“`html
Short Summary
Dark Angels, also referred to as Dunghill Leak, is a highly disruptive ransomware group known for its aggressive tactics and record-breaking ransom demands. Emerging around May 2022, they have targeted various industries, including healthcare and finance, and have gained notoriety for demanding up to $75 million in ransom. Their sophisticated operational methods and focus on high-profile targets make them a significant threat in the cybersecurity landscape.
Key Points
- Group Name: Dark Angels (Dunghill Leak)
- Emergence: Around May 2022
- Notable Attack: $75 million ransom demand from a major organization
- Targeted Industries: Healthcare, government, finance, education, technology, and telecommunications
- Attack Approach: Highly targeted attacks on single large companies
- Data Exfiltration: Stealing 1-100 TB of data from compromised organizations
- High-Profile Attack: September 2023 attack demanding $51 million and stealing over 27 TB of data
- Ransomware Variants: Initially used Babuk, later switched to RagnarLocker
- Protection Strategies: Anti-malware solutions, security audits, strong authentication, backup planning, and dark web monitoring
MITRE ATT&CK TTPs – created by AI
- Initial Access (T1078)
- Utilization of compromised credentials to gain access to target systems.
- Data Encrypted for Impact (T1486)
- Encrypting files on compromised systems to disrupt operations.
- Exfiltration Over Command and Control Channel (T1041)
- Transmitting stolen data back to the attacker via established command and control channels.
“`
Dark Angels or Dunghill Leak is a sophisticated and highly disruptive ransomware group that has recently gained notoriety. Known for their aggressive tactics and significant financial demands, Dark Angels has made headlines for their record-breaking ransom amounts.
Who is Dark Angels?
Dark Angels is a sophisticated and highly disruptive ransomware group that has recently gained notoriety after a published report and a staggering amount of ransomware fee. Known for their aggressive tactics and significant financial demands, Dark Angels has made headlines for their record-breaking ransom amounts. This profile delves into their operational methods, notable incidents, targeted industries, and the broader implications of their activities.

Dark Angels illustration, created with BING AI
In a recent and highly publicized attack, Dark Angels demanded a staggering $75 million ransom from their victim. This demand is one of the highest ever recorded in the history of ransomware attacks, highlighting the audacity and scale at which this group operates. The victim, a major organization with substantial financial resources, faced severe operational disruptions, underscoring the potential impact of such high-stakes ransomware attacks .
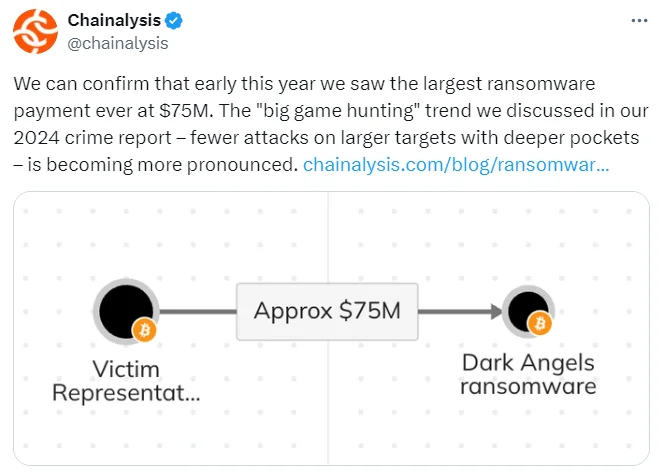
A crypto intelligence company, Chainalysis confirmed the transaction (X)
Modus Operandi
The tactics mentioned in the report are as follows:
Emergence and Operations
According to researchers, Dark Angels ransomware group, which operates the Dunghill data leak site, emerged around May 2022. Despite conducting some of the largest ransomware attacks to date, they have managed to attract minimal attention. Their most notable incident occurred in early 2024, when ThreatLabz uncovered a victim who paid Dark Angels $75 million—a record-breaking amount that has drawn the attention of other attackers seeking to replicate their success.
They are also operating a Telegram channel
Targeted Industries
Dark Angels targets a broad range of industries, including healthcare, government, finance, and education. More recently, they have expanded their focus to large industrial, technology, and telecommunication companies.

Attack Approach
Highly Targeted Attacks
Unlike most ransomware groups, which target victims indiscriminately and often rely on affiliate networks for initial access, Dark Angels employs a highly targeted approach. They typically attack a single large company at a time, focusing their efforts to maximize the impact and potential payout.
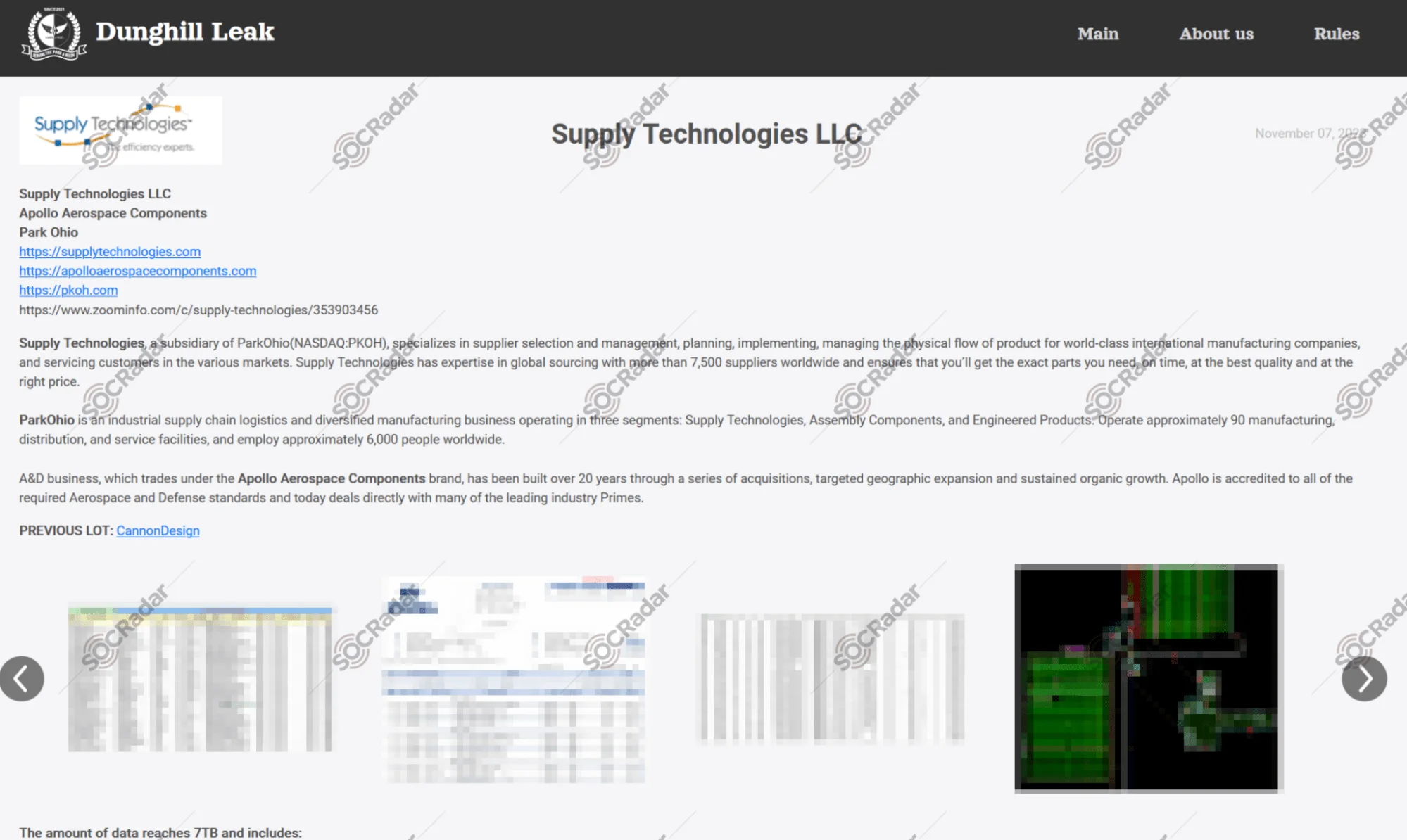
Dunghill Leak’s data leak site, a victim announcement
Initial Access and Compromise
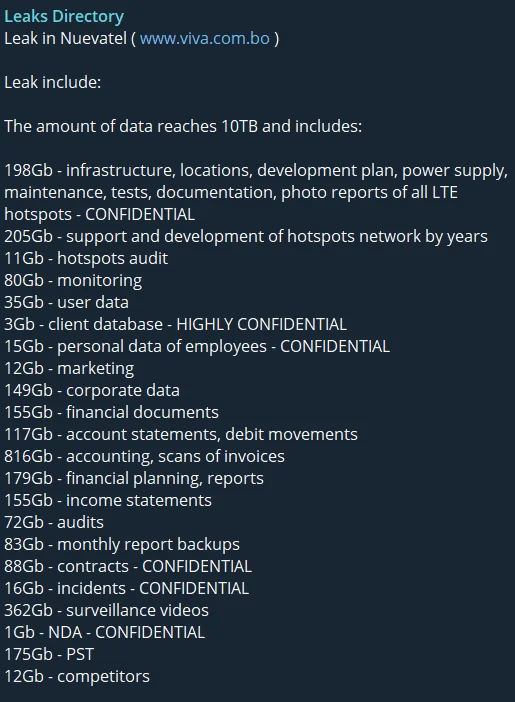
Once Dark Angels have identified and compromised a target, they selectively decide whether to encrypt the company’s files. They usually steal a vast amount of information, ranging from 1-10 TB for typical businesses to 10-100 TB for large enterprises. This exfiltration process can take days to weeks.
Notable Attacks
High-Profile Attack in September 2023
The highest-profile attack conducted by Dark Angels occurred in September 2023. The group breached an international conglomerate that provides solutions for building automation systems and other services. Dark Angels demanded a $51 million ransom, claimed to have stolen over 27 TB of corporate data, and encrypted the company’s VMware ESXi virtual machines. They used a RagnarLocker ransomware variant to encrypt the files, although the exact relationship between RagnarLocker and Dark Angels is unclear. Dark Angels had been using RagnarLocker prior to the law enforcement action against RagnarLocker, which resulted in the arrest of a key member in October 2023. Initially, Dark Angels deployed a Babuk variant before switching to RagnarLocker.
Conclusion
Therefore, Dark Angels represent a formidable threat in the realm of ransomware. Their ability to demand unprecedented ransom amounts and their sophisticated operational tactics make them a group to be reckoned with. As they continue to evolve and adapt, it is crucial for organizations to stay vigilant and proactive in their cybersecurity efforts to mitigate the risk posed by such advanced threats.
How to Protect Yourself Against Dark Angels Ransomware
As cyber threats continue to evolve, organizations must adopt a multifaceted approach to cybersecurity, especially in defending against ransomware attacks like Dark Angels. Leveraging advanced security tools and implementing proactive strategies are imperative in fortifying digital defenses.
Anti-Malware Solutions: Implementing advanced anti-malware software is essential in combating Dark Angels ransomware. These tools use signature-based detection, heuristic analysis, and machine learning algorithms to identify and block known and emerging ransomware variants. Coupled with Endpoint Detection and Response (EDR) solutions, organizations can enhance real-time threat detection and response capabilities.
Security Audits and Vulnerability Management: Conducting routine security audits and vulnerability assessments is critical to identifying and addressing potential security gaps within an organization’s infrastructure. By systematically evaluating network configurations, system settings, and application vulnerabilities, organizations can proactively remediate weaknesses exploited by Dark Angels ransomware attackers.
Authentication and Access Controls: Enforcing strong authentication mechanisms like Multi-Factor Authentication (MFA) and implementing stringent access controls significantly enhances user account security and mitigates the risk of unauthorized access. This adds an extra layer of protection against Dark Angels ransomware attacks targeting user credentials.
Comprehensive Backup and Disaster Recovery Planning: Developing a robust Backup and Disaster Recovery (BDR) plan is essential in mitigating the impact of Dark Angels ransomware attacks and ensuring business continuity. Regular backup schedules for critical data, both onsite and offsite, along with backup testing and data recovery drills, validate the effectiveness of the BDR plan and ensure timely restoration of operations in case of an attack.
Dark Web Monitoring: Utilize SOCRadar’s Advanced Dark Web Monitoring to track unauthorized data transfers, detect PII exposures, and monitor dark web channels for potential threats related to Dark Angels ransomware.
For further information about protection against ransomware, also check out our blog post titled “How to Detect & Prevent Ransomware Attacks (2024 CISO Edition).”
How Can SOCRadar Help?
Understanding the tactics and strategies of ransomware groups like Dark Angels is crucial for organizations looking to bolster their cybersecurity defenses. Implementing robust mitigation measures and staying vigilant are key steps in combating these threats effectively.
SOCRadar, Attack Surface Management has a Ransomware Check function
SOCRadar’s Attack Surface Management includes a specialized Ransomware Check function designed to help organizations protect against ransomware attacks, including those orchestrated by groups like Dark Angels. Our platform empowers you to proactively monitor potential attack vectors, detect suspicious activities, and take preemptive actions to safeguard your digital assets.
By leveraging SOCRadar’s intelligence-driven solutions, you can gain insights into threat actors’ methods and vulnerabilities, enabling you to fortify your cybersecurity posture. Our continuous monitoring and timely alerts ensure that you stay ahead of potential threats, allowing for swift responses and enhanced overall defense against ransomware and other cyber threats.
Integrating SOCRadar into your cybersecurity framework adds an additional layer of protection, helping you mitigate the risks posed by ransomware groups like Dark Angels and ensuring the resilience of your organization’s security defenses.

Source: Original Post