08/04/2024
As already highlighted and extensively documented in each of our weekly reports, since the beginning of the year there has been a significant increase in AgentTesla campaigns targeting Italy.
Just last week, CERT-AGID detected a particularly intense activity characterized by the use of PDF attachments. Today, another extensive operation aimed at distributing AgentTesla in Italy emerges, which seems to follow a constant monthly rhythm that has been going on for about nine months now.
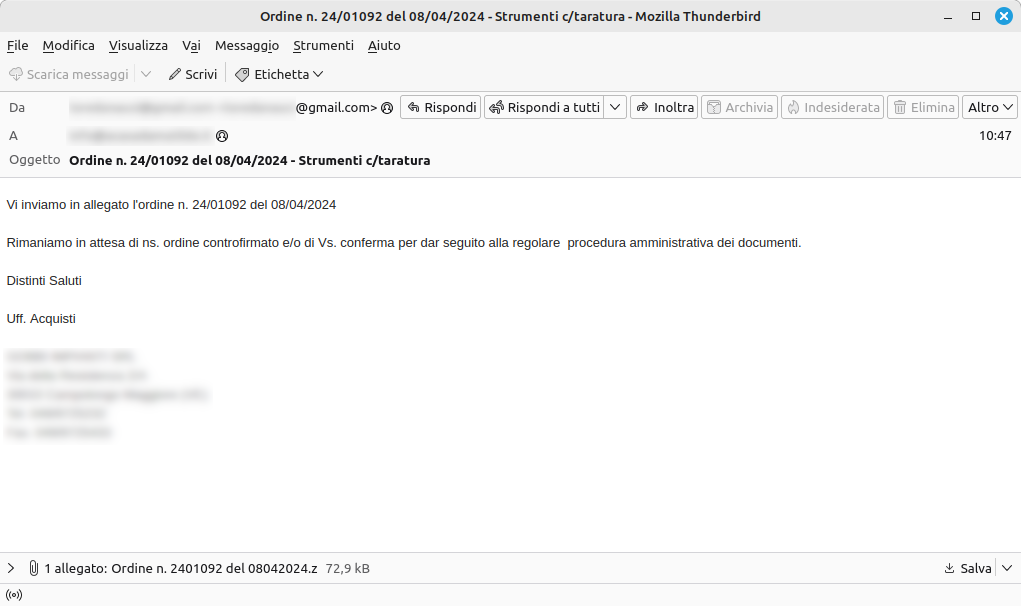
The strategy adopted to promote this campaign over the months has consistently focused on the theme of “Order”, based on a new existing Italian SRL company each time.
Although the content and, in part, the subject of the emails tend to vary, the constant element remains the attachment: a compressed file in .ZIP (or .Z) format that includes an executable .EXE file or a .SRC file, always with different hashes.
Command and Control Server
Although the techniques used may vary, the command and control (C2) server involved has already been identified several times by CERT-AGID since July 2023.
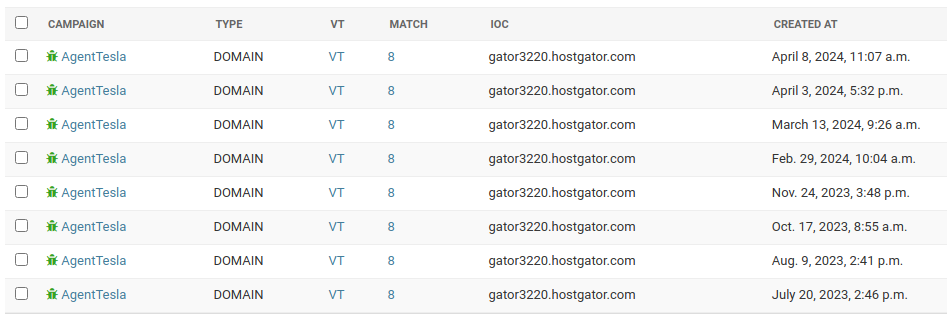
The constant reuse of the same C2 server suggests that the attackers continue to use known infrastructures, probably relying on the slowness of defenses or the ineffectiveness of the mitigation measures adopted in Italy so far.
Different Loaders
The initial loader used to proceed through the subsequent phases until reaching the final DLL changes with each iteration, alternating between 64-bit and 32-bit versions. In the July 2023 campaign, resources were decrypted using the AES algorithm, while in the latest wave, Triple DES was used.
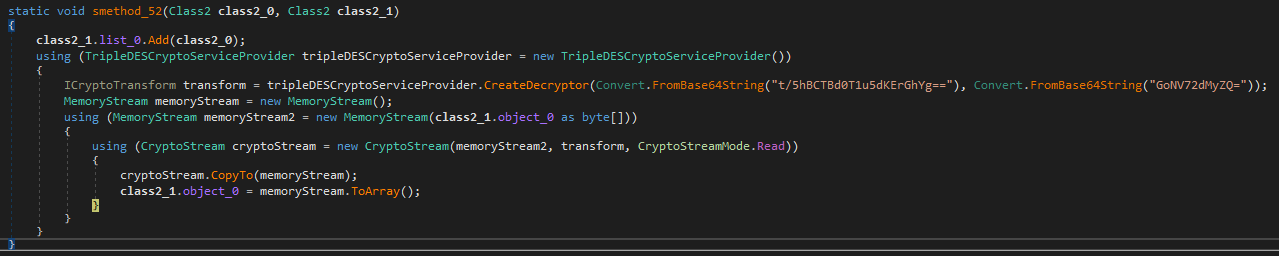
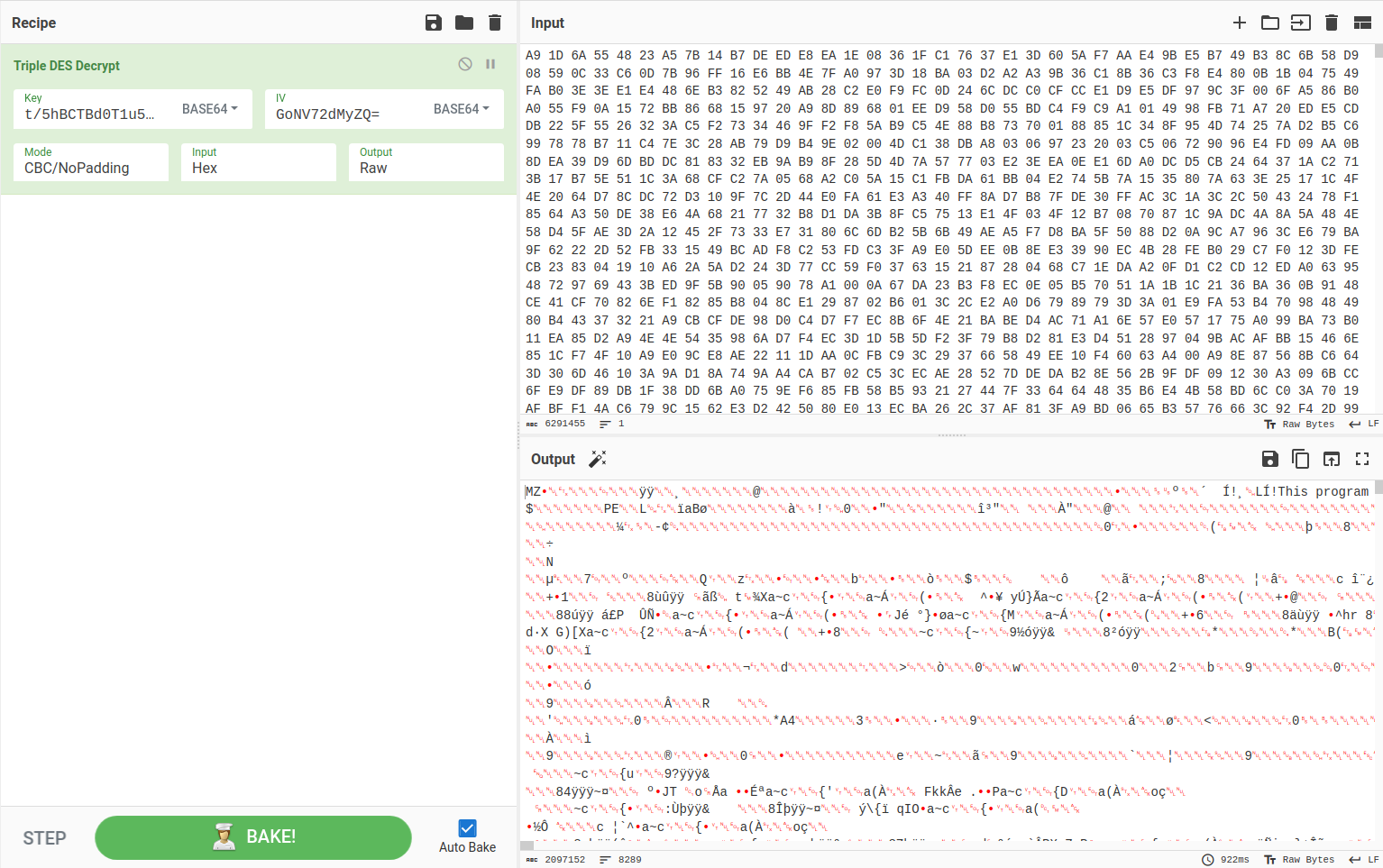
The keys, integrated directly into the system, are easily identifiable. In this specific scenario, a CyberChef recipe was used to decrypt the initial phase and obtain the first DLL:
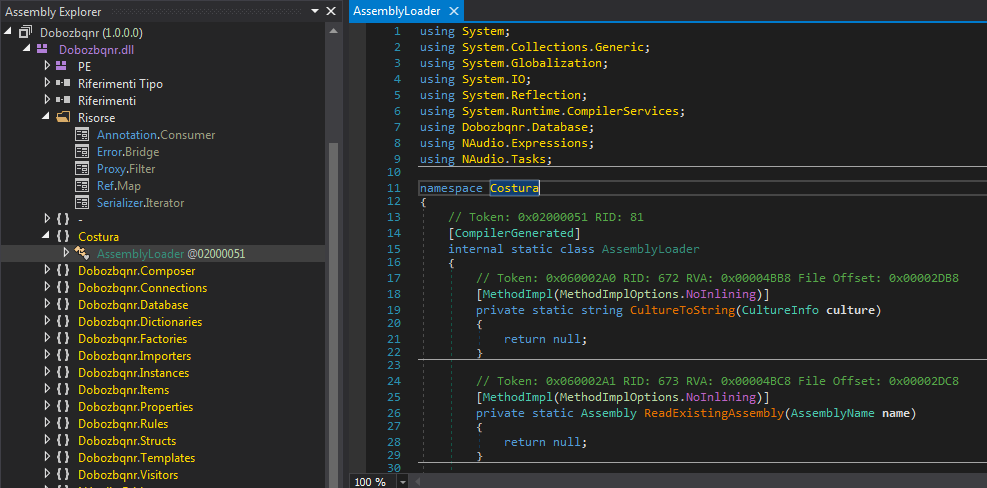
Final AssemblyLoader
The final loader adopted by AgentTesla is Costura, an open-source project proposed as an alternative to ILMerge. This library is specifically used to load the payload into memory during execution. This element is also now a constant:
Conclusions
The entire campaign under examination operates almost exclusively using RAM memory, emphasizing the essential need to implement both real-time and background memory scans for greater security. This approach, now used by the majority of malware, highlights the high complexity of the methods used by attackers to bypass conventional security mechanisms that still rely on scans of persistent memory. The fact that the only element of the campaign that is actually saved to the hard disk is the initial attachment demonstrates a refined masking capability and highlights the crucial need for careful monitoring to detect the attack in its early stages, in order to prevent larger and more damaging system breaches.
As already mentioned, the repeated identification of the command and control (C2) server suggests that the attackers persist in using already known infrastructures, presumably leveraging the slowness of defensive reactions or the possible ineffectiveness of mitigation strategies implemented in Italy. This could indicate not only a deep knowledge of the Italian security landscape by the attackers but also a calculated approach that relies on tactics that have proven successful in the past.
This scenario highlights the critical need to accelerate threat response and strengthen security measures, including timely updating of detection systems and continuous review of security policies to effectively counter these persistent threats.
Indicators of Compromise
In order to make the details for countering this campaign public, the detected IoCs are listed below, already shared with the Accredited Public Administrations through the CERT-AgID IoC Feed.
Link: Download IoC
Source: Original Post