By: Cofense Intelligence
Threat actors are running a series of campaigns spoofing several departments of the United States government. The emails claim to request bids for government projects but lead victims to credential phishing pages instead. These campaigns have been ongoing since at least mid-2019 and were first covered in our Flash Alert in July 2019. These advanced campaigns are well crafted, have been seen in environments protected by secure email gateways (SEGs), are very convincing, and appear to be targeted. They have evolved over time by improving the email contents, the PDF contents, and the appearance and behavior of the credential phishing pages.
Email Contents: More Convincing, More Evasive
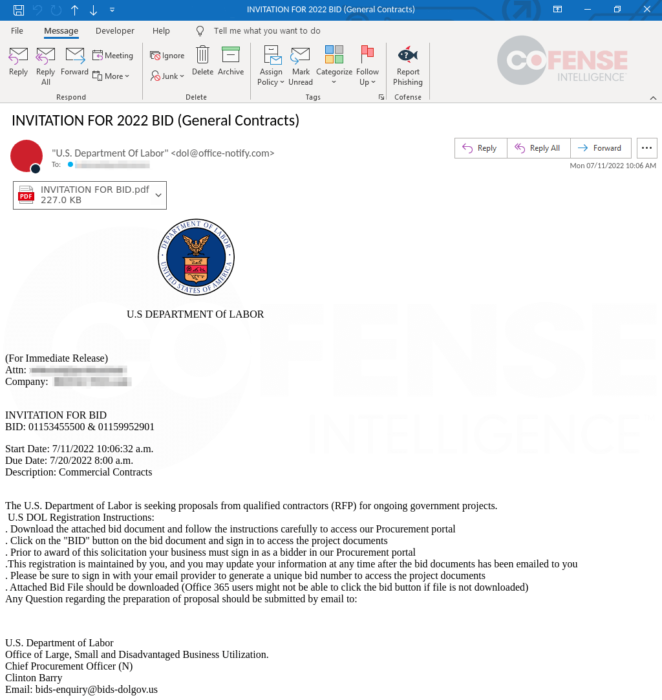 Figure 1: Initial Email of Most Recent Campaign
Figure 1: Initial Email of Most Recent CampaignThe campaigns targeted companies across a variety of sectors but focused most heavily on the energy and professional services sectors, including construction companies. The attackers likely targeted companies which could credibly receive invitations to bid from the relevant government department. The emails spoofed the U.S. Departments of Labor, Commerce, or Transportation. This was evident in the sender’s name and email address (as seen in Figure 1) as well as in the email signature. Sender email addresses for these campaigns originally appeared to be hosted on [.]us domains such as openbids[@]dol-gov[.]us, but towards the end of 2021, the addresses were more consistently spoofed as coming from a [.]gov email address like no-reply[@]dot[.]gov. These emails were typically sent from IP addresses hosted by the Hivelocity Inc ASN. In some cases, the service located at the sending IP address identified itself as a Microsoft IIS Windows server. Early emails had more simplistic email bodies without logos and with relatively straightforward language. The more recent emails made use of logos, signature blocks, consistent formatting, and more detailed instructions. Recent emails also include links to access the PDFs rather than directly attaching them.
PDF Contents: Lures Appear More Authentic
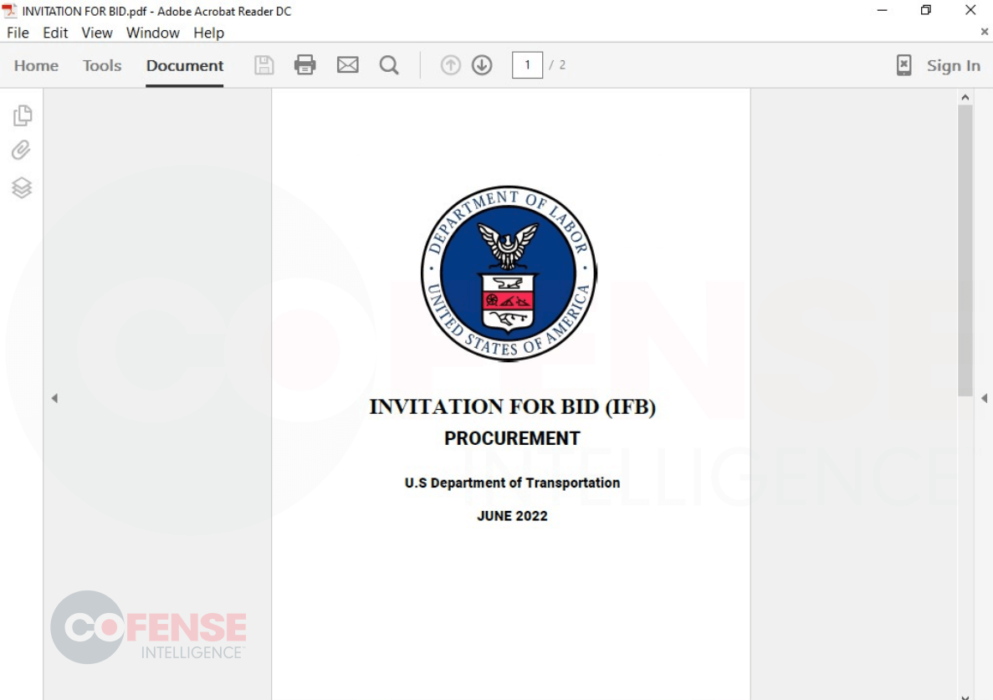 Figure 2: First Page of an Attached PDF
Figure 2: First Page of an Attached PDFPDFs attached to these emails have changed over time. Within recent emails, the first page (seen in Figure 2) is typically the logo of the spoofed government department with additional information about the bid. The second page (shown in Figure 3) typically contains information about the process and will lure victims into clicking the link. In older versions, the PDFs were usually 1 or 3 pages. They contained more technical information about the bidding process, a signature of the spoofed sender, and a watermark of the spoofed department.
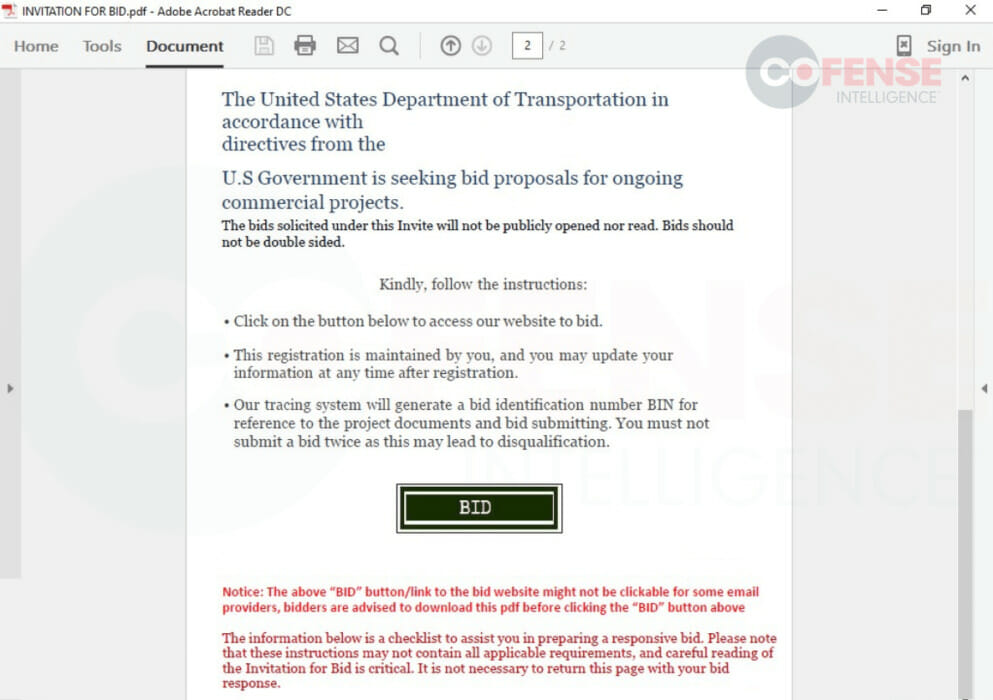 Figure 3: Second Page of an Attached PDF with Embedded Link to Credential Phishing Page
Figure 3: Second Page of an Attached PDF with Embedded Link to Credential Phishing Page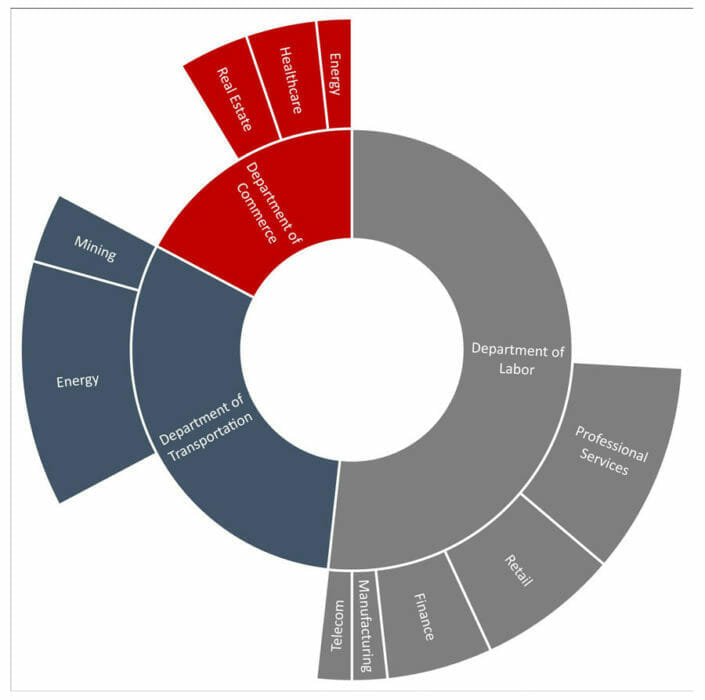 Figure 4: Targeted Sector by Spoofed Department
Figure 4: Targeted Sector by Spoofed DepartmentThe metadata of the PDFs provides additional interesting information, as well as evidence of advancements in the threat actor’s TTPs. Older PDFs had little customization, and all listed the same “edward ambakederemo” as the author of the document. In the most recent PDFs, both the attached and downloaded versions, there is spoofed information more relevant to the recipient. The author is listed as “WisDOT”, the company is listed as “Wisconsin Department of Transportation”, and the subject, title, and description are all listed as “WisDOT Procurement – Invitation for Bid Toolkit”. The new information is an almost exact match with the metadata associated with an authentic invitation-for-bid toolkit PDF published by Wisconsin DOT. The change from using PDFs with consistent meta data for multiple campaigns to using customized meta data that appears authentic and is relevant to the specific campaign shows clear advancement in the TTPs of the threat actor.
Credential Phishing Page: Improved “Login” Process
In each case, the initial page of the phish is a copy of the home page of the spoofed department with the addition of a single red button encouraging victims to click it in order to bid. In cases spoofing the Department of Labor, the spoofed page (Figure 6) is a near duplicate of the legitimate DoL page (Figure 5) from about a year ago, but shows the added button. When victims click the link, they are taken to a different page on the same malicious domain (Figure 7), or in the case of some of the older pages, a popup window showing a page still on the same domain. The use of HTTPS ensures that a green padlock will appear, further giving the page a sense of
legitimacy. The domains used for the phishing pages and for the links embedded in the PDF are specifically chosen to emulate government-bid-related themes. Therefore, they often include the department spoofed (such as dol) and “bid”. In addition to the URL seen in Figure 5, there were also URLs including .gov in the subdomain such as transportation[.]gov[.]bidprocure[.]secure[.]akjackpot[.]com, which has a purposefully long subdomain that could make only the part of the URL with .gov in it appear in the URL bar in smaller browser windows.
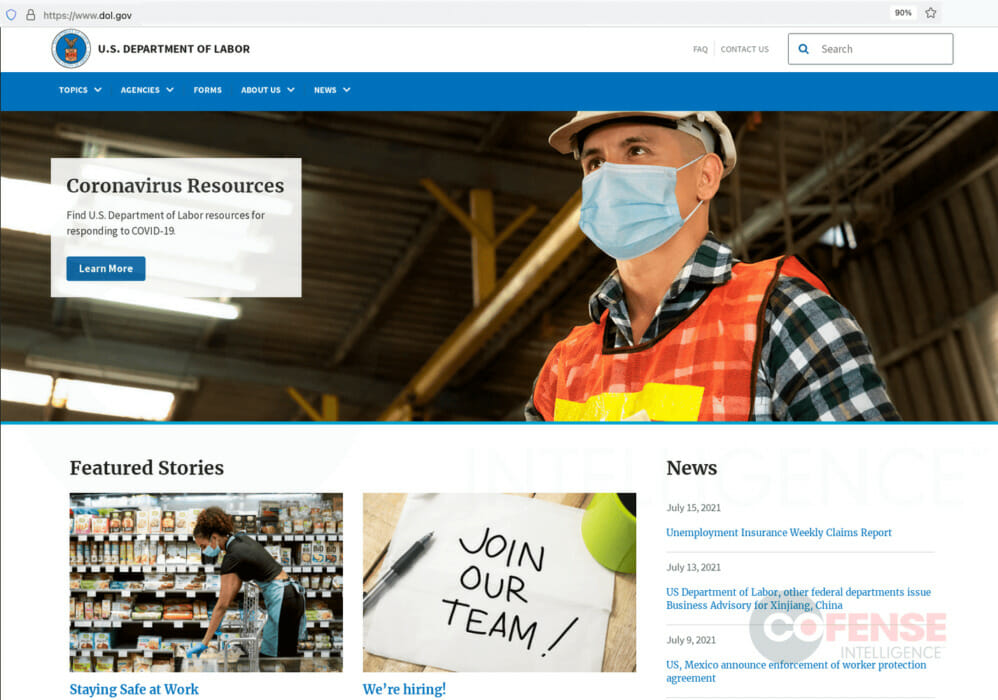 Figure 5: Legitimate Department of Labor Website from July 2021
Figure 5: Legitimate Department of Labor Website from July 2021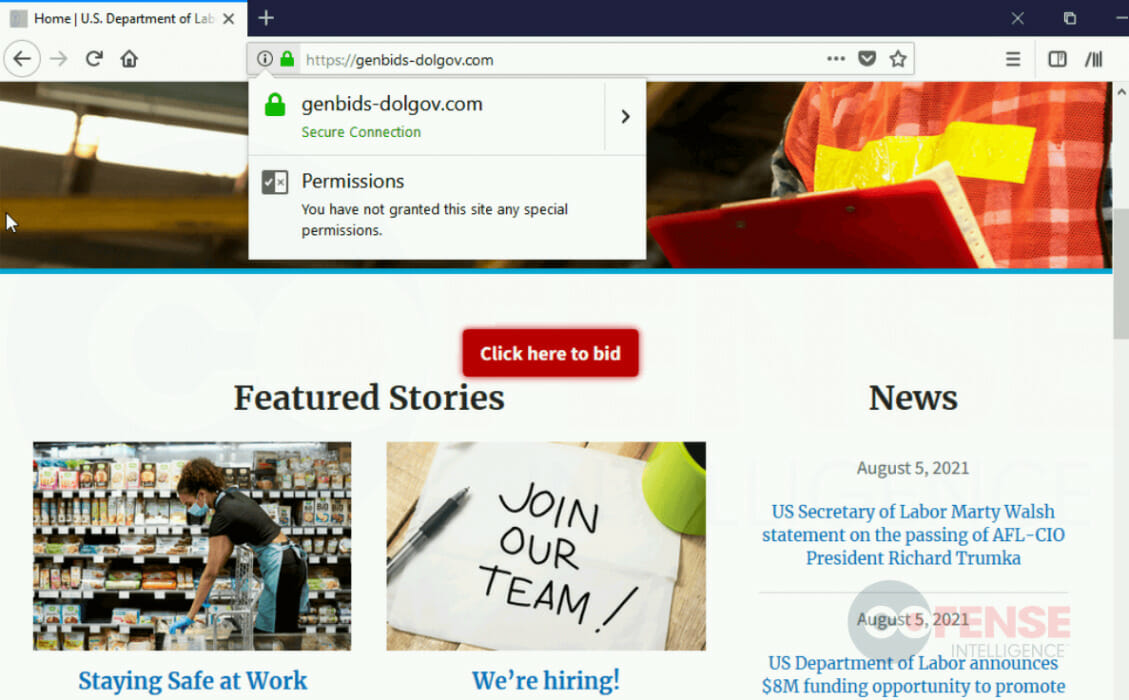
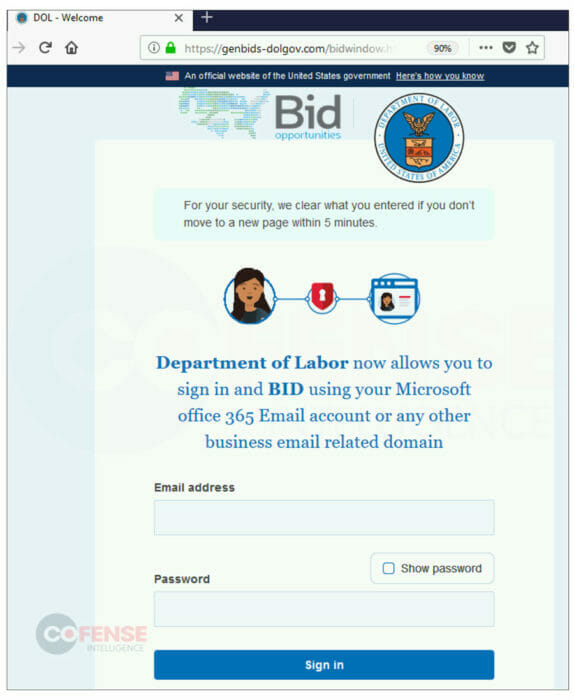 Figure 7: Credential Request Form
Figure 7: Credential Request FormThe page helpfully informs victims that the page will accept Microsoft Office (i.e., corporate) credentials. This would appear in a popup window in some of the older pages. This initial page is consistently hosted on “/bidwindow.htm”. Subsequent pages (consisting of the URL paths “/openbid.php” and “/completegen.html”) ask victims to reenter credentials.
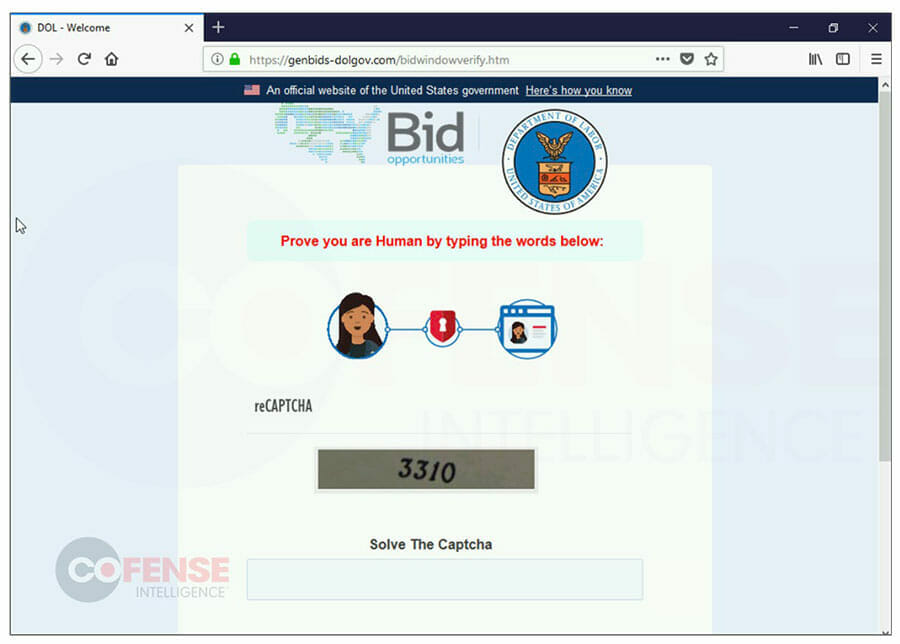 Figure 8: Captcha Challenge After Credentials Are Entered
Figure 8: Captcha Challenge After Credentials Are EnteredVictims are then prompted with a captcha to verify that they are indeed human. This captcha is always hosted at “/bidwindowverify.htm”. After the captcha is complete and the credentials are exfiltrated, victims are redirected to the legitimate page of the relevant government department. After being redirected to the relevant government department’s website, victims are left to wonder if their credentials were accepted for the bid or if something else entirely happened. Specific instructions in the PDF inform victims that submitting twice is likely going to cause the whole process to fail, discouraging victims from trying again. The original credential phishing pages lacked multi step processes, captcha checks, and had limited interactions. Instead, the credential harvesting form was hosted on the initial landing page. The improvements over time have made the pages more likely to trick victims into entering credentials and less likely to realize after the fact that they have fallen for a phish.
Results of The Campaign
These campaigns are convincing from start to finish and make use of preexisting data copied from legitimate sources in order to mislead victims. The consistent impersonation of a United States federal department is carried out each time with updated information including watermarks on PDFs and information on the credential phishing pages. The only place where the threat actors fall slightly behind is their spoofed pages can be out of date, which will likely go unnoticed by most victims. Given the advancements seen in each area of the phishing chain, it is likely the threat actors behind these campaigns will continue to innovate and improve upon their already believable campaigns. The first step towards defending against these kinds of attacks is ensuring that employees do not click malicious links. The next step is ensuring that employees realize this applies to attachments just as much as it does to links directly embedded in emails. Training employees to be suspicious of emails and carefully examine both links and sender information can also help here. An observant employee might notice that sometimes the sending email address, such as Figure 1, is not in fact a .gov address, and the embedded links are not in fact .gov domains. Cofense Intelligence will continue to track these campaigns and provide up to date IOCs and rules allowing customers to track and predict similar campaigns. In fact, Cofense Intelligence recently posted about a campaign which used similarly advanced emails and copies of legitimate websites with an embedded “click to bid” link.
To download this report, click here.
Source: https://cofense.com/blog/credential-phishing-targeting-government-contractors-evolves-over-time