Summary: This content discusses the security analysis of Microsoft Warbird and Protected Media Path technologies conducted by Security Explorations, a research lab of AG Security Research company. It highlights the vulnerabilities discovered in these technologies and their potential impact on content security.
Threat Actor: Security Explorations | Security Explorations
Victim: Microsoft | Microsoft
Key Point:
- The research conducted by Security Explorations revealed several deficiencies in Microsoft Warbird and Protected Media Path technologies, which could be exploited to gain access to plaintext content keys protected by PlayReady DRM in Windows OS environment.
- The vulnerabilities discovered in these technologies could potentially allow attackers to decrypt high-definition movies and compromise content security on various streaming platforms.
- The research highlights the importance of content security in the streaming industry, as well as the need for continuous efforts to identify and mitigate vulnerabilities in DRM technologies.
In a result of its research investigation efforts, Security Explorations, a research lab of AG Security Research company, conducted security analysis of Microsoft Warbird and Protected Media Path technologies.
This section of our website presents initial information regarding the project.
Microsoft Warbird and Protected Media Path description
Microsoft Protected Media Path (PMP) is a set of technologies of which goal is to enforce security of content (security of PlayReady DRM) in a Windows OS environment (Wikipedia).
In Windows OS, Protected Media Path is implemented both in kernel and user space. It relies on crypto, code integrity, auth checks, whitebox crypto and code obfuscation.
Microsoft Warbird is a compiler technology from Microsoft of which goal is to make reverse engineering (such as static and dynamic analysis) of code components comprising certain Windows OS components hard. More specifically, the goal is to make it hard to extract secrets pertaining to code implementation in an untrusted (under attacker’s control) environment.
Binaries produced by Warbird can be encrypted and its code obfuscated. These binaries can execute “encrypted” code too.
Demonstration movies
- “Content key sniffing, arbitrary movie download and decryption (Canal+ Online VOD scenario, Win10 SW DRM)”, MP4 movie file, 32MB
- “Content key sniffing for Netflix (Win10 SW DRM)”, MP4 movie file, 10MB

Notes
As a result of the research several deficiencies have been discovered in various PMP components, which could be exploited to gain access to plaintext content keys guarded by PlayReady (Windows 10 / Windows 11 environment and SW DRM case).
It has been demonstrated that these plaintext keys could be successfully used to decrypt high definition (1080p) movies protected by PlayReady content protection (Canal+ Online VOD platform scenario).
On Windows platforms with HW DRM capability, the attack can still proceed as this feature can be easily disabled. Also, none of the streaming platforms tested enforced HW DRM for Windows (with HW DRM disabled, SW DRM was used and content key extraction could proceed both in Windows 10 and 11).
The root cause of the issue lies in SW DRM implementation used by default on Windows 10 without HW DRM capability. This version of Microsoft OS still (as of Mar 2024) has a 69% market share worldwide, which is partially caused by inability for users to upgrade to Windows 11 as their systems do not meet minimum upgrade requirements, such as having a TPM 2.0 chip. Windows 10 is set to retire on Oct 14, 2025. As such, a potential weak chain is to still persist for 1.5 year (due to the implementation done solely in SW, on a client side and in an environment under attacker’s control).
Please, note that this is a different research than our research from 2022 (and different Canal+ VOD service). The results and know-how obtained by this new research make the previous research obsolete in many ways.
Content security as part of a security field
DRM technology lies at the core of a security of the industry that is valued at $544 billion.
In that context, content security should not be different than the usual information security safeguarding organizations’ trade secrets, IT assets or personal data.
Exposure of the weaknesses or false security claims in the PayTV / video streaming / content security industry is equally important too.
This research is a continuation of our journey spanning 12 years during which we investigated security of PayTV / content security systems such as DVB chipsets / Conax Conditional Access System, SAT TV Platforms, set-top-boxes / VOD platforms and implementation of a DRM system.
Microsoft seeking details
On Apr 12, 2024, Microsoft PlayReady team reached to us with a request to report technical details and POC code through MSRC channel claiming that “by following the MSRC process to report your finding, it may be eligible for a reward” and that “close partnerships with the researcher community make customers more secure and we play an integral role by sharing issues under Coordinated Vulnerability Disclosure“).
As a response, we informed Microsoft that we cannot provide the company with additional details / codes pertaining to our PlayReady security research on Windows as this can only happen through a commercial agreement, not MSRC reporting channel (Apr 15, 2024).
The rationale for it is quite simple. The research took us nearly 9 months of work (on top of the 6 months of R&D done in 2022, which has been “consumed” and in some way ignored by the company).
The new research embeds some potentially valuable IP / know-how, which we need to protect too (see “Additional materials” paragraph describing potentially unauthorised, commercial use of our original idea for a rogue subscriber detection / deactivation). Finally, disclosure of our know-how / toolset to Microsoft might jeopardize our future projects targeting Windows OS platform.
If we decide to release any additional details, Microsoft will learn about these from a public source (this page in particular) and completely for free.
We believe the above should not impose any limits for Microsoft when it comes to the work aimed at making PlayReady on Windows more secure (vide details posted and access to all the know-how and engineering resources at company’s end).
We also believe the final outcome can be only positive too. Instead of limiting its focus on a single attack, Microsoft needs to conduct a more comprehensive review of Protected Media Path environment. Such an approach usually results in a discovery / fixing of additional issues.
Affected streaming platforms
- Disney Channel
- CNBC
- CNN
- BBC News
- Warner TV
- Paramount Channel
Our tests indicate that the following streaming platforms are affected:
The keys above should constitute a sufficient prove for the platforms mentioned to be able to confirm the attack.
All licenses received during testing were issued with SL2000 security level, which indicate the default presence of “Software-DRM Clients” on Windows 10 and 11 (clients backed mostly with software means, secrets protected through software or hardware means).
Taking into account the technique used to extract plaintext value of content keys, we assume that key extraction might also work for some other platforms relying on SW Microsoft PlayReady technology in a Windows OS environment (VOD and Live TV services). We verified it to work for Canal+ Live TV services and the following 6 sample live TV channels available through it:
In general, the ability to extract plaintext value of a content key from a DRM system constitutes a base for considering it to be compromised. This is especially valid taking into account the amount of efforts at Microsoft end (vide 10 years of innovation and more than $1B invested) to make it hard to conduct static and dynamic analysis of PlayReady operation on Windows platform.
Attack summary
- Windows 10 22H2 build 19045.1889 (Aug 2022)
- Windows 10 22H2 build 19045.2364 (Dec 2022)
- Windows 10 22H2 build 19045.2728 (Mar 2023)
- Windows 10 22H2 build 19045.3086 (Jun 2023)
- Windows 10 22H2 build 19045.3448 (Sep 2023)
- Windows 10 22H2 build 19045.3803 (Dec 2023)
- Windows 10 22H2 build 19045.4170 (Mar 2024)
- Windows 10 22H2 build 19045.4291 (Apr 2024)
- Windows 11 22H2 build 22621.521 (Sep 2022)
- Windows 11 22H2 build 22621.963 (Dec 2022)
- Windows 11 22H2 build 22621.1413 (Mar 2023)
- Windows 11 23H2 build 22631.3296 (Mar 2024)
- Windows 11 23H2 build 22631.3447 (Apr 2024)
The attack scenario makes it possible to extract plaintext values of content keys from a Protected Media Path process. The attack proceeds by exploiting a time window during which content keys have a XORed form – the plaintext value of such keys can be obtained by the means of a simple XOR operation with a magic 128-bit key sequence.
Our tests indicate that there are only two such magic key sequences used across Windows OS versions released since 2022 (one for Windows 10, the other for Windows 11).
The above has been confirmed on Windows 10 / 11 x64 systems across various builds from late 2022 till Apr 2024 (systems without and with HW DRM capability):
XOR_KEY_1
XOR_KEY_2
Identity and license store theft
We verified that content key extraction can be also performed in an offline manner. What is needed for that purpose are the encrypted license blobs and a client identity file.
In that context, a theft of a client identity and accompanying license store files from a user system does constitute a potential risk too (Windows 10 / 11 and SW DRM scenario).
Public CDN access
The risk related to unauthenticated Content Delivery Network (CDN) has been signalled by us at the time of 2022 research. Yet, we noticed that some providers still rely on publicly available CDN (Canal+ and Orange Web Cache scenario).
Public CDN makes it difficult to detect anomalous and/or unauthorised download behaviours.
Even though the content is encrypted, it does carry valuable information. A leak or extraction of a content key (such as demonstrated through this research) may result in the information to become immediately decrypted and compromised.
The above makes protection of content keys even more important (and content keys extraction even more severe).
Key validity and sharing
- Canal+ Online (1 month)
- Netflix (10 hours)
- HBO Max (6 hours)
- Amazon Prime Video (unknown)
- Sky Showtime (unknown)
It’s worth to note that validity of content keys issued for tested VOD content was set as following:
All live TV channels tested (Canal+ Online service) had key validity set to 8 hours.
These validity times are far longer than the validity of the decryption key (the so called Control Word key) used in a digital satellite TV (valid for 10 seconds only). Sharing of the keys has been also a significant problem for SAT TV providers.
Validity times implicate the exploitation window in case of content keys leak or extraction (how frequently the keys would need to be extracted by attackers for sharing before they get changed).
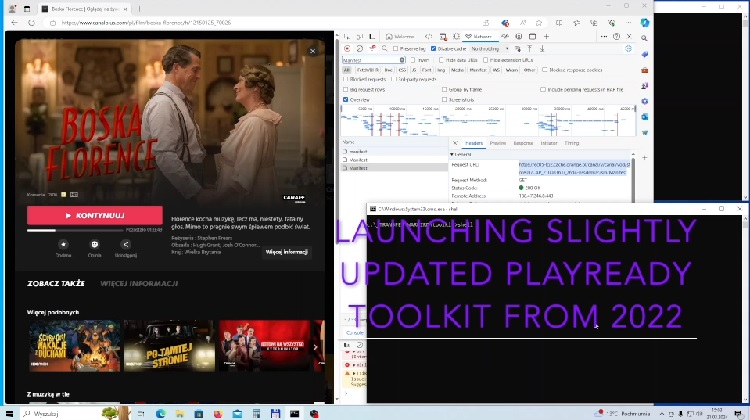
In general, it is questionable whether VOD and LiveTV content keys get changed at all. Our tests indicate this might not be the case. For instance, license data for “Boska Florence” movie available through Canal+ Online service carried the same content key on Mar 21, 2024 and Apr 25, 2024. This implicates key validity beyond initially granted license period (1 month). Similarly, same content keys were issued on Apr 24 and 25, 2024 (beyond the designated 8 hours license period) for all previously mentioned (tested) Live TV channels.
Possible mitigations
Streaming / VOD platforms that are either dissatisfied with PlayReady security or would like to implement a temporary mitigation might consider transition to / enforcement of other widely supported (by web browsers applications) content protection technologies.
Research impact
The research shows that the underlying technology such as Microsoft PlayReady can constitute a significant weak point. As such, it should not be ignored if streaming platforms are concerned about security of content.
One needs to keep in mind that a cost for a streaming platform subscription is in the range of 10-15 EUR (Poland). But, streaming platforms need to secure assets, which in some cases can generate nearly a billion in profits alone (vide Oppenheimer movie Box Office data, of which key is part of the posted key samples).
The attack that is able to extract content keys to premium movies for an arbitrary streaming platform requires just one rogue subscriber.
Content key extraction is also one of the worst things that can happen from a content security point of view as extracted keys can be shared online, they can be used to access premium video content without paying a subscription fee or decrypt and distribute movies over the Internet. Content key extraction and its impact is further explained in this blog post.
Potential disruptions in services reception
Some changes have been observed and information received with respect to “Terms of Use” service agreements of some streaming platforms / video services.
On 23 Apr 2024, a message has been received from Sky Showtime (to e-mail subscription address), which informs about changes to the terms of use of the service. The new terms seem to free Sky Showtime from a responsibility (liability) related to no reception of the programming (service) and no support for old applications versions (users might need to apply latest application / OS upgrades in order to be able to continue using Sky Showtime streaming services).
It’s also worth to mention that Sky Terms and Conditions have a separate “Microsoft PlayReady Notice” stating that “if the PlayReady technology fails to protect the content, content owners may require the service to restrict or prevent the delivery of protected content to specified devices or PC software applications”.
The above could implicate potential disruptions in some streaming services reception occurring as a result of a delivery of a fix / mitigation for this (or future) DRM hack or a switch off of the affected content protection technology.
Source: https://security-explorations.com/microsoft-warbird-pmp.html
“An interesting youtube video that may be related to the article above”