
Insikt Group examines a large-scale Russian-language cybercrime operation using fake Web3 gaming initiatives to distribute malware designed to steal information from both macOS and Windows users. These Web3 games, which are based on blockchain technology, offer the potential for financial gains through cryptocurrency earnings.
Web of Deceit: The Rise of Imitation Web3 Gaming Scams and Malware Infections
The campaign involves creating imitation Web3 gaming projects with slight name and branding modifications to appear legitimate, along with fake social media accounts to bolster their authenticity. The main webpages of these projects offer downloads that, once installed, infect devices with various types of "infostealer" malware such as Atomic macOS Stealer (AMOS), Stealc, Rhadamanthys, or RisePro, depending on the operating system.
 Fraudulent Web3 gaming project status (Source: Recorded Future)
Fraudulent Web3 gaming project status (Source: Recorded Future)
The campaign targets Web3 gamers, exploiting their potential lack of cyber hygiene in the pursuit of profits. It represents a significant cross-platform threat, utilizing a variety of malware to compromise users' systems. The threat actors have prepared a resilient infrastructure, allowing them to quickly adapt by rebranding or shifting focus upon detection. The report highlights the necessity of continuous vigilance and recommends that individuals and organizations adopt comprehensive mitigation strategies against these sophisticated phishing tactics.
Specific findings reveal that the malware versions, including AMOS, can infect both Intel and Apple M1 Macs, indicating a broad vulnerability among users. The primary goal appears to be the theft of cryptocurrency wallets, posing a significant risk to financial security. Despite potential mitigations like endpoint detection and antivirus software, the campaign's techniques remain effective, suggesting the need for broader defense measures. Artifacts within the HTML code hint at the Russian origin of the threat actors, though their exact location remains uncertain. The report underscores the critical need for awareness and education to prevent downloads from unverified sources, highlighting the risk of brand damage to legitimate Web3 gaming projects if such threats are not adequately addressed.
To read the entire analysis, click here to download the report as a PDF.
Appendix A Indicators of Compromise
| Domains: ai-zerolend[.]xyz argongame[.]com argongame[.]fun argongame[.]network argongame[.]xyz astration[.]io astrationgame[.]com astrationgame[.]io astrationplay[.]com astrationplay[.]io blastl2[.]net cosmicwayrb[.]org crypterium[.]world crypteriumplay[.]com crypteriumplay[.]io crypteriumworld[.]io dustfighter[.]io dustfighter[.]space dustfightergame[.]com dustoperation[.]xyz gameastration[.]com playastration[.]com playcrypterium[.]com playcrypterium[.]io testload[.]pythonanywhere[.]com vether-testers[.]org vether[.]org worldcrypterium[.]io IP Addresses: File Hashes: |
Appendix B Mitre ATT&CK Techniques
| Tactic: Technique | ATT&CK Code |
| Data Obfuscation | T1001 |
| Data from Local System | T1005 |
| Query Registry | T1012 |
| Obfuscated Files or Information | T1027 |
| Exfiltration Over C2 Channel | T1041 |
| Scheduled Task/Job | T1053 |
| Process Discovery | T1057 |
| Command and Scripting Interpreter | T1059 |
| Application Layer Protocol | T1071 |
| System Information Discovery | T1082 |
| Modify Registry | T1112 |
| Data Encoding: Standard Encoding | T1132.001 |
| Indirect Command Execution | T1202 |
| User Execution | T1204 |
| User Execution: Malicious Link | T1204.001 |
| User Execution: Malicious File | T1204.002 |
| Virtualization/Sandbox Evasion | T1497 |
| Steal Web Session Cookie | T1539 |
| Unsecured Credentials | T1552 |
| Unsecured Credentials: Credentials in Files | T1552.001 |
| Disable or Modify Tools | T1562.001 |
| Phishing | T1566 |
| Acquire Infrastructure: Domains | T1583.001 |
| Acquire Infrastructure: Web Services | T1583.006 |
| Acquire Infrastructure: Malvertising | T1583.008 |
| Establish Accounts: Social Media Accounts | T1585.001 |
| Develop Capabilities | T1587 |
| Gather Victim Identity Information: Credentials | T1589.001 |
| Gather Victim Host Information: Software | T1592.002 |
| Financial Theft | T1657 |
Appendix C Domain and IP Correlations
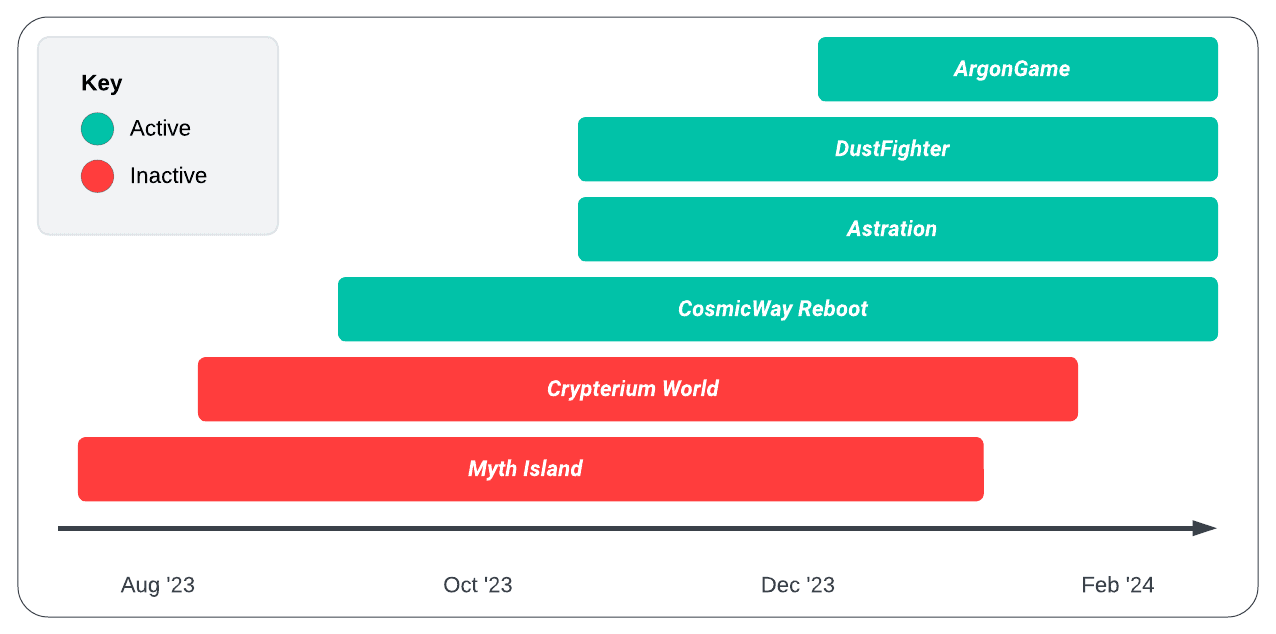
| Domain | Created | IP Address | Server | Active |
| astration[.]io | 2023-10-31 | 5.42.66[.]22 | nginx/1.22.0 | No |
| astrationplay[.]io | 2024-01-20 | 5.42.66[.]22 | Golfe2 | No |
| astrationplay[.]com | 2024-01-21 | 5.42.66[.]22 | Golfe2 | No |
| astrationgame[.]com | 2024-02-07 | 5.42.66[.]22 | nginx/1.22.0 | No |
| astrationgame[.]io | 2024-02-07 | 5.42.66[.]22 | nginx/1.22.0 | No |
| playastration[.]com | 2024-02-08 | 5.42.66[.]22 | nginx/1.22.0 | No |
| gameastration[.]com | 2024-02-12 | 5.42.66[.]22 | nginx/1.22.0 | Yes |
| dustfighter[.]io | 2024-01-31 | 5.42.65[.]102 | nginx/1.22.0 | Yes |
| dustfighter[.]space | 2024-02-22 | 5.42.65[.]102 | N/A | No |
| dustfightergame[.]com | 2024-02-26 | CLOUDFLARE | CLOUDFLARE | Yes |
| dustoperation[.]xyz | 2024-02-25 | 31.31.196[.]178 | nginx | Yes |
| ai-zerolend[.]xyz | 2024-02-23 | 31.31.196[.]161 | N/A | No |
| cosmicwayrb[.]org | 2023-10-27 | CLOUDFLARE | CLOUDFLARE | Yes |
| argongame[.]com | 2023-12-16 | CLOUDFLARE | CLOUDFLARE | Yes |
| argongame[.]network | 2024-02-04 | CLOUDFLARE | CLOUDFLARE | Yes |
| argongame[.]fun | 2024-02-04 | CLOUDFLARE | CLOUDFLARE | No |
| argongame[.]xyz | 2024-02-04 | CLOUDFLARE | CLOUDFLARE | Yes |
| crypteriumplay[.]com | 2023-09-09 | 5.42.67[.]1 | nginx/1.22.0 | No |
| playcrypterium[.]com | 2023-09-19 | 5.42.67[.]1 | nginx/1.22.0 | No |
| playcrypterium[.]io | 2023-10-11 | 5.42.67[.]1 | nginx/1.22.0 | No |
| worldcrypterium[.]io | 2023-09-06 | 5.42.67[.]1 | nginx/1.22.0 | No |
| crypterium[.]world | 2023-08-03 | CLOUDFLARE | CLOUDFLARE | No |
| crypteriumworld[.]io | 2023-08-28 | 5.42.64[.]83 | nginx/1.22.0 | No |
| crypteriumplay[.]io | 2023-10-25 | 5.42.65[.]102 | AliyunOSS | No |
| vether[.]org | 2023-11-30 | CLOUDFLARE | CLOUDFLARE | Yes |
| vether-testers[.]org | 2024-01-30 | 82.115.223[.]26 | nginx/1.20.2 | Yes |
Source: Original Post