Executive Summary
On July 19th, 2024, Windows 7 and above systems running CrowdStrike’s Falcon sensor were served a faulty channel file that caused kernel instability and would result in a Blue Screen of Death (BSOD) loop and the largest global IT outage in history. The culprit is Channel File 291 (named with a pattern ‘C-00000291-*.sys’) contained a new detection logic to address malicious misuse of named pipes. The file was reportedly only served for a short window of one hour between 4 and 5 AM UTC. In that time, Microsoft estimates that 8.5 million Windows devices were affected worldwide. Given the nature of a BSOD loop, guidance for remediating affected devices requires booting into safe mode and deleting the faulty channel file or by using Microsoft’s remediation scripts. If the device is encrypted with Bitlocker, the key will be required before the file can be removed. Millions of enterprise systems crashing had cascading outages across multiple industries, including disruptions in manufacturing, air travel, and hospitals.
As affected parties continue the laborious remediation process, we want to proactively reassure our customers regarding the reliability, granularity, and phased approach taken by our Live Security Updates (LSU) mechanism. Update mechanisms and on-time patching are essential for continued and effective security, despite the particulars of this incident. Additionally, we have noted early signs of this global outage being exploited by threat actors, which should be closely monitored by those affected.
Why SentinelOne is Different? SentinelOne’s Update Mechanism
At SentinelOne, our Live Security Updates (LSU) are confined to detection-related logic and models that operate in an isolated user-mode space, separate from the core of our agent. These updates do not affect the kernel or core components of the SentinelOne agent. Since our agent primarily operates in user-space, our Live Security Updates only impact user-space components. This was an intentional design choice to increase stability and significantly decrease interoperability risks.
Core components of the SentinelOne agents are updated through our Upgrade Policy process or manually by our customers’ IT and Security departments, ensuring customers have full control over these updates. Furthermore, SentinelOne implements an extensive pre-General Availability (GA) process, offering customers Early-Access (EA) builds. This enables customers to test updates in their labs and on select machines, providing insight into how the upcoming GA release will perform in their environments.
Presently, hundreds of thousands agents participate in our EA program across our customer base, ensuring that GA releases have undergone rigorous testing by both SentinelOne Quality Assurance and on a substantial number of opt-in customer endpoints before being widely released. Customers also maintain complete control over when and where they deploy EA builds.
Finally, all of our Live Security Updates rollouts are a closely monitored, phased rollout across the fleet.
Early Cybercrime Attempts to Weaponize this Incident
As is often the case with major newsworthy incidents, cybercriminals immediately began to use CrowdStrike-themed components in their campaigns in an attempt to capitalize on the misfortune of system administrators and users desperate to get their systems operational. This includes registering potentially malicious domains and naming files after ‘CrowdStrike remediation’ themes. This activity remains low-grade and opportunistic. Recently registered potentially malicious infrastructure and additional Indicators of Compromise are provided in the Appendix.
Since the disclosure of the CrowdStrike issue, thousands (and growing) of typo-squatting domains have been registered to attempt to take advantage of victims.
These domains are being used by threat actors to lure in victims for a variety of extortion/scamming opportunities, including phishing and the distribution of malicious ‘fixes’ for the issue.
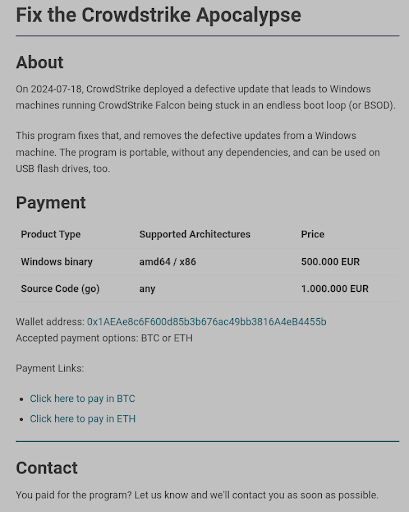
Threat actors have been using these domains, along with threatening emails, to attempt to extort BTC from potential victims. One of the more prominent examples, that has quickly arisen, is threat actors constructing these sites to directly request payment for their “fix” to the issue.
For example: The domain fix-crowdstrike-apocalypse[.]com attempts to scam victims into paying for either the stand-alone Windows binary, or the source code for the fix, for 500,000 and 1,000,000 EUR respectively (BTC: 0x1AEAe8c6F600d85b3b676ac49bb3816A4eB4455b.
Malicious actors are also attempting to distribute fake ‘hotfixes’ as described here and here. Examples:
crowdstrike-hotfix.zip fef212ec979f2fe2f48641160aadeb86b83f7b35
udpate.zip 66fbe2b33e545062a1399a4962b9af4fbbd4b356
crowdstrike-hotfix.zip fef212ec979f2fe2f48641160aadeb86b83f7b35
CrowdStrike Updater.exe 5b2f56953b3c925693386cae5974251479f03928
Conclusion
Incidents like the CrowdStrike outage showcase just how interconnected the different verticals of our society have become. Cybersecurity is an essential aspect of business continuity and needs to be carefully guarded as such. It’s of the utmost importance that system administrators continue to trust their software update mechanisms and patching in order to ensure continued and effective security. As affected verticals take on the laborious remediation process, SentinelOne continues to monitor cybercriminal threat actors attempting to take advantage of the ensuing chaos and concern.
Indicators of Compromise
fef212ec979f2fe2f48641160aadeb86b83f7b35
66fbe2b33e545062a1399a4962b9af4fbbd4b356
Ffef212ec979f2fe2f48641160aadeb86b83f7b35
5b2f56953b3c925693386cae5974251479f03928
cdfa4966d7a859b09a411f0d90efbf822b2d6671link.storjshare[.]io/s/jvktcsf5ypoak5aucs6fn6noqgga/crowdstrikesupport/update.zip
Below are recently registered domains using the CrowdStrike BSOD theme. They’re considered suspicious until confirmed weaponized.
- crashstrike[.]com
- crowdstrikefix[.]com
- crowdstrikebluescreen[.]com
- crowdstrike-helpdesk[.]com
- crowdfalcon-immed-update[.]com
- crowdstrike-bsod[.]com
- crowdstrikebsod[.]com
- crowdstrikedown[.]sitecrowdstrike-helpdesk[.]comcrowdstrike[.]buzz
- crowdstrike0day[.]com
- crowdstrikedoomsday[.]com
- crowdstriketoken[.]com
- crowdstrikeoutage[.]info
- crowdstrikecommuication[.]app
- fix-crowdstrike-bsod[.]com
- fix-crowdstrike-apocalypse[.]com
- crowdstrike[.]fail
- crowdstrike-solutions[.]nl
- crowdstrike[.]cam
- crowdstrike-fix[.]com
- crowdstroke[.]io
- crowstrike[.]org
- croudstrike[.]org
- crowdstroke[.]zip
- crowstrike[.]net
- crowdstrife[.]com
- pay.crowdstrife[.]com
- crowdstroke.pages[.]dev
- cloudstrike[.]website
- clownstrike[.]gg
- crudstrike[.]com
- clownstrike.co[.]uk
- britishairways.crowdstrike[.]feedback
- crowdstrike.immed-update[.]com
- crowdstrike-bluescreen[.]com
- crowdstrike[.]bot
- crowdstrike.com[.]vc
- crowdstrike[.]blue
- crowdstrike.develop[.]net
- crowdstrike[.]help
- crowdstrike.fix[.]com
- crowdstrike.orora[.]group
- cCcrowdstrike[.]ee
- fuckcrowdstrike.com[.]com
- fuckingcrowdstrike[.]com
- conflictstrike[.]com
- crowdstrikeeventshub[.]com
- crowdstrike.phpartners[.]org
- crowdstrikeoutage[.]com
- thecrowdstrike[.]com
- microsoftcrowdstrike[.]com
- winsstrike[.]com
- crowdstrikeodayl[.]com
- crowdstrikeblueteam[.]com
- crowdstrikeclaim[.]com
- crowdstrikedown[.]com
- crowdstrikereport[.]com
- bsodsm8r.xamzgjedu[.]com
- crowdstrikefix[.]zip
- crowdstrike[.]buzz
- crowdstuck[.]org
- whatiscrowdstrike[.]com
- failstrike[.]com
- clownstrike[.]co
- crowdstrikeupdate[.]com
- crowdstrikebsodfix.blob.core.windows[.]net
MITRE ATT&CK TTPs – created by AI
- Phishing – T1566
- Threat actors are using CrowdStrike-themed phishing sites to lure victims.
- These phishing attempts often involve threatening emails requesting payment for fake fixes.
- Domain Spoofing – TLD-0001
- Thousands of typo-squatting domains have been registered to exploit the CrowdStrike incident.
- Malicious infrastructure is being created to capitalize on the chaos from the BSOD loop.
- Malware Distribution – T1203
- Threat actors are distributing fake ‘hotfixes’ and malicious binaries disguised as legitimate updates.
- Examples include files named ‘crowdstrike-hotfix.zip’ and ‘CrowdStrike Updater.exe’.