Summary: The content discusses the increase in the exploitation of vulnerabilities as an initial access step for a breach, highlighting the significant growth between 2022 and 2023.
Threat Actor: Cybercriminals | Cybercriminals
Victim: Organizations | Organizations
Key Point :
- The exploitation of vulnerabilities as an initial access step for a breach increased by 180% between 2022 and 2023, accounting for 14% of malicious actors’ way into a network.
- This growth can be attributed to the exploitation of the MOVEit vulnerability and other zero-day exploits used by ransomware actors in 2024.
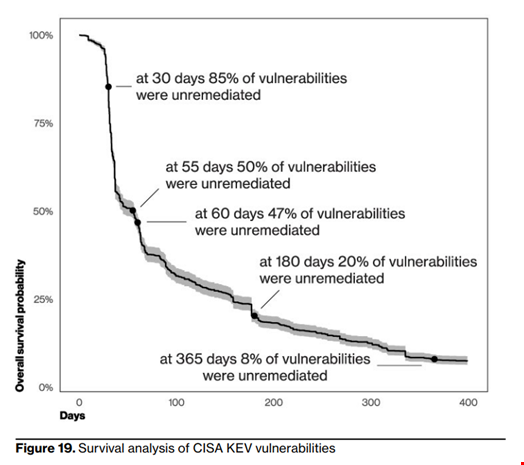
- Organizations take an average of 55 days to remediate 50% of critical vulnerabilities after their patches are available, creating a dangerous lag in cybersecurity.
The exploitation of vulnerabilities as an initial access step for a breach increased by a staggering 180% between 2022 and 2023.
According to Verizon’s 2024 Data Breach Investigations Report (DBIR), published on May 1, this method of gaining unauthorized access leading to a breach accounted for 14% of malicious actors’ way into a network. It is the third most used after credential theft and phishing.
This growth is partly due to the exploitation of the MOVEit vulnerability and several other zero-day exploits that ransomware actors used throughout 2024, the report said.
“It is truly concerning. Even when considering only the US Cybersecurity Infrastructure and Security Agency’s (CISA) Known Exploited Vulnerabilities (KEV) catalog, it takes organizations around 55 days to remediate 50% of those critical vulnerabilities after their patches are available – a dangerous lag,” warned Verizon.
“On the flip side, the median time for detecting the first scan for a CISA KEV vulnerability is five days from publication in the Common Vulnerabilities and Exposures (CVE) database (not from the patch being available).”
This exploitation of these vulnerabilities also comes at a critical moment for the software security community. Recently, the US National Institute of Standards and Technology struggled to keep the National Vulnerability Database (NVD) afloat, marred by resource and financial issues.
The NVD is the most used vulnerability repository worldwide. It lists reported CVEs and provides metadata that helps mitigate the risk associated with them. However, the NVD program has experienced a serious backlog of vulnerability enrichment since February 2024.
Read more: NIST Unveils New Consortium to Operate National Vulnerability Database
With the prevalence of vulnerability exploits, Verizon started monitoring software supply chain attacks, which rose by 68% in 2023 compared to 2022.
In total, 15% of breaches involved a third party, including data custodians or hosting partners being breached and direct or indirect software supply chain issues.
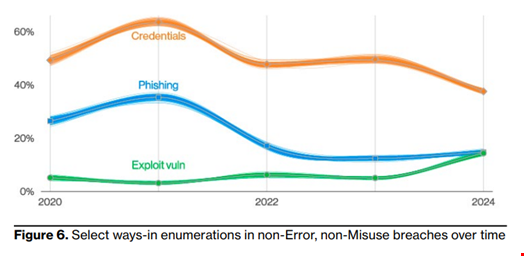
Stolen Credential, Top Initial Access Method
Stolen credentials remain a popular tool for cybercriminals, with credential theft being the top initial access method leading to a breach and representing 38% of all breaches recorded in 2023.
This is a long-lasting trend, as 31% of all breaches over the past ten years involved credential theft, Verizon said.
Phishing comes as the second most used initial access method, representing 15% of all cases recorded by Verizon in 2023.
“The median time for users to fall for phishing emails is less than 60 seconds,” Verizon noted in the report.
Non-Malicious Humans Still at Fault
In general, non-malicious human beings are still strongly involved in data breaches, with 68% of all breaches involving a non-malicious human element. The most common causes are someone falling victim to a social engineering attack or someone making a mistake.
“In either case, these could have been mitigated by basic security awareness and training. This is an updated metric in the report (we would previously include malicious insiders), and it is roughly the same as the previous period described in the 2023 DBIR,” Verizon added.
Ransomware and Extortion Blend into ‘Ramstortion’
Traditional ransomware’s prevalence declined slightly in 2023, representing 23% of all breaches.
However, roughly one-third (32%) of all breaches involved some type of extortion technique, including ransomware.
“The meteoric growth of extortion attacks made this combined threat stand out in our dataset. When you combine [ransomware] with extortion, we hit a similar ratio [than] last year’s ‘Ramstortion,’” Verizon said.
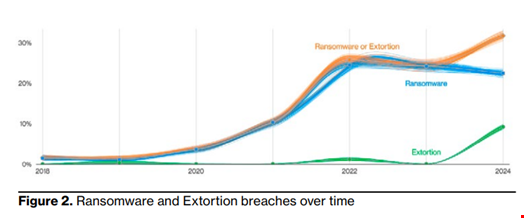
Over the past three years, almost two-thirds (between 59% and 66%) of financially motivated incidents involved either ransomware or extortion of some kind.
In 2023, the median loss associated with these types of breaches was $46,000, fluctuating between $3 and $1,141,467 for 95% of the criminal complaints made to the FBI’s Internet Crime Complaint Center (IC3).
By comparison, the median transaction amount for business email compromise (BEC) incidents in 2022 and 2023 was around $50,000.
This report is Verizon’s 17th edition of the DBIR. It results from a record-high 30,458 real-world security incidents analyzed, of which 10,626 were confirmed data breaches (more than double last year’s number), with victims in 94 countries.
Source: https://www.infosecurity-magazine.com/news/dbir-vulnerability-exploits-triple/
“An interesting youtube video that may be related to the article above”