Summary: Microsoft has identified a new North Korean threat actor called Moonstone Sleet, which has been active since August 2023 and shows similarities to another North Korean group, Diamond Sleet.
Threat Actor: Moonstone Sleet | Moonstone Sleet
Victim: Not specified
Key Point :
- Moonstone Sleet is a new North Korean threat actor that has been active since August 2023.
- It shares code and techniques with another North Korean group, Diamond Sleet.
- Overlaps are common within the North Korean threat landscape as most groups serve the regime.
Microsoft has revealed the existence of a new North Korean threat actor, dubbed Moonstone Sleet.
Previously tracked as Storm-1789, a denomination used by the tech giant for uncategorized malicious activity clusters, Moonstone Sleet has been active since at least early August 2023.
Until now, the threat actor demonstrated substantial overlaps with Diamond Sleet, another North Korean group.
“[Moonstone Sleet] was extensively reusing code from known Diamond Sleet malware like Comebacker and using well-established Diamond Sleet techniques to gain access to organizations, such as using social media to deliver trojanized software,” Microsoft explained in their report published on May 28.
Overlaps are common within the North Korean threat landscape, inside of which almost all threat groups work for the same cause: serving the regime. This leads some cyber threat intelligence researchers to attribute any malicious activity from a North Korean group to the umbrella group Lazarus.
Moonstone Sleet’s Techniques, Tactics and Procedures
Moonstone Sleet has shifted to its own bespoke infrastructure and attacks, prompting Microsoft to attribute the group a unique name.
To compromise its victims’ IT systems, Moonstone Sleet employs a combination of tried-and-tested and new techniques, including setting up fake companies and job opportunities to engage with potential targets, deploying trojanized versions of legitimate tools and creating malicious games.
The group also delivers its own custom ransomware.
Trojanized Legitimate Tools
One of the earliest Moonstone Sleet strategies detected by Microsoft dates back to August 2023, when the threat actor was observed delivering a trojanized version of PuTTY, an open-source terminal emulator, via apps like LinkedIn and Telegram as well as developer freelancing platforms.
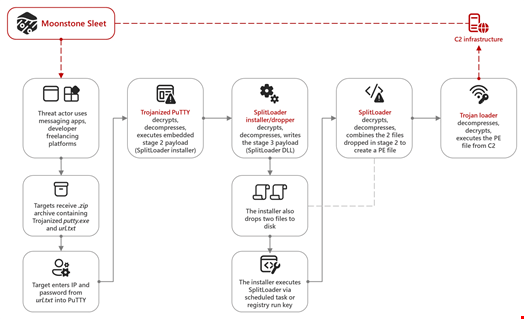
Similarly, the group targeted potential victims with projects that used malicious npm packages, often through freelancing websites or other platforms like LinkedIn.
This use of common social media platforms to deliver malicious payloads has been observed with other North Korean actors like Diamond Sleet.
Fake Companies
From January 2024, Moonstone Sleet was observed creating several fake companies impersonating software development and IT services, typically relating to blockchain and AI.
StarGlow Ventures and C.C. Waterfall were two examples of companies created by the group to reach potential targets.
The group used a combination of created websites and social media accounts to add legitimacy to their campaigns.
Malicious Game
In February 2024, Moonstone Sleet added a malicious mobile tank-themed game it developed to its hacking portfolio.
The game has several names, including DeTankWar, DeFiTankWar, DeTankZone, and TankWarsZone.
“In this campaign, Moonstone Sleet typically approaches its targets through messaging platforms or by email, presenting itself as a game developer seeking investment or developer support and either masquerading as a legitimate blockchain company or using fake companies,” Microsoft wrote.
FakePenny Ransomware
Finally, in April 2024, Microsoft detected that Moonstone Sleet had started delivering a new custom ransomware variant, which the tech giant named FakePenny.
The ransomware includes a loader and an encryptor. The ransomware note dropped by FakePenny closely overlaps with the note used by Seashell Blizzard in its malware NotPetya.
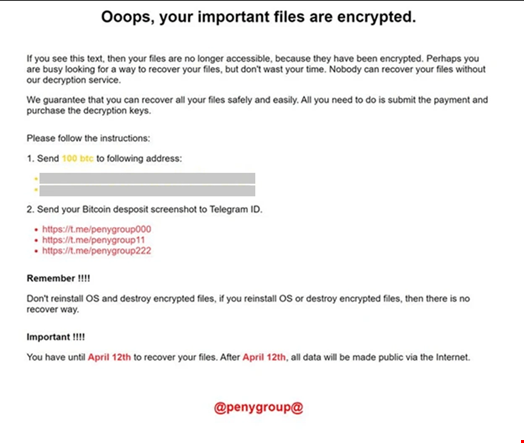
One ransom demand the group sought from a compromised company was $6.6m in Bitcoin, which is significantly higher than ransom demands for other North Korean ransomware, such as WannaCry 2.0 and H0lyGh0st.
Source: https://www.infosecurity-magazine.com/news/new-north-korean-hacking-group
“An interesting youtube video that may be related to the article above”