Recent findings from a Microsoft security blog reveal that attackers exploit newly discovered critical vulnerabilities in the OpenMetadata platform to target Kubernetes workloads. Subsequently, they use these workloads for cryptomining operations.
What is OpenMetadata?
OpenMetadata, an open-source platform, serves as a central repository for metadata lineage, enabling users to manage metadata across multiple data sources.
What are the vulnerabilities in OpenMetadata?
Microsoft’s security article highlights five vulnerabilities in OpenMetadata, namely CVE-2024-28255, CVE-2024-28847, CVE-2024-28253, CVE-2024-28848, and CVE-2024-28254. Published on March 15, 2024, these vulnerabilities impact the platform’s versions preceding 1.3.1.
Exploiting these vulnerabilities could enable attackers to bypass authentication and execute Remote Code Execution (RCE). Among them, CVE-2024-28255 (CVSS: 9.8) and CVE-2024-28253 (CVSS: 9.4) pose the most significant risks.
CVE-2024-28255 stems from JWT token validation deficiencies in JwtFilter, allowing attackers to manipulate path parameters, evade authentication, and potentially inject arbitrary SpEL expressions.
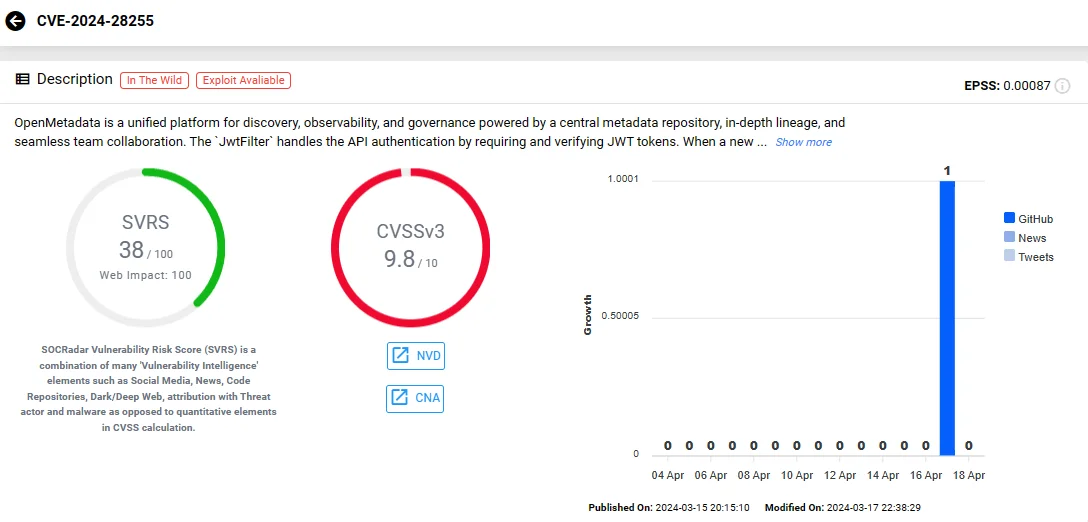
SOCRadar vulnerability card of CVE-2024-28255
CVE-2024-28253 facilitates Remote Code Execution by exploiting inadequate authorization checks in PolicyRepository.prepare, triggered by sending a PUT request to /api/v1/policies, leading to SpEL expression evaluation.
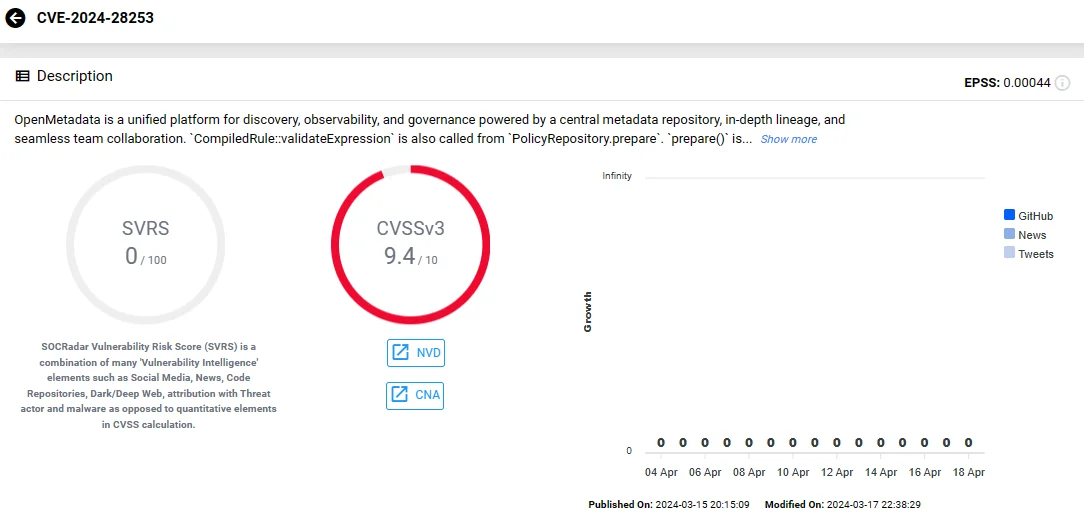
SOCRadar vulnerability card of CVE-2024-28253
Use the SOCRadar Attack Surface Management (ASM) module’s advanced monitoring capabilities to proactively identify vulnerabilities across your company’s digital assets.
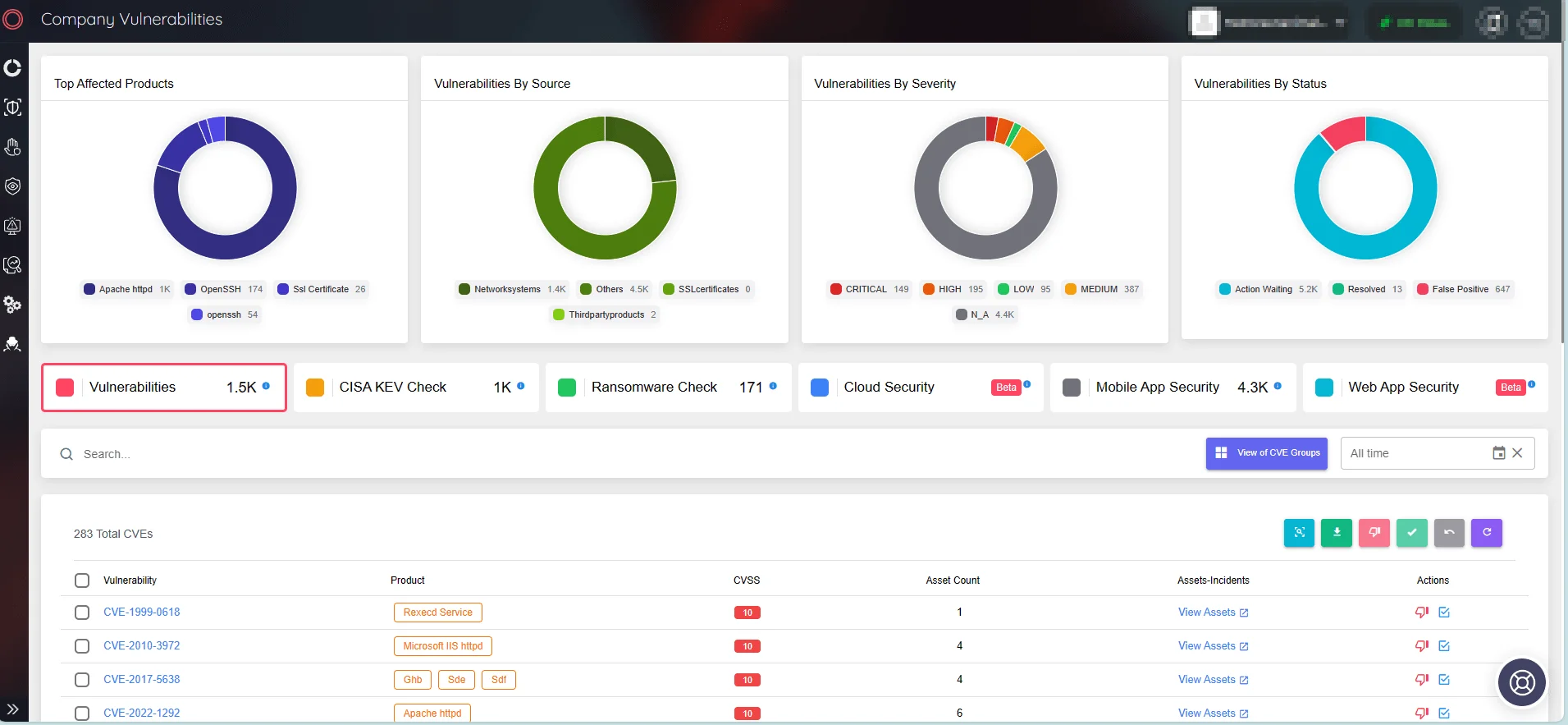
SOCRadar XTI provides real-time insights into vulnerabilities that affect your assets, allowing you to take quick action and improve patching strategies.
How is the attack initiated?
Concerningly, Microsoft reports that it has detected exploitation activity in Kubernetes environments since the beginning of April.
The following is an outline of the attack chain targeting Kubernetes through OpenMetadata vulnerabilities:
Initial Access
Attackers begin by targeting Kubernetes workloads of OpenMetadata that are exposed to the internet. Upon identifying a vulnerable version, they exploit the vulnerabilities to gain code execution on the container hosting the vulnerable OpenMetadata image.
Reconnaissance
After infiltrating the system, attackers validate their intrusion and assess control by contacting a publicly available service. They utilize ping requests to domains ending with oast[.]me and oast[.]pro, associated with Interactsh – an open-source tool for detecting out-of-band interactions.
Attackers establish network connectivity without raising suspicion by leveraging OAST domains, which are publicly resolvable but unique. This enables them to confirm exploitation success and validate connectivity before establishing a command-and-control channel and deploying malicious payloads.
Once access is established, attackers execute reconnaissance commands to gather information on the victim’s environment, including network configuration, OS version, and active users. They also extract environment variables of the Kubernetes workload, potentially containing connection strings and credentials for lateral movement.
Payload Deployment
Upon confirming access and connectivity, attackers download a cryptomining malware for mining XMR from a remote server, which is then executed with elevated permissions. Microsoft observed that the attacker/s used a server located in China.
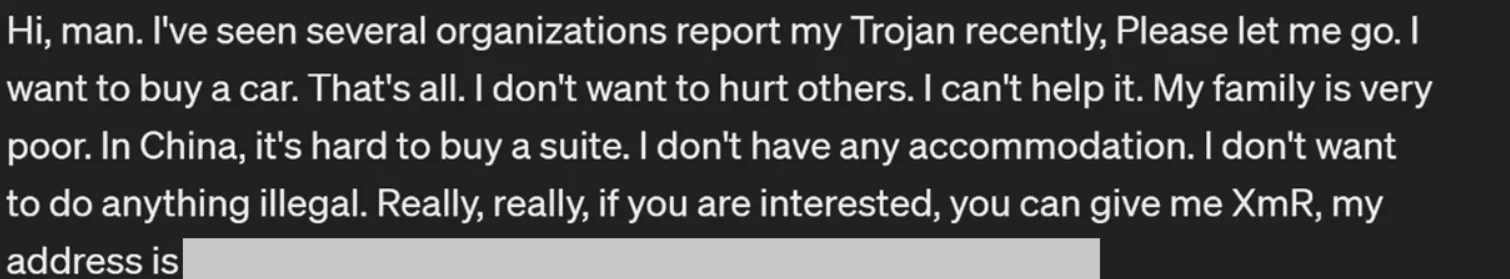
The attacker, purportedly located in China, left a personal note for the victims, mentioning their intention to “buy a car” as the reason for the attacks. (Microsoft)
Additional malware for both Linux and Windows operating systems was also discovered on the attacker’s server.
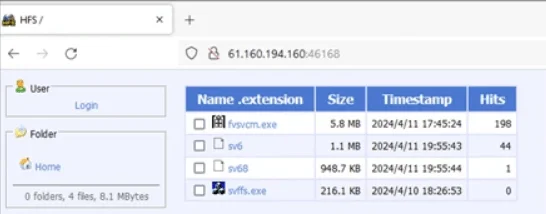
Additional malware hosted on the attacker’s server (Microsoft)
Following the malware’s deployment, attackers initiate a reverse shell connection to their remote server using the Netcat tool for remote access. Additionally, they establish persistence by scheduling tasks using cronjobs, ensuring the execution of malicious code at specific intervals.
How can you check if your cluster is vulnerable?
To get a list of all the images running on the cluster, use the following command:
kubectlgetpods–all-namespaces-o=jsonpath='{range.items[*]}{.spec.containers[*].image}{“n”}{end}’|grep’openmetadata’
Additionally, Microsoft advises updating the image version to the latest release if a pod contains a vulnerable image.
How to prevent the exploitation of OpenMetadata vulnerabilities?
Microsoft strongly urges customers to verify that clusters hosting OpenMetadata workloads are using an up-to-date image, specifically version 1.3.1 or newer. Also, when exposing OpenMetadata to the internet, it is advised to use strong authentication and avoid default credentials.
Additionally, it is recommended to review the indicators of compromise provided at the end of this blog post, as they can assist in threat hunting and investigation efforts.
Monitor the Latest Vulnerability Trends and Exploits with SOCRadar
SOCRadar’s Vulnerability Intelligence enables real-time monitoring of CVE and exploitation trends. Use its comprehensive database and advanced analytics to monitor updates, identify exploits, and gain actionable insights for proactive vulnerability management.
SOCRadar’s Vulnerability Intelligence
Indicators of Compromise (IOCs)
IOCs associated with this activity, as listed by Microsoft, are as follows.
IP Addresses:
- 8[.]222[.]144[.]60
- 61[.]160[.]194[.]160
- 8[.]130[.]115[.]208
SHA-256 hashes:
- 7c6f0bae1e588821bd5d66cd98f52b7005e054279748c2c851647097fa2ae2df
- 19a63bd5d18f955c0de550f072534aa7a6a6cc6b78a24fea4cc6ce23011ea01d
- 31cd1651752eae014c7ceaaf107f0bf8323b682ff5b24c683a683fdac7525bad
https://socradar.io/openmetadata-attackers-cryptomine-in-kubernetes