The AhnLab Security Emergency response Center’s (ASEC) analysis team is constantly monitoring malware distributed to vulnerable database servers. MySQL server is one of the main database servers that provides the feature of managing large amounts of data in a corporate or user environment. Typically, in Windows environments, MS-SQL is primarily installed for database services, while in Linux environments, database services like MySQL and PostgreSQL are used. However, although not as frequently as MS-SQL servers, there are instances where MySQL servers are installed on Windows since DBMS services like MySQL also support Windows environments. Consequently, attacks targeting MySQL servers running in Windows environments are constantly being identified.
Based on the information from our AhnLab Smart Defense (ASD) logs, it appears that a majority of the malware strains targeting vulnerable MySQL servers are variants of Gh0st RAT. It is worth noting that in addition to these Gh0st RAT variants, various other types of malware can potentially be utilized as well. For example, a previous ASEC blog post covered an incident involving the use of AsyncRAT. [1]
The ASEC analysis team has recently discovered that the Ddostf DDoS bot is being installed on vulnerable MySQL servers. Ddostf is a DDoS bot capable of conducting Distributed Denial of Service (DDoS) attacks on specific targets and was first identified around 2016. [2] It is known to have been developed in China and is notable for its support for both Windows and Linux environments.
 Figure 1. Ddostf DDoS bot being installed via MySQL service
Figure 1. Ddostf DDoS bot being installed via MySQL service
1. Attacks Targeting MySQL Servers
Threat actors will identify potential targets for their attacks via scans. Among the systems that are publicly accessible, scanners search for systems using the 3306/TCP port, which is used by MySQL servers. Afterward, threat actors can use brute-force or dictionary attacks on the system. If the system manages its account credentials poorly, threat actors can gain access to administrator account credentials. Of course, if the system is running an unpatched version with vulnerabilities, threat actors could exploit these vulnerabilities to execute commands without the need for the aforementioned process.
Normally, multiple methods to execute OS commands are provided in MS-SQL environments. The most well-known command is xp_cmdshell, and there are other various methods such as OLE Store Procedure, MS-SQL Agent Jobs, Extended Stored Procedure, and CLR Stored Procedure. Being able to execute a user’s command using OS commands (e.g. CMD or PowerShell) means that control over the system can be obtained.
Unlike MS-SQL, MySQL does not support direct OS commands such as xp_cmdshell. It can, however, use a feature called User-defined Function (UDF) to ultimately allow threat actors to execute commands.
 Figure 2. Metasploit’s UDF attack feature
Figure 2. Metasploit’s UDF attack feature
2. UDF (User-Defined Function) DLL
UDF is an implementation of desired features in a DLL, and threat actors upload a DLL containing malicious commands as a UDF library to the infected system. They then load this DLL into the MySQL server. Subsequently, they can deliver malicious commands to the infected system by executing the defined commands.
This process is similar to MS-SQL server’s CLR SqlShell. [3] Like WebShell, which can be installed on web servers, SqlShell is a malware strain that supports various features after being installed on an MS-SQL server, such as executing commands from threat actors and carrying out all sorts of malicious behaviors.
MS-SQL servers support a method known as CLR Stored Procedure, which allows the usage of expanded features, and SqlShell is a DLL created with this method. CLR Stored Procedure is one of the major methods that threat actors can use to execute malicious commands in MS-SQL servers along with the xp_cmdshell command. Threat actors mainly use SqlShell as a means to install the ultimate malware, such as CoinMiners or ransomware.
Examining the infection logs from systems that were actually targeted reveals that malicious UDF DLLs, like the one below, are also installed on infected systems in addition to Ddostf. Of course, these UDF DLLs have been used for various attacks long before threat actors decided to use them for installing the Ddostf DDoS bot. Therefore, the threat actor utilized the UDF malware as a tool during their process of attacking poorly managed MySQL servers.
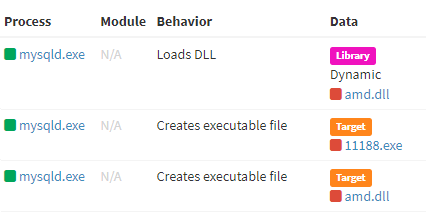 Figure 3. Log showing UDF DLL being installed with Ddostf
Figure 3. Log showing UDF DLL being installed with DdostfThis UDF malware supports features to download files from URLs passed as arguments or execute commands provided by threat actors. It is presumed that the threat actor utilized the downloader() function provided by the UDF DLL to download Ddostf from an external source before executing the downloaded Ddostf using the cmdshelv() function. Additionally, besides command execution, the cmdshelv() function also supports the feature to output the execution results as a “cmd.tmp” file, where it then transmits the results of the command that reads and executes the file to the C&C server.
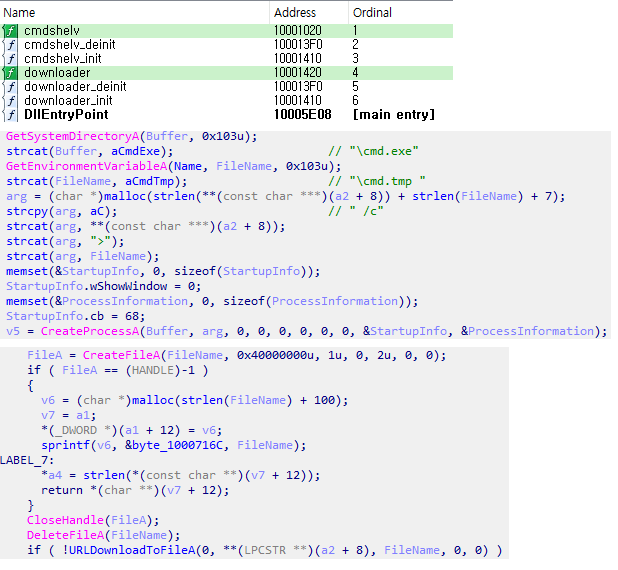 Figure 4. Features supported by UDF library
Figure 4. Features supported by UDF library
3. Analysis of Ddostf DDoS Bot
There is the ELF format of Ddostf that can target Linux environments and the PE format that can operate in Windows environments. Here, we will cover the PE format used in attacks targeting Windows environments. A main characteristic of Ddostf is the inclusion of the “ddos.tf” string in its binary, as shown below.
 Figure 5. ddos.tf string contained within the binary
Figure 5. ddos.tf string contained within the binaryWhen Ddostf is executed, it first copies itself under a random name in the %SystemRoot% directory before registering itself as a service.
 Figure 6. Ddostf DDoS Bot registered as a service
Figure 6. Ddostf DDoS Bot registered as a serviceAfterward, it decrypts the encrypted C&C server URL string “C8AF3371ACB79AA6119CB33C80C40AE544F319” to obtain and connect to the actual C&C server URL. Additionally, the malware creator inserted meaningless printf() functions in the middle of the actual code routine to hinder analysis. Upon initial connection, it collects basic pieces of information from the infected system and sends them to the C&C server.
 Figure 7. C&C server connection routine
Figure 7. C&C server connection routine| Offset | Size | Description |
|---|---|---|
| 0x00 | 0x04 | Signature (0x0000000B) |
| 0x08 | 0x40 | Windows version |
| 0x48 | 0x20 | Malware version information (Ver 8.0) |
| 0x68 | 0x04 | CPU performance (MHz) |
| 0x6C | 0x04 | Number of processors |
| 0x70 | 0x20 | Computer name |
| 0x90 | 0x04 | Language information |
Table 1. System information sent to the C&C server
 Figure 8. System information transmitted to the C&C server
Figure 8. System information transmitted to the C&C serverAdditionally, during the initial transmission of system information, the value 0x0000000B is also sent as a signature. However, among the C&C server commands, when sending the current status information of a system, such as network speed and CPU usage, the value 0x0000000A is used.
 Figure 9. Routine to transmit the status information of a system
Figure 9. Routine to transmit the status information of a system| Offset | Size | Description |
|---|---|---|
| 0x00 | 0x04 | Signature (0x0000000A) |
| 0x08 | 0x10 | Network interface speed (kb/bps) / CPU usage (%) |
Table 2. Status information sent to the C&C server
When the infected system’s information is transmitted to the C&C server, the C&C server responds with a size of 0x000000C4. This response not only contains commands but also data. For example, in the case of specific DDoS attack methods or download commands, it includes the download URL.
| Offset | Size | Description |
|---|---|---|
| 0x00 | 0x04 | Dummy |
| 0x04 | 0x04 | Command |
| 0x08 | 0xBC | Additional data |
Table 3. Structure of commands received from the C&C server
While there are only six supported commands, DDoS attacks internally encompass a variety of methods, including SYN Flood, UDP Flood, HTTP GET/POST Flood attacks, among others.
 Figure 10. Various User-Agent strings used in attack
Figure 10. Various User-Agent strings used in attack| Command | Feature |
|---|---|
| 0x00000005 | Starts DDoS attack |
| 0x00000006 | Stops DDoS attack |
| 0x00000007 | Downloads and runs additional payload |
| 0x00000008 | Starts transmitting system status information |
| 0x00000009 | Stops transmitting system status information |
| 0x00000013 | Executes DDoS command from new C&C server |
Table 4. List of supported commands
Although most of the commands supported by Ddostf are similar to those from typical DDoS bots, a distinctive feature of Ddostf is its ability to connect to a newly received address from the C&C server and execute commands there for a certain period. As shown below, only DDoS commands can be performed on the new C&C server. This implies that the Ddostf threat actor can infect numerous systems and then sell DDoS attacks as a service.
 Figure 11. DDoS attack commands supported only
Figure 11. DDoS attack commands supported only
4. Conclusion
Typical attacks that target database servers (MS-SQL, MySQL servers) include brute force attacks and dictionary attacks on systems where account credentials are poorly managed. Although it seems as if these methods make up the majority of the attacks, there can also be vulnerability attacks against systems with unpatched vulnerabilities.
Because of this, administrators should use passwords that are difficult to guess for their accounts and change them periodically to protect the database server from brute force attacks and dictionary attacks. They should also apply the latest patches to prevent vulnerability attacks. Administrators should also use security programs such as firewalls for externally accessible database servers to restrict access from external threat actors. If the above measures are not taken in advance, continuous infections by threat actors and malware can occur.
AhnLab MDS Sandbox detects the Ddostf malware under the detection names “Persistence/MDP.Event.M29”, “Malware/MDP.Manipulate.M491”, and “Malware/MDP.AutoRun.M1038”.
 Figure 12. Malware detection screen from AhnLab MDS
Figure 12. Malware detection screen from AhnLab MDS Figure 13. Detection of Ddostf’s efforts to maintain persistence
Figure 13. Detection of Ddostf’s efforts to maintain persistenceAhnLab’s anti-malware software, V3, detects and blocks the malware using the following aliases:
File Detection
– Trojan/Win32.Nitol.R215641 (2017.12.18.00)
– Downloader/Win32.Agent.R24480 (2012.05.08.03)
Behavior Detection
– Malware/MDP.Behavior.M29
– Malware/MDP.Behavior.M1091
– Persistence/MDP.Event.M29
– Malware/MDP.Manipulate.M491
– Malware/MDP.AutoRun.M1038
IOC
MD5
– 6e7e26a6e237f84b51bc61aa7dff5680: Ddostf (11188.exe)
– fe550baf5205d4b2503ad0d48014fccf: UDF DLL (amd.dll)
C&C URL
– 136.243.103[.]119:6681
AhnLab MDS detects and responds to unknown threats by performing sandbox-based dynamic analysis. For more information about the product, please visit our official website.

The post Ddostf DDoS Bot Malware Attacking MySQL Servers appeared first on ASEC BLOG.
Article Link: https://asec.ahnlab.com/en/58878/
Source: https://malware.news/t/ddostf-ddos-bot-malware-attacking-mysql-servers/75611