Summary: Researchers have sinkholed a command and control server for a variant of the PlugX malware and observed over 2.5 million connections from unique IP addresses in six months.
Threat Actor: PlugX | PlugX
Victim: Various organizations worldwide
Key Point:
- Researchers sinkholed a command and control server for a variant of the PlugX malware and observed over 2.5 million connections from unique IP addresses in six months.
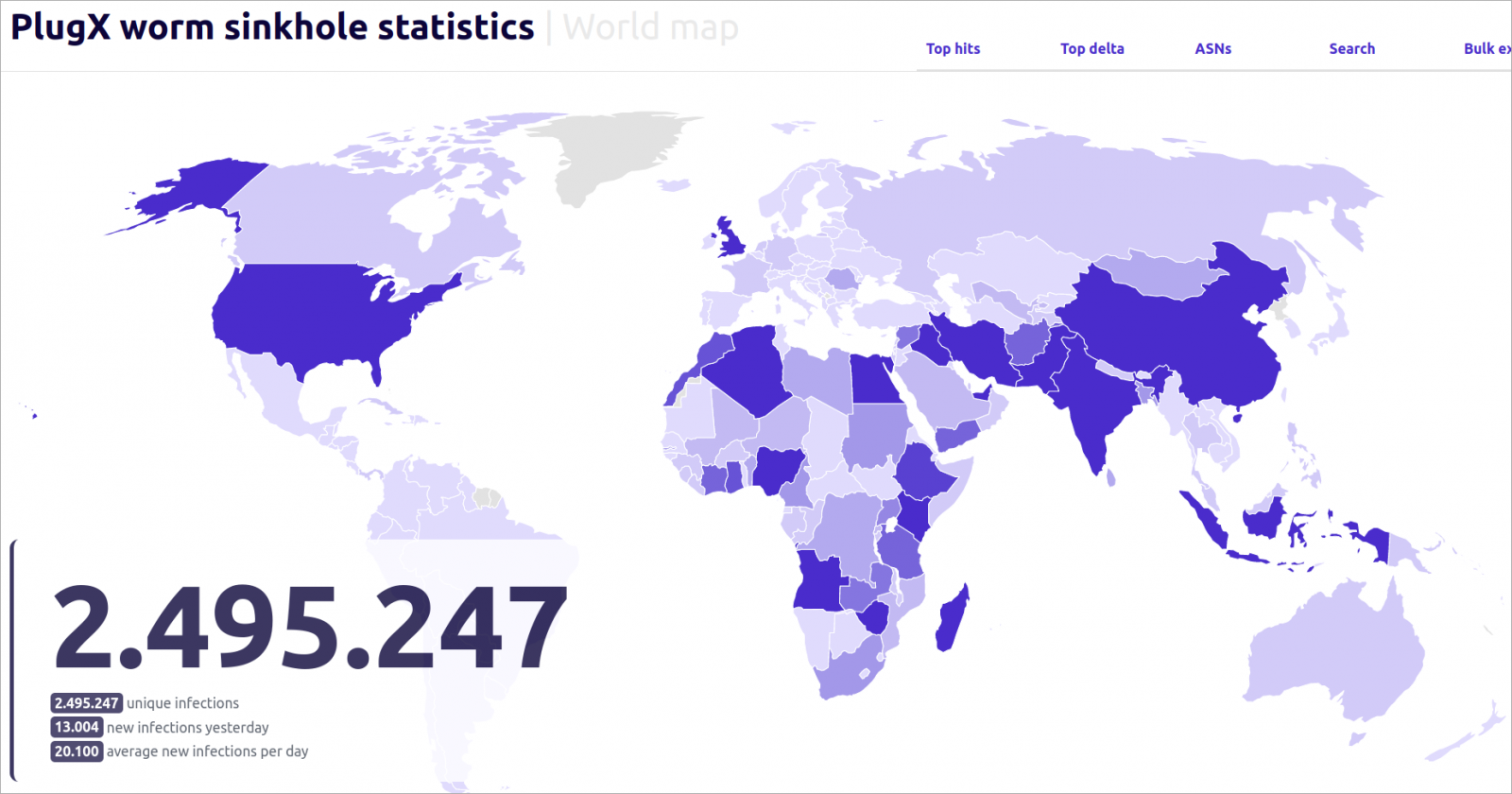
- The sinkhole operation revealed that the malware spread to 170 countries, with Nigeria, India, China, Iran, Indonesia, the UK, Iraq, and the United States being the most affected.
- Sekoia, the cybersecurity firm behind the sinkhole operation, formulated two strategies to clean infected computers and called for national cybersecurity teams and law enforcement agencies to join the disinfection effort.
- The researchers note that although China’s strategic interest is plausible due to the Belt and Road Initiative, PlugX has been used by various threat actors over the years.
- PlugX has been used since at least 2008, primarily in espionage and remote access operations, and has targeted government, defense, technology, and political organizations.
Researchers have sinkholed a command and control server for a variant of the PlugX malware and observed in six months more than 2.5 million connections from unique IP addresses.
Since last September, the sinkhole server received over 90,000 requests every day from infected hosts in more than 170 countries.
Since September 2023, when Sekoia captured the unique IP address associated with the particular C2, it has logged over 2,495,297 unique IPs from 170 countries interacting with its sinkhole.
This action enabled the security firm to analyze traffic, map infections, prevent malicious exploitation of clients, and devise effective disinfection plans.
Taking control of the PlugX server
Researchers at cybersecurity company Seqoia spent $7 to acquire the IP address 45.142.166[.]112 corresponding to a command and control (C2) server for a variant of the PlugX malware that the threat actor no longer uses.
The C2 IP address was documented in a report in March 2023 from Sophos about a new version of PlugX that had spread to “locations nearly halfway around the world from each other.” The malware had already gained self-spreading capabilities over USB devices.
After Seqoia contacted the hosting company and requested control over the IP, the researchers obtained shell access to a server using the IP.
A simple web server was set up at mimic the original C2 server’s behavior, which enabled the analysts to capture HTTP requests from infected hosts and observe variations in the flow.
The sinkhole operation revealed that between 90,000 and 100,000 systems were sending requests daily, and over six months more than 2.5 million unique IPs connected to the server from all over the world.
Sekoia
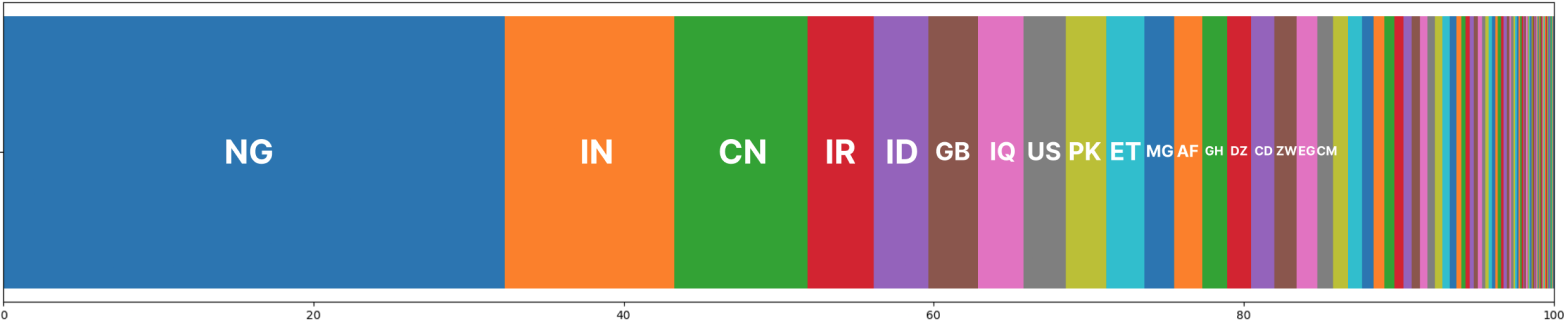
While the worm spread to 170 countries, just 15 of them account for over 80% of the total infections, with Nigeria, India, China, Iran, Indonesia, the UK, Iraq, and the United States being at the top of the list.
The researchers highlight that the sinkholed PlugX C2 does not have unique identifiers, which leads to an unreliable count of infected hosts:
- many compromised workstations can exit through the same IP address
- because of dynamic IP addressing, one infected system can connect with multiple IP addresses
- many connections are through VPN services, which can make the source country irrelevant
Sekoia says the victimology might indicate strategic interest from the perspective of China, as most of the infections are seen in countries participating in China’s Belt and Road Initiative global infrastructure development strategy.
However, the researchers note that although this conclusion is plausible, it “must be taken with a grain of salt, because after four years of activities, it had time to spread everywhere.”
Sekoia
While PlugX was initially associated with state-sponsored operations of Chinese origin, the malware has turned into a common tool over the years and has been used by various threat actors, some of them involved in financially motivated activities such as ransomware.
Disinfection challenges
Sekoia has formulated two strategies to clean computers reaching their sinkhole and called for national cybersecurity teams and law enforcement agencies to join the disinfection effort.
One method is to send the self-delete command supported by PlugX, which should remove it from computers without additional actions.
However, even if the malware is removed from the host, there is still a risk of re-infection because the malware spreads over USB devices, and cleaning them is not possible this way.
A more complex method involves developing and deploying a custom payload on infected machines to remove PlugX both from the system as well as from infected USB drives connected to them.
The cybersecurity firm has offered to provide national CERTs with the required information to perform “sovereign disinfection” to avoid the legal complexity of sending commands to other people’s workstations.
Regardless of the method, Sekoia notes that air-gapped networks already impacted by PlugX are beyond reach and the same applies to infected USB drives that are not plugged in.
Sequia researchers say that the botnet built with the sinkholed version of PlugX can be considered as “dead” because the malware operators are no longer in control.
Nevertheless, “anyone with interception capabilities” or able to take control of the C2 server can revive it for malicious purposes by sending arbitrary commands to an infected host.
PlugX background
PlugX has been used since at least 2008 mainly in espionage and remote access operations from groups linked to the Chinese Ministry of State Security. It has been used by multiple attack groups often for targeting government, defense, technology, and political organizations, primarily in Asia and later expanding in the West.
Over time, PlugX builders emerged in the public space and some researchers believe that the malware’s source code was leaked around 2015. This and the fact that the tool received multiple updates, makes it difficult to attribute PlugX to a specific actor or agenda.
The malware features extensive capabilities including command execution, uploading and downloading files, logging keystrokes, and accessing system information.
A recent variant of PlugX features a wormable component, allowing it to spread autonomously by infecting removable drives such as USB flash drives, and potentially reaching air-gapped systems.
“An interesting youtube video that may be related to the article above”