Threat Actor: Unknown | Unknown
Victim: BreingAir | BreingAir
Price: Not disclosed
Exfiltrated Data Type: User credentials (client, employee, and admin)
Additional Information:
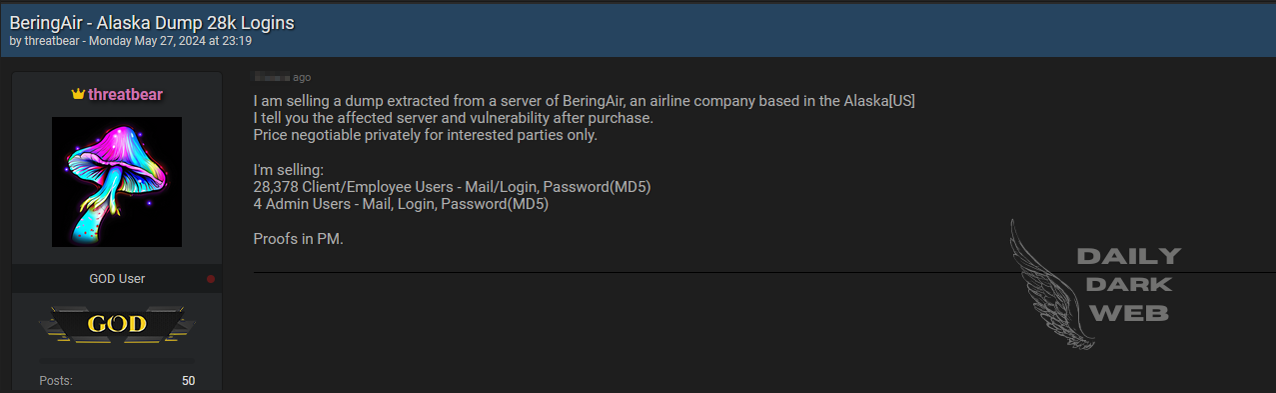
- The threat actor claims to be selling sensitive data from BreingAir, an airline company based in Alaska, USA.
- The compromised data includes 28,378 client/employee user credentials, including email/login information and passwords encrypted using the MD5 hashing algorithm.
- Additionally, the breach allegedly includes 4 admin user credentials, comprising email, login, and MD5-encrypted passwords.
- The specific server or vulnerability exploited to obtain this information has not been disclosed by the threat actor.
- The price for the data is said to be negotiable, and interested parties are instructed to engage privately for further discussions.
A threat actor has claimed to be selling sensitive data from BreingAir, an airline company based in Alaska, USA. The alleged sale includes user credentials for both clients and employees, as well as administrative users.
According to the threat actor’s announcement, the compromised data includes:
28,378 Client/Employee User Credentials: This dataset reportedly contains user credentials, including email/login information and passwords encrypted using the MD5 hashing algorithm.
4 Admin User Credentials: Additionally, the breach allegedly includes credentials for administrative accounts, comprising email, login, and MD5-encrypted passwords.
The threat actor has not disclosed the specific server or vulnerability exploited to obtain this information, intending to share these details only with potential buyers after purchase. The price for the data is said to be negotiable, with interested parties instructed to engage privately for further discussions.
Original Source: https://dailydarkweb.net/threat-actor-claims-to-sell-breingair-user-data-including-client-employee-and-admin-credentials/