Summary: This content discusses the STR RAT, a remote access trojan (RAT) written in Java, its capabilities, and its history of updates.
Threat Actor: STR RAT | STR RAT
Victim: Various targets | Various targets
Key Point :
- STR RAT is a Java-based remote access trojan that grants full control to threat actors upon successful installation.
- It is capable of keylogging, credential theft, and delivering additional malicious payloads.
- The malware receives annual version updates, with 60% of recent samples delivered via email.
- STR RAT was first discovered in 2020 and has since evolved with new features and infection chain updates.
By Jacob Malimban
STR RAT is a remote access trojan (RAT) written in Java that was first seen in 2020. Like other RATs, it gives threat actors full control when it is successfully installed onto a machine. STR RAT is capable of keylogging, stealing credentials, and even delivering additional malicious payloads. The malware receives a version update every year, on average. These updates correlate with the renewed use of STR RAT by threat actors. Currently, 60% of the STR RAT samples that Cofense analyzed from January 2023 to April 2024 are delivered directly to the email as opposed to an embedded link.
History
STR RAT is like a seasonal flu. Every year, some part of the infection chain receives an update, and STR RAT becomes more prominent for a short period of time. STR RAT was first discovered on an antivirus forum post in 2020. Already in version 1.2, it had the main RAT features we have come to expect: password stealing, keystroke logging, and backdoor access. It also had a fake “.crimson“ ransomware module, that only renamed files without encrypting them.
In 2021, Microsoft Threat Intelligence tweeted about STR RAT and its appearance in phishing campaigns. STR RAT started appearing again in 2022, with emails spoofing the Maersk shipping brand. It also employed the polyglot file technique where the malware could be executed as an MSI or Java file. In 2023, STR RAT reached version 1.6 and started using Zelix KlassMaster along with the already implemented Allatori software. These tools obfuscated the source code and made it harder for cybersecurity professionals to analyze the malware. Finally in 2024, STR RAT was uploaded to legitimate services like GitHub and Amazon Web Services (AWS) so that it could be downloaded via links embedded in emails and clogged user inboxes with a vengeance.
Capabilities
Like other RATs, STR RAT is capable of password stealing, keystroke logging, and backdoor access. It can steal passwords saved in Chrome, Firefox, and Internet Explorer. For email clients, it targets Outlook, Thunderbird, and China’s Foxmail. Other commands are shown in Table 1.
Key commands include o-keylogger, which creates a text file containing all subsequent text typed out. For RAT capabilities, there’s down-n-exec to download and execute a file, remote-screen for the attacker to commandeer the computer, and power-shell for a PowerShell terminal.
Table 1: STR RAT commands from G Data.
| reboot | power-shell | hrdp-new | ie-pass |
| shutdown | file-manager | hrdp-res | all-pass |
| uninstall | keylogger | chrome-pass | chk-priv |
| disconnect | o-keylogger | foxmail-pass | req-priv |
| down-n-exec | processes | outlook-pass | rw-encrypt |
| update | startup-list | fox-pass | rw-decrypt |
| up-n-exec | remote-screen | tb-pass | show-msg |
| remote-cmd | rev-proxy |
In the Wild
STR RAT has never been as prevalent as more popular RATs like Remcos RAT. Nevertheless, there are interesting patterns with the frequency of STR RAT and the months from January 2023 to April 2024 as shown in Figure 1. In 2023, there is a sustained use of STR RAT from March to August. This is likely due to the new STR RAT update, version 1.6, and the polyglot file technique for more compatibility with Windows. In March 2024, STR RAT again appears in significant numbers. This can be attributed to attackers using legitimate services like GitHub and AWS to host and deliver STR RAT. This is because GitHub and AWS links appear more legitimate than a domain registered just two days prior to both secure email gateways (SEGs) and recipients.
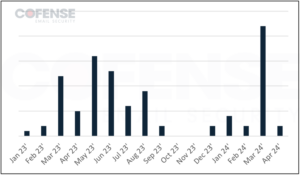

Figure 1: STR RAT active threat report (ATR) Volume from January 2023 to April 2024.
Delivery Mechanisms
Figure 2 shows the delivery mechanisms for STR RAT. The lion’s share is just attaching STR RAT to the phishing email. Thus, direct attachment constitutes about 60% of Cofense’s STR RAT Active Threat Reports (ATRs). Loaders are next at 20%, beating URLs embedded in PDFs by 5%. The last 5% is delivered by droppers.


Figure 2: Delivery Mechanisms used to deliver STR RAT between January 2023 and April 2024.
Attachment
STR RAT is typically delivered in an archive attached to the email. STR RAT is typically a .jar file, requiring specialized components to run on a victim machine. This component is a Java Runtime Environment (JRE). Since STR RAT JAR files needs a JRE to execute, attached archive files have the potential to contain all necessary JRE binaries. However, STR RAT is also known to download the required files from the Maven and GitHub repositories.
Loaders
Surprisingly, STR RAT’s 2nd most common delivery mechanism is Loaders instead of an embedded URL like other malware. Loaders are malware that reach out to a payload location to download and run the malware. STR RAT is commonly loaded by Jar Downloaders. Jar Downloaders require Java to execute, but the attacker can customize or update the payload STR RAT while keeping the original Jar Downloader malware link. A second loader is CVE-2017-11882, a commonly exploited Microsoft Office vulnerability. When run, the Word or Excel document will download a payload to execute. In this case, the Office document runs STR RAT. A third loader used is the Windows Registry File downloader. It involves a .reg file attached to the email, which installs a registry key to the computer when executed. After installation, the registry file will download either STR RAT or a dropper. The malicious registry key can be configured to run on every restart, gaining persistence.
Embedded URLs
Threat actors may use links to download malware instead of attaching malware to the email in an attempt to bypass email security. The victim recipient would click on the link and download the malware unknowingly. For STR RAT, the URLs are either linked in the email or in an attached PDF. The attached PDF encourages the victim to click and download the expected content but downloads malware instead. The file downloaded is either the .jar STR RAT or an archive file containing the malware.
As mentioned earlier, most URLs use legitimate services to host the malware. Attackers have uploaded STR RAT to AWS, GitHub, and Discord’s CDN (Content Delivery Network). The link to the malware is then embedded in the emails. For STR RAT, threat actors also use link shorteners to bypass email security and hide the file downloaded typically shown in the full URL.
Droppers
Unlike loaders, droppers already contain the malware to be deployed. A dropper file contains both its own harmful code and the final malware (like STR RAT). It does not need to reach an online payload like a loader does. A dropper file has an anomalously larger file size which hints to something malicious. For example, an HTML file is usually just kilobytes; therefore, an HTML file that is several megabytes large is suspicious.
For STR RAT, our records show that the JavaScript Dropper (JS Dropper) is the most common dropper. A JS Dropper is a .js file that is natively executed on Windows computers. JS Droppers are usually attached to the email. Naturally, as JS Dropper contains both itself and STR RAT, the JS Dropper file is quite large.
Behavior (Capabilities)
Once STR RAT is executed by a JRE, it starts placing files, creating persistence, and installing dependencies. Some versions of STR RAT even print out debug information when running, showing successful installation of downloaded files as shown in Figure 3.


Figure 3: Debug information from STR RAT.
One file of particular interest is XXXXlock.file located in the user’s local home profile (C:Usersusername). The XXXX is replaced with the port used to communicate back to STR RAT’s command and control servers. The lock file also appears to prevent multiple instances of STR RAT. This is especially useful as this malware doesn’t typically delete itself and run in memory like other malware.
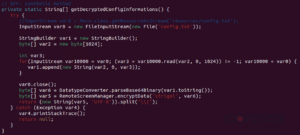

Figure 4: Main.java in STR RAT.
A JAR is a Java Archive file that we can extract to get more information about the configuration of a STR RAT sample. In the resources folder, there is a base 64 encoded config.txt. The config is also encrypted using AES. To decrypt, we can find the passphrase “strigoi” in Main.java. There are also more details about the encryption in RemoteScreenManager.java. In Figure 5 we see that a PBKDF2 key is made using that passphrase, as well as the other AES decryption details.
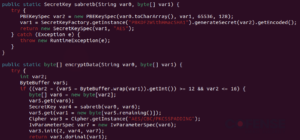

Figure 5: RemoteScreenManager.java with decryption details.
In the newly created lib folder in the user’s local home profile (C:Users<username>), the legitimate files can be found. Note that these files can also be found in AppData Roaming (C:Users<username>AppDataRoaming) folder. These legitimate files can either be downloaded, as described in the networking section, or dropped to disk by larger samples that have bundled the necessary files. JNA, or java native access, allows easy use of windows DLLs (dynamic link libraries). A software developer or threat actor can work with Windows libraries by just writing Java code. SQLite JDBC (Java DataBase Connectivity) allows STR RAT to use SQLite as a database. Most importantly, system-hook is a “keyboard and mouse listener for Java”, as stated in its GitHub page. It is used illegitimately in STR RAT for keylogging.


Figure 6: Downloaded files in lib.
After setup and execution, it uses a geolocator service. It uses a legitimate service such as hxxp//ip-api[.]com/json/ to geo-fingerprint the infected computer and will send this and other system information to the C2 server.
Detection and Hunting
There are different versions of STR RAT which leave different IOCs on disk. Here are some indicators to expect.
Installation
After execution, STR RAT can copy itself to multiple locations. A renamed “txt” file can be found in AppData Roaming (C:Users<username>AppDataRoaming) and the user’s local home profile (C:Users<username>). Those locations will also have a new folder, lib, containing legitimate files that are used by STR RAT. For more information on the keylogging system-hook, see the in the Behaviors section. Finally, there should be a XXXXlock.file where XXXX is the port of the STR RAT C2, like 7888lock.file. This file will be in the user’s local home profile.
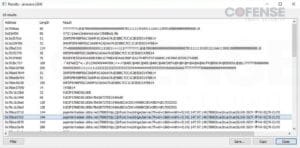

Figure 7: STR RAT configuration in memory.
The configuration of STR RAT can also be seen through memory analysis. This is the same configuration encrypted using the passphrase ‘strigoi’, among other things. In Figure 7, the C2 server, port, and a domain associated with STR RAT, jbfrost[.]live, can be seen. The domain jbfrost[.]live was in use since STR RAT first appeared in 2020. The current whois records show the register date occurred on March 14, 2022. It is interesting how STR RAT uses both hardcoded (jbfrost[.]live) and randomly generated C2s for communication. For the randomly generated C2s, see the Network Traffic section.
Persistence
STR RAT can create persistence. Whether by Registry Run Keys / Startup Folder (MITRE T1547.001) or a Scheduled Task/Job (MITRE T1053), the malware will run every time the user logs in as well as at set time intervals. Endpoint detection and response software can monitor the following location for STR RAT persistence.
- HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun
- HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun
- C:UsersAppDataRoamingMicrosoftWindowsStart MenuProgramsStartup
- C:ProgramDataMicrosoftWindowsStart MenuProgramsStartUp
- Skype in Task Scheduler


Figure 8: ‘Skype’ scheduled task for STR RAT persistence.
Network Traffic
Cofense has observed STR RAT reaching out to domain name and port combination. The C2s are typically subdomains of free dynamic DNS services, like Duck DNS. There are also ports combined with pure IP address and recently, AWS. Like other RATs, HTTP is used for C2 communications, though the port is not the standard tcp/80.
Legitimate Services
STR RAT also reaches out to legitimate services. GitHub and Maven are legitimate sites that host legitimate tools for software development. Although the domain of these indicators cannot be blocked, seeing an endpoint reach out to these locations in tandem with other behavior is highly suspicious and warrants further investigation.
- hxxpsrepo1[.]maven[.]org/maven2/net/java/dev/jna/jna/5[.]5[.]0/jna-5[.]5[.]0[.]jar
- hxxpsrepo1[.]maven[.]org/maven2/net/java/dev/jna/jna-platform/5[.]5[.]0/jna-platform-5[.]5[.]0[.]jar
- hxxpsrepo1[.]maven[.]org/maven2/org/xerial/sqlite-jdbc/3[.]14[.]2[.]1/sqlite-jdbc-3[.]14[.]2[.]1[.]jar
- hxxpsgithub[.]com/kristian/system-hook/releases/download/3[.]5/system-hook-3[.]5[.]jar
- hxxpip-api[.]com/json/
Source: https://cofense.com/blog/str-rat-phishing-malware-baseline
“An interesting youtube video that may be related to the article above”