Perception Point’s team of researchers recently investigated a malware attack aimed to bypass threat detection engines. The sophisticated attack was caught by our advanced threat prevention platform; the payload was detected by our next-gen sandboxing technology. Read on to learn more.

Distribution
In this campaign, the attacker impersonates a financial services company and sends the target an email containing a fake invoice. The user is prompted to click on the button “View & Download Invoice.” To add legitimacy to the message, a legitimate website is included in the message to serve as an alternative to clicking the button.
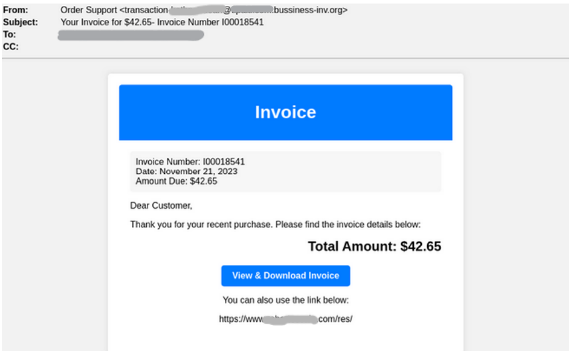
Upon clicking on the button to view the invoice, the user is sent to a website that is unavailable. The user must instead go back to the email and click on the website link.
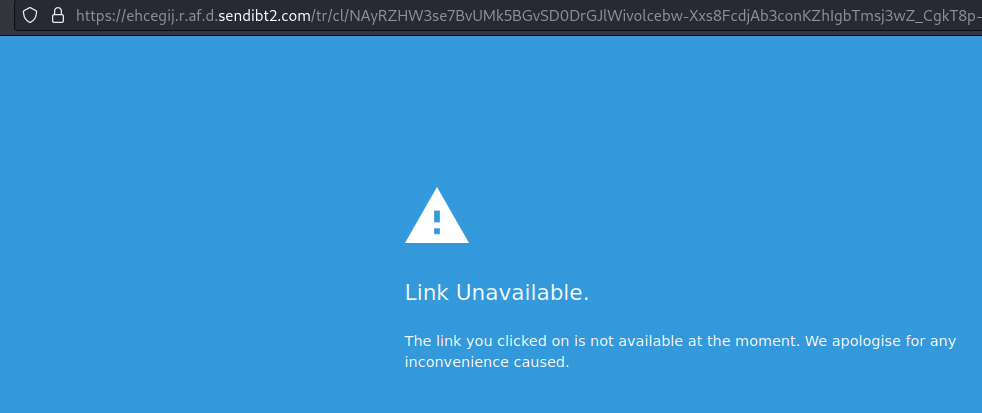
The attacker uses the unavailable page and the legitimate website link as a form of evasion, to avoid detection. When most security solutions scan the message, they are unable to locate the malicious payload, as the button (the first link) leads to an error page and the second link’s URL seemingly belongs to a non-malicious website.
However, when the user clicks on the website link, they are redirected to another URL, which automatically triggers the download of a JavaScript file, containing several other files including the malicious payload.
It is important to note that the attacker had to first breach the legitimate website in order to host the URL redirect.
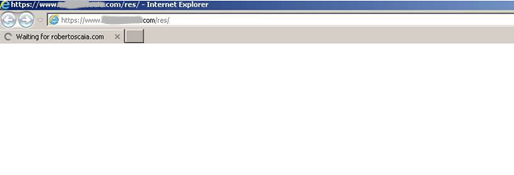
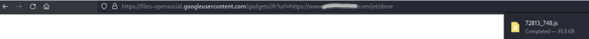
Looking at the website code shows that there are multiple redirects to malicious URLs.
One of these URLs (hxxps://robertoscaia.com/eco) automatically downloads malware onto the user’s device. This website uses a malware .exe file generator to continuously download different executable files.

Execution
The malware used in this attack is LUMMA, an InfoStealer malware written in C language and distributed through a Malware-as-a-Service model.

In this malware attack, tasks involve the execution of three processes: “1741.exe,” “RegSvcs.exe,” and “wmpnscfg.exe.” The first process, “1741.exe,” is executed from the user’s temporary folder. This is notable, as legitimate programs typically do not run from the temporary folder, raising concerns about the file’s potential malicious or unwanted nature.
The second process, “RegSvcs.exe,” is executed from the Microsoft.NET framework folder. This behavior is also suspicious since “RegSvcs.exe” is commonly associated with malware activities, particularly in registering and executing malicious .NET assemblies.
Similarly, the third process, “wmpnscfg.exe,” is executed from the Windows Media Player folder, adding another layer of complexity to the task.
In addition, each process has a parent process with specific Process IDs (PIDs). The first process, “1741.exe,” has a parent process with PID 1388, while the second and third processes, “RegSvcs.exe” and “wmpnscfg.exe,” have parent processes with PIDs 3428 and 1388, respectively. The deliberate choice of parent processes and specific Process IDs adds complexity to the attack, aiming to obfuscate the malicious activities.
Conclusion
This incident underscores the evolving tactics of threat actors and the need for organizations to continuously check the efficacy of their security systems. It highlights the importance of advanced threat prevention technologies, continuous monitoring, and a multi-layered security approach to effectively detect malware attacks and mitigate such sophisticated cyber threats. As cyber adversaries adapt, so must our defense strategies to safeguard sensitive information and systems.
Perception Point can provide malware protection and help prevent sophisticated cyber attacks like this one from reaching your organization.
Contact us to learn more.

Mitre AT&CK TTPs
T1204 Execution
T1012 Query Registry
T1082 System Information Discovery
IOCs
Main object – 3827.exe
md5 0563076ebdeaa2989ec50da564afa2bb
sha1 ac14e7468619ed486bf6c3d3570bea2cee082fbc
sha256 515ad6ad76128a8ba0f005758b6b15f2088a558c7aa761c01b312862e9c1196b
Dropped executable file
sha256 C:UsersadminAppDataLocalTempProtect544cd51a.dll dfce2d4d06de6452998b3c5b2dc33eaa6db2bd37810d04e3d02dc931887cfddd
DNS requests
domain taretool[.]pw
Connections
ip 104[.]21[.]21[.]50
ip 224[.]0[.]0[.]252
HTTP/HTTPS requests
url hxxp://taretool[.]pw/api
url hxxp://www[.]patrickforeilly[.]com/eco/
url hxxps://www[.]patrickforeilly[.]com/eco/
url hxxps://www[.]robertoscaia[.]com/eco/
url hxxps://fuelrescue[.]ie/eco/
url hxxps://www[.]7-zip[.]org/a/7zr[.]exe
Source: https://perception-point.io/blog/behind-the-attack-lumma-malware/