In a recent TLP:CLEAR publication the European Union Agency for Cybersecurity (ENISA) and CERT-EU warned about malicious activities against EU governments and businesses attributed to Chinese Advanced Persistent Threat (APT) groups. In contrast to other nation state-backed Threat Groups from e.g. North Korea, who seek to profit financially from cyber attacks, Chinese Threat Actors are motivated to conduct political and industrial espionage and establish long-term persistence. In this news bulletin we would like to inform you about the Chinese APT groups that are currently active and their respective tools and techniques.
APT27
This Threat Group, sometimes also referred to as “Lucky Mouse”, has been targeting foreign embassies and organizations to gather intelligence on political, defense and technology sectors for more than a decade. In addition to free/open-source and system tooling they employ Malware known from the China-Nexus like HyperBro and PlugX.
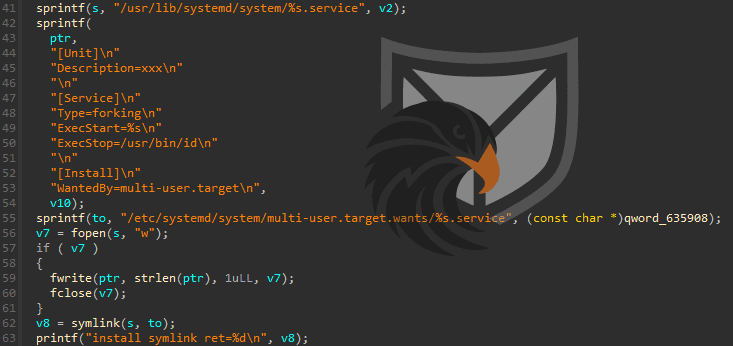
Another piece custom piece from their toolkit is a backdoor called “SysUpdate”. TrendMicro recently found that this previously Windows-only Malware is now also targeting Linux systems, as can be seen in Figure 1 below. SysUpdate’s features include information retrieval (Screenshots, System information), and different Execution options (Process/Service, File Manager, Remote Shell). A subset of samples also contains a feature to use Domain Resolution (DNS) traffic for its Command&Control communications.
APT31
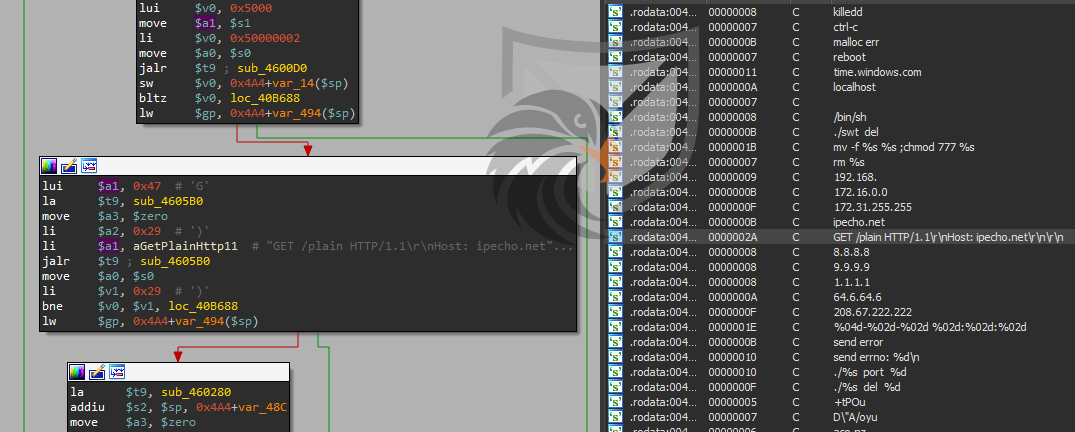
The activities of APT31 are, compared to other Chinese Threat Groups, more stealthy, less frequent and completely separate from other groups. They focus on exploitation of different software to gather political, economic and military intelligence. In 2021 researchers uncovered the so-called “SoWaT” backdoor, targeting Routers (MIPS architecture) in multiple western European countries. Figure 2 shows a screenshot of the analysis of the backdoor and contains a few hints on its functionality: manipulating router settings and receiving remote commands. The complexity of the Command&Control traffic handling and encryption shows that this backdoor was designed for covert deployment. A thorough analysis of the backdoor was conducted by imp0rtp3.
APT15
In recent reporting done by Palo Alto Networks Unit42 the APT15 Advanced Persistent Threat group was specifically targeting Iranian government infrastructure with a custom Windows backdoor called “Turian”, which was first spotted in 2021 by ESET. APT15’s tooling is comparable in sophistication with the other Threat groups in this article, but currently attributed campaigns show that their current focus is on countries in the Middle East, Africa and North/South America.
Mustang Panda
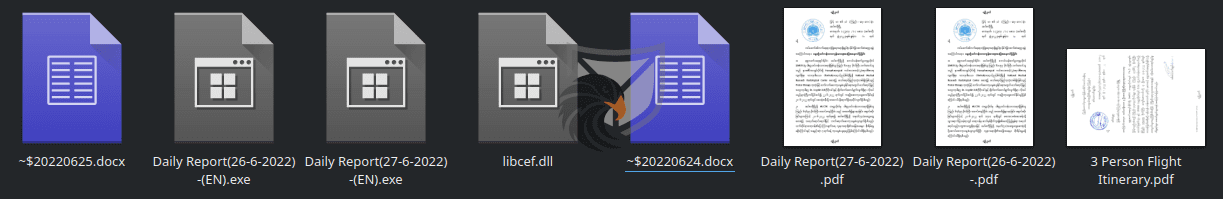
Mustang Panda’s activity dates back to at least 2017/2018, when they were first targeting Mongolia for intelligence gathering purposes. The Threat group is known for a somewhat more overt approach to compromising political targets, with their preferred tool being malicious office documents or document lures combined with (file-less) Malware, as can be seen in Figure 3. Another tool of choice for them are customized versions of PlugX/Korplug.
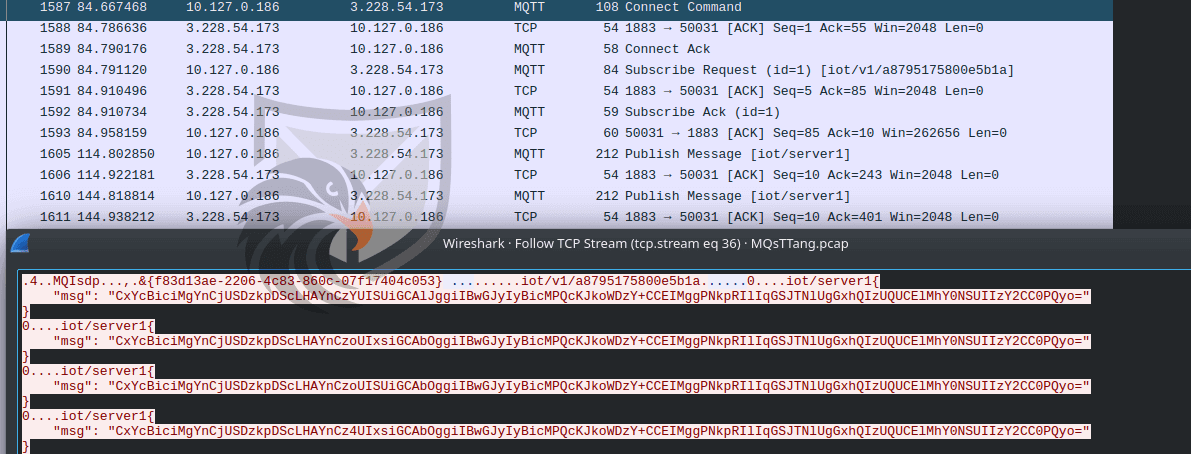
ESET recently discovered a new backdoor attributed to Mustang Panda which they named “MQsTTang” after the utilized MQTT Network protocol used for their Command&Control infrastructure (see Figure 4).
Detection and Response Measures
We second the measures proposed by CERT-EU and would like to highlight a few of them that will have a large impact on security posture of organizations in focused branches:
- Establishing Log collection and monitoring for security events on assets and networking equipment.
- Protection of assets (clients, servers) should be reinforced through the use of an Endpoint Detection & Response (EDR) solution and continuous monitoring.
- Manage vulnerabilities through a centralized system and keep up with patch cycles.
- Conduct regular assessments of your environment, either in an offensive (Pentests, Red-Teaming) or a defensive nature (Compromise Assessments).
- Prepare a thorough backup strategy and Incident Response plans and test them periodically.
- Create user awareness for possible malicious activity with e.g. Phishing simulation and targeted trainings.
Hashsums for the mentioned samples
APT27 – SysUpdate
e9c6e9aba10b5e26e578efc6105727d74fbd3a02450fbda2b4ee052b3fbbaecb
APT31 – SoWaT
1d60edb577641ce47dc2a8299f8b7f878e37120b192655aaf80d1cde5ee482d2
MustangPanda
RAR – 447a62c7e29e2da85884b6e4aea80aca2cc5ba86694733ca397a2c8ba0f8e197
MQsTTang backdoor – 4936b873cfe066ec5efce01ef8fb1605f8bc29a98408a13bc8fe4462b2f09c5a