Summary: This content discusses a phishing campaign that targets business accounts by using email lures and compromising the accounts through a series of steps.
Threat Actor: Unknown | Unknown
Victim: Business accounts | Business accounts
Key Point :
- Email Link – The phishing emails contain links hosted on domains like Netlify[.]app or Vercel[.]app, which are used to host phishing sites. In some cases, a link shortener is also used as an additional redirect.
- Step 1: Landing Page – After clicking the email link, users encounter a landing page designed to manipulate them into believing…
The campaign starts with an email and ends with the account being compromised, but there are a few notable steps throughout the infection chain before the target business account is fully compromised. Each step follows the same lure to draw victims in and collect sensitive information related to the account. Images of the phishing pages can be seen in Figure 2 below.
- Email Link – The phishing emails start with a link that is either hyperlinked to text or embedded into a clickable image like the “Verify” button seen earlier. These links are all hosted on the domains Netlify[.]app or Vercel[.]app, which are web hosting services that the threat actors are abusing to host their phishing sites. In some cases, the campaign incorporates a t[.]co, X’s link shortener, into the infection chain that just acts as an additional redirect.
- Step 1: Landing Page – Following the email, users are met with a landing page that serves no functional purpose other than to manipulate users into believing this is a legitimate process to recover their account.
- Step 2: Account Information – The second step harvests Meta account information such as business email, page name, page owner, email address, phone number, information related to financial information, and recent travel arrangements, and an area to submit an appeal. Some of this information may seem unnecessary, but in the case of the threat actors successfully gaining access to an account, this could help them disrupt Meta’s account recovery process.
- Step 3: Account Password – The third step is pretty straightforward, it just requests that the user enter their password. Stolen information in this campaign is exfiltrated to various locations set up by the threat actors, one example is that credentials have been posted to a Telegram bot.
- MFA Bypass Step – This step is what makes this campaign such a high-level and potentially successful threat. It’s relatively simple at first glance, it just requests that the user inputs their 6-digit or 8-digit code from their authenticator app. Once entered, there is a loading process that essentially waits long enough for a new code to be generated and then requests it again. This additional step is likely used to ensure that access to the account has successfully been stolen.
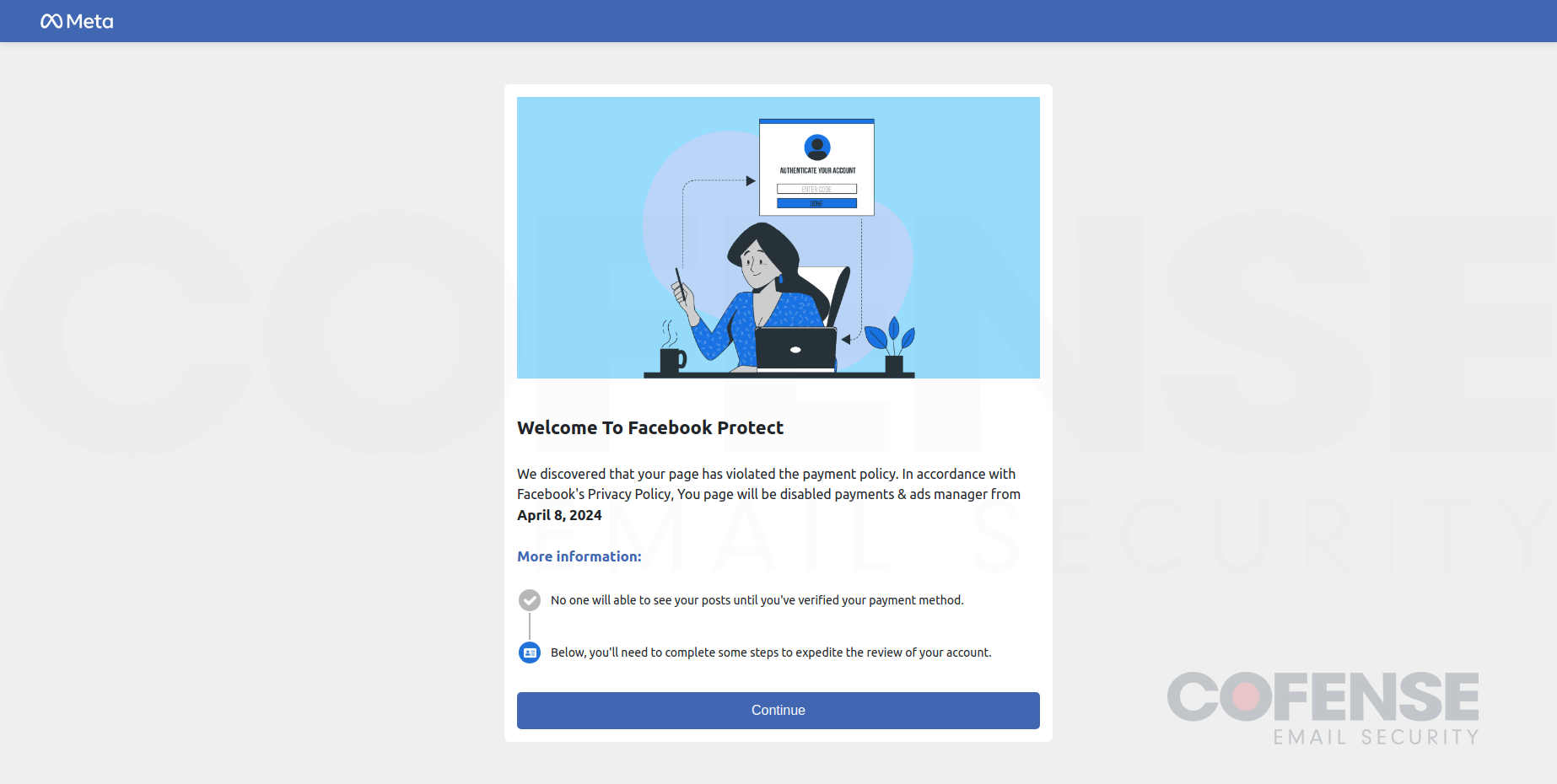

Figure 2: The landing page, the first page that users will see after interacting with the phishing URL.
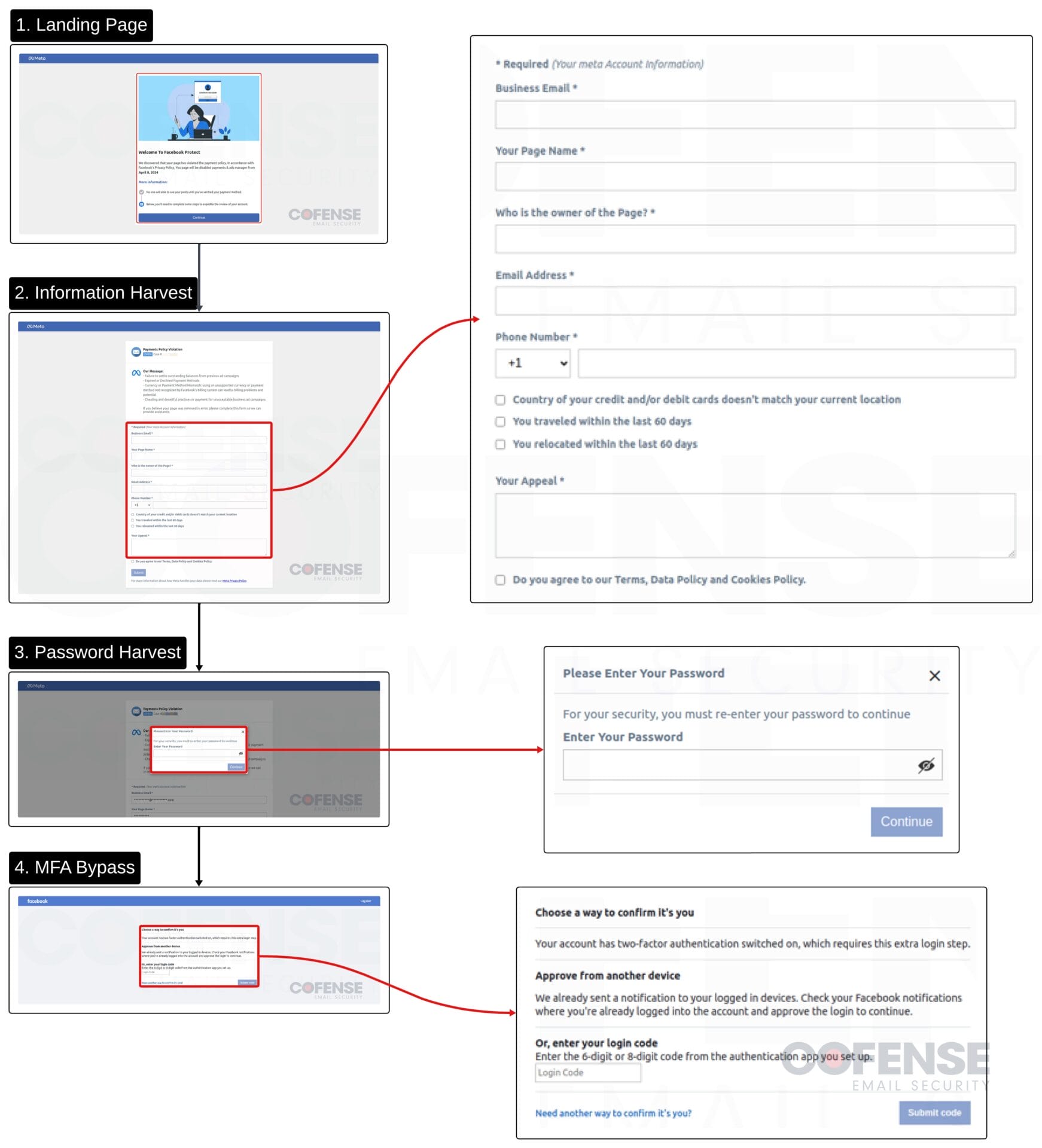

Figure 3: Breakdown of the full phishing infection chain.
A Deep Analysis of Threat Actor Infrastructure
During an analysis, a Cofense threat analyst identified open access to tooling used for this campaign hosted on bot1[.]sieulike[.]com. The site contains several redirects that have been translated from Vietnamese to English. These redirects go to areas the threat actors frequently visit like Netlify[.]app to create new links, Microsoft email login for Hotmail, and two spreadsheets; one for profits and costs in addition to one containing data on countries they target. Most of these are locked behind logins and require access to be granted by the threat actors.
In particular, the Profit / cost spreadsheet requires a login to be able to access the spreadsheet. The fact that there is a spreadsheet specifically for costs and profits implies that the threat actors are seeking financial gain. While that is obvious for most campaigns, for this one, in particular, it certainly proves that the threat actors will employ an additional attack vector once the business ad account has been compromised.
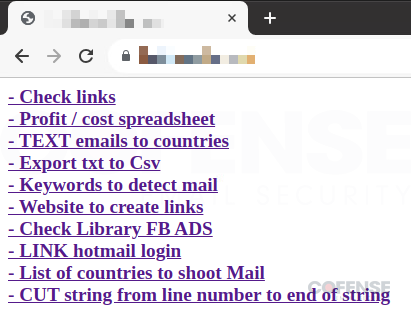

Figure 4: Threat actor resources, infrastructure, and tools used in this campaign.
The site also hosts several tools that show how efficient and advanced these threat actors are. These tools vary from simply converting input text into a CSV to generating complete phishing emails. A breakdown of some of the more notable tools that are listed in Figure 4:
- Check Links (Figures 5 and 6) – All of the indicators of compromise you could ever want are conveniently included in this tool. Not only does it contain a long list of phishing URLs that are actively being used, but it also allows the threat actors to automatically check if the links are still live or have been taken down.
- TEXT emails to countries (Figure 7) – This is a unique tool used to automatically generate phishing emails based on criteria entered by the threat actors. The threat actors select one of the 19 different countries they target, the theme they want the email to be (policy violation or copywriting infringement), the phishing link they want to use, and then it generates a text version of the email and the headers.
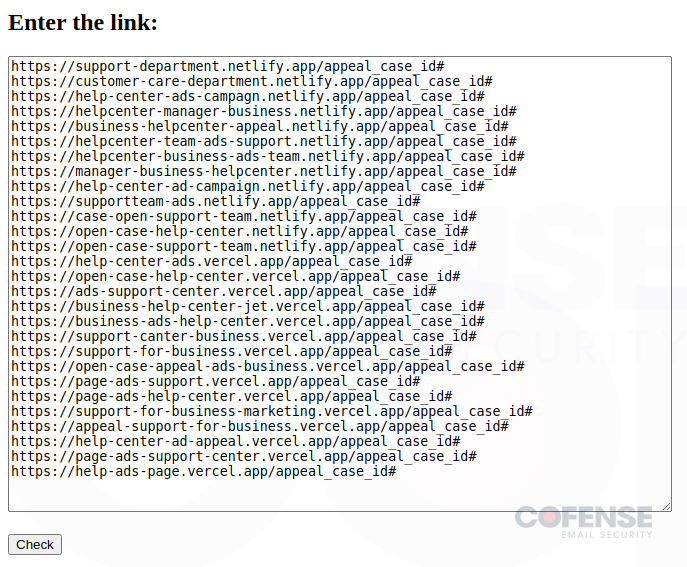

Figure 5: Threat actor tool to input malicious links to check if they’re active.
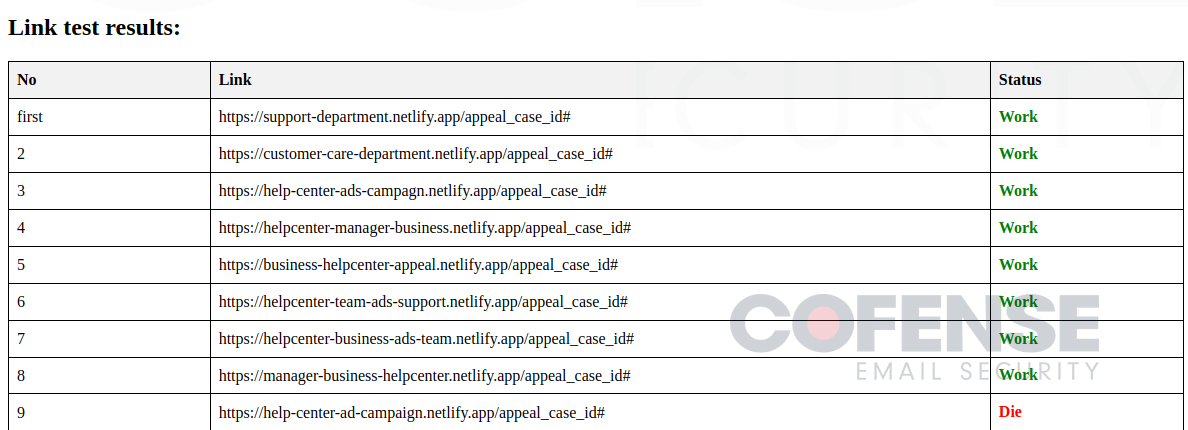

Figure 6: Results from the URL input showing if active or dead.
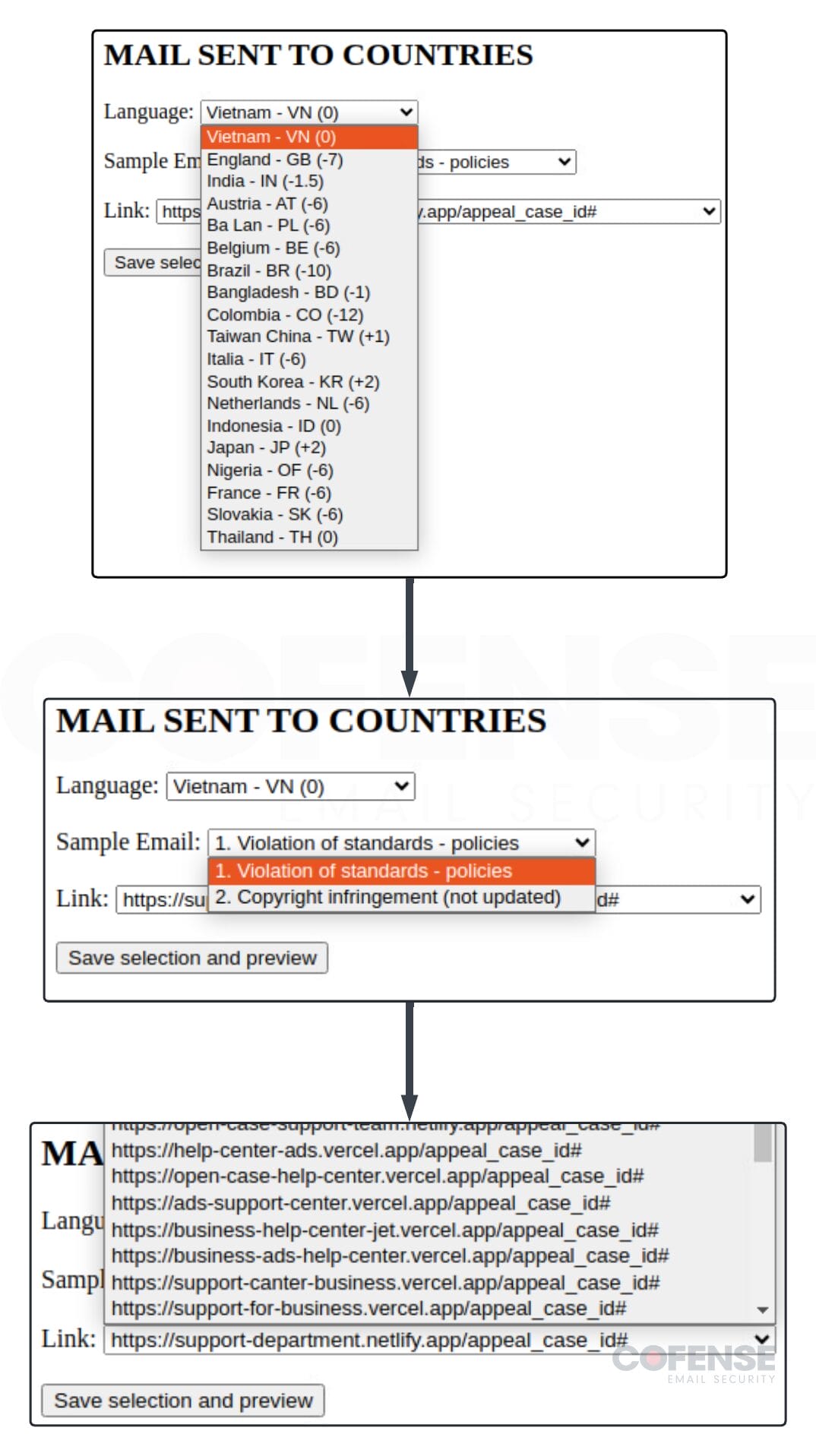

Figure 7: Threat actor tool to generate phishing emails for this campaign.
Meta Spoofing in the Threat Landscape
Cofense reports on a significant amount of credential phishing emails every day that were uncovered inside of an enterprise user’s inbox. Of those emails, Meta is the second most spoofed brand seen in the first quarter of 2024. Out of the campaigns spoofing Meta, emails from this campaign make up a good portion of the volume. Figure 8 below shows the top 5 brands spoofed in Credential Phishing campaigns seen by Cofense in Q1 of this year. Meta follows behind Microsoft, which is well-known for being spoofed in a high percentage of phishing emails due to the popular use of Microsoft email services.
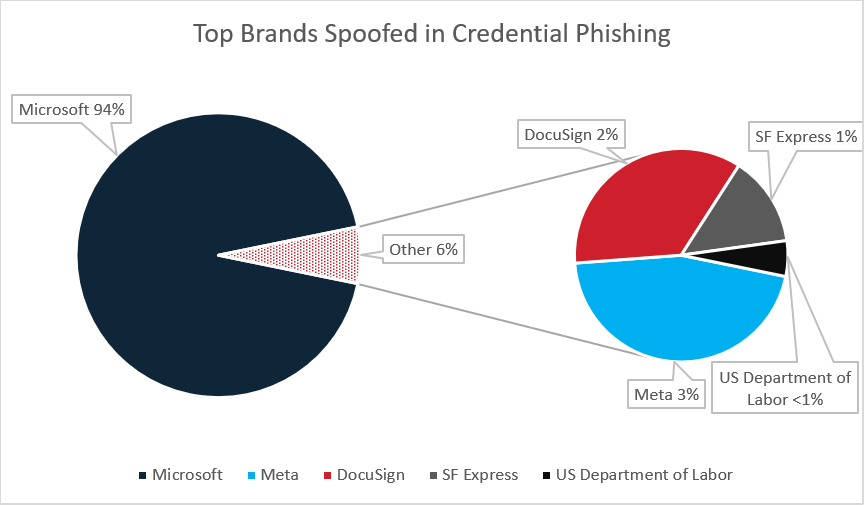

Figure 8: Top brands spoofed in Credential Phishing campaigns seen by Cofense in Q1 2024.
Source: https://cofense.com/blog/cyber-attack-that-targets-meta-business-accounts
“An interesting youtube video that may be related to the article above”