
This post is also available in:
日本語 (Japanese)
Executive Summary
Earlier this month, our quiz Crossing the Line: Unit 42 Wireshark Quiz for RedLine Stealer introduced a packet capture (pcap) from July 2023 with a RedLine Stealer infection. This article provides answers to the quiz, and it offers a more in-depth look at RedLine Stealer traffic.
If you would like to review this material without any answers, please see our previous post announcing the standalone quiz.
Palo Alto Networks customers are protected from RedLine Stealer and other malware through Cortex XDR and our Next-Generation Firewall with Cloud-Delivered Security Services that include WildFire and Advanced Threat Prevention.
Table of Contents
Scenario, Requirements and Quiz Material
Local Area Network (LAN) Details
Quiz Questions
Quiz Answers
Pcap Analysis: Victim Details
Pcap Analysis: Malicious Web Traffic
Pcap Analysis: RedLine Stealer Data Exfiltration
Conclusion
Indicators of Compromise
Additional Resources
Scenario, Requirements and Quiz Material
Traffic for this quiz occurred in an Active Directory (AD) environment during July 2023. Details of the Local Area Network (LAN) environment for the pcap follow.
Local Area Network (LAN) Details
- LAN segment range: 10.7.10[.]0/24 (10.7.10[.]1 through 10.7.10[.]255)
- Domain: coolweathercoat[.]com
- Domain controller IP address: 10.7.10[.]9
- Domain controller hostname: WIN-S3WT6LGQFVX
- LAN segment gateway: 10.7.10[.]1
- LAN segment broadcast address: 10.7.10[.]255
This quiz requires Wireshark, and we recommend using the latest version, since it has more features, capabilities and bug fixes over previous versions.
We also recommend readers customize their Wireshark display to better analyze web traffic. A list of tutorials and videos is available. As always, we recommend using Wireshark in a non-Windows environment like BSD, Linux or macOS when analyzing malicious Windows-based traffic.
To obtain the pcap, visit our GitHub repository, download the July 2023 ZIP archive and extract the pcap. Use infected as the password to unlock the ZIP archive.
Quiz Questions
For this RedLine Stealer infection, we ask participants to answer the following questions previously described in our standalone quiz post.
- What is the date and time in UTC the infection started?
- What is the IP address of the infected Windows client?
- What is the MAC address of the infected Windows client?
- What is the hostname of the infected Windows client?
- What is the user account name from the infected Windows host?
- What type of information did this RedLine Stealer try to steal?
Quiz Answers
Answers for this Wireshark quiz follow:
- The infection started on July 10, 2023, at 22:39 UTC.
- Infected Windows client IP address: 10.7.10[.]47
- Infected Windows client MAC address: 80:86:5b:ab:1e:c4
- Infected Windows hostname: DESKTOP-9PEA63H
- Infected Windows client IP user account name: rwalters
- Information RedLine malware attempted to steal:
- Various types of files on the victim’s desktop
- Various types of files in the victim’s Documents folder
- User data for Chrome, Chromium, Edge, Opera, Vivaldi and various other web browsers
- Data for various cryptocurrency wallets and browser plugins for those cryptocurrency wallets
- API keys and login credentials from other applications
Pcap Analysis: Victim Details
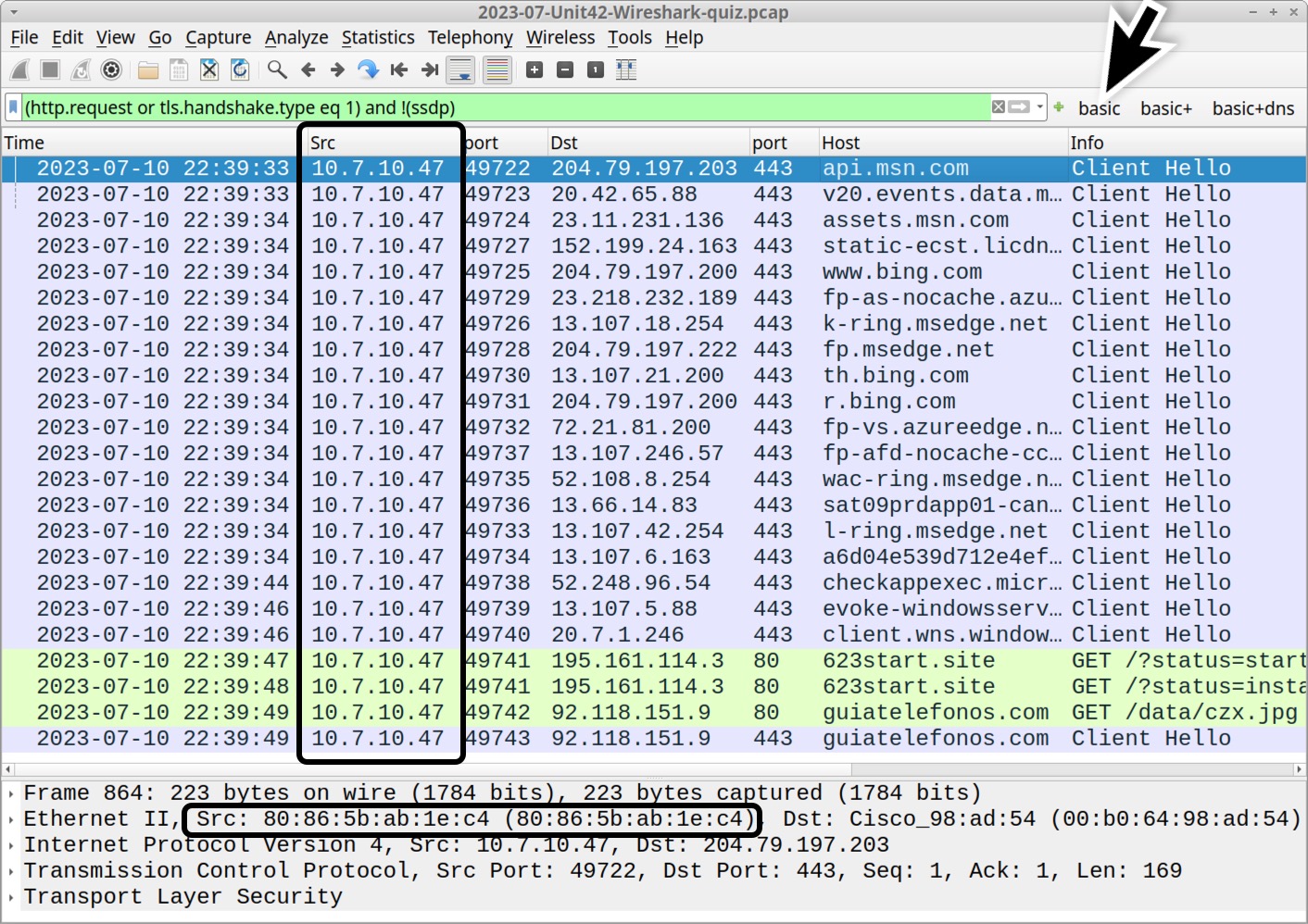
The following analysis uses Wireshark customized from our tutorials. Applying the basic web filter reveals a single internal IP address at 10.7.10[.]47 as the only source IP address, as shown below in Figure 1. Using the frame details, we can correlate this source IP with a MAC address at 80:86:5b:ab:1e:c4.
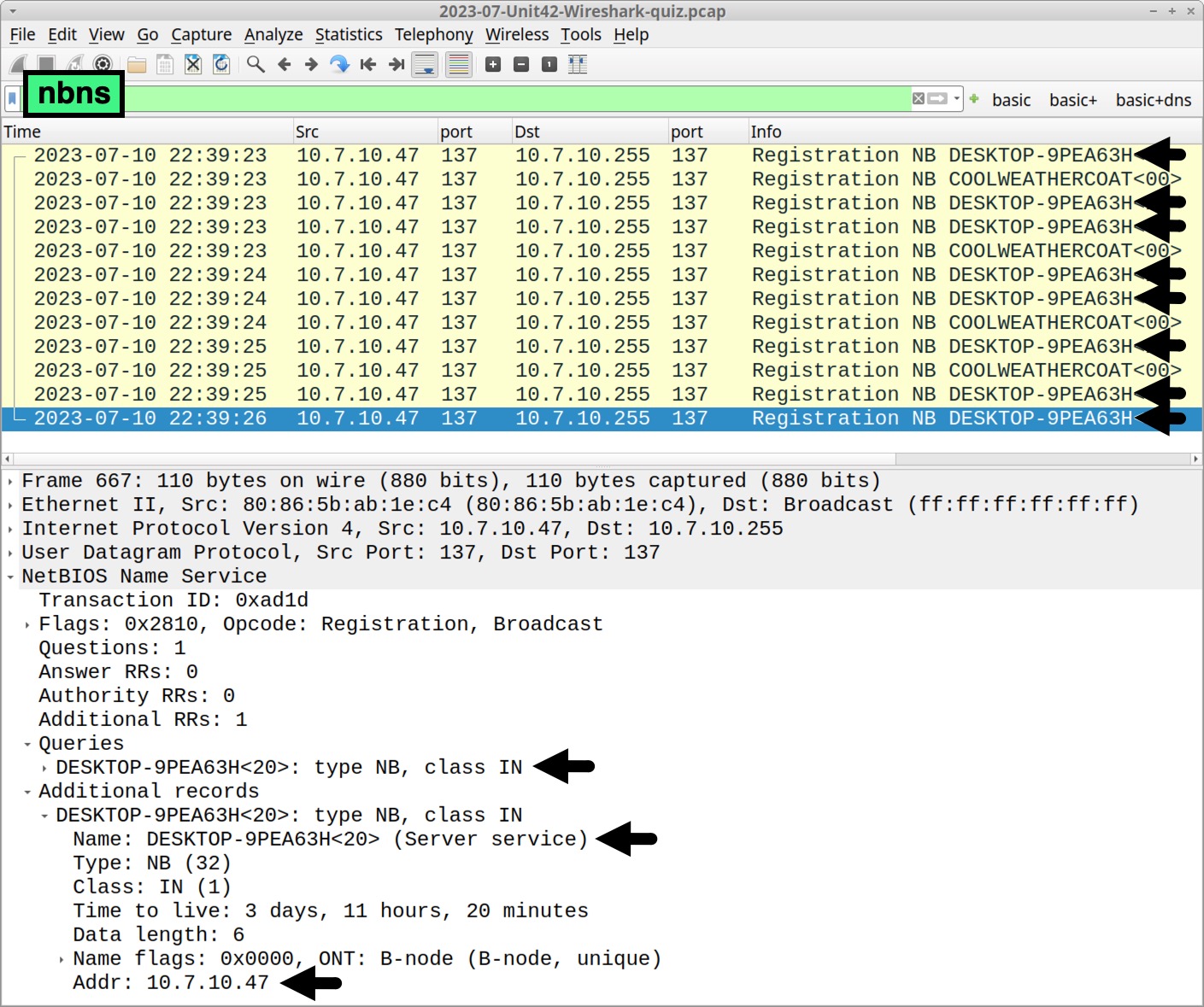
Determine the victim’s hostname by filtering on NetBIOS Name Service (NBNS) traffic. Use the Wireshark filter nbns to find DESKTOP-9PEA63H, as shown below in Figure 2.
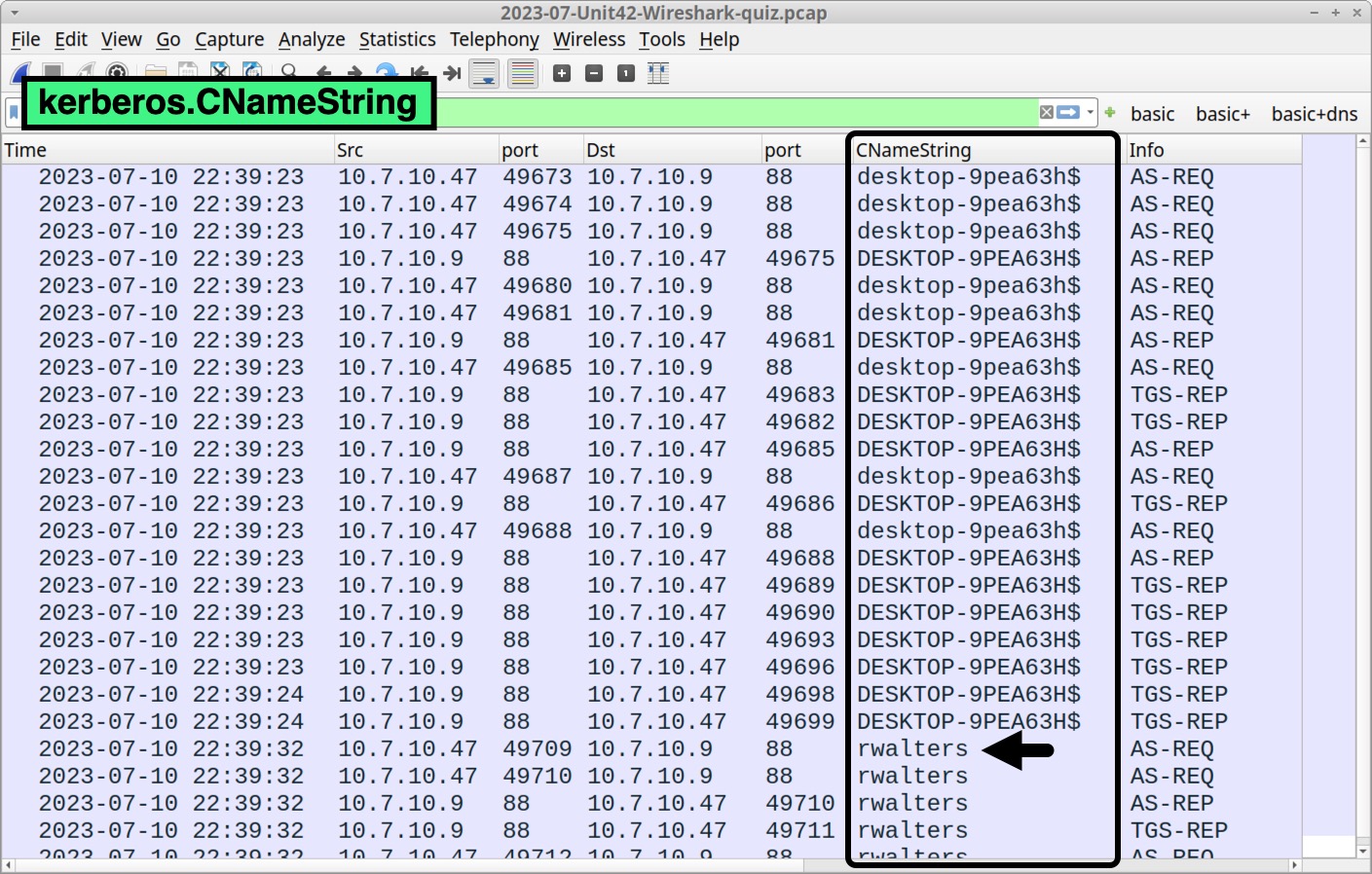
Verify the victim’s hostname and Windows user account name through Kerberos authentication traffic. Filter on kerberos.CNameString to find the Windows user account name rwalters, as shown below in Figure 3.
Pcap Analysis: Malicious Web Traffic
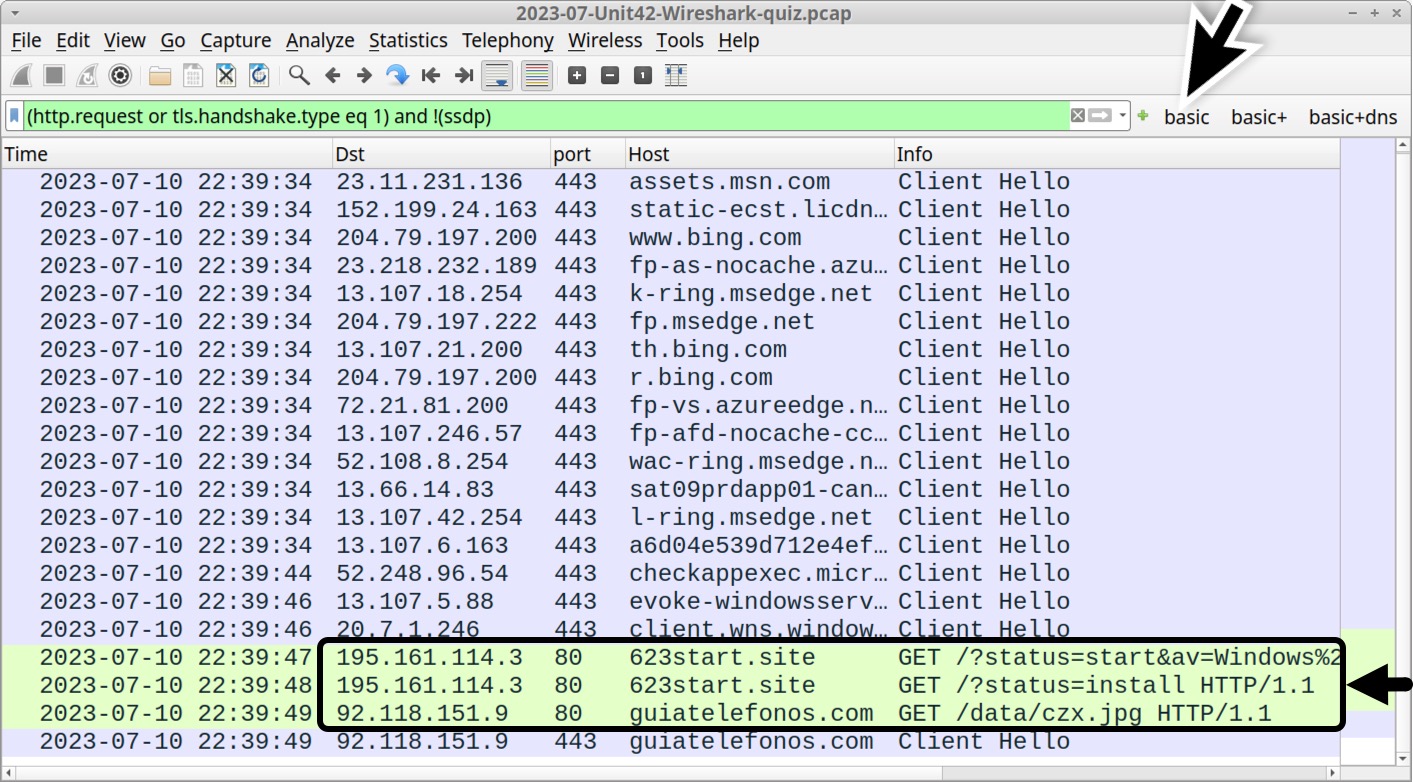
Go back to the basic web filter to find three unencrypted HTTP GET requests in our pcap as shown below in Figure 4. Two of the GET requests are to 623start[.]site. The other GET request is a URL to hxxp://guiatelefonos[.]com/data/czx.jpg.
Unencrypted HTTP GET requests not caused by the operating system are worth investigating. Follow the TCP stream for either of the HTTP GET requests to 623start[.]site. This should appear as TCP stream 68, and the User-Agent line in the HTTP request headers indicate this traffic was issued through Windows PowerShell as shown below in Figure 5.
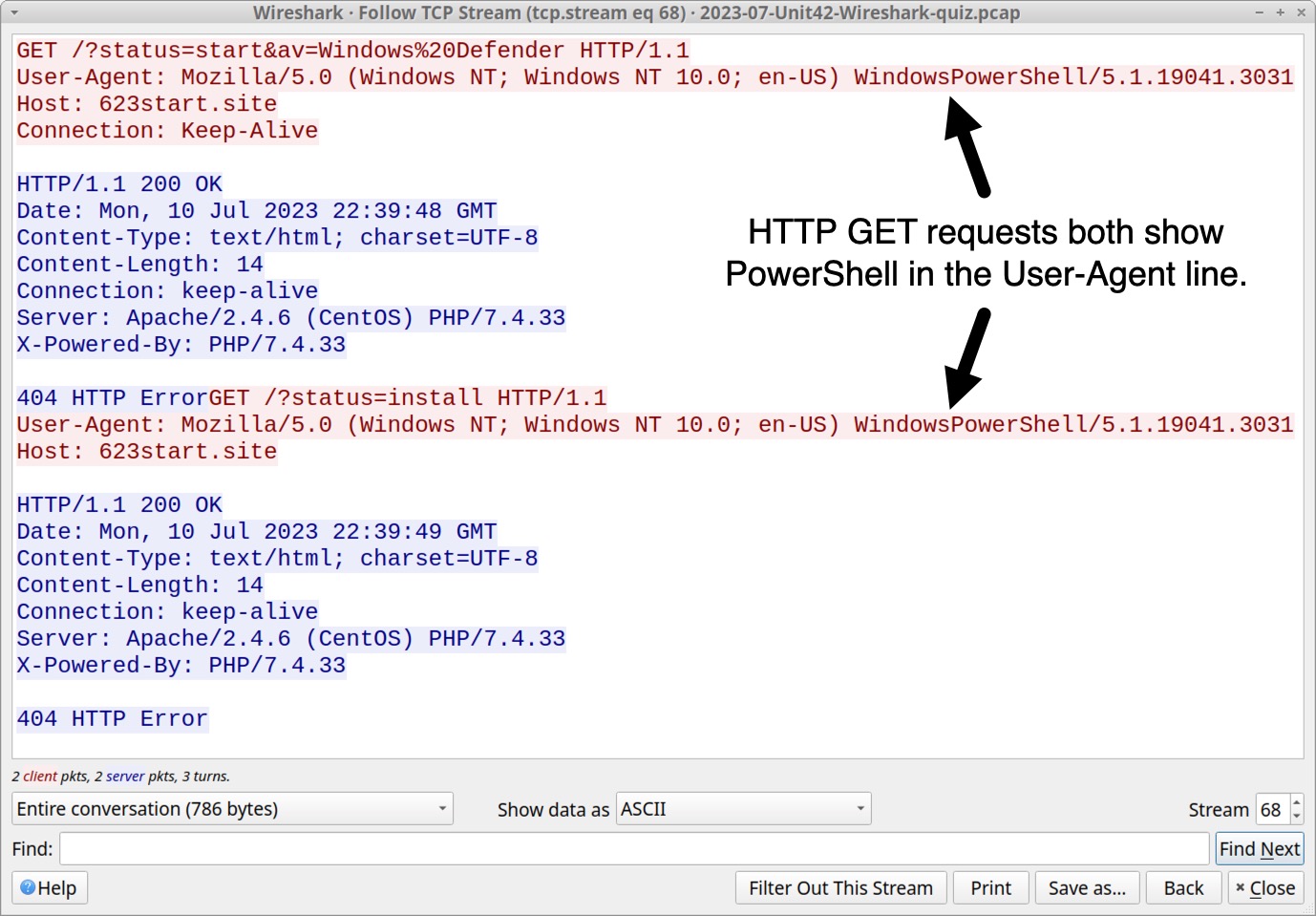
While User-Agent strings can be spoofed by malware or web browser extensions, WindowsPowerShell in the User-Agent line is a reliable indicator that this traffic was generated by a PowerShell script. URLs for these two HTTP GET requests are:
- hxxp://623start[.]site/?status=start&av=Windows%20Defender
- hxxp://623start[.]site/?status=install
These requests both returned a 404 HTTP Error from the server. The first HTTP request reported an antivirus used on the victim host. In this case, av=Windows%20Defender indicates Windows Defender is the antivirus. The second URL reports an install status for this malware.
In our pcap, the last unencrypted HTTP GET request is hxxp://guiatelefonos[.]com/data/czx.jpg. Follow the TCP stream for this GET request. The TCP stream reveals this URL redirected to an HTTPS version of the same URL as shown below in Figure 6.
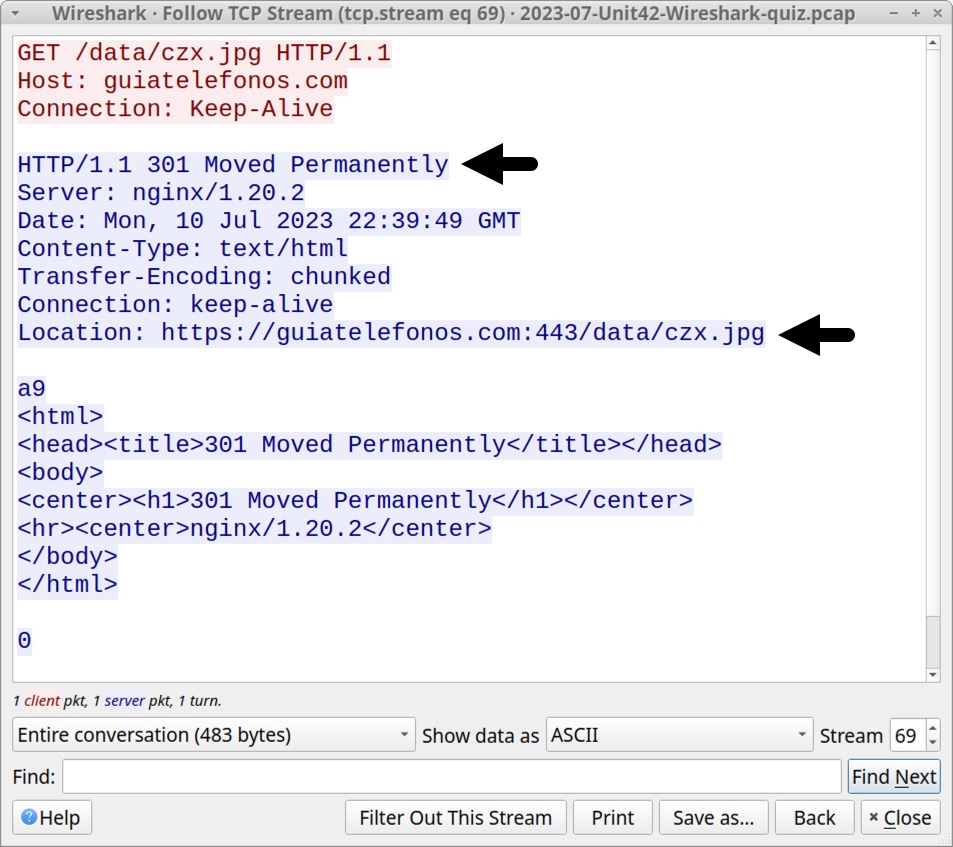
hxxps://guiatelefonos[.]com/data/czx.jpg has been reported to URLhaus as hosting a RedLine Stealer malware binary, and this specific RedLine Stealer malware binary is associated with the URL.
Pcap Analysis: RedLine Stealer Data Exfiltration
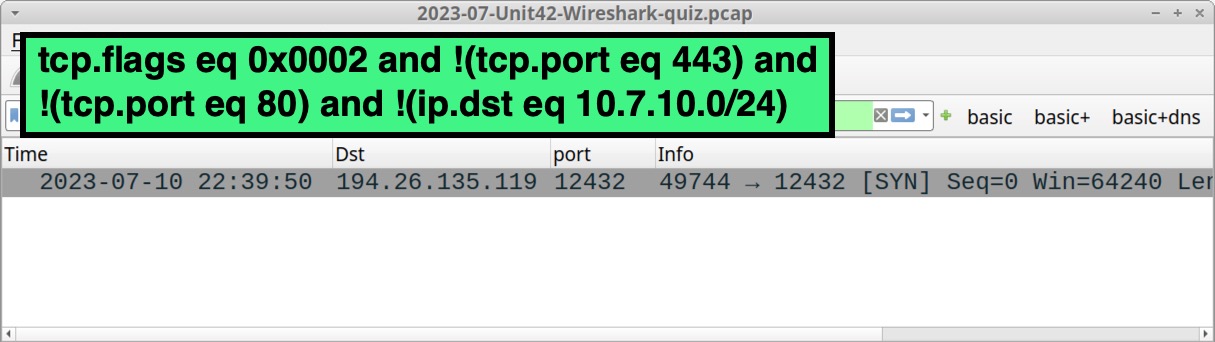
Command and Control (C2) traffic for RedLine Stealer uses TCP traffic over an ephemeral port. To find this traffic in our pcap, use the following Wireshark filter:
tcp.flags eq 0x0002 and !(tcp.port eq 443) and !(tcp.port eq 80) and !(ip.dst eq 10.7.10.0/24)
This filter searches for TCP SYN segments that represent the start of a TCP stream. The search excludes any web traffic over TCP port 80 and TCP port 443. This filter also excludes any SYN segments sent to the internal IP addresses from this AD environment. The result reveals a single TCP SYN segment sent to 194.26.135[.]119 over TCP port 12432 as shown below in Figure 7.
Follow the TCP stream to examine post-infection traffic from this RedLine Stealer infection. The window should show TCP stream 71 as shown below in Figure 8.
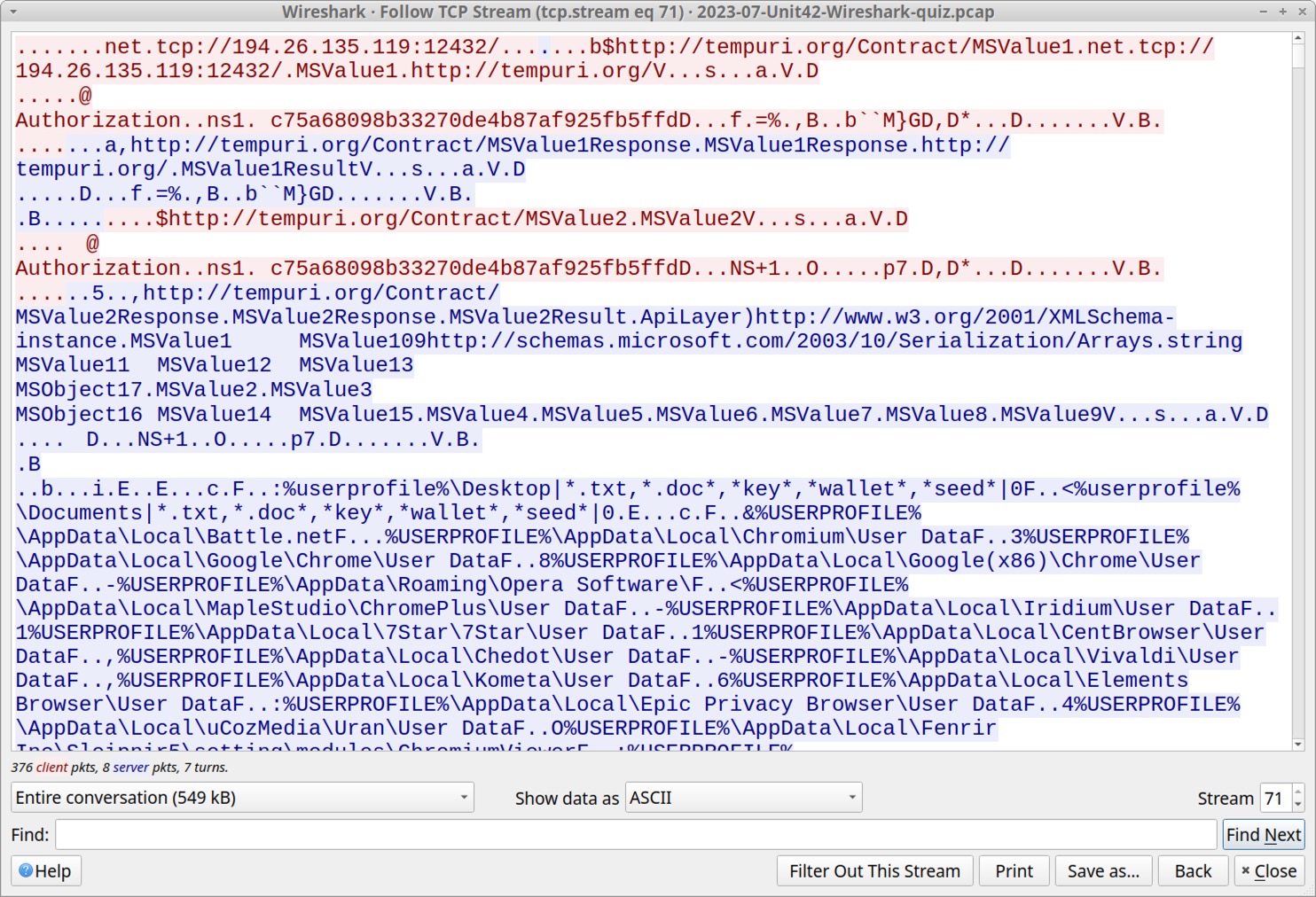
In Figure 8, initial strings from the TCP stream include the C2 channel at tcp://194.26.135[.]119:12432/ and URLs using tempuri[.]org. The term “tempuri” is short for “temporary URI,” and the domain tempuri[.]org is a placeholder namespace URI used in Microsoft development tools like Visual Studio. This tempuri domain is not seen in any other traffic from our RedLine Stealer infection.
To better understand what this RedLine Stealer sample is looking for, select data sent from the server to the infected Windows host as shown below in Figure 9.
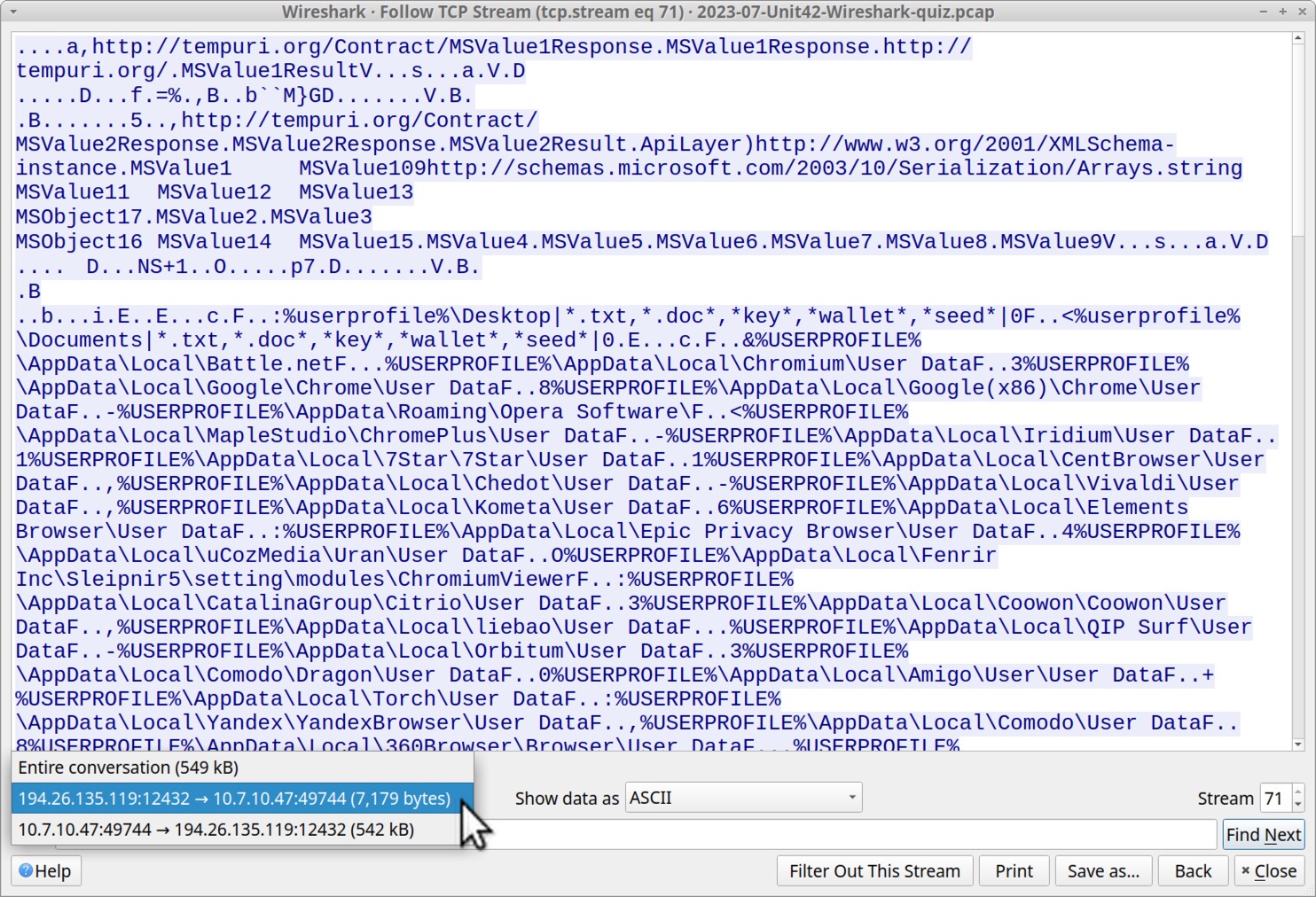
Data from the RedLine C2 server is requesting various types of user information from the victim’s host. Figure 10 highlights data this infection is looking for under the victim’s user profile.
The list includes wildcard searches on the victim’s desktop and the victim’s Documents folder. This includes text files, Word documents and cryptocurrency wallet files as shown below.
- %userprofile%Desktop|*.txt,*.doc*,*key*,*wallet*,*seed*|0
- %userprofile%Documents|*.txt,*.doc*,*key*,*wallet*,*seed*|0
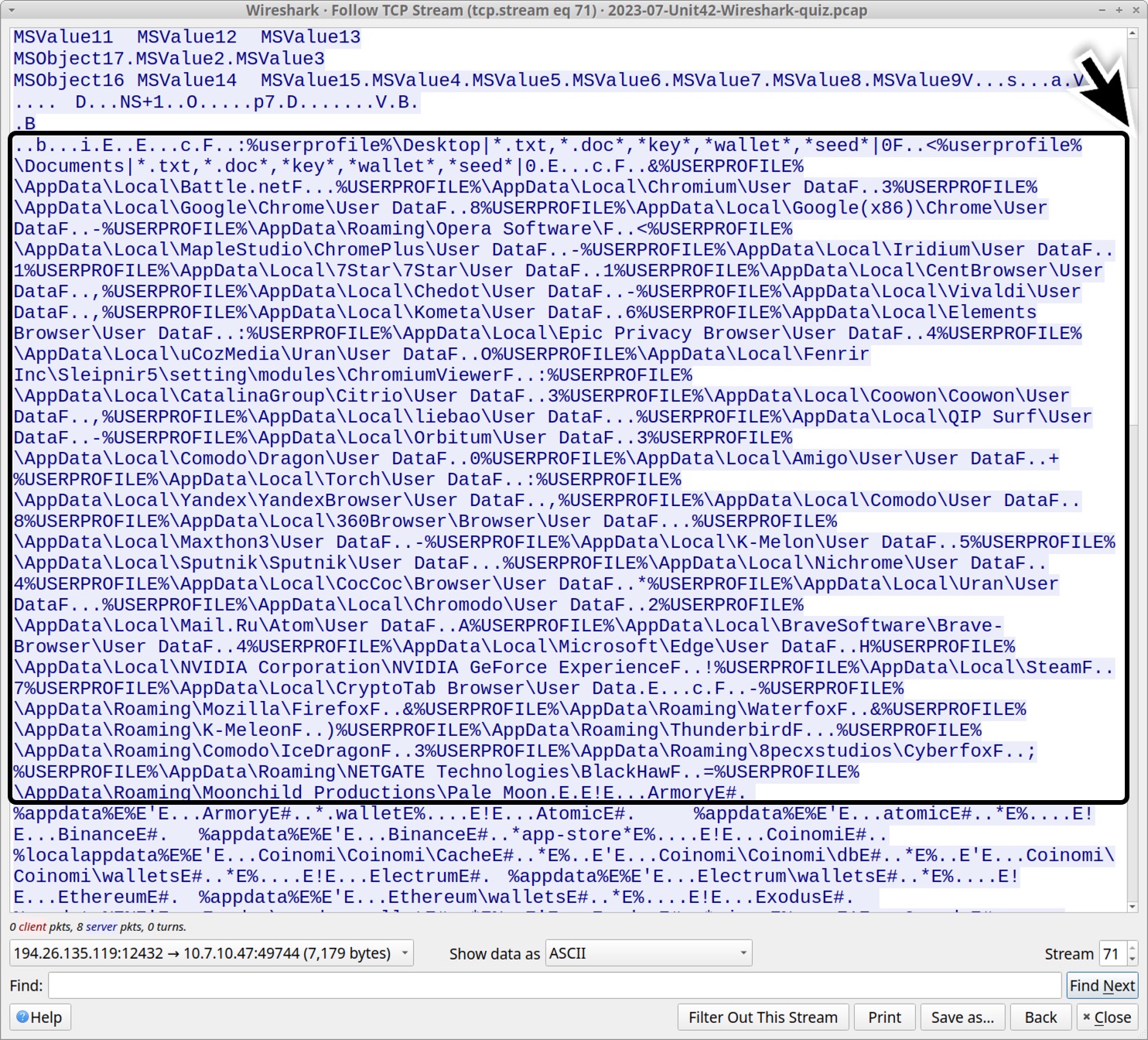
The list then indicates data from different applications, based on their expected locations under the victim’s AppData directory in their user profile. The list is shown below in alphabetical order.
- %USERPROFILE%AppDataLocal360BrowserBrowserUser Data
- %USERPROFILE%AppDataLocal7Star7StarUser Data
- %USERPROFILE%AppDataLocalAmigoUserUser Data
- %USERPROFILE%AppDataLocalBattle.net
- %USERPROFILE%AppDataLocalBraveSoftwareBrave-BrowserUser Data
- %USERPROFILE%AppDataLocalCatalinaGroupCitrioUser Data
- %USERPROFILE%AppDataLocalCentBrowserUser Data
- %USERPROFILE%AppDataLocalChedotUser Data
- %USERPROFILE%AppDataLocalChromiumUser Data
- %USERPROFILE%AppDataLocalChromodoUser Data
- %USERPROFILE%AppDataLocalCocCocBrowserUser Data
- %USERPROFILE%AppDataLocalComodoDragonUser Data
- %USERPROFILE%AppDataLocalComodoUser Data
- %USERPROFILE%AppDataLocalCoowonCoowonUser Data
- %USERPROFILE%AppDataLocalCryptoTab BrowserUser Data
- %USERPROFILE%AppDataLocalElements BrowserUser Data
- %USERPROFILE%AppDataLocalEpic Privacy BrowserUser Data
- %USERPROFILE%AppDataLocalFenrir IncSleipnir5settingmodulesChromiumViewer
- %USERPROFILE%AppDataLocalGoogle(x86)ChromeUser Data
- %USERPROFILE%AppDataLocalGoogleChromeUser Data
- %USERPROFILE%AppDataLocalIridiumUser Data
- %USERPROFILE%AppDataLocalK-MelonUser Data
- %USERPROFILE%AppDataLocalKometaUser Data
- %USERPROFILE%AppDataLocalliebaoUser Data
- %USERPROFILE%AppDataLocalMail.RuAtomUser Data
- %USERPROFILE%AppDataLocalMapleStudioChromePlusUser Data
- %USERPROFILE%AppDataLocalMaxthon3User Data
- %USERPROFILE%AppDataLocalMicrosoftEdgeUser Data
- %USERPROFILE%AppDataLocalNichromeUser Data
- %USERPROFILE%AppDataLocalNVIDIA CorporationNVIDIA GeForce Experience
- %USERPROFILE%AppDataLocalOrbitumUser Data
- %USERPROFILE%AppDataLocalQIP SurfUser Data
- %USERPROFILE%AppDataLocalSputnikSputnikUser Data
- %USERPROFILE%AppDataLocalSteam
- %USERPROFILE%AppDataLocalTorchUser Data
- %USERPROFILE%AppDataLocaluCozMediaUranUser Data
- %USERPROFILE%AppDataLocalUranUser Data
- %USERPROFILE%AppDataLocalVivaldiUser Data
- %USERPROFILE%AppDataLocalYandexYandexBrowserUser Data
- %USERPROFILE%AppDataRoaming8pecxstudiosCyberfox
- %USERPROFILE%AppDataRoamingComodoIceDragon
- %USERPROFILE%AppDataRoamingK-Meleon
- %USERPROFILE%AppDataRoamingMoonchild ProductionsPale Moon
- %USERPROFILE%AppDataRoamingMozillaFirefox
- %USERPROFILE%AppDataRoamingNETGATE TechnologiesBlackHaw
- %USERPROFILE%AppDataRoamingOpera Software
- %USERPROFILE%AppDataRoamingThunderbird
- %USERPROFILE%AppDataRoamingWaterfox
Scroll down a little further, and we find what appears to be various cryptocurrency wallets this infection looked for as shown below in Figure 11. The data includes identifiers for extensions used by Chromium-based web browsers like Google Chrome and Microsoft Edge.
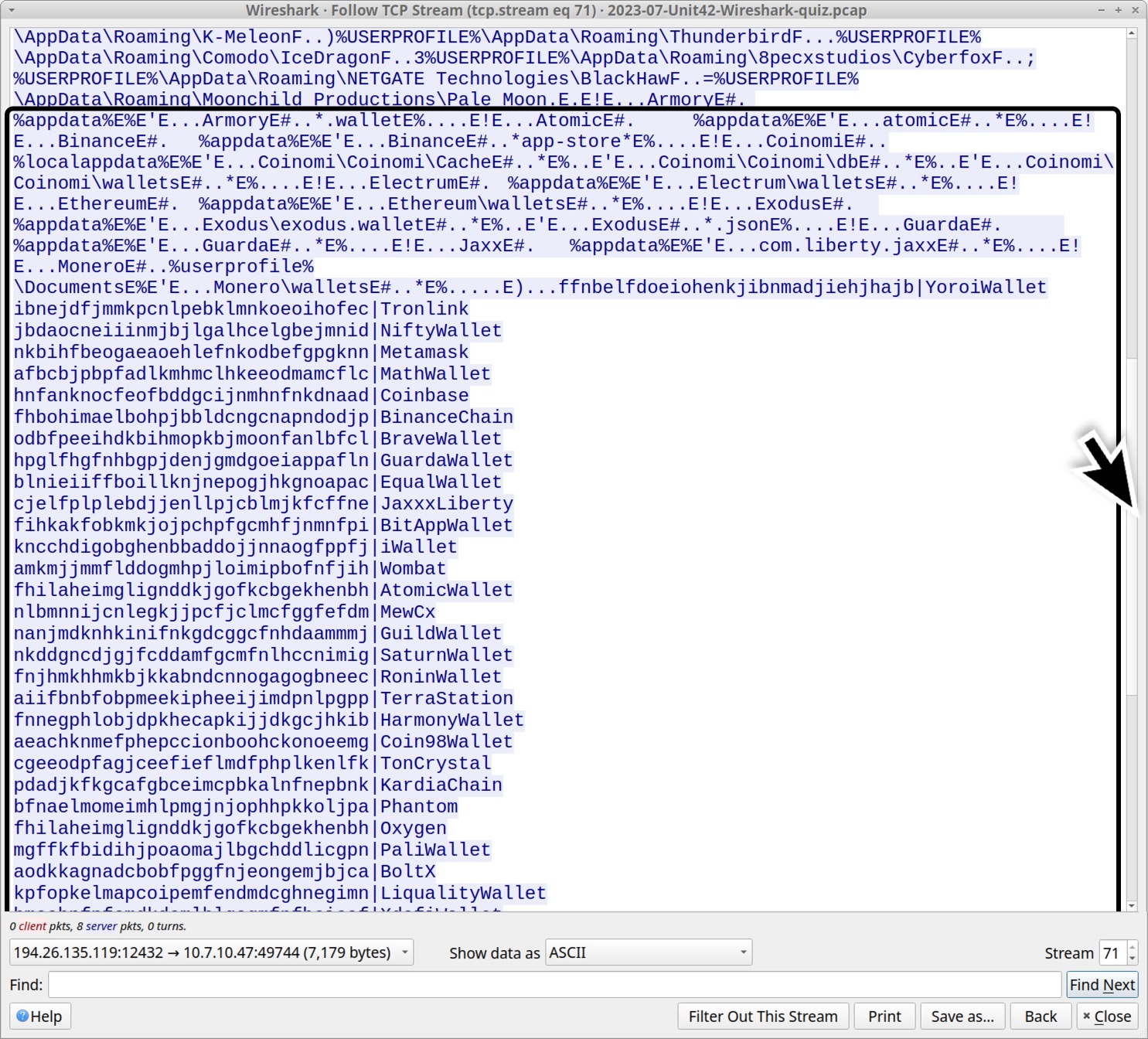
These cryptocurrency wallet browser extensions are listed below, sorted alphabetically by wallet name. (Read: Chromium-based extension string|extension name.)
- fhilaheimglignddkjgofkcbgekhenbh|AtomicWallet
- fhbohimaelbohpjbbldcngcnapndodjp|BinanceChain
- fihkakfobkmkjojpchpfgcmhfjnmnfpi|BitAppWallet
- aodkkagnadcbobfpggfnjeongemjbjca|BoltX
- odbfpeeihdkbihmopkbjmoonfanlbfcl|BraveWallet
- aeachknmefphepccionboohckonoeemg|Coin98Wallet
- hnfanknocfeofbddgcijnmhnfnkdnaad|Coinbase
- blnieiiffboillknjnepogjhkgnoapac|EqualWallet
- hpglfhgfnhbgpjdenjgmdgoeiappafln|GuardaWallet
- nanjmdknhkinifnkgdcggcfnhdaammmj|GuildWallet
- fnnegphlobjdpkhecapkijjdkgcjhkib|HarmonyWallet
- kncchdigobghenbbaddojjnnaogfppfj|iWallet
- cjelfplplebdjjenllpjcblmjkfcffne|JaxxxLiberty
- pdadjkfkgcafgbceimcpbkalnfnepbnk|KardiaChain
- kpfopkelmapcoipemfendmdcghnegimn|LiqualityWallet
- dngmlblcodfobpdpecaadgfbcggfjfnm|MaiarDeFiWallet
- afbcbjpbpfadlkmhmclhkeeodmamcflc|MathWallet
- nkbihfbeogaeaoehlefnkodbefgpgknn|Metamask
- nlbmnnijcnlegkjjpcfjclmcfggfefdm|MewCx
- lpfcbjknijpeeillifnkikgncikgfhdo|NamiWallet
- jbdaocneiiinmjbjlgalhcelgbejmnid|NiftyWallet
- fhilaheimglignddkjgofkcbgekhenbh|Oxygen
- mgffkfbidihjpoaomajlbgchddlicgpn|PaliWallet
- bfnaelmomeimhlpmgjnjophhpkkoljpa|Phantom
- fnjhmkhhmkbjkkabndcnnogagogbneec|RoninWallet
- nkddgncdjgjfcddamfgcmfnlhccnimig|SaturnWallet
- aiifbnbfobpmeekipheeijimdpnlpgpp|TerraStation
- cgeeodpfagjceefieflmdfphplkenlfk|TonCrystal
- ibnejdfjmmkpcnlpebklmnkoeoihofec|Tronlink
- amkmjjmmflddogmhpjloimipbofnfjih|Wombat
- hmeobnfnfcmdkdcmlblgagmfpfboieaf|XdefiWallet
- ffnbelfdoeiohenkjibnmadjiehjhajb|YoroiWallet
Scroll to the end of the stream, and we find this infection searches for API keys and login data for other programs that might be installed on the host as shown below in Figure 12.
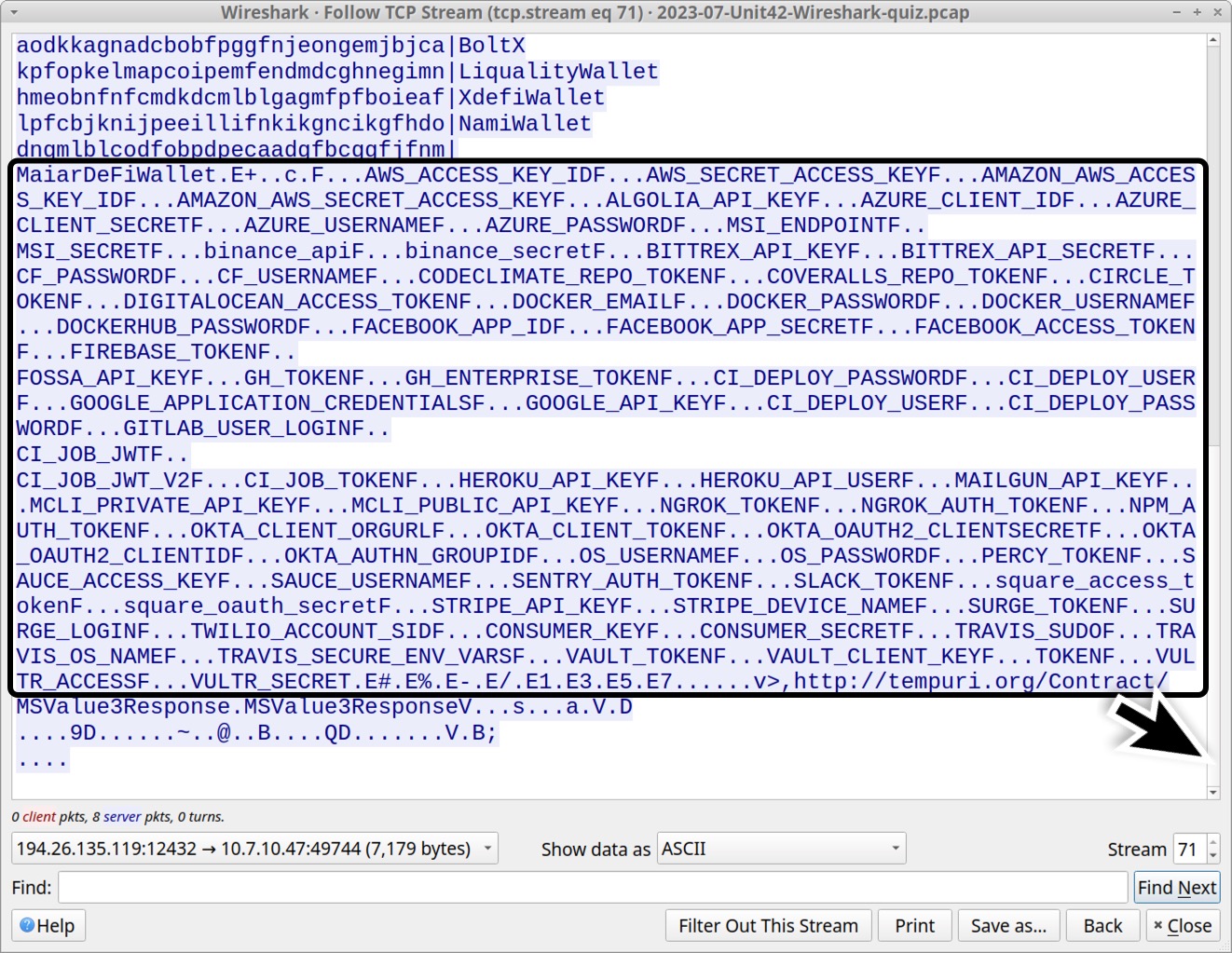
This list includes various cloud platforms, social media applications, and miscellaneous tools. An alphabetically-sorted list follows.
- ALGOLIA_API_KEY
- AMAZON_AWS_ACCESS_KEY_ID
- AMAZON_AWS_SECRET_ACCESS_KEY
- AWS_ACCESS_KEY_ID
- AWS_SECRET_ACCESS_KEY
- AZURE_CLIENT_ID
- AZURE_CLIENT_SECRET
- AZURE_PASSWORD
- AZURE_USERNAME
- binance_api
- binance_secret
- BITTREX_API_KEY
- BITTREX_API_SECRET
- CF_PASSWORD
- CF_USERNAME
- CI_DEPLOY_PASSWORD
- CI_DEPLOY_PASSWORD
- CI_DEPLOY_USER
- CI_DEPLOY_USER
- CI_JOB_JWT
- CI_JOB_JWT_V2
- CI_JOB_TOKEN
- CIRCLE_TOKEN
- CODECLIMATE_REPO_TOKEN
- CONSUMER_KEY
- CONSUMER_SECRET
- COVERALLS_REPO_TOKEN
- DIGITALOCEAN_ACCESS_TOKEN
- DOCKER_EMAIL
- DOCKER_PASSWORD
- DOCKER_USERNAME
- DOCKERHUB_PASSWORD
- FACEBOOK_ACCESS_TOKEN
- FACEBOOK_APP_ID
- FACEBOOK_APP_SECRET
- FIREBASE_TOKEN
- FOSSA_API_KEY
- GH_ENTERPRISE_TOKEN
- GH_TOKEN
- GITLAB_USER_LOGIN
- GOOGLE_API_KEY
- GOOGLE_APPLICATION_CREDENTIALS
- HEROKU_API_KEY
- HEROKU_API_USER
- MAILGUN_API_KEY
- MCLI_PRIVATE_API_KEY
- MCLI_PUBLIC_API_KEY
- MSI_ENDPOINT
- MSI_SECRET
- NGROK_AUTH_TOKEN
- NGROK_TOKEN
- NPM_AUTH_TOKEN
- OKTA_AUTHN_GROUPID
- OKTA_CLIENT_ORGURL
- OKTA_CLIENT_TOKEN
- OKTA_OAUTH2_CLIENTID
- OKTA_OAUTH2_CLIENTSECRET
- OS_PASSWORD
- OS_USERNAME
- PERCY_TOKEN
- SAUCE_ACCESS_KEY
- SAUCE_USERNAME
- SENTRY_AUTH_TOKEN
- SLACK_TOKEN
- square_access_token
- square_oauth_secret
- STRIPE_API_KEY
- STRIPE_DEVICE_NAME
- SURGE_LOGIN
- SURGE_TOKEN
- TOKEN
- TRAVIS_OS_NAME
- TRAVIS_SECURE_ENV_VARS
- TRAVIS_SUDO
- TWILIO_ACCOUNT_SID
- VAULT_CLIENT_KEY
- VAULT_TOKEN
- VULTR_ACCESS
- VULTR_SECRET
Next, switch the TCP stream window to view data sent from the infected host to the server. This reveals indicators that a screenshot of the infected victim’s Windows desktop was sent to the C2 server as shown below in Figure 13.
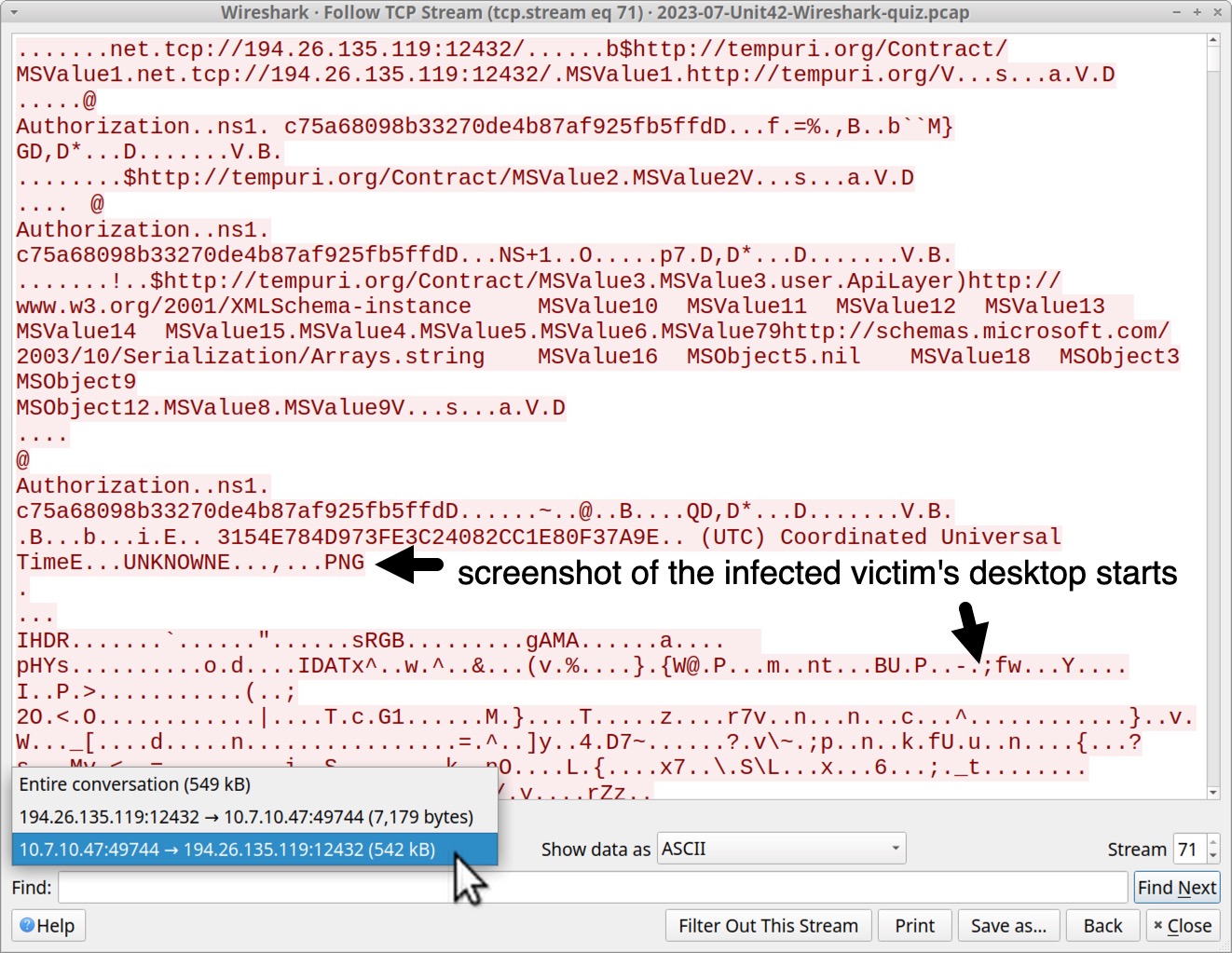
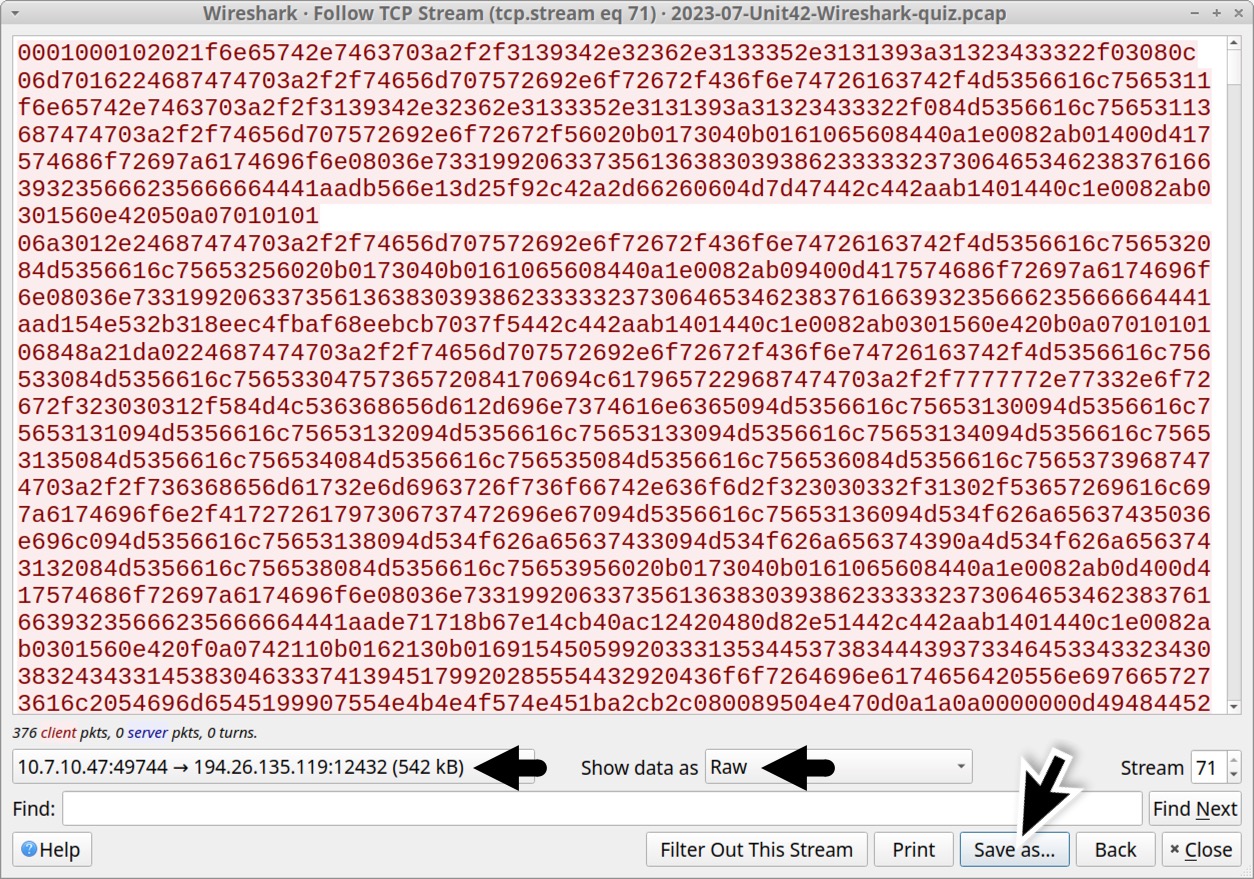
We can extract the screenshot from this traffic. First, show the data from the infected Windows host to the C2 server as “Raw,” then save it, as shown below in Figure 14.
Open the saved binary in a hex editor, and delete everything before the PNG image file starts as shown below in Figure 15.
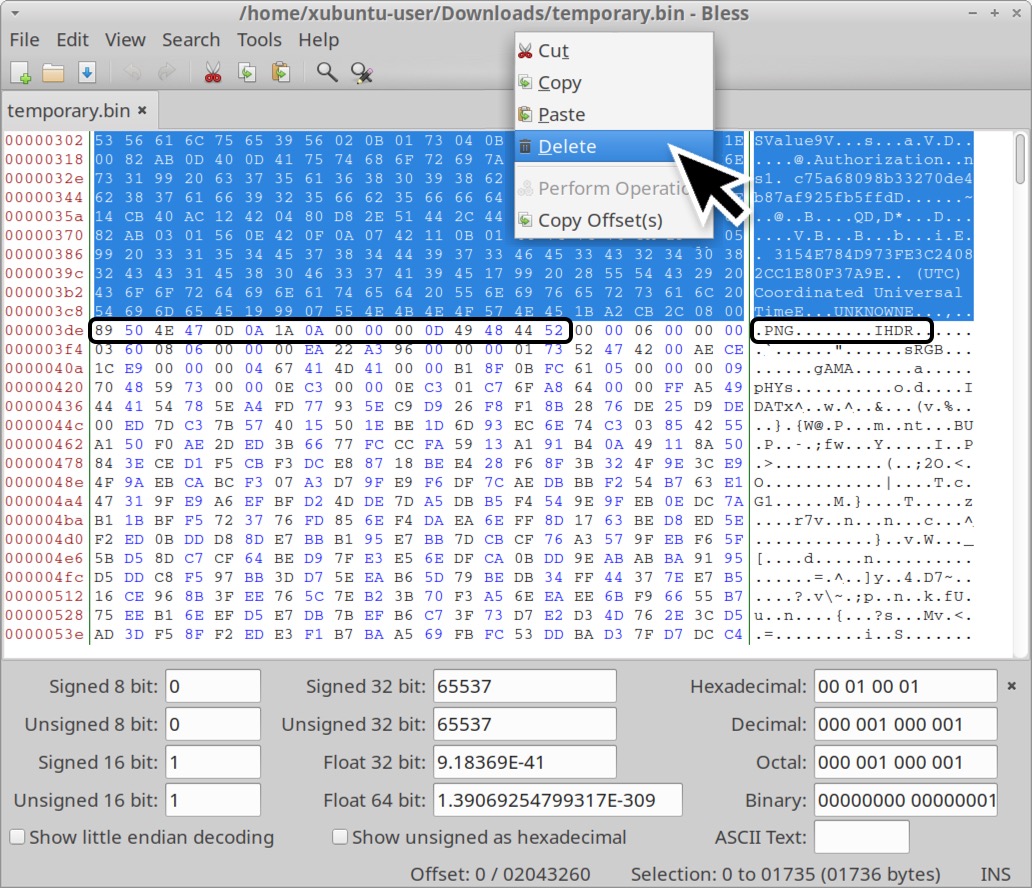
Save the edited file under a new name using the file extension .png. The first byte of your newly saved file should be 0x89. This newly saved file still contains other non-image data, but we can see the screenshot with an image viewer as shown below in Figure 16.
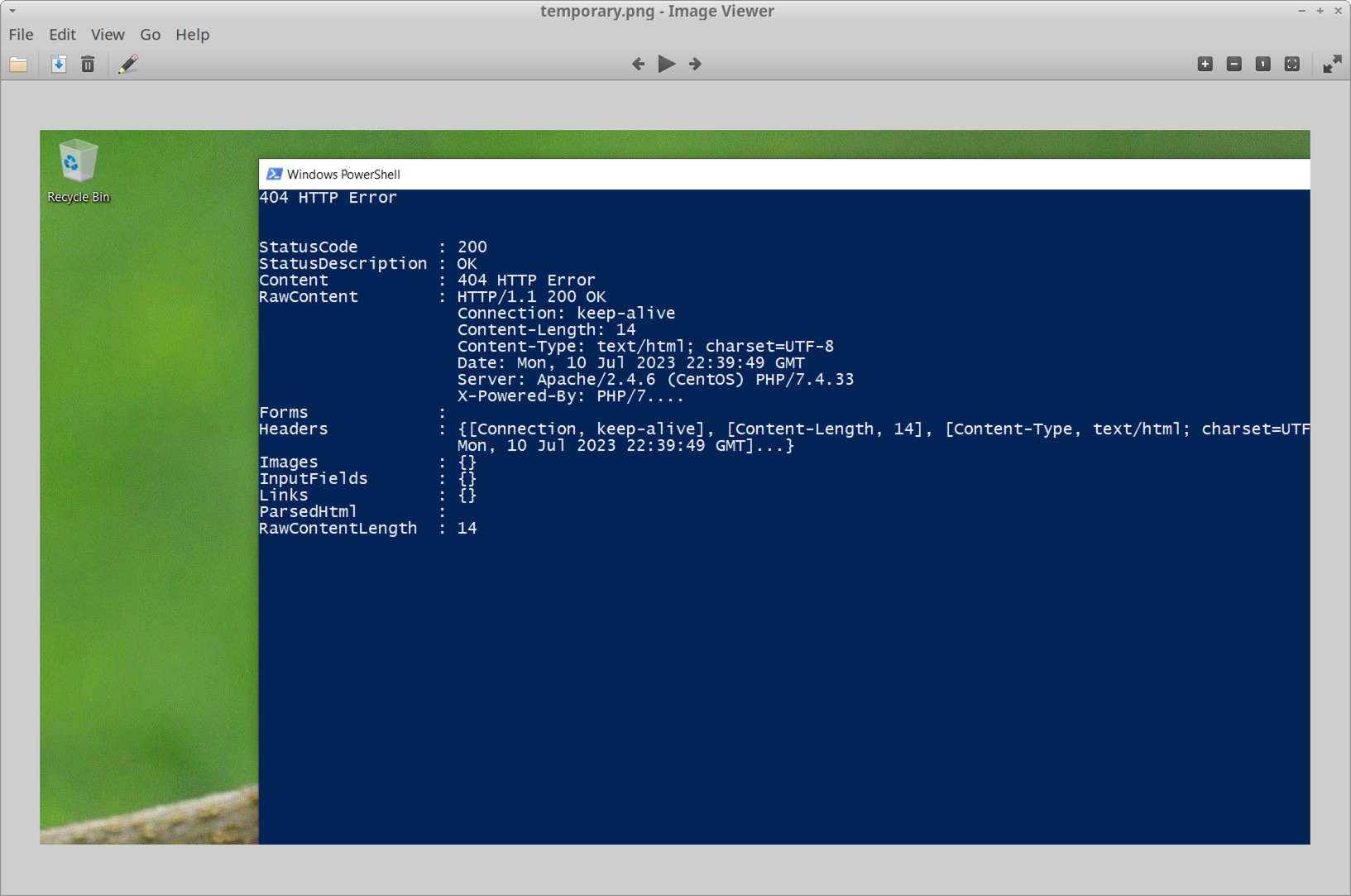
In Figure 16, the screenshot reveals a PowerShell window with data from a web traffic connection.
After reviewing the image, return to the TCP stream (tcp.stream eq 71), view it as ASCII data and select traffic only going from the infected Windows host to the C2 server. Scroll to the end to review additional data sent to the C2 server.
Knowing a little more about the infected Windows host will help us better understand this data. The infected Windows host was a minimal installation, and it only had one set of login credentials stored in the Microsoft Edge browser. The host had just one Word document stored in the user’s Documents folder. The file was named Top_secret_ducment.docx.
Near the end of this TCP stream we find a list of running processes as shown below in Figure 17. We can also find hardware information from the infected host, login credentials from the Edge browser, and the file named Top_secret_ducment.docx.
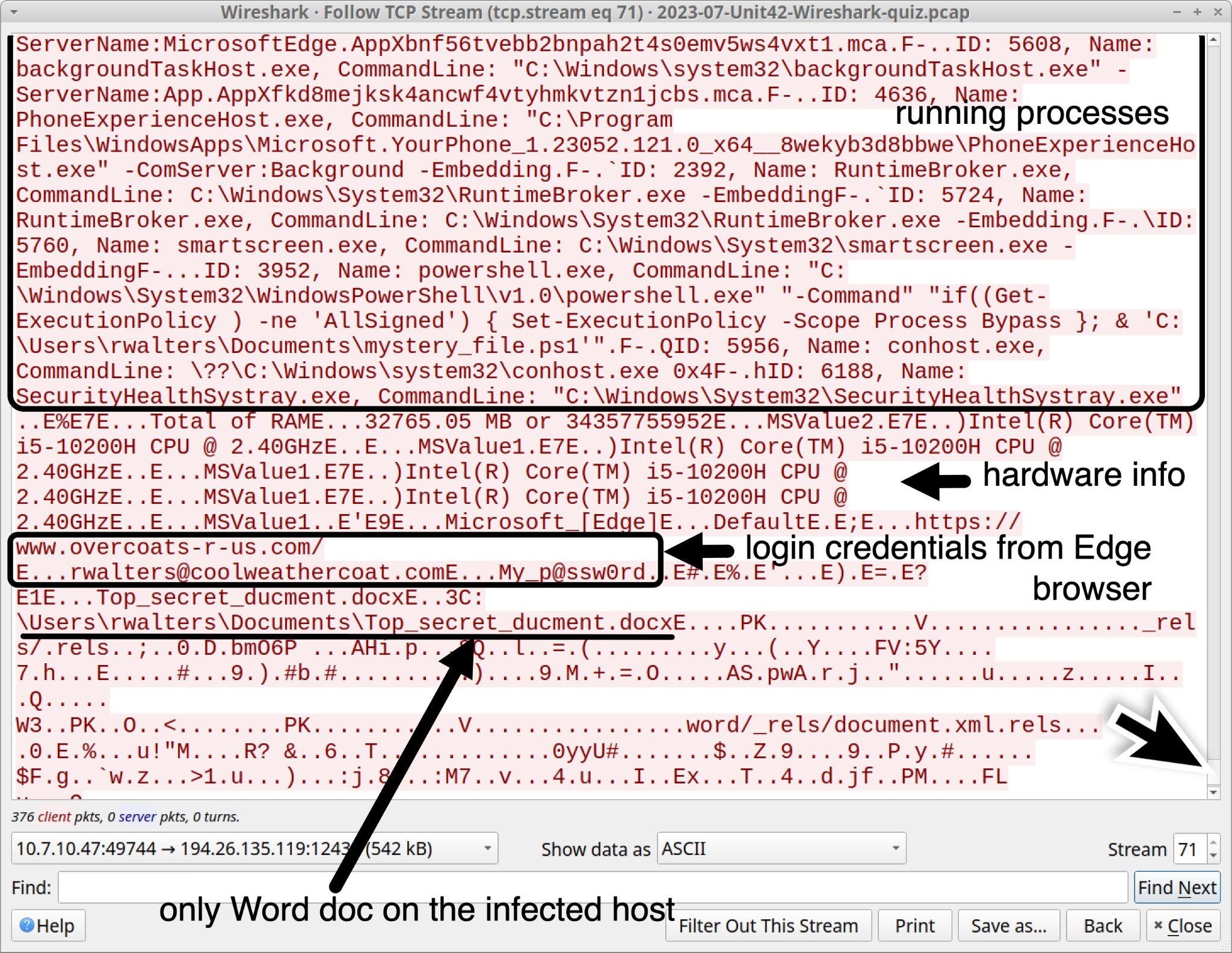
The running process list in Figure 17 also reveals a process for powershell.exe running a file at C:UsersrwaltersDocumentsmystery_file.ps1. That .ps1 file generated the infection traffic for this Wireshark quiz.
Conclusion
This post provides answers and analysis for our Unit 42 Wireshark quiz featuring a RedLine Stealer infection from July 2023. We now have a better idea of the information this malware looks for, and the types of data it sends from an infected host. RedLine Stealer is important to identify and stop, because it targets sensitive information like login credentials and cryptocurrency wallet info.
Since many security professionals lack access to full packet capture, they may also lack experience with RedLine Stealer and other malware traffic. Training material like this Wireshark quiz is designed to help. Pcap analysis is a very useful skill when investigating a malware infection.
You can read the original post, without answers, from our standalone quiz post.
Palo Alto Networks customers are protected from RedLine Stealer and other malware through Cortex XDR and our Next-Generation Firewall with Cloud-Delivered Security Services that include WildFire, Advanced Threat Prevention and Advanced URL Filtering.
If you think you might have been compromised or have an urgent matter, get in touch with the Unit 42 Incident Response team or call:
- North America Toll-Free: 866.486.4842 (866.4.UNIT42)
- EMEA: +31.20.299.3130
- APAC: +65.6983.8730
- Japan: +81.50.1790.0200
Palo Alto Networks has shared these findings, including file samples and indicators of compromise, with our fellow Cyber Threat Alliance (CTA) members. CTA members use this intelligence to rapidly deploy protections to their customers and to systematically disrupt malicious cyber actors. Learn more about the Cyber Threat Alliance.
Indicators of Compromise
Traffic from the pcap related to the RedLine Stealer infection:
- hxxp://623start[.]site/?status=start&av=
- hxxp://623start[.]site/?status=install
- hxxp://guiatelefonos[.]com/data/czx.jpg
- hxxps://guiatelefonos[.]com/data/czx.jpg
- tcp://194.26.135[.]119:12432/
Files associated with traffic from this RedLine Stealer infection:
- SHA256 hash: f754d7674a3a74969cccb7d834c99b72b9f79c29dc8d0e9c15854a6bfb1a9c97
- File size: 800 bytes
- File name: SECT_v4.ps1
- File description: PowerShell script used to kick off the RedLine Stealer infection
- Sample available at MalwareBazaar Database
- SHA256 hash: 3c42b93801f02696487de64bb623f81cf7baf73a379a46e1459ca19ae7dc2454
- File size: 348,160 bytes
- File location: hxxps://guiatelefonos[.]com/data/czx.jpg
- File description: Windows executable file for RedLine Stealer
- Sample available at MalwareBazaar Database
Additional Resources
- Wireshark Tutorial: Wireshark Workshop Videos Now Available – Unit 42, Palo Alto Networks
- Unit 42 Wireshark Quiz, January 2023 – Unit 42, Palo Alto Networks
- Answers to January 2023 Unit 42 Wireshark Quiz – Unit 42, Palo Alto Networks
- Unit 42 Wireshark Quiz, February 2023 – Unit 42, Palo Alto Networks
- Answers to February 2023 Unit 42 Wireshark Quiz – Unit 42, Palo Alto Networks
- Finding Gozi: Unit 42 Wireshark Quiz, March 2023 – Unit 42, Palo Alto Networks
- Finding Gozi: Answers to Unit 42 Wireshark Quiz, March 2023 – Unit 42, Palo Alto Networks
- Cold as Ice: Unit 42 Wireshark Quiz for IcedID – Unit 42, Palo Alto Networks
- Cold as Ice: Answers to Unit 42 Wireshark Quiz for IcedID – Unit 42, Palo Alto Networks
- New Redline Password Stealer Malware – Proofpoint Threat Insight, March 2020
- 2023-03-02: Rig EK –> malware loader –> Redline Stealer – malware-traffic-analysis.net
- Malicious AI Tool Ads Used to Deliver Redline Stealer – Trend Micro Research, May 2023
- Do Not Cross The ‘RedLine’ Stealer: Detections and Analysis – Splunk Threat Research Team, June 2023
Get updates from
Palo Alto
Networks!
Sign up to receive the latest news, cyber threat intelligence and research from us
Source: https://unit42.paloaltonetworks.com/wireshark-quiz-redline-stealer-answers/