
Recent Insikt research analyzes ransomware and vulnerability trends spanning the past six years and offers insights into future expectations.
Ransomware groups exploit vulnerabilities in two distinct categories: those targeted by only a few groups and those widely exploited by several. Each category necessitates different defense strategies. Groups targeting specific vulnerabilities tend to follow particular patterns, enabling companies to prioritize defenses and audits. To defend against unique exploitation, understanding the likely targets and vulnerability types is crucial.
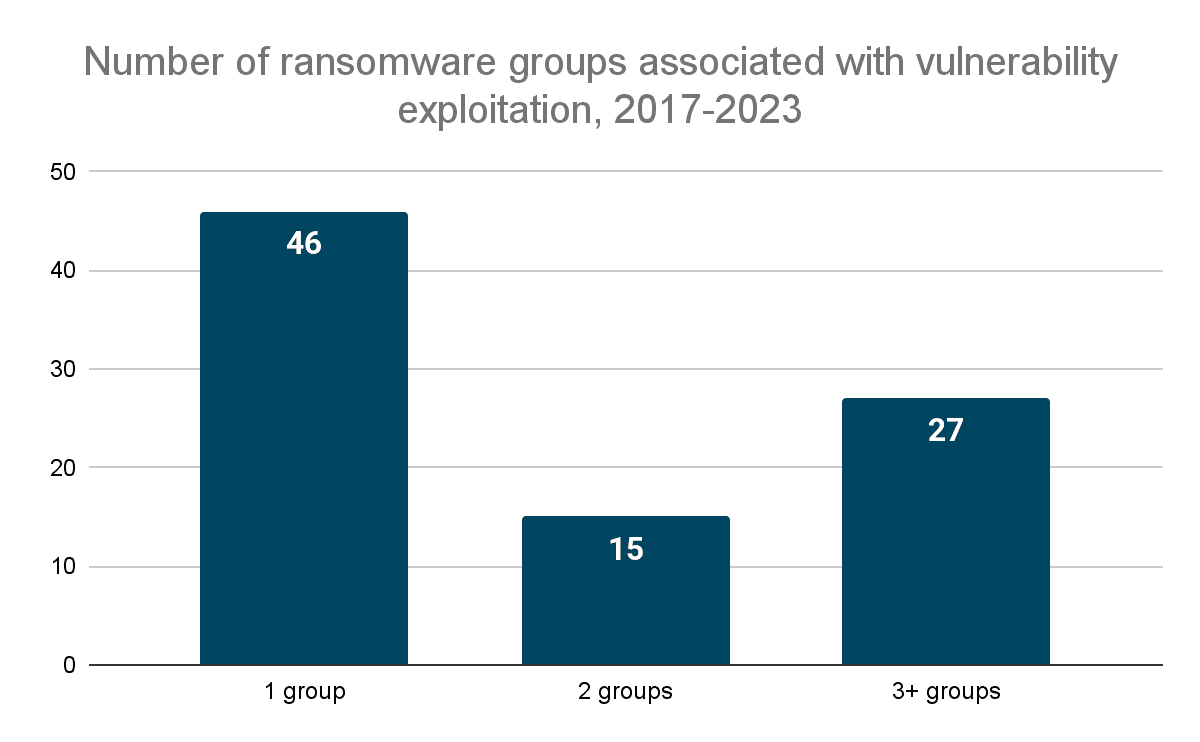 Diagram showing the number of ransomware groups that have been associated with vulnerability exploitation in the last five years. By one group, for example, we mean that only one group has been reported to have exploited a vulnerability (Source: Recorded Future)
Diagram showing the number of ransomware groups that have been associated with vulnerability exploitation in the last five years. By one group, for example, we mean that only one group has been reported to have exploited a vulnerability (Source: Recorded Future)
Widely exploited vulnerabilities are found in commonly used enterprise software and are easily exploited through various means like penetration testing modules. Defending against such exploits involves promptly patching vulnerabilities, monitoring security research for proofs of concept, and observing criminal forums for references to tech stack components rather than specific vulnerabilities.
Some ransomware groups focus on exploiting three or more vulnerabilities, providing clear targeting patterns for defenders. For instance, CL0P has targeted file transfer software from Accellion, SolarWinds, and MOVEit. Most targeted vulnerabilities are in widely used enterprise software and can be exploited easily. Vulnerabilities requiring unique vectors are typically exploited by only a few groups.
Ransomware operators and affiliates seldom discuss specific vulnerabilities, but the broader cybercriminal ecosystem identifies and discusses publicly known vulnerabilities and potential targets for exploitation.
Looking ahead to 2024, advancements in generative AI may lower the technical barrier for cybercriminals, facilitating the exploitation of more zero-day vulnerabilities. Major vendors like Google and Apple may become targets of ransomware campaigns, which were previously immune to such threats. Additionally, a potential rebound in cryptocurrency value might shift extortion groups' focus towards crypto wallet theft from vulnerability research.
To read the entire analysis, click here to download the report as a PDF.
Source: Original Post