Keypoints :
APT28 is engaged in cyber espionage targeting Central Asia and Kazakhstan.…
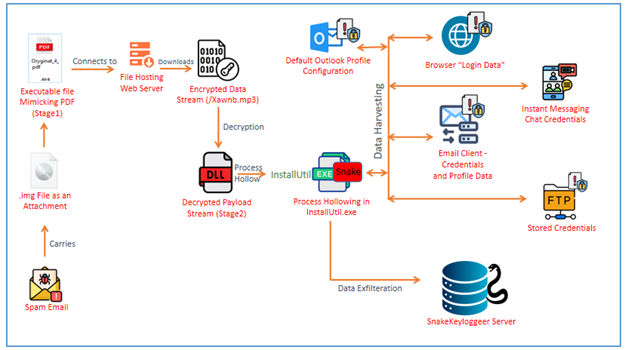
APT28 has been observed conducting cyber espionage activities focusing on Central Asia and Kazakhstan. This analysis explores a heavily obfuscated malware sample, assessing its capabilities, particularly its use of VBScript and interaction with a command-and-control server. Affected: APT28, Central Asia, Kazakhstan
Read More 




 , Launch Your Own Ransomware(RAAS) Business with Our Exclusive Ransomware Panel Source Cod…
, Launch Your Own Ransomware(RAAS) Business with Our Exclusive Ransomware Panel Source Cod…