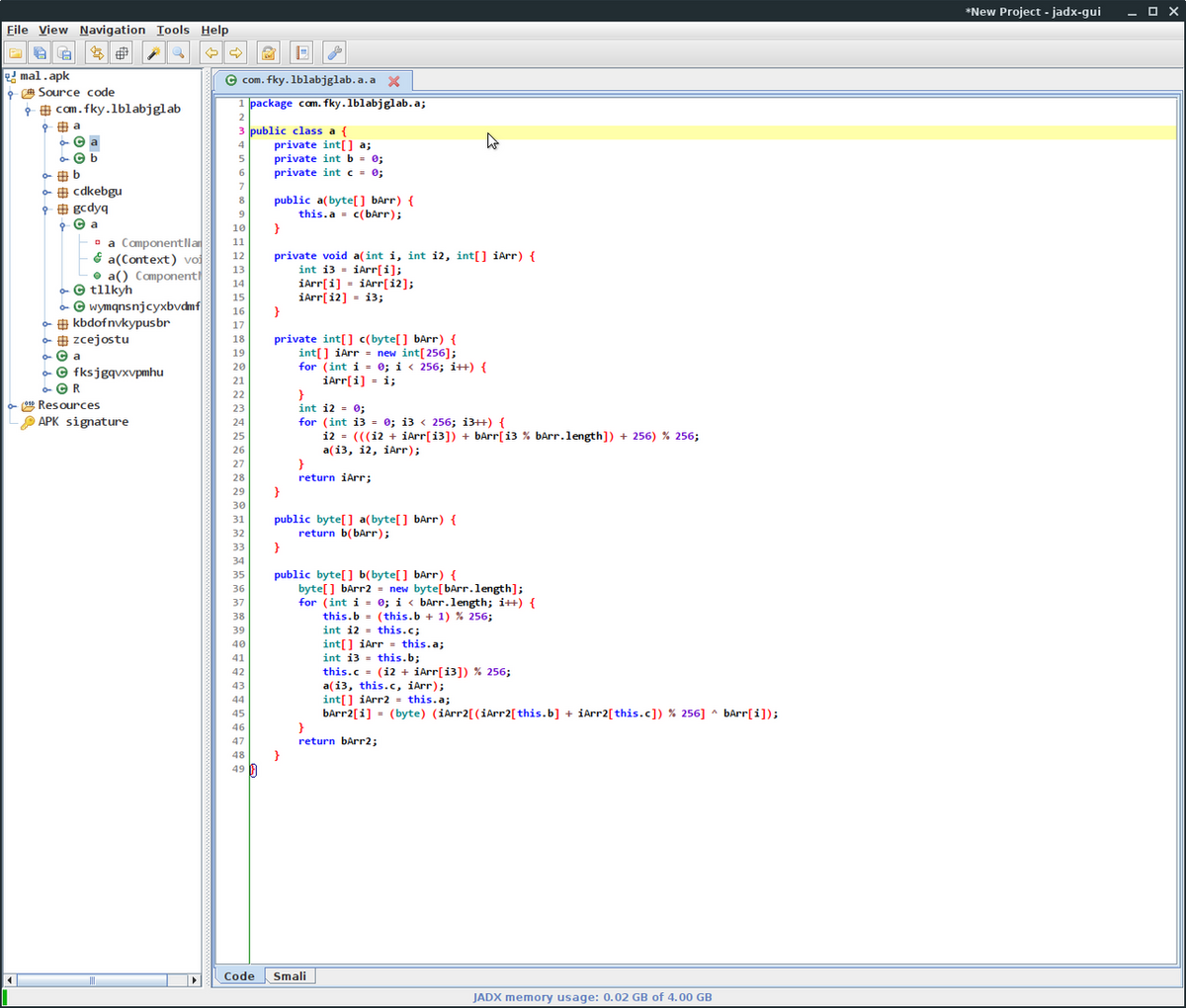
Figure 1: Decompile results of a method to decrypt RC4 strings using JADX
Extract smali file and inject gadget
Once you identify which part to analyze, extract the Android malware next. You can use Apktool [3] to extract APK files. By executing the following command, the specified APK file is extracted as shown in Figure 2, and the smali file to inject a gadget can be edited. The smali file can be found by referring to the decompile result obtained by JADX or other tools. In this example, let’s assume that the gadget will be injected in the smali file smali/com/fky/lblabjglab/a.smali, which is calling the RC4 decryption function.
$ apktool d mal.apk
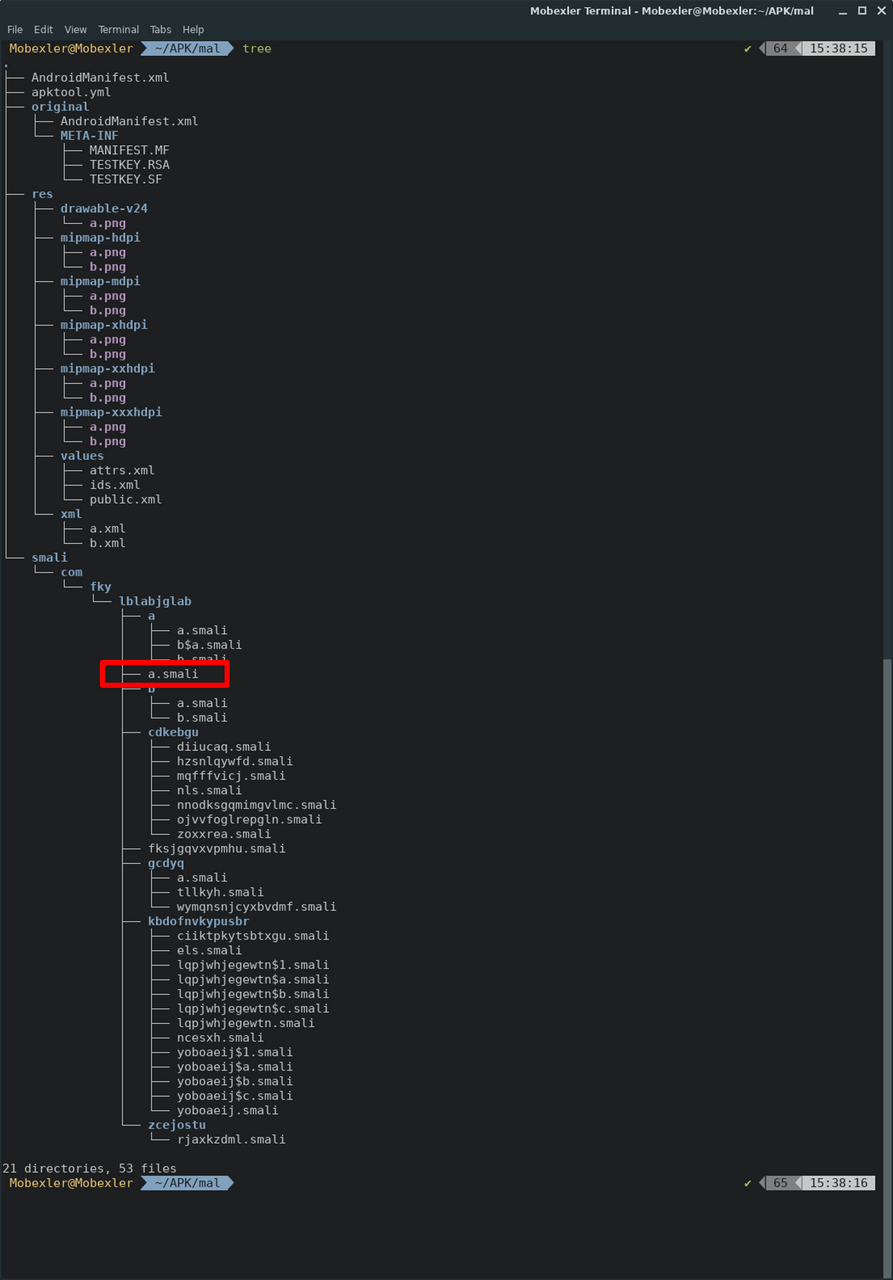
Figure 2: Directory structure of decompressed APK files
Here, as an example, the file smali/com/fky/lblabjglab/a.smali is opened in a text editor, and a gadget that outputs the argument and returns value to the debug log is injected as shown in Figure 3. You need to specify the variables to be displayed. In the method, p0 is this pointer, and p1 is the first argument. Therefore, if you wish to check the value of the first argument, p1 is specified, and the string log is output in android.util.Log.e.
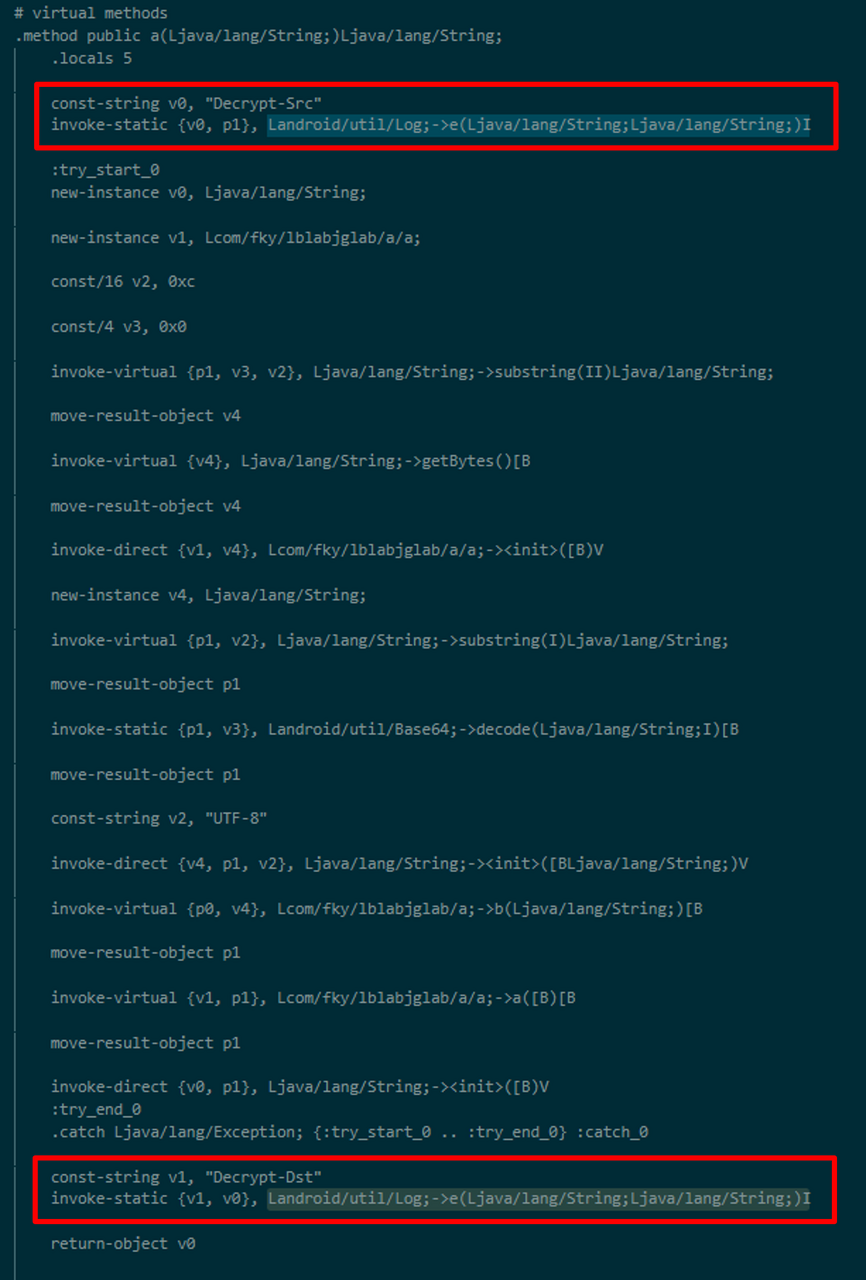

Figure 3: Example of injecting a gadget for analysis
Assemble and sign smali file
After injecting the gadget for analysis, assemble the smali file and create an APK file. After that, create a certificate file and sign the APK file. You can create an APK file with the gadget for analysis injected by executing the following commands.
$ apktool b mal $ keytool -genkey -v -keystore test.store -alias example -keyalg RSA -validity 32767 $ apksigner sign --ks test.store -v --v2-signing-enabled true --ks-key-alias example mal.apk
Execute the repackaged APK file
Finally, you can perform a dynamic analysis. Use Android Studio [4] or other applications to launch an Android virtual device as shown in Figure 4 and install the repackaged APK file on it. Note that the virtual device environment must be disconnected from the Internet prior to running the Android malware.
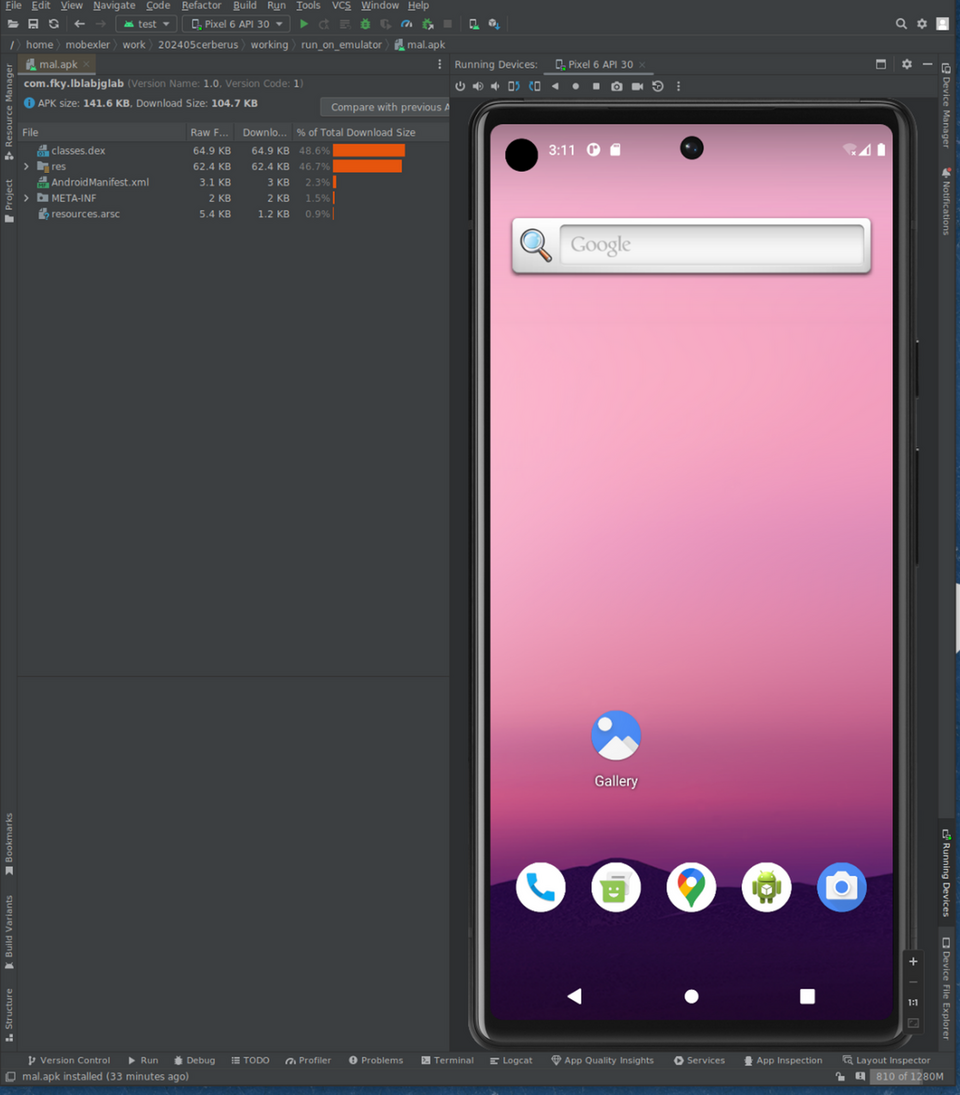
Figure 4: Installing the APK file on the Android Studio’s emulator
After installing the APK file, launch the application on the virtual device. Then, as shown in Figure 5, by referring to the Logcat tab and setting the appropriate filter, you can view the strings before and after decryption. This technique can be applied to perform various types of analysis, such as referencing or changing the contents of a variable or calling another method in the middle of a method.
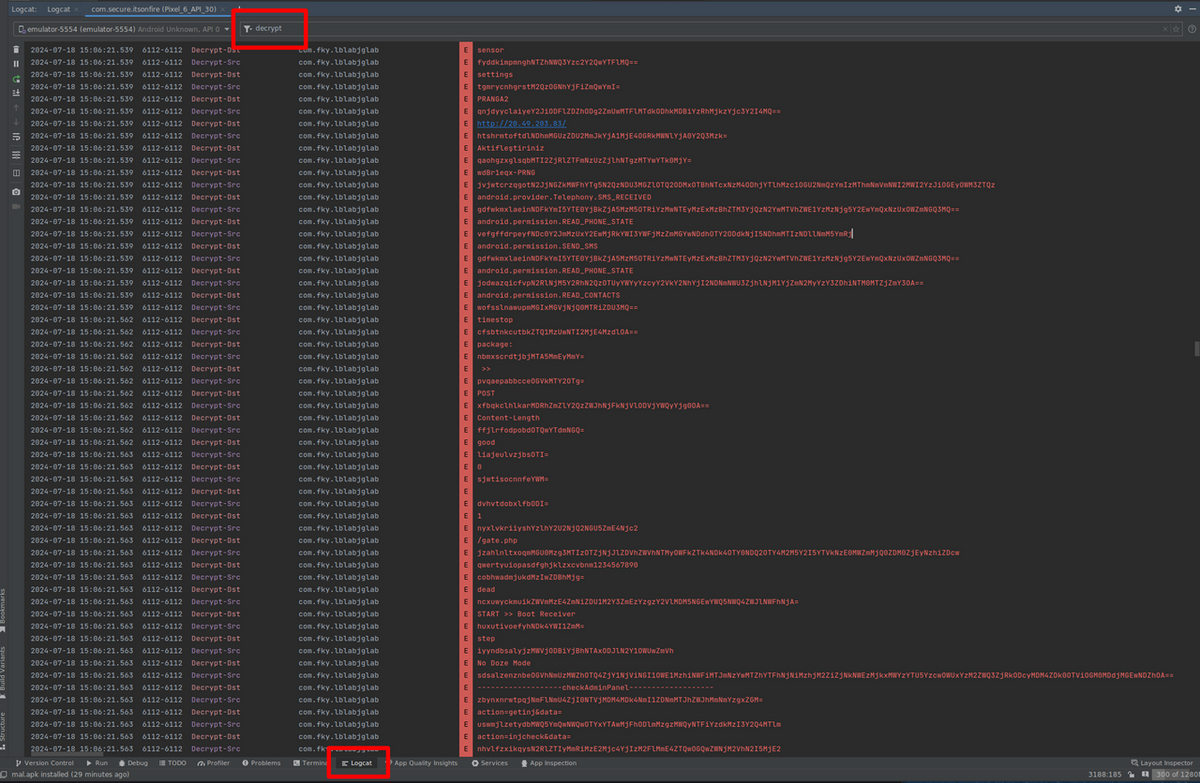
Figure 5: Result of decrypted strings output
In closing
This technique enables flexible dynamic analysis, which has been difficult to achieve with Android malware, although it requires some preparations in advance, such as checking decompile results and preparing a suitable smali gadget. The Android malware used for testing this technique is presented in the Appendix.
Yuma Masubuchi
(Translated by Takumi Nakano)
References
https://frida.re/
https://www.fortinet.com/blog/threat-research/defeating-an-android-packer-with-frida
https://apktool.org/
https://developer.android.com/studio
Appendix: Hash value of Android malware used
- Cerberus: 1249c4d3a4b499dc8a9a2b3591614966145daac808d440e5202335d9a4226ff8
Source: Original Post