Threat Actor: USDoD | USDoD
Victim: Various high-profile organizations and critical industries | various high-profile organizations and critical industries
Price: Not specified
Exfiltrated Data Type: Military data, law enforcement emails, sensitive data
Additional Information :
- USDoD’s motivation for involvement in cybercrime activities is purely for fun, challenge, and exploiting the security systems of the USA and Europe.
- The threat actor employs social engineering and impersonation techniques to gain unauthorized access to sensitive data.
- The transition from “NetSec” to “USDoD” was not related to the #RaidAgainstTheUS campaign but rather a personal request from a project called Tulip, which aimed to acquire military data for artificial intelligence development.
- USDoD denies having any political, racial, or religious motivations and dislikes being called a pro-Russian threat actor.
- The threat actor plans each step before execution to evade detection and maintain anonymity while targeting defense entities like CEPOL and NATO.
- USDoD does not have any political views and envisions cyber threats continuing to grow with the development of new technologies and geopolitical movements.
- The threat actor plans to establish a private company to sell military intelligence on the dark web in the long term.
- USDoD has doubts about the current state of BreachForums and has their own channel on Telegram.
- The rebranding of the Telegram channel from BlackSec to SparrowCorp was done for identification purposes and to prioritize targeting certain countries.
- USDoD is not affiliated with BlackSec or the five families.
- An investigation targeting a network of pedophile sites involving offshore shell companies was paused due to a lack of expected help and differences in evidence standards with the FBI.
- USDoD does not believe their cyber criminal activities pose a significant risk for them and continues to be active in breaching companies.
- The threat actor acknowledges the potential harm caused by cybercrime activities but avoids directly attacking entities such as hospitals, child care facilities, and critical infrastructure.
- USDoD rationalizes the impact of their activities by accepting the legal and cybersecurity risks and taking responsibility for their actions.
Cyber threats are not just theoretical but often materialize in the form of individuals or groups targeting critical infrastructures and organizations worldwide. Our interview dives deep into the mindset and motivations of a threat actor who operates under the alias “USDoD.”
This persona has been associated with high-profile cyber incidents, one of the recent being the alleged “Fico” breach, prompting questions about their motives, methods, and impact on the digital landscape. Let’s look at the questions we prepared and USDoD’s answers.
Typo errors in USDoD’s answers have been rectified, while the sentences remain unaltered.
Q1: Can you share the motivations behind your involvement in cybercrime activities, particularly targeting high-profile organizations and many critical industries?
– “I told to databreachs.net that my motivation is purely for fun, challenge, the USA and Europe have the most security system and since the begin I always liked of a real challenge and exploit these system it is the challenge I need to do and take it.”
Q2: Your approach seems to rely heavily on social engineering and impersonation. Could you elaborate on how you employ these techniques to gain unauthorized access to sensitive data?
– “Usually to do this there is two main approaches, the first and the most important one it is to find a key people who may work in some big company or in public sector, I run a full dox on those people and start impersonating these targets.
The second approach is similar but I just take some military or law enforcement emails using stealer and I starting impersonating these tho.”
Q3: What led to your transition from being known as “NetSec” on RaidForums to adopting the moniker “USDoD” and engaging in the #RaidAgainstTheUS campaign?
– “First my alias transition it is not related to the campaign I made back on RF.
The attack against military and industrial base it as because of a personal request from a project called tulip.
I was contacted by an a very closed friend with ties to me to contribute to an artificial intelligence initiative named Tulip. The primary objective of this project was to acquire military data for further development within the artificial intelligence domain.
I need to gathering a lot of military data to help my friend develop this project and since my work on that none confidential information have been shared in public or caused any harm to the USA, because that is not the main goal at this project.”
Q4: Could you once again clarify your stance regarding political affiliations or motivations, especially allegations of being a pro-Russian threat actor?
– “I don’t have any political, racial or religious motivation, I disliked a lot to be called as a pro-Russia, my work with some individuals are based on professional request not in political reason.”
Q5: What challenges have you encountered in your operations, particularly in evading detection and maintaining anonymity while targeting defense entities like CEPOL and NATO?
– “I generally plan each step before execution and follow each task according to plan, I don’t usually encounter any difficulties.
NATO just closed my access due to the fact that I request the increase of level from my account.”
Q6: Is there a reason other than your political views that the US and its allies are such a primary target for you?
– “I don’t have any political views, I would like to live in a world where everyone should live without political view. I don’t like of political but I understand the fact of their existence.”
Q7: How do you envision the future of cyber threats evolving, and what role do you play in this landscape?
– “My thought is that with new technologies being developed for defense the number of attacks will tend to continue to grow.
There is no way to pause or stagnant cyber threats, the only way for this to happen is some catastrophe that exterminates a large part of the population, it is pure and logical, the more new technologies are developed and the more geopolitical movements become more intense, the greater the threats will be inside and outside the cybernetic field.”
Q8: According to some articles, you plan to establish some sort of a private company to sell military intelligence on the dark web. Is there any realism to this for you? What are your long-term goals in this regard?
– “Yes the plan is already in an ongoing situation and the phase one is already finished. (Acquisition and access to a tool that will give me access for most of military servers) I can’t disclose more than that for now.
Right now I have all the tools to start to pivoting access into military servers around the globe plus I know how the system works and I know how I will be able to access without any problem and the long term goals it is to get a huge dataset to start selling around the interwebs partly a few tasks need to be done first but I’m already more than half done of it.”
Q9: What are your thoughts on the current state of BreachForums? You mentioned some of your doubts in a tweet. Is this suspicion one of the reasons why you have your own channel on Telegram now?
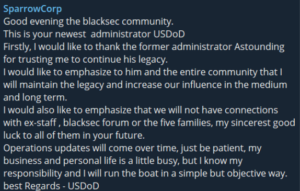 USDoD’s first statement on SparrowCorp
USDoD’s first statement on SparrowCorp
– “I took this as an opportunity. Astounding trusted me a lot to keep his legacy and I’m doing it right now and about The breachforums situation: That is what my intuition is telling me about.
I don’t have any concrete evidence but still I have that intuition telling me that something is coming. But after my posts on twitter seems that the staff fixed most of the issues but they still have a way to go on it.
I hope everyone keep a eyes open and I hope everything stay good and ok with Breachforum system and staff.”
Q10: While we’re on the subject of Telegram, you recently rebranded an ongoing Telegram channel from BlackSec to SparrowCorp, signaling a new beginning and new operations. Could you elaborate on the reasons behind this rebranding and the changes you plan to implement regarding operations and modus operandi?
– “I made this change purely to have more identification with the group and play something on my way, you know?
I like to place targets in certain countries that I believe the old group did not have as a priority target. But this is something that I will manage in the long term.”
Q11: Can it be said that there is an affiliation with Blacksec? How did you agree on the channel transaction?
– “Glad you asked me this. Before taking ownership I talked with Astounding and he personally told to me that I’m not related to blacksec or with the five families.
I’m on my own like usual and I wish all of success to the five families.”
Q12: Your announcements on Telegram mentioned an upcoming operation targeting an alleged network of pedophile sites spanning multiple countries and involving offshore shell companies. Could you elaborate on the situation?
– “The investigation is currently paused. As you can see I’m back to my old activities.
Someone I trusted that I expected help simply let me down at the moment I needed it most.
I managed to evolve a lot, I identified a person behind, as the owner of the shell company and he is also a porn producer.
I reported it to the FBI at the beginning of the investigation, but what the FBI considers evidence is much higher than what I consider it to be.
This kind of made me upset, because as much as I managed to bring down the entire system in a illegally way , I was really hoping for help in the investigation either from my “friend” or from the FBI but they have their own interest going on they simple don’t care.”
Q13: We’ve noticed significant shifts in cybercrime due to recent law enforcement successes. Do you believe that attention from your cyber criminal activities poses a similar risk for you?
– “No. I don’t think so and I wish to all federal agencies and military personnel around the globe a good luck to find me.”
Q14: Have these events effectively halted your activities for the time being? After the SparrowCorp channel, besides your somewhat regular updates, there isn’t much going on, at least from an outsider’s perspective.
– “I would like to say that you are wrong, after the airbus attack all my operation are still going on but due to the pedo network investigation I have paused breaching companies but Last week i released fico.com database, Last month I release 24gb of Thales software and a few days back I got access to epa.gov and dumped their entire contact database.
I’m 100% back on business and even more motivated.”
Q15: There is always potential harm caused by engaging in activities that clearly fall under cybercrime. Therefore, don’t you believe your actions also negatively impact innocent people?
– “I agree and disagree at the same time. It’s a fine line, you know.
This is one of the reasons I would never attack a hospital or child care facility.
I would not dare to put this type of entity at risk, moreover, critical infrastructure such as the energy sector and the water and food sector, and the nuclear sector are also outside my jurisdiction.
I would never directly attack entities of this level”
Q16: Finally, considering the legal and cybersecurity risks associated with your activities, how do you rationalize their impact on individuals and organizations?
– “I know that I’m facing a huge and higher legal risky during all these activities but I already crossed a line so there is no point of return now.
I will face whatever I had to do and I’m ok with that but yeah I will answer from my actions only and I will always take responsibility of it don’t matter how hard should be.”
In this way, we have come to the end of our questions. Although having to prepare and forward the questions in advance due to the usual difficulties in communication prevents us from focusing on the latest breaches, we have reached a broad framework about the USDoD persona. USDoD, active on BreachForums, X, and the Telegram channel, made major breach claims last week and looks set to continue its cyber criminal activities.
Original Source: https://dailydarkweb.net/from-netsec-to-sparrowcorp-an-exclusive-interview-with-the-enigmatic-usdod/