Threat Actor: Cvsp | Cvsp
Victim: Microsoft Outlook users | Microsoft Outlook
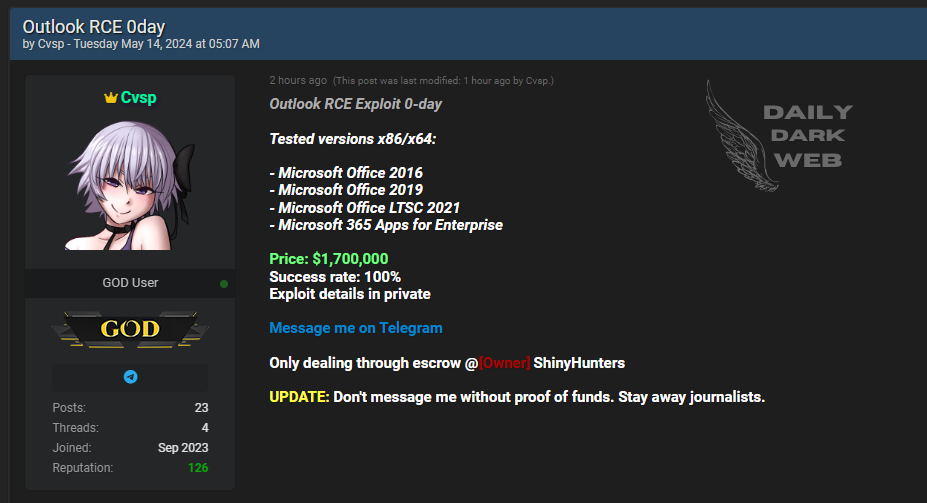
Price: $1,700,000
Exfiltrated Data Type: Not specified
Additional Information :
- The Outlook RCE exploit 0-day is designed to target various versions of Microsoft Office across both x86 and x64 architectures.
- The exploit has been tested on Office 2016, 2019, LTSC 2021, and Microsoft 365 Apps for Enterprise with a success rate of 100%.
- Specific information about the exploit will only be disclosed privately.
- All transactions related to the sale of the exploit are conducted exclusively through escrow services provided by ShinyHunters.
- The high price of $1,700,000 reflects the severity and potency of the exploit.
In a concerning development, a threat actor known as “Cvsp” has announced the sale of an alleged Outlook Remote Code Execution (RCE) exploit 0-day. This alleged exploit, designed to target various versions of Microsoft Office across both x86 and x64 architectures, poses a significant security threat to users worldwide.
According to Cvsp’s claims, the Outlook RCE Exploit 0-day has undergone rigorous testing on multiple versions of Microsoft Office software, including Office 2016, 2019, LTSC 2021, and Microsoft 365 Apps for Enterprise. The threat actor claims an alarming success rate of 100%, indicating the exploit’s reliability and effectiveness in compromising vulnerable systems.
The threat actor emphasizes that specific information regarding the exploit will only be disclosed privately. Additionally, all transactions related to the sale of the exploit are to be conducted exclusively through escrow services provided by ShinyHunters, underscoring the clandestine nature of the transaction and the illicit activities associated with the sale of such high-level vulnerabilities in the cyber underground.
The price for the Outlook RCE exploit 0-day is $1,700,000, as claimed by the threat actor, Cvsp. This substantial sum reflects the severity and potency of the exploit, which poses a significant threat to users.
Original Source: https://dailydarkweb.net/a-threat-actor-claims-sale-of-outlook-rce-exploit-0-day-for-1700000/